diff --git a/ObjectivePGP.framework/Headers/ObjectivePGP.h b/ObjectivePGP.framework/Headers/ObjectivePGP.h
new file mode 100644
index 0000000000000000000000000000000000000000..e375c89e2ae6655d38c6750e42c0241a29e83fa6
--- /dev/null
+++ b/ObjectivePGP.framework/Headers/ObjectivePGP.h
@@ -0,0 +1,28 @@
+//
+// ObjectivePGP
+//
+// Copyright © Marcin Krzyżanowski. All rights reserved.
+//
+// DO NOT MODIFY. FILE GENERATED AUTOMATICALLY.
+
+#import <Foundation/Foundation.h>
+
+//! Project version number for ObjectivePGP.
+FOUNDATION_EXPORT double ObjectivePGPVersionNumber;
+
+//! Project version string for ObjectivePGP.
+FOUNDATION_EXPORT const unsigned char ObjectivePGPVersionString[];
+
+#import <ObjectivePGP/PGPMacros.h>
+#import <ObjectivePGP/PGPTypes.h>
+#import <ObjectivePGP/ObjectivePGPObject.h>
+#import <ObjectivePGP/PGPKeyGenerator.h>
+#import <ObjectivePGP/PGPKeyring.h>
+#import <ObjectivePGP/PGPFingerprint.h>
+#import <ObjectivePGP/PGPKeyID.h>
+#import <ObjectivePGP/PGPUser.h>
+#import <ObjectivePGP/PGPPartialSubKey.h>
+#import <ObjectivePGP/PGPPartialKey.h>
+#import <ObjectivePGP/PGPKey.h>
+#import <ObjectivePGP/PGPExportableProtocol.h>
+#import <ObjectivePGP/PGPArmor.h>
diff --git a/ObjectivePGP.framework/Info.plist b/ObjectivePGP.framework/Info.plist
new file mode 100644
index 0000000000000000000000000000000000000000..820bd0f02dea0c14260f8c62e2bacc75631dc6a1
Binary files /dev/null and b/ObjectivePGP.framework/Info.plist differ
diff --git a/ObjectivePGP.framework/LICENSE.txt b/ObjectivePGP.framework/LICENSE.txt
new file mode 100644
index 0000000000000000000000000000000000000000..0c16858c7f766620f86675fdd6c88addbe9186d6
--- /dev/null
+++ b/ObjectivePGP.framework/LICENSE.txt
@@ -0,0 +1,32 @@
+The ObjectivePGP stays under a dual license:
+
+====================================================================
+Free for non-commercial use:
+
+Copyright (C) 2014-2017, Marcin Krzyżanowski All rights reserved.
+
+Redistribution and use in source and binary forms, with or without
+modification, are permitted provided that the following conditions are met:
+
+- Redistributions of source code must retain the above copyright notice, this
+ list of conditions and the following disclaimer.
+
+- Redistributions in binary form must reproduce the above copyright notice,
+ this list of conditions and the following disclaimer in the documentation
+ and/or other materials provided with the distribution.
+
+THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
+AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
+IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
+DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR CONTRIBUTORS BE LIABLE
+FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL
+DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
+SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER
+CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
+OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
+OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
+
+====================================================================
+Paid for commercial use:
+
+Commercial-use license to use in commercial products. Please contact me via email (marcin@krzyzanowskim.com) for details.
\ No newline at end of file
diff --git a/ObjectivePGP.framework/Modules/module.modulemap b/ObjectivePGP.framework/Modules/module.modulemap
new file mode 100644
index 0000000000000000000000000000000000000000..ebf6c60158ac70b3e220cf2f2a6589449c672674
--- /dev/null
+++ b/ObjectivePGP.framework/Modules/module.modulemap
@@ -0,0 +1,6 @@
+framework module ObjectivePGP {
+ umbrella header "ObjectivePGP.h"
+
+ export *
+ module * { export * }
+}
diff --git a/ObjectivePGP.framework/ObjectivePGP b/ObjectivePGP.framework/ObjectivePGP
new file mode 100755
index 0000000000000000000000000000000000000000..d1ada8e13bd0885950ae87cbbb471baff8a10d09
Binary files /dev/null and b/ObjectivePGP.framework/ObjectivePGP differ
diff --git a/ObjectivePGP.framework/PrivateHeaders/ObjectivePGP-Private.h b/ObjectivePGP.framework/PrivateHeaders/ObjectivePGP-Private.h
new file mode 100644
index 0000000000000000000000000000000000000000..c2b3ae2ddb79cb194d1bac7554b0c13c4085f672
--- /dev/null
+++ b/ObjectivePGP.framework/PrivateHeaders/ObjectivePGP-Private.h
@@ -0,0 +1,70 @@
+//
+// ObjectivePGP
+//
+// Copyright © Marcin Krzyżanowski. All rights reserved.
+//
+// DO NOT MODIFY. FILE GENERATED AUTOMATICALLY.
+
+#import <Foundation/Foundation.h>
+
+//! Project version number for ObjectivePGP.
+FOUNDATION_EXPORT double ObjectivePGPVersionNumber;
+
+//! Project version string for ObjectivePGP.
+FOUNDATION_EXPORT const unsigned char ObjectivePGPVersionString[];
+
+#import <ObjectivePGP/PGPCryptoHash.h>
+#import <ObjectivePGP/PGPMacros+Private.h>
+#import <ObjectivePGP/PGPFoundation.h>
+#import <ObjectivePGP/PGPSecretKeyPacket+Private.h>
+#import <ObjectivePGP/PGPPacket+Private.h>
+#import <ObjectivePGP/PGPCryptoUtils.h>
+#import <ObjectivePGP/PGPRSA.h>
+#import <ObjectivePGP/PGPS2K.h>
+#import <ObjectivePGP/NSArray+PGPUtils.h>
+#import <ObjectivePGP/PGPUserIDPacket.h>
+#import <ObjectivePGP/PGPSymetricKeyEncryptedSessionKeyPacket.h>
+#import <ObjectivePGP/PGPSecretKeyPacket.h>
+#import <ObjectivePGP/PGPPublicKeyPacket.h>
+#import <ObjectivePGP/PGPPublicSubKeyPacket.h>
+#import <ObjectivePGP/PGPUserAttributeImageSubpacket.h>
+#import <ObjectivePGP/NSData+compression.h>
+#import <ObjectivePGP/PGPSignatureSubpacket.h>
+#import <ObjectivePGP/PGPSecretSubKeyPacket.h>
+#import <ObjectivePGP/NSMutableData+PGPUtils.h>
+#import <ObjectivePGP/PGPUserAttributePacket.h>
+#import <ObjectivePGP/PGPPacket.h>
+#import <ObjectivePGP/NSData+PGPUtils.h>
+#import <ObjectivePGP/PGPUser+Private.h>
+#import <ObjectivePGP/PGPBigNum.h>
+#import <ObjectivePGP/PGPKeyMaterial.h>
+#import <ObjectivePGP/PGPMPI.h>
+#import <ObjectivePGP/PGPLiteralPacket.h>
+#import <ObjectivePGP/PGPTrustPacket.h>
+#import <ObjectivePGP/PGPSignatureSubpacketHeader.h>
+#import <ObjectivePGP/PGPSignatureSubpacketCreationTime.h>
+#import <ObjectivePGP/PGPUserAttributeSubpacket.h>
+#import <ObjectivePGP/PGPSignaturePacket.h>
+#import <ObjectivePGP/PGPOnePassSignaturePacket.h>
+#import <ObjectivePGP/PGPPublicKeyEncryptedSessionKeyPacket.h>
+#import <ObjectivePGP/PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h>
+#import <ObjectivePGP/PGPModificationDetectionCodePacket.h>
+#import <ObjectivePGP/PGPEncryptedSessionKeyPacketProtocol.h>
+#import <ObjectivePGP/PGPSymmetricallyEncryptedDataPacket.h>
+#import <ObjectivePGP/PGPPKCSEmsa.h>
+#import <ObjectivePGP/PGPPKCSEme.h>
+#import <ObjectivePGP/PGPCryptoCFB.h>
+#import <ObjectivePGP/PGPPacketHeader.h>
+#import <ObjectivePGP/PGPLogging.h>
+#import <ObjectivePGP/PGPCompressedPacket.h>
+#import <ObjectivePGP/PGPPartialSubKey+Private.h>
+#import <ObjectivePGP/PGPDSA.h>
+#import <ObjectivePGP/PGPPublicKeyPacket+Private.h>
+#import <ObjectivePGP/PGPSignatureSubpacket+Private.h>
+#import <ObjectivePGP/PGPSignaturePacket+Private.h>
+#import <ObjectivePGP/PGPKey+Private.h>
+#import <ObjectivePGP/PGPPacketFactory.h>
+#import <ObjectivePGP/PGPKeyring+Private.h>
+#import <ObjectivePGP/PGPBigNum+Private.h>
+#import <ObjectivePGP/PGPPartialKey+Private.h>
+#import <ObjectivePGP/PGPSignatureSubpacketEmbeddedSignature.h>
diff --git a/ObjectivePGP.framework/PrivateHeaders/PGPPartialKey+Private.h b/ObjectivePGP.framework/PrivateHeaders/PGPPartialKey+Private.h
new file mode 100644
index 0000000000000000000000000000000000000000..8d24ac66479bc2dc6e0ba08e5068dc4ac6377703
--- /dev/null
+++ b/ObjectivePGP.framework/PrivateHeaders/PGPPartialKey+Private.h
@@ -0,0 +1,24 @@
+//
+// Copyright (c) Marcin Krzyżanowski. All rights reserved.
+//
+// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
+// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
+// This notice may not be removed from this file.
+//
+
+#import <ObjectivePGP/ObjectivePGP.h>
+
+NS_ASSUME_NONNULL_BEGIN
+
+@interface PGPPartialKey ()
+
+@property (nonatomic, readwrite) PGPKeyType type;
+@property (nonatomic, copy, readwrite) NSArray<PGPPartialSubKey *> *subKeys;
+@property (nonatomic, copy, readwrite) NSArray<PGPSignaturePacket *> *directSignatures;
+@property (nonatomic, nullable, copy, readwrite) PGPSignaturePacket *revocationSignature;
+
+- (void)loadPackets:(NSArray<PGPPacket *> *)packets NS_REQUIRES_SUPER;
+
+@end
+
+NS_ASSUME_NONNULL_END
diff --git a/ObjectivePGP.framework/PrivateHeaders/PGPUser+Private.h b/ObjectivePGP.framework/PrivateHeaders/PGPUser+Private.h
new file mode 100644
index 0000000000000000000000000000000000000000..314f57ed8473955a2ab48783488bbcdef1622b83
--- /dev/null
+++ b/ObjectivePGP.framework/PrivateHeaders/PGPUser+Private.h
@@ -0,0 +1,32 @@
+// Copyright (c) Marcin Krzyżanowski. All rights reserved.
+//
+// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
+// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
+// This notice may not be removed from this file.
+//
+
+#import <ObjectivePGP/ObjectivePGP.h>
+#import <ObjectivePGP/PGPUserIDPacket.h>
+#import <ObjectivePGP/PGPUserAttributePacket.h>
+#import <ObjectivePGP/PGPSignaturePacket.h>
+
+NS_ASSUME_NONNULL_BEGIN
+
+@interface PGPUser ()
+
+@property (nonatomic, copy) NSArray<PGPSignaturePacket *> *selfCertifications;
+@property (nonatomic, copy) NSArray<PGPSignaturePacket *> *otherSignatures;
+@property (nonatomic, copy) NSArray<PGPSignaturePacket *> *revocationSignatures;
+
+@property (nonatomic, copy, nullable) PGPUserAttributePacket *userAttribute;
+@property (nonatomic, copy, readonly) PGPUserIDPacket *userIDPacket;
+
+@property (nonatomic, readonly) NSArray<PGPPacket *> *allPackets;
+
+- (instancetype)initWithUserIDPacket:(PGPUserIDPacket *)userPacket NS_DESIGNATED_INITIALIZER;
+
+- (nullable PGPSignaturePacket *)validSelfCertificate;
+
+@end
+
+NS_ASSUME_NONNULL_END
diff --git a/ObjectivePGP.framework/README.md b/ObjectivePGP.framework/README.md
new file mode 100644
index 0000000000000000000000000000000000000000..1b91f05f9f45d13a6fdf6f86c56ced98633ae2f5
--- /dev/null
+++ b/ObjectivePGP.framework/README.md
@@ -0,0 +1,220 @@
+
+
+[](https://cocoapods.org/pods/ObjectivePGP)
+[](http://cocoadocs.org/docsets/ObjectivePGP)
+[](./ObjectivePGP.playground/Contents.swift)
+[](http://twitter.com/krzyzanowskim)
+
+
+**ObjectivePGP** is an implementation of [OpenPGP](https://en.wikipedia.org/wiki/Pretty_Good_Privacy#OpenPGP) protocol for iOS and macOS. OpenPGP is the most widely used email encryption standard. It is defined by the OpenPGP Working Group of the Internet Engineering Task Force (IETF).
+
+Here is the [blog post](http://blog.krzyzanowskim.com/2014/07/31/short-story-about-openpgp-for-ios-and-os-x-objectivepgp/) story.
+
+## Contribution
+
+You are welcome to contribute. Please create [Pull Request](https://github.com/krzyzanowskim/ObjectivePGP/pulls) against `develop` branch.
+
+## Usage
+
+```objective-c
+#import <ObjectivePGP/ObjectivePGP.h>
+```
+
+```swift
+import ObjectivePGP
+```
+
+##### Read keys (private or public)
+
+```objective-c
+NSArray<PGPKey *> *keys = [ObjectivePGP readKeysFromPath:@"/path/to/key.asc" error:nil];
+```
+
+```swift
+let keys = try ObjectivePGP.readKeys(fromPath: "/path/to/key.asc")
+```
+
+##### Keyring
+
+Keyring is a storage (in memory or on disk) that keep all sorts of PGP keys.
+
+```objective-c
+PGPKeyring *keyring = ObjectivePGP.defaultKeyring;
+PGPKeyring *keyring = [[PGPKeyring alloc] init];
+
+NSArray<PGPKey *> *allKeys = keyring.keys;
+[keyring importKeys:@[key]];
+[keyring deleteKeys:@[key]];
+
+[keyring importKey:@"979E4B03DFFE30C6" fromPath:@"/path/to/secring.gpg"];
+PGPKey *key = [keyring findKeyWithIdentifier:@"979E4B03DFFE30C6"];
+NSArray<PGPKey *> keys = [pgp findKeysForUserID:@"Name <email@example.com>"];
+```
+
+```swift
+let keyring = ObjectivePGP.defaultKeyring
+let keyring = Keyring()
+
+let allKeys = keyring.keys
+keyring.import(keys: [key])
+keyring.delete(keys: [key])
+
+keyring.import(keyIdentifier:"979E4B03DFFE30C6", fromPath:"/path/to/secring.gpg")
+if let key = keyring.findKey("979E4B03DFFE30C6") {
+ // key found in keyring
+}
+
+keyring.findKeys("Name <email@example.com>").forEach(key) {
+ // process key
+}
+```
+
+##### Export keys (private or public)
+
+```objective-c
+// Write keyring to file
+[[keyring export:error] writeToURL:[NSURL fileURLWithString:@"keyring.gpg"]];
+
+// Public keys data
+NSData *publicKeys = [keyring exportKeysOfType:PGPKeyTypePublic error:nil];
+```
+
+```swift
+// Write keyring to file
+try keyring.export().write(to: URL(fileURLWithPath: "keyring.gpg"))
+
+// Public keys (Data)
+let publicKeys = keyring.exportKeys(of: .public)
+```
+
+##### Sign & verify data (or file)
+
+Sign a data with a key:
+
+```objective-c
+NSData *signature = [ObjectivePGP sign:fileContent detached:YES usingKeys:@[key] passphraseForKey:nil error:nil];
+[ObjectivePGP verify:fileContent withSignature:signature usingKeys:@[key] passphraseForKey:nil error:nil];
+```
+
+```swift
+let signature = try ObjectivePGP.sign(encryptedBin, detached:true, using: [key1])
+try ObjectivePGP.verify(encryptedBin, withSignature: signature, using: [key1])
+```
+
+##### Encrypt & Decrypt
+
+```objective-c
+NSData *encrypted = [ObjectivePGP encrypt:fileContent addSignature:YES usingKeys:@[key] passphraseForKey:nil error:nil];
+[ObjectivePGP decrypt:encrypted andVerifySignature:YES usingKeys:@[key] passphraseForKey:nil error:nil];
+```
+
+```swift
+let encrypted = try ObjectivePGP.encrypt(fileContent), addSignature: true, using: [key1, key2])
+let decrypted = try ObjectivePGP.decrypt(encrypted, andVerifySignature: true, using: [key1])
+```
+
+##### Generate new key pair
+
+```objective-c
+PGPKeyGenerator *generator = [[PGPKeyGenerator alloc] init];
+PGPKey *key = [generator generateFor:@"Marcin <marcin@example.com>" passphrase:nil];
+NSData *publicKeyData = [key export:PGPKeyTypePublic error:nil];
+NSData *secretKeyData = [key export:PGPKeyTypeSecret error:nil];
+```
+
+```swift
+let key = KeyGenerator().generate(for: "marcin@example.com", passphrase: "password")
+let publicKey = try key.export(keyType: .public)
+let secretKey = try key.export(keyType: .secret)
+```
+
+#### ASCII Armor
+
+ASCII armor is a binary-to-textual encoding converter. ASCII armor involves encasing encrypted messaging in ASCII so that they can be sent in a standard messaging format such as email.
+
+Example:
+```
+-----BEGIN PGP PUBLIC KEY BLOCK-----
+Comment: For info see http://www.objectivepgp.org
+
+[...]
+-----END PGP PUBLIC KEY BLOCK-----
+```
+
+Class `PGPArmor` can be used to convert binary format to ASCII format
+
+```objective-c
+NSString *armoredKey = [PGPArmor armoredData:encrypted as:PGPArmorPublicKey];
+```
+
+```swift
+let armoredKey = Armor.armored(Data(), as: .publicKey)
+```
+
+When convert manually, it is important to use right `PGPArmorType` value that define the header. It may be a tricky part so here's the cheatsheet:
+
+| Type data | PGPArmorType | Example |
+| ---------- | --------------------- |-------- |
+| Encrypted | `PGPArmorMessage` | `Armor.armored(ObjectivePGP.encrypt(...), as: .message)` |
+| Decrypted | `PGPArmorMessage` | `Armor.armored(ObjectivePGP.decrypt(...), as: .message)` |
+| Pubic key | `PGPArmorTypePublic` | `Armor.armored(key.export(), as: .publicKey)` |
+| Secret key | `PGPArmorTypeSecret` | `Armor.armored(key.export(), as: .secretKey)` |
+
+For any result of encryption the type is `PGPArmorMessage`
+
+## Installation
+
+#### [CocoaPods](https://cocoapods.org/pods/ObjectivePGP)
+
+```ruby
+target 'TargetName' do
+ use_frameworks!
+ pod 'ObjectivePGP'
+end
+```
+
+#### ObjectivePGP.framework
+
+ObjectivePGP comes with the [Frameworks](./Frameworks) for the latest release.
+
+1. Download latest [ObjectivePGP.framework](https://github.com/krzyzanowskim/ObjectivePGP/releases) or build a framework with the [build-frameworks.sh](./build-frameworks.sh) script.
+1. Link framework with the target
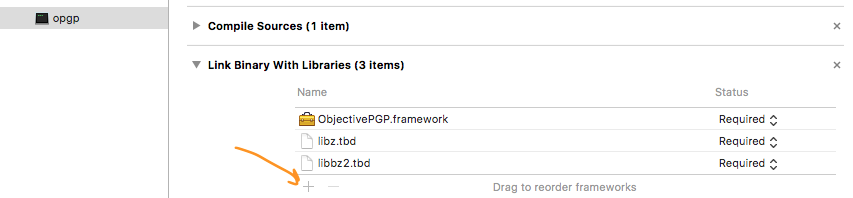
+ - Add `ObjectivePGP.framework` to "**Link Binary With Libraries**" list for the target.
+ 
+1. Link libraries and frameworks
+ 1. Add `Security.framework` to "**Link Binary With Libraries**" list for the target. These are system libraries.
+ 1. Add `libz` and `libbz2` to "**Link Binary With Libraries**" list for the target. These are system libraries.
+1. In the Build Phases tab, click the + button at the top and select “New Run Script Phase”. Enter the following code into the script text field:
+
+```sh
+bash "${BUILT_PRODUCTS_DIR}/${FRAMEWORKS_FOLDER_PATH}/ObjectivePGP.framework/strip-frameworks.sh"
+```
+
+(The last step, is required for working around an iOS App Store bug when archiving universal binaries.)
+
+## Changelog
+
+See [CHANGELOG](./CHANGELOG)
+
+Known limitations:
+
+- Elgamal cipher is not supported.
+- Cleartext signature.
+
+## The license
+
+The ObjectivePGP stays under a dual license:
+
+- Free for non-commercial use, covered by the standard 2-clause BSD license. That means you have to mention Marcin Krzyżanowski as the original author of this code and reproduce the [LICENSE](./LICENSE.txt) text inside your app.
+
+- Commercial-use license to use in commercial products. Please bear in mind that some free products remain commercial products. Please contact me via [email](http://www.krzyzanowskim.com) for details.
+
+Not sure what to choose? check this [thread](https://twitter.com/krzyzanowskim/status/868481597204508672)
+
+### Acknowledgment
+
+This product uses software developed by the [OpenSSL](http://www.openssl.org/) Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)
+
+### Author
+
+[Marcin Krzyżanowski](http://krzyzanowskim.com)
diff --git a/enzevalos_iphone.xcodeproj/project.pbxproj b/enzevalos_iphone.xcodeproj/project.pbxproj
index 0eccd46c82fafebd2bfd268094299ea4746bc577..825d3340a9b07e80204fc7a8b39c2a490f75d986 100644
--- a/enzevalos_iphone.xcodeproj/project.pbxproj
+++ b/enzevalos_iphone.xcodeproj/project.pbxproj
@@ -11,44 +11,27 @@
3E048C061FAC9ABD00948524 /* HockeySDK.swift in Sources */ = {isa = PBXBuildFile; fileRef = 3E048C041FAC9ABD00948524 /* HockeySDK.swift */; };
3E6B07DE2011246500E49609 /* invitationText.html in Resources */ = {isa = PBXBuildFile; fileRef = 3E6B07DD2011246500E49609 /* invitationText.html */; };
3E6B07DF2011246500E49609 /* invitationText.html in Resources */ = {isa = PBXBuildFile; fileRef = 3E6B07DD2011246500E49609 /* invitationText.html */; };
- 3E9708B31FAC95F5005825C9 /* PGPPartialKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F01F960B7C00D64416 /* PGPPartialKey.m */; };
3E9708B41FAC95F5005825C9 /* Mail.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47691A891ECB56D1004BCFC5 /* Mail.swift */; };
3E9708B51FAC95F5005825C9 /* Contact.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F39891E251787009260FB /* Contact.swift */; };
3E9708B61FAC95F5005825C9 /* Record.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F39851E1FA34E009260FB /* Record.swift */; };
- 3E9708B71FAC95F5005825C9 /* PGPPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AF1F960B7C00D64416 /* PGPPacket.m */; };
- 3E9708B81FAC95F5005825C9 /* PGPKeyID.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E71F960B7C00D64416 /* PGPKeyID.m */; };
- 3E9708B91FAC95F5005825C9 /* NSData+compression.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8FE1F960B7C00D64416 /* NSData+compression.m */; };
3E9708BA1FAC95F5005825C9 /* TextFormatter.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1C3270D1DB907D900CE2ED5 /* TextFormatter.swift */; };
- 3E9708BC1FAC95F5005825C9 /* PGPSymmetricallyEncryptedDataPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C81F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m */; };
3E9708BD1FAC95F5005825C9 /* ListViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = F12041FC1DA409A5002E4940 /* ListViewCell.swift */; };
- 3E9708BE1FAC95F5005825C9 /* PGPUser.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8FB1F960B7C00D64416 /* PGPUser.m */; };
- 3E9708BF1FAC95F5005825C9 /* PGPSecretKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BA1F960B7C00D64416 /* PGPSecretKeyPacket.m */; };
3E9708C01FAC95F5005825C9 /* FolderListCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1E2324D1F0FA41A00DC9D40 /* FolderListCell.swift */; };
3E9708C11FAC95F5005825C9 /* NSDateCompare.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB059B1D956957008659C1 /* NSDateCompare.swift */; };
- 3E9708C21FAC95F5005825C9 /* PGPCompressedPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A61F960B7C00D64416 /* PGPCompressedPacket.m */; };
- 3E9708C31FAC95F5005825C9 /* PGPRSA.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89E1F960B7C00D64416 /* PGPRSA.m */; };
3E9708C41FAC95F5005825C9 /* InboxCellDelegator.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05931D956931008659C1 /* InboxCellDelegator.swift */; };
3E9708C51FAC95F5005825C9 /* Badges.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8591F436A05007649A5 /* Badges.swift */; };
3E9708C61FAC95F5005825C9 /* BadgeCaseCollectionViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8601F436A11007649A5 /* BadgeCaseCollectionViewCell.swift */; };
3E9708C71FAC95F5005825C9 /* Mail_Address+CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F397F1E1E5347009260FB /* Mail_Address+CoreDataClass.swift */; };
3E9708C81FAC95F5005825C9 /* CollectionDataDelegate.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05811D95685B008659C1 /* CollectionDataDelegate.swift */; };
3E9708C91FAC95F5005825C9 /* DebugSettings.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47D1302A1F7CEE6D007B14DF /* DebugSettings.swift */; };
- 3E9708CA1FAC95F5005825C9 /* PGPS2K.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F81F960B7C00D64416 /* PGPS2K.m */; };
- 3E9708CB1FAC95F5005825C9 /* PGPPacketFactory.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8EE1F960B7C00D64416 /* PGPPacketFactory.m */; };
3E9708CD1FAC95F5005825C9 /* SendViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB057F1D956851008659C1 /* SendViewController.swift */; };
- 3E9708CE1FAC95F5005825C9 /* PGPModificationDetectionCodePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AA1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m */; };
3E9708CF1FAC95F5005825C9 /* EphemeralMail.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47691A8B1ECC3EC7004BCFC5 /* EphemeralMail.swift */; };
- 3E9708D01FAC95F5005825C9 /* PGPPKCSEme.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F41F960B7C00D64416 /* PGPPKCSEme.m */; };
3E9708D11FAC95F5005825C9 /* SubBadgeHeaderTableViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8621F436A11007649A5 /* SubBadgeHeaderTableViewCell.swift */; };
3E9708D21FAC95F5005825C9 /* InboxViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05971D956947008659C1 /* InboxViewController.swift */; };
- 3E9708D31FAC95F5005825C9 /* PGPPublicSubKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B71F960B7C00D64416 /* PGPPublicSubKeyPacket.m */; };
3E9708D41FAC95F5005825C9 /* IconsStyleKit.swift in Sources */ = {isa = PBXBuildFile; fileRef = F1984D711E1D327200804E1E /* IconsStyleKit.swift */; };
- 3E9708D51FAC95F5005825C9 /* PGPKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E31F960B7C00D64416 /* PGPKey.m */; };
3E9708D61FAC95F5005825C9 /* UserNameGamificationTableViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8641F436A11007649A5 /* UserNameGamificationTableViewCell.swift */; };
3E9708D71FAC95F5005825C9 /* CNContactExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398B1E2519C8009260FB /* CNContactExtension.swift */; };
- 3E9708D81FAC95F5005825C9 /* PGPPKCSEmsa.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F61F960B7C00D64416 /* PGPPKCSEmsa.m */; };
3E9708D91FAC95F5005825C9 /* QRScannerView.swift in Sources */ = {isa = PBXBuildFile; fileRef = F113C3841F30D06800E7F1D6 /* QRScannerView.swift */; };
- 3E9708DA1FAC95F5005825C9 /* PGPCryptoCFB.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8DB1F960B7C00D64416 /* PGPCryptoCFB.m */; };
3E9708DB1FAC95F5005825C9 /* ReplaceSegue.swift in Sources */ = {isa = PBXBuildFile; fileRef = F18B445F1E704C550080C041 /* ReplaceSegue.swift */; };
3E9708DD1FAC95F5005825C9 /* ArrowTableViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8611F436A11007649A5 /* ArrowTableViewCell.swift */; };
3E9708DE1FAC95F5005825C9 /* ContactViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = F1ACF21B1E0C1C6800C1B843 /* ContactViewController.swift */; };
@@ -56,43 +39,28 @@
3E9708E01FAC95F5005825C9 /* VENDataDelegate.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB057D1D956848008659C1 /* VENDataDelegate.swift */; };
3E9708E11FAC95F5005825C9 /* InviteFriendViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A86B1F436A1E007649A5 /* InviteFriendViewController.swift */; };
3E9708E21FAC95F5005825C9 /* UIViewResolver.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1E81B661DCA296200535F98 /* UIViewResolver.swift */; };
- 3E9708E31FAC95F5005825C9 /* PGPArmor.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D61F960B7C00D64416 /* PGPArmor.m */; };
3E9708E41FAC95F5005825C9 /* SwiftPGP.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00301F7B9565006CDD41 /* SwiftPGP.swift */; };
- 3E9708E51FAC95F5005825C9 /* PGPCryptoUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8981F960B7C00D64416 /* PGPCryptoUtils.m */; };
3E9708E61FAC95F5005825C9 /* QRCodeGenerator.swift in Sources */ = {isa = PBXBuildFile; fileRef = F14239C01F30A99C00998A83 /* QRCodeGenerator.swift */; };
- 3E9708E81FAC95F5005825C9 /* NSMutableData+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC9041F960B7C00D64416 /* NSMutableData+PGPUtils.m */; };
3E9708E91FAC95F5005825C9 /* EnzevalosContact+CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F39261E1277D2009260FB /* EnzevalosContact+CoreDataClass.swift */; };
3E9708EA1FAC95F5005825C9 /* CustomCells.swift in Sources */ = {isa = PBXBuildFile; fileRef = F1AF938E1E2D04BA00755128 /* CustomCells.swift */; };
3E9708EB1FAC95F5005825C9 /* GamificationStatusViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A86D1F436A1E007649A5 /* GamificationStatusViewController.swift */; };
- 3E9708EC1FAC95F5005825C9 /* ObjectivePGPObject.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A31F960B7C00D64416 /* ObjectivePGPObject.m */; };
- 3E9708ED1FAC95F5005825C9 /* PGPFingerprint.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8DE1F960B7C00D64416 /* PGPFingerprint.m */; };
- 3E9708EE1FAC95F5005825C9 /* PGPBigNum.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D91F960B7C00D64416 /* PGPBigNum.m */; };
3E9708EF1FAC95F5005825C9 /* FolderViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A10DE41F1EFAA2CE005E8189 /* FolderViewController.swift */; };
3E9708F01FAC95F5005825C9 /* Theme.swift in Sources */ = {isa = PBXBuildFile; fileRef = 476142071E07E52B00FD5E4F /* Theme.swift */; };
3E9708F11FAC95F5005825C9 /* LinearBadgeViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A86C1F436A1E007649A5 /* LinearBadgeViewController.swift */; };
3E9708F21FAC95F5005825C9 /* ContactCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05791D956829008659C1 /* ContactCell.swift */; };
- 3E9708F41FAC95F5005825C9 /* PGPSecretSubKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BC1F960B7C00D64416 /* PGPSecretSubKeyPacket.m */; };
- 3E9708F51FAC95F5005825C9 /* PGPUserIDPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D41F960B7C00D64416 /* PGPUserIDPacket.m */; };
3E9708F61FAC95F5005825C9 /* Folder+CoreDataProperties.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475DF4781F0D54C9009D807F /* Folder+CoreDataProperties.swift */; };
3E9708F71FAC95F5005825C9 /* PersistentMail +CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F39281E1277D2009260FB /* PersistentMail +CoreDataClass.swift */; };
- 3E9708F81FAC95F5005825C9 /* PGPTrustPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8CE1F960B7C00D64416 /* PGPTrustPacket.m */; };
3E9708F91FAC95F5005825C9 /* PersistentKey+CoreDataProperties.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00411F7BB6D6006CDD41 /* PersistentKey+CoreDataProperties.swift */; };
3E9708FA1FAC95F5005825C9 /* AnimatedSendIcon.swift in Sources */ = {isa = PBXBuildFile; fileRef = F119D28F1E364B59001D732A /* AnimatedSendIcon.swift */; };
3E9708FB1FAC95F5005825C9 /* ExportViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = 4707096C1F8F9F4900657F41 /* ExportViewController.swift */; };
3E9708FC1FAC95F5005825C9 /* RefreshControlExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = F120607F1DA540FE00F6EF37 /* RefreshControlExtension.swift */; };
- 3E9708FD1FAC95F5005825C9 /* PGPMPI.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8EC1F960B7C00D64416 /* PGPMPI.m */; };
3E9708FF1FAC95F5005825C9 /* Mail_Address+CoreDataProperties.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F39801E1E5347009260FB /* Mail_Address+CoreDataProperties.swift */; };
3E9709001FAC95F5005825C9 /* UserData.swift in Sources */ = {isa = PBXBuildFile; fileRef = 476373C11E09BA88004D5EFE /* UserData.swift */; };
- 3E9709011FAC95F5005825C9 /* PGPCryptoHash.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8961F960B7C00D64416 /* PGPCryptoHash.m */; };
- 3E9709021FAC95F5005825C9 /* PGPKeyMaterial.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89C1F960B7C00D64416 /* PGPKeyMaterial.m */; };
3E9709031FAC95F5005825C9 /* MessageBodyTableViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB059F1D95696C008659C1 /* MessageBodyTableViewCell.swift */; };
3E9709041FAC95F5005825C9 /* ReadVENDelegate.swift in Sources */ = {isa = PBXBuildFile; fileRef = F18B44611E73286C0080C041 /* ReadVENDelegate.swift */; };
- 3E9709051FAC95F5005825C9 /* PGPUserAttributePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D01F960B7C00D64416 /* PGPUserAttributePacket.m */; };
3E9709061FAC95F5005825C9 /* PersistentKey+CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00401F7BB6D6006CDD41 /* PersistentKey+CoreDataClass.swift */; };
- 3E9709071FAC95F5005825C9 /* PGPSignaturePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BF1F960B7C00D64416 /* PGPSignaturePacket.m */; };
3E9709081FAC95F5005825C9 /* KeyViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1D5076E1E80257A00B68B38 /* KeyViewController.swift */; };
3E9709091FAC95F5005825C9 /* ExportCells.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1A9DE721F864B0500B808AA /* ExportCells.swift */; };
- 3E97090A1FAC95F5005825C9 /* PGPSignatureSubpacketCreationTime.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C41F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m */; };
3E97090B1FAC95F5005825C9 /* CNMailAddressesExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398F1E252470009260FB /* CNMailAddressesExtension.swift */; };
3E97090C1FAC95F5005825C9 /* FolderListViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1E2324B1F0FA13F00DC9D40 /* FolderListViewController.swift */; };
3E97090D1FAC95F5005825C9 /* ViewControllerPannable.swift in Sources */ = {isa = PBXBuildFile; fileRef = F113C38A1F3344C200E7F1D6 /* ViewControllerPannable.swift */; };
@@ -106,32 +74,19 @@
3E9709151FAC95F5005825C9 /* FolderCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1ECE54A1EFBE7ED0009349F /* FolderCell.swift */; };
3E9709161FAC95F5005825C9 /* GamificationData.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A85B1F436A05007649A5 /* GamificationData.swift */; };
3E9709171FAC95F5005825C9 /* Folder+CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475DF4771F0D54C9009D807F /* Folder+CoreDataClass.swift */; };
- 3E9709181FAC95F5005825C9 /* PGPPublicKeyEncryptedSessionKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B21F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m */; };
3E97091A1FAC95F5005825C9 /* Cryptography.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00311F7B9565006CDD41 /* Cryptography.swift */; };
3E97091B1FAC95F5005825C9 /* MailHandler.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB057B1D956838008659C1 /* MailHandler.swift */; };
3E97091C1FAC95F5005825C9 /* AddressHandler.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05871D956879008659C1 /* AddressHandler.swift */; };
3E97091D1FAC95F5005825C9 /* DataHandler.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F396F1E14F75C009260FB /* DataHandler.swift */; };
- 3E97091E1FAC95F5005825C9 /* PGPSignatureSubpacketHeader.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C61F960B7C00D64416 /* PGPSignatureSubpacketHeader.m */; };
- 3E97091F1FAC95F5005825C9 /* NSData+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC9001F960B7C00D64416 /* NSData+PGPUtils.m */; };
3E9709201FAC95F5005825C9 /* ReadViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB058F1D956923008659C1 /* ReadViewController.swift */; };
- 3E9709211FAC95F5005825C9 /* PGPSignatureSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C21F960B7C00D64416 /* PGPSignatureSubpacket.m */; };
3E9709221FAC95F5005825C9 /* InitViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = A11E733B1E019AE3006574DD /* InitViewController.swift */; };
3E9709231FAC95F5005825C9 /* MailAddress.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398D1E251B8D009260FB /* MailAddress.swift */; };
3E9709241FAC95F5005825C9 /* MailHandlerDelegator.swift in Sources */ = {isa = PBXBuildFile; fileRef = F12060811DA552FC00F6EF37 /* MailHandlerDelegator.swift */; };
- 3E9709251FAC95F5005825C9 /* PGPFoundation.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E01F960B7C00D64416 /* PGPFoundation.m */; };
- 3E9709261FAC95F5005825C9 /* PGPLiteralPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A81F960B7C00D64416 /* PGPLiteralPacket.m */; };
- 3E9709271FAC95F5005825C9 /* PGPPublicKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B51F960B7C00D64416 /* PGPPublicKeyPacket.m */; };
- 3E9709281FAC95F5005825C9 /* PGPKeyGenerator.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E51F960B7C00D64416 /* PGPKeyGenerator.m */; };
- 3E9709291FAC95F5005825C9 /* PGPDSA.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89A1F960B7C00D64416 /* PGPDSA.m */; };
3E97092A1FAC95F5005825C9 /* LabelStyleKit.swift in Sources */ = {isa = PBXBuildFile; fileRef = F1984D731E1E92B300804E1E /* LabelStyleKit.swift */; };
- 3E97092B1FAC95F5005825C9 /* PGPPartialSubKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F21F960B7C00D64416 /* PGPPartialSubKey.m */; };
3E97092C1FAC95F5005825C9 /* SubBadgeTableViewCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A8631F436A11007649A5 /* SubBadgeTableViewCell.swift */; };
3E97092D1FAC95F5005825C9 /* FrequentCell.swift in Sources */ = {isa = PBXBuildFile; fileRef = A1EB05851D956872008659C1 /* FrequentCell.swift */; };
3E97092E1FAC95F5005825C9 /* ListViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = F12041FA1DA3FBF7002E4940 /* ListViewController.swift */; };
3E97092F1FAC95F5005825C9 /* FlipTransition.swift in Sources */ = {isa = PBXBuildFile; fileRef = F18B445D1E7044B70080C041 /* FlipTransition.swift */; };
- 3E9709301FAC95F5005825C9 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8CA1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m */; };
- 3E9709311FAC95F5005825C9 /* PGPUserAttributeSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D21F960B7C00D64416 /* PGPUserAttributeSubpacket.m */; };
- 3E9709321FAC95F5005825C9 /* PGPOnePassSignaturePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AC1F960B7C00D64416 /* PGPOnePassSignaturePacket.m */; };
3E9709331FAC95F5005825C9 /* EnzevalosContact+CoreDataProperties.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F397A1E1D0B0B009260FB /* EnzevalosContact+CoreDataProperties.swift */; };
3E9709341FAC95F5005825C9 /* BadgeCase.swift in Sources */ = {isa = PBXBuildFile; fileRef = 8428A86A1F436A1E007649A5 /* BadgeCase.swift */; };
3E9709371FAC95F5005825C9 /* CoreData.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = 472F396D1E14F384009260FB /* CoreData.framework */; };
@@ -146,7 +101,6 @@
3E9709421FAC95F5005825C9 /* alice_enzevalos_public.asc in Resources */ = {isa = PBXBuildFile; fileRef = 479BBDD91EFEA17900A2107C /* alice_enzevalos_public.asc */; };
3E9709431FAC95F5005825C9 /* providers.json in Resources */ = {isa = PBXBuildFile; fileRef = A16BA2111E0439B6005E29E3 /* providers.json */; };
3E9709441FAC95F5005825C9 /* idsolutions-private.gpg in Resources */ = {isa = PBXBuildFile; fileRef = F189C17D1ED59FEF00BAE9B3 /* idsolutions-private.gpg */; };
- 3E9709451FAC95F5005825C9 /* Info.plist in Resources */ = {isa = PBXBuildFile; fileRef = 471BC89F1F960B7C00D64416 /* Info.plist */; };
3E9709461FAC95F5005825C9 /* nchr-public.gpg in Resources */ = {isa = PBXBuildFile; fileRef = F14D18991ED880680080515D /* nchr-public.gpg */; };
3E9709471FAC95F5005825C9 /* nchr-private.gpg in Resources */ = {isa = PBXBuildFile; fileRef = F14D18981ED880680080515D /* nchr-private.gpg */; };
3E9709481FAC95F5005825C9 /* idsolutions-public.gpg in Resources */ = {isa = PBXBuildFile; fileRef = F189C17E1ED59FEF00BAE9B3 /* idsolutions-public.gpg */; };
@@ -184,52 +138,6 @@
45262931B4C72A96C686C533 /* Pods_enzevalos_iphoneTests.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = C9B9CE43043CF806E1C02FCA /* Pods_enzevalos_iphoneTests.framework */; };
4707096D1F8F9F4900657F41 /* ExportViewController.swift in Sources */ = {isa = PBXBuildFile; fileRef = 4707096C1F8F9F4900657F41 /* ExportViewController.swift */; };
4715F637202A0248001BFFD0 /* CoreDataTests.swift in Sources */ = {isa = PBXBuildFile; fileRef = 4715F636202A0248001BFFD0 /* CoreDataTests.swift */; };
- 471BC9051F960B7C00D64416 /* PGPCryptoHash.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8961F960B7C00D64416 /* PGPCryptoHash.m */; };
- 471BC9061F960B7C00D64416 /* PGPCryptoUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8981F960B7C00D64416 /* PGPCryptoUtils.m */; };
- 471BC9071F960B7C00D64416 /* PGPDSA.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89A1F960B7C00D64416 /* PGPDSA.m */; };
- 471BC9081F960B7C00D64416 /* PGPKeyMaterial.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89C1F960B7C00D64416 /* PGPKeyMaterial.m */; };
- 471BC9091F960B7C00D64416 /* PGPRSA.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC89E1F960B7C00D64416 /* PGPRSA.m */; };
- 471BC90A1F960B7C00D64416 /* Info.plist in Resources */ = {isa = PBXBuildFile; fileRef = 471BC89F1F960B7C00D64416 /* Info.plist */; };
- 471BC90B1F960B7C00D64416 /* ObjectivePGPObject.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A31F960B7C00D64416 /* ObjectivePGPObject.m */; };
- 471BC90C1F960B7C00D64416 /* PGPCompressedPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A61F960B7C00D64416 /* PGPCompressedPacket.m */; };
- 471BC90D1F960B7C00D64416 /* PGPLiteralPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8A81F960B7C00D64416 /* PGPLiteralPacket.m */; };
- 471BC90E1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AA1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m */; };
- 471BC90F1F960B7C00D64416 /* PGPOnePassSignaturePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AC1F960B7C00D64416 /* PGPOnePassSignaturePacket.m */; };
- 471BC9101F960B7C00D64416 /* PGPPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8AF1F960B7C00D64416 /* PGPPacket.m */; };
- 471BC9111F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B21F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m */; };
- 471BC9121F960B7C00D64416 /* PGPPublicKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B51F960B7C00D64416 /* PGPPublicKeyPacket.m */; };
- 471BC9131F960B7C00D64416 /* PGPPublicSubKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8B71F960B7C00D64416 /* PGPPublicSubKeyPacket.m */; };
- 471BC9141F960B7C00D64416 /* PGPSecretKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BA1F960B7C00D64416 /* PGPSecretKeyPacket.m */; };
- 471BC9151F960B7C00D64416 /* PGPSecretSubKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BC1F960B7C00D64416 /* PGPSecretSubKeyPacket.m */; };
- 471BC9161F960B7C00D64416 /* PGPSignaturePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8BF1F960B7C00D64416 /* PGPSignaturePacket.m */; };
- 471BC9171F960B7C00D64416 /* PGPSignatureSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C21F960B7C00D64416 /* PGPSignatureSubpacket.m */; };
- 471BC9181F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C41F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m */; };
- 471BC9191F960B7C00D64416 /* PGPSignatureSubpacketHeader.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C61F960B7C00D64416 /* PGPSignatureSubpacketHeader.m */; };
- 471BC91A1F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8C81F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m */; };
- 471BC91B1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8CA1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m */; };
- 471BC91D1F960B7C00D64416 /* PGPTrustPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8CE1F960B7C00D64416 /* PGPTrustPacket.m */; };
- 471BC91E1F960B7C00D64416 /* PGPUserAttributePacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D01F960B7C00D64416 /* PGPUserAttributePacket.m */; };
- 471BC91F1F960B7C00D64416 /* PGPUserAttributeSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D21F960B7C00D64416 /* PGPUserAttributeSubpacket.m */; };
- 471BC9201F960B7C00D64416 /* PGPUserIDPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D41F960B7C00D64416 /* PGPUserIDPacket.m */; };
- 471BC9211F960B7C00D64416 /* PGPArmor.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D61F960B7C00D64416 /* PGPArmor.m */; };
- 471BC9221F960B7C00D64416 /* PGPBigNum.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8D91F960B7C00D64416 /* PGPBigNum.m */; };
- 471BC9231F960B7C00D64416 /* PGPCryptoCFB.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8DB1F960B7C00D64416 /* PGPCryptoCFB.m */; };
- 471BC9241F960B7C00D64416 /* PGPFingerprint.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8DE1F960B7C00D64416 /* PGPFingerprint.m */; };
- 471BC9251F960B7C00D64416 /* PGPFoundation.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E01F960B7C00D64416 /* PGPFoundation.m */; };
- 471BC9261F960B7C00D64416 /* PGPKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E31F960B7C00D64416 /* PGPKey.m */; };
- 471BC9271F960B7C00D64416 /* PGPKeyGenerator.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E51F960B7C00D64416 /* PGPKeyGenerator.m */; };
- 471BC9281F960B7C00D64416 /* PGPKeyID.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8E71F960B7C00D64416 /* PGPKeyID.m */; };
- 471BC9291F960B7C00D64416 /* PGPMPI.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8EC1F960B7C00D64416 /* PGPMPI.m */; };
- 471BC92A1F960B7C00D64416 /* PGPPacketFactory.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8EE1F960B7C00D64416 /* PGPPacketFactory.m */; };
- 471BC92B1F960B7C00D64416 /* PGPPartialKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F01F960B7C00D64416 /* PGPPartialKey.m */; };
- 471BC92C1F960B7C00D64416 /* PGPPartialSubKey.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F21F960B7C00D64416 /* PGPPartialSubKey.m */; };
- 471BC92D1F960B7C00D64416 /* PGPPKCSEme.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F41F960B7C00D64416 /* PGPPKCSEme.m */; };
- 471BC92E1F960B7C00D64416 /* PGPPKCSEmsa.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F61F960B7C00D64416 /* PGPPKCSEmsa.m */; };
- 471BC92F1F960B7C00D64416 /* PGPS2K.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8F81F960B7C00D64416 /* PGPS2K.m */; };
- 471BC9301F960B7C00D64416 /* PGPUser.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8FB1F960B7C00D64416 /* PGPUser.m */; };
- 471BC9311F960B7C00D64416 /* NSData+compression.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC8FE1F960B7C00D64416 /* NSData+compression.m */; };
- 471BC9321F960B7C00D64416 /* NSData+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC9001F960B7C00D64416 /* NSData+PGPUtils.m */; };
- 471BC9341F960B7C00D64416 /* NSMutableData+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 471BC9041F960B7C00D64416 /* NSMutableData+PGPUtils.m */; };
472276BC1FCD46B200ADA507 /* LoggingEventType.swift in Sources */ = {isa = PBXBuildFile; fileRef = A18E7D761FBDE5D9002F7CC9 /* LoggingEventType.swift */; };
472276BE1FCD484C00ADA507 /* StringExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = A114E4311FACB23000E40243 /* StringExtension.swift */; };
4725C4F71EDDADA10068235E /* bob-public.gpg in Resources */ = {isa = PBXBuildFile; fileRef = 4725C4F51EDDADA10068235E /* bob-public.gpg */; };
@@ -246,20 +154,6 @@
472F398C1E2519C8009260FB /* CNContactExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398B1E2519C8009260FB /* CNContactExtension.swift */; };
472F398E1E251B8D009260FB /* MailAddress.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398D1E251B8D009260FB /* MailAddress.swift */; };
472F39901E252470009260FB /* CNMailAddressesExtension.swift in Sources */ = {isa = PBXBuildFile; fileRef = 472F398F1E252470009260FB /* CNMailAddressesExtension.swift */; };
- 473AC39320054D07006EB8A6 /* PGPUserAttributeImageSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39120054D06006EB8A6 /* PGPUserAttributeImageSubpacket.m */; };
- 473AC39420054D07006EB8A6 /* PGPUserAttributeImageSubpacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39120054D06006EB8A6 /* PGPUserAttributeImageSubpacket.m */; };
- 473AC39720054D29006EB8A6 /* NSArray+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39620054D29006EB8A6 /* NSArray+PGPUtils.m */; };
- 473AC39820054D29006EB8A6 /* NSArray+PGPUtils.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39620054D29006EB8A6 /* NSArray+PGPUtils.m */; };
- 473AC39C20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39A20054D7C006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m */; };
- 473AC39D20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39A20054D7C006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m */; };
- 473AC3A120054DDA006EB8A6 /* PGPPacketHeader.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39F20054DD9006EB8A6 /* PGPPacketHeader.m */; };
- 473AC3A220054DDA006EB8A6 /* PGPPacketHeader.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC39F20054DD9006EB8A6 /* PGPPacketHeader.m */; };
- 473AC3A520054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3A420054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m */; };
- 473AC3A620054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3A420054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m */; };
- 473AC3AA20054E25006EB8A6 /* twofish.c in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3A820054E25006EB8A6 /* twofish.c */; };
- 473AC3AB20054E25006EB8A6 /* twofish.c in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3A820054E25006EB8A6 /* twofish.c */; };
- 473AC3AE20054EAA006EB8A6 /* PGPKeyring.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3AC20054EAA006EB8A6 /* PGPKeyring.m */; };
- 473AC3AF20054EAA006EB8A6 /* PGPKeyring.m in Sources */ = {isa = PBXBuildFile; fileRef = 473AC3AC20054EAA006EB8A6 /* PGPKeyring.m */; };
4756DE0E20402F8E00452288 /* invitationTextCensor.html in Resources */ = {isa = PBXBuildFile; fileRef = 4756DE0D20402F8E00452288 /* invitationTextCensor.html */; };
475B00331F7B9565006CDD41 /* SwiftPGP.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00301F7B9565006CDD41 /* SwiftPGP.swift */; };
475B00341F7B9565006CDD41 /* Cryptography.swift in Sources */ = {isa = PBXBuildFile; fileRef = 475B00311F7B9565006CDD41 /* Cryptography.swift */; };
@@ -283,9 +177,14 @@
47CD5AAA2012368D00E771A1 /* logging_pk.asc in Resources */ = {isa = PBXBuildFile; fileRef = 47CD5AA82012368D00E771A1 /* logging_pk.asc */; };
47CD5AAB2012368D00E771A1 /* bitcoinde.asc in Resources */ = {isa = PBXBuildFile; fileRef = 47CD5AA92012368D00E771A1 /* bitcoinde.asc */; };
47CD5AAD2012369400E771A1 /* support_pk.asc in Resources */ = {isa = PBXBuildFile; fileRef = 47CD5AAC2012369300E771A1 /* support_pk.asc */; };
+ 47CEF4EB2052C3C800887CDB /* ObjectivePGP.framework in CopyFiles */ = {isa = PBXBuildFile; fileRef = 47CEF4EA2052C3C700887CDB /* ObjectivePGP.framework */; settings = {ATTRIBUTES = (CodeSignOnCopy, RemoveHeadersOnCopy, ); }; };
+ 47CEF4ED2052C3E700887CDB /* ObjectivePGP.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = 47CEF4EC2052C3E600887CDB /* ObjectivePGP.framework */; };
47D1302B1F7CEE6D007B14DF /* DebugSettings.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47D1302A1F7CEE6D007B14DF /* DebugSettings.swift */; };
47F79240203492E3005E7DB6 /* KeyRecord+CoreDataClass.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47F7923E203492E3005E7DB6 /* KeyRecord+CoreDataClass.swift */; };
47F79241203492E3005E7DB6 /* KeyRecord+CoreDataProperties.swift in Sources */ = {isa = PBXBuildFile; fileRef = 47F7923F203492E3005E7DB6 /* KeyRecord+CoreDataProperties.swift */; };
+ 47F867E02052B47C00AA832F /* Security.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = 47F867DF2052B47C00AA832F /* Security.framework */; };
+ 47F867E22052B48E00AA832F /* libz.tbd in Frameworks */ = {isa = PBXBuildFile; fileRef = 47F867E12052B48E00AA832F /* libz.tbd */; };
+ 47F867E42052B49800AA832F /* libbz2.tbd in Frameworks */ = {isa = PBXBuildFile; fileRef = 47F867E32052B49800AA832F /* libbz2.tbd */; };
5DC190F2042BE7D956F796BE /* Pods_enzevalos_iphone_AdHoc.framework in Frameworks */ = {isa = PBXBuildFile; fileRef = C1F4458FC892EBE555836F55 /* Pods_enzevalos_iphone_AdHoc.framework */; };
8428A8531F4369C0007649A5 /* Gamification.storyboard in Resources */ = {isa = PBXBuildFile; fileRef = 8428A8521F4369C0007649A5 /* Gamification.storyboard */; };
8428A8551F4369CF007649A5 /* GamificationElements.xcassets in Resources */ = {isa = PBXBuildFile; fileRef = 8428A8541F4369CF007649A5 /* GamificationElements.xcassets */; };
@@ -399,6 +298,19 @@
};
/* End PBXContainerItemProxy section */
+/* Begin PBXCopyFilesBuildPhase section */
+ 47F867DB2052B33C00AA832F /* CopyFiles */ = {
+ isa = PBXCopyFilesBuildPhase;
+ buildActionMask = 2147483647;
+ dstPath = "";
+ dstSubfolderSpec = 10;
+ files = (
+ 47CEF4EB2052C3C800887CDB /* ObjectivePGP.framework in CopyFiles */,
+ );
+ runOnlyForDeploymentPostprocessing = 0;
+ };
+/* End PBXCopyFilesBuildPhase section */
+
/* Begin PBXFileReference section */
1D4A9E60565DECF52C011BC0 /* Pods-enzevalos_iphone-AdHoc.release.xcconfig */ = {isa = PBXFileReference; includeInIndex = 1; lastKnownFileType = text.xcconfig; name = "Pods-enzevalos_iphone-AdHoc.release.xcconfig"; path = "../enzevalos_iphone_workspace/Pods/Target Support Files/Pods-enzevalos_iphone-AdHoc/Pods-enzevalos_iphone-AdHoc.release.xcconfig"; sourceTree = "<group>"; };
3E048C041FAC9ABD00948524 /* HockeySDK.swift */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.swift; path = HockeySDK.swift; sourceTree = "<group>"; };
@@ -417,111 +329,6 @@
411EB2B85F99B48FFD36F966 /* Pods-enzevalos_iphoneTests.debug.xcconfig */ = {isa = PBXFileReference; includeInIndex = 1; lastKnownFileType = text.xcconfig; name = "Pods-enzevalos_iphoneTests.debug.xcconfig"; path = "../workspace/Pods/Target Support Files/Pods-enzevalos_iphoneTests/Pods-enzevalos_iphoneTests.debug.xcconfig"; sourceTree = "<group>"; };
4707096C1F8F9F4900657F41 /* ExportViewController.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = ExportViewController.swift; sourceTree = "<group>"; };
4715F636202A0248001BFFD0 /* CoreDataTests.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = CoreDataTests.swift; sourceTree = "<group>"; };
- 471BC8951F960B7C00D64416 /* PGPCryptoHash.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPCryptoHash.h; sourceTree = "<group>"; };
- 471BC8961F960B7C00D64416 /* PGPCryptoHash.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPCryptoHash.m; sourceTree = "<group>"; };
- 471BC8971F960B7C00D64416 /* PGPCryptoUtils.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPCryptoUtils.h; sourceTree = "<group>"; };
- 471BC8981F960B7C00D64416 /* PGPCryptoUtils.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPCryptoUtils.m; sourceTree = "<group>"; };
- 471BC8991F960B7C00D64416 /* PGPDSA.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPDSA.h; sourceTree = "<group>"; };
- 471BC89A1F960B7C00D64416 /* PGPDSA.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPDSA.m; sourceTree = "<group>"; };
- 471BC89B1F960B7C00D64416 /* PGPKeyMaterial.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPKeyMaterial.h; sourceTree = "<group>"; };
- 471BC89C1F960B7C00D64416 /* PGPKeyMaterial.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPKeyMaterial.m; sourceTree = "<group>"; };
- 471BC89D1F960B7C00D64416 /* PGPRSA.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPRSA.h; sourceTree = "<group>"; };
- 471BC89E1F960B7C00D64416 /* PGPRSA.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPRSA.m; sourceTree = "<group>"; };
- 471BC89F1F960B7C00D64416 /* Info.plist */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text.plist.xml; path = Info.plist; sourceTree = "<group>"; };
- 471BC8A01F960B7C00D64416 /* ObjectivePGP-Prefix.pch */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "ObjectivePGP-Prefix.pch"; sourceTree = "<group>"; };
- 471BC8A11F960B7C00D64416 /* ObjectivePGP.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = ObjectivePGP.h; sourceTree = "<group>"; };
- 471BC8A21F960B7C00D64416 /* ObjectivePGPObject.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = ObjectivePGPObject.h; sourceTree = "<group>"; };
- 471BC8A31F960B7C00D64416 /* ObjectivePGPObject.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = ObjectivePGPObject.m; sourceTree = "<group>"; };
- 471BC8A51F960B7C00D64416 /* PGPCompressedPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPCompressedPacket.h; sourceTree = "<group>"; };
- 471BC8A61F960B7C00D64416 /* PGPCompressedPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPCompressedPacket.m; sourceTree = "<group>"; };
- 471BC8A71F960B7C00D64416 /* PGPLiteralPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPLiteralPacket.h; sourceTree = "<group>"; };
- 471BC8A81F960B7C00D64416 /* PGPLiteralPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPLiteralPacket.m; sourceTree = "<group>"; };
- 471BC8A91F960B7C00D64416 /* PGPModificationDetectionCodePacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPModificationDetectionCodePacket.h; sourceTree = "<group>"; };
- 471BC8AA1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPModificationDetectionCodePacket.m; sourceTree = "<group>"; };
- 471BC8AB1F960B7C00D64416 /* PGPOnePassSignaturePacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPOnePassSignaturePacket.h; sourceTree = "<group>"; };
- 471BC8AC1F960B7C00D64416 /* PGPOnePassSignaturePacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPOnePassSignaturePacket.m; sourceTree = "<group>"; };
- 471BC8AD1F960B7C00D64416 /* PGPPacket+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPPacket+Private.h"; sourceTree = "<group>"; };
- 471BC8AE1F960B7C00D64416 /* PGPPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPacket.h; sourceTree = "<group>"; };
- 471BC8AF1F960B7C00D64416 /* PGPPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPacket.m; sourceTree = "<group>"; };
- 471BC8B11F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPublicKeyEncryptedSessionKeyPacket.h; sourceTree = "<group>"; };
- 471BC8B21F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPublicKeyEncryptedSessionKeyPacket.m; sourceTree = "<group>"; };
- 471BC8B31F960B7C00D64416 /* PGPPublicKeyPacket+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPPublicKeyPacket+Private.h"; sourceTree = "<group>"; };
- 471BC8B41F960B7C00D64416 /* PGPPublicKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPublicKeyPacket.h; sourceTree = "<group>"; };
- 471BC8B51F960B7C00D64416 /* PGPPublicKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPublicKeyPacket.m; sourceTree = "<group>"; };
- 471BC8B61F960B7C00D64416 /* PGPPublicSubKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPublicSubKeyPacket.h; sourceTree = "<group>"; };
- 471BC8B71F960B7C00D64416 /* PGPPublicSubKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPublicSubKeyPacket.m; sourceTree = "<group>"; };
- 471BC8B81F960B7C00D64416 /* PGPSecretKeyPacket+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPSecretKeyPacket+Private.h"; sourceTree = "<group>"; };
- 471BC8B91F960B7C00D64416 /* PGPSecretKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSecretKeyPacket.h; sourceTree = "<group>"; };
- 471BC8BA1F960B7C00D64416 /* PGPSecretKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSecretKeyPacket.m; sourceTree = "<group>"; };
- 471BC8BB1F960B7C00D64416 /* PGPSecretSubKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSecretSubKeyPacket.h; sourceTree = "<group>"; };
- 471BC8BC1F960B7C00D64416 /* PGPSecretSubKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSecretSubKeyPacket.m; sourceTree = "<group>"; };
- 471BC8BD1F960B7C00D64416 /* PGPSignaturePacket+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPSignaturePacket+Private.h"; sourceTree = "<group>"; };
- 471BC8BE1F960B7C00D64416 /* PGPSignaturePacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSignaturePacket.h; sourceTree = "<group>"; };
- 471BC8BF1F960B7C00D64416 /* PGPSignaturePacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSignaturePacket.m; sourceTree = "<group>"; };
- 471BC8C01F960B7C00D64416 /* PGPSignatureSubpacket+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPSignatureSubpacket+Private.h"; sourceTree = "<group>"; };
- 471BC8C11F960B7C00D64416 /* PGPSignatureSubpacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSignatureSubpacket.h; sourceTree = "<group>"; };
- 471BC8C21F960B7C00D64416 /* PGPSignatureSubpacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSignatureSubpacket.m; sourceTree = "<group>"; };
- 471BC8C31F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSignatureSubpacketCreationTime.h; sourceTree = "<group>"; };
- 471BC8C41F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSignatureSubpacketCreationTime.m; sourceTree = "<group>"; };
- 471BC8C51F960B7C00D64416 /* PGPSignatureSubpacketHeader.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSignatureSubpacketHeader.h; sourceTree = "<group>"; };
- 471BC8C61F960B7C00D64416 /* PGPSignatureSubpacketHeader.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSignatureSubpacketHeader.m; sourceTree = "<group>"; };
- 471BC8C71F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSymmetricallyEncryptedDataPacket.h; sourceTree = "<group>"; };
- 471BC8C81F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSymmetricallyEncryptedDataPacket.m; sourceTree = "<group>"; };
- 471BC8C91F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h; sourceTree = "<group>"; };
- 471BC8CA1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m; sourceTree = "<group>"; };
- 471BC8CD1F960B7C00D64416 /* PGPTrustPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPTrustPacket.h; sourceTree = "<group>"; };
- 471BC8CE1F960B7C00D64416 /* PGPTrustPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPTrustPacket.m; sourceTree = "<group>"; };
- 471BC8CF1F960B7C00D64416 /* PGPUserAttributePacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPUserAttributePacket.h; sourceTree = "<group>"; };
- 471BC8D01F960B7C00D64416 /* PGPUserAttributePacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPUserAttributePacket.m; sourceTree = "<group>"; };
- 471BC8D11F960B7C00D64416 /* PGPUserAttributeSubpacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPUserAttributeSubpacket.h; sourceTree = "<group>"; };
- 471BC8D21F960B7C00D64416 /* PGPUserAttributeSubpacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPUserAttributeSubpacket.m; sourceTree = "<group>"; };
- 471BC8D31F960B7C00D64416 /* PGPUserIDPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPUserIDPacket.h; sourceTree = "<group>"; };
- 471BC8D41F960B7C00D64416 /* PGPUserIDPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPUserIDPacket.m; sourceTree = "<group>"; };
- 471BC8D51F960B7C00D64416 /* PGPArmor.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPArmor.h; sourceTree = "<group>"; };
- 471BC8D61F960B7C00D64416 /* PGPArmor.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPArmor.m; sourceTree = "<group>"; };
- 471BC8D71F960B7C00D64416 /* PGPBigNum+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPBigNum+Private.h"; sourceTree = "<group>"; };
- 471BC8D81F960B7C00D64416 /* PGPBigNum.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPBigNum.h; sourceTree = "<group>"; };
- 471BC8D91F960B7C00D64416 /* PGPBigNum.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPBigNum.m; sourceTree = "<group>"; };
- 471BC8DA1F960B7C00D64416 /* PGPCryptoCFB.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPCryptoCFB.h; sourceTree = "<group>"; };
- 471BC8DB1F960B7C00D64416 /* PGPCryptoCFB.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPCryptoCFB.m; sourceTree = "<group>"; };
- 471BC8DC1F960B7C00D64416 /* PGPExportableProtocol.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPExportableProtocol.h; sourceTree = "<group>"; };
- 471BC8DD1F960B7C00D64416 /* PGPFingerprint.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPFingerprint.h; sourceTree = "<group>"; };
- 471BC8DE1F960B7C00D64416 /* PGPFingerprint.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPFingerprint.m; sourceTree = "<group>"; };
- 471BC8DF1F960B7C00D64416 /* PGPFoundation.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPFoundation.h; sourceTree = "<group>"; };
- 471BC8E01F960B7C00D64416 /* PGPFoundation.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPFoundation.m; sourceTree = "<group>"; };
- 471BC8E11F960B7C00D64416 /* PGPKey+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPKey+Private.h"; sourceTree = "<group>"; };
- 471BC8E21F960B7C00D64416 /* PGPKey.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPKey.h; sourceTree = "<group>"; };
- 471BC8E31F960B7C00D64416 /* PGPKey.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPKey.m; sourceTree = "<group>"; };
- 471BC8E41F960B7C00D64416 /* PGPKeyGenerator.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPKeyGenerator.h; sourceTree = "<group>"; };
- 471BC8E51F960B7C00D64416 /* PGPKeyGenerator.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPKeyGenerator.m; sourceTree = "<group>"; };
- 471BC8E61F960B7C00D64416 /* PGPKeyID.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPKeyID.h; sourceTree = "<group>"; };
- 471BC8E71F960B7C00D64416 /* PGPKeyID.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPKeyID.m; sourceTree = "<group>"; };
- 471BC8E81F960B7C00D64416 /* PGPLogging.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPLogging.h; sourceTree = "<group>"; };
- 471BC8E91F960B7C00D64416 /* PGPMacros+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPMacros+Private.h"; sourceTree = "<group>"; };
- 471BC8EA1F960B7C00D64416 /* PGPMacros.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPMacros.h; sourceTree = "<group>"; };
- 471BC8EB1F960B7C00D64416 /* PGPMPI.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPMPI.h; sourceTree = "<group>"; };
- 471BC8EC1F960B7C00D64416 /* PGPMPI.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPMPI.m; sourceTree = "<group>"; };
- 471BC8ED1F960B7C00D64416 /* PGPPacketFactory.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPacketFactory.h; sourceTree = "<group>"; };
- 471BC8EE1F960B7C00D64416 /* PGPPacketFactory.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPacketFactory.m; sourceTree = "<group>"; };
- 471BC8EF1F960B7C00D64416 /* PGPPartialKey.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPartialKey.h; sourceTree = "<group>"; };
- 471BC8F01F960B7C00D64416 /* PGPPartialKey.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPartialKey.m; sourceTree = "<group>"; };
- 471BC8F11F960B7C00D64416 /* PGPPartialSubKey.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPartialSubKey.h; sourceTree = "<group>"; };
- 471BC8F21F960B7C00D64416 /* PGPPartialSubKey.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPartialSubKey.m; sourceTree = "<group>"; };
- 471BC8F31F960B7C00D64416 /* PGPPKCSEme.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPKCSEme.h; sourceTree = "<group>"; };
- 471BC8F41F960B7C00D64416 /* PGPPKCSEme.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPKCSEme.m; sourceTree = "<group>"; };
- 471BC8F51F960B7C00D64416 /* PGPPKCSEmsa.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPKCSEmsa.h; sourceTree = "<group>"; };
- 471BC8F61F960B7C00D64416 /* PGPPKCSEmsa.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPKCSEmsa.m; sourceTree = "<group>"; };
- 471BC8F71F960B7C00D64416 /* PGPS2K.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPS2K.h; sourceTree = "<group>"; };
- 471BC8F81F960B7C00D64416 /* PGPS2K.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPS2K.m; sourceTree = "<group>"; };
- 471BC8F91F960B7C00D64416 /* PGPTypes.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPTypes.h; sourceTree = "<group>"; };
- 471BC8FA1F960B7C00D64416 /* PGPUser.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPUser.h; sourceTree = "<group>"; };
- 471BC8FB1F960B7C00D64416 /* PGPUser.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPUser.m; sourceTree = "<group>"; };
- 471BC8FD1F960B7C00D64416 /* NSData+compression.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSData+compression.h"; sourceTree = "<group>"; };
- 471BC8FE1F960B7C00D64416 /* NSData+compression.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSData+compression.m"; sourceTree = "<group>"; };
- 471BC8FF1F960B7C00D64416 /* NSData+PGPUtils.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSData+PGPUtils.h"; sourceTree = "<group>"; };
- 471BC9001F960B7C00D64416 /* NSData+PGPUtils.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSData+PGPUtils.m"; sourceTree = "<group>"; };
- 471BC9031F960B7C00D64416 /* NSMutableData+PGPUtils.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSMutableData+PGPUtils.h"; sourceTree = "<group>"; };
- 471BC9041F960B7C00D64416 /* NSMutableData+PGPUtils.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSMutableData+PGPUtils.m"; sourceTree = "<group>"; };
4725C4F41EDDADA10068235E /* bob-private.gpg */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; name = "bob-private.gpg"; path = "keys/bob-private.gpg"; sourceTree = "<group>"; };
4725C4F51EDDADA10068235E /* bob-public.gpg */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; name = "bob-public.gpg"; path = "keys/bob-public.gpg"; sourceTree = "<group>"; };
472F39261E1277D2009260FB /* EnzevalosContact+CoreDataClass.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; name = "EnzevalosContact+CoreDataClass.swift"; path = "../EnzevalosContact+CoreDataClass.swift"; sourceTree = "<group>"; };
@@ -537,23 +344,6 @@
472F398B1E2519C8009260FB /* CNContactExtension.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = CNContactExtension.swift; sourceTree = "<group>"; };
472F398D1E251B8D009260FB /* MailAddress.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = MailAddress.swift; sourceTree = "<group>"; };
472F398F1E252470009260FB /* CNMailAddressesExtension.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = CNMailAddressesExtension.swift; sourceTree = "<group>"; };
- 473AC39120054D06006EB8A6 /* PGPUserAttributeImageSubpacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPUserAttributeImageSubpacket.m; sourceTree = "<group>"; };
- 473AC39220054D07006EB8A6 /* PGPUserAttributeImageSubpacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPUserAttributeImageSubpacket.h; sourceTree = "<group>"; };
- 473AC39520054D29006EB8A6 /* NSArray+PGPUtils.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "NSArray+PGPUtils.h"; sourceTree = "<group>"; };
- 473AC39620054D29006EB8A6 /* NSArray+PGPUtils.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = "NSArray+PGPUtils.m"; sourceTree = "<group>"; };
- 473AC39920054D54006EB8A6 /* ObjectivePGP-Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "ObjectivePGP-Private.h"; sourceTree = "<group>"; };
- 473AC39A20054D7C006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSymetricKeyEncryptedSessionKeyPacket.m; sourceTree = "<group>"; };
- 473AC39B20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSymetricKeyEncryptedSessionKeyPacket.h; sourceTree = "<group>"; };
- 473AC39E20054DBA006EB8A6 /* PGPEncryptedSessionKeyPacketProtocol.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPEncryptedSessionKeyPacketProtocol.h; sourceTree = "<group>"; };
- 473AC39F20054DD9006EB8A6 /* PGPPacketHeader.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPPacketHeader.m; sourceTree = "<group>"; };
- 473AC3A020054DDA006EB8A6 /* PGPPacketHeader.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPPacketHeader.h; sourceTree = "<group>"; };
- 473AC3A320054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPSignatureSubpacketEmbeddedSignature.h; sourceTree = "<group>"; };
- 473AC3A420054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPSignatureSubpacketEmbeddedSignature.m; sourceTree = "<group>"; };
- 473AC3A820054E25006EB8A6 /* twofish.c */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.c; path = twofish.c; sourceTree = "<group>"; };
- 473AC3A920054E25006EB8A6 /* twofish.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = twofish.h; sourceTree = "<group>"; };
- 473AC3AC20054EAA006EB8A6 /* PGPKeyring.m */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.objc; path = PGPKeyring.m; sourceTree = "<group>"; };
- 473AC3AD20054EAA006EB8A6 /* PGPKeyring.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = PGPKeyring.h; sourceTree = "<group>"; };
- 473AC3B020054EB2006EB8A6 /* PGPKeyring+Private.h */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.c.h; path = "PGPKeyring+Private.h"; sourceTree = "<group>"; };
4756DE0D20402F8E00452288 /* invitationTextCensor.html */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text.html; name = invitationTextCensor.html; path = Invitation/invitationTextCensor.html; sourceTree = "<group>"; };
475B00301F7B9565006CDD41 /* SwiftPGP.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = SwiftPGP.swift; sourceTree = "<group>"; };
475B00311F7B9565006CDD41 /* Cryptography.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = Cryptography.swift; sourceTree = "<group>"; };
@@ -578,9 +368,14 @@
47CD5AA82012368D00E771A1 /* logging_pk.asc */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; name = logging_pk.asc; path = keys/logging_pk.asc; sourceTree = "<group>"; };
47CD5AA92012368D00E771A1 /* bitcoinde.asc */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; name = bitcoinde.asc; path = keys/bitcoinde.asc; sourceTree = "<group>"; };
47CD5AAC2012369300E771A1 /* support_pk.asc */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = text; name = support_pk.asc; path = keys/support_pk.asc; sourceTree = "<group>"; };
+ 47CEF4EA2052C3C700887CDB /* ObjectivePGP.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; path = ObjectivePGP.framework; sourceTree = "<group>"; };
+ 47CEF4EC2052C3E600887CDB /* ObjectivePGP.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = ObjectivePGP.framework; path = ../enzevalos_iphone_workspace/ObjectivePGP.framework; sourceTree = "<group>"; };
47D1302A1F7CEE6D007B14DF /* DebugSettings.swift */ = {isa = PBXFileReference; fileEncoding = 4; lastKnownFileType = sourcecode.swift; path = DebugSettings.swift; sourceTree = "<group>"; };
47F7923E203492E3005E7DB6 /* KeyRecord+CoreDataClass.swift */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.swift; path = "KeyRecord+CoreDataClass.swift"; sourceTree = "<group>"; };
47F7923F203492E3005E7DB6 /* KeyRecord+CoreDataProperties.swift */ = {isa = PBXFileReference; lastKnownFileType = sourcecode.swift; path = "KeyRecord+CoreDataProperties.swift"; sourceTree = "<group>"; };
+ 47F867DF2052B47C00AA832F /* Security.framework */ = {isa = PBXFileReference; lastKnownFileType = wrapper.framework; name = Security.framework; path = System/Library/Frameworks/Security.framework; sourceTree = SDKROOT; };
+ 47F867E12052B48E00AA832F /* libz.tbd */ = {isa = PBXFileReference; lastKnownFileType = "sourcecode.text-based-dylib-definition"; name = libz.tbd; path = usr/lib/libz.tbd; sourceTree = SDKROOT; };
+ 47F867E32052B49800AA832F /* libbz2.tbd */ = {isa = PBXFileReference; lastKnownFileType = "sourcecode.text-based-dylib-definition"; name = libbz2.tbd; path = usr/lib/libbz2.tbd; sourceTree = SDKROOT; };
48FB10FF406523D174F4202A /* Pods_enzevalos_iphoneUITests.framework */ = {isa = PBXFileReference; explicitFileType = wrapper.framework; includeInIndex = 0; path = Pods_enzevalos_iphoneUITests.framework; sourceTree = BUILT_PRODUCTS_DIR; };
4AE42F42E91A1BFBF1D5BF6A /* Pods_enzevalos_iphone.framework */ = {isa = PBXFileReference; explicitFileType = wrapper.framework; includeInIndex = 0; path = Pods_enzevalos_iphone.framework; sourceTree = BUILT_PRODUCTS_DIR; };
66E758F271CD65AB3E5FE7A7 /* Pods-enzevalos_iphoneUITests.debug.xcconfig */ = {isa = PBXFileReference; includeInIndex = 1; lastKnownFileType = text.xcconfig; name = "Pods-enzevalos_iphoneUITests.debug.xcconfig"; path = "../enzevalos_iphone_workspace/Pods/Target Support Files/Pods-enzevalos_iphoneUITests/Pods-enzevalos_iphoneUITests.debug.xcconfig"; sourceTree = "<group>"; };
@@ -720,6 +515,10 @@
isa = PBXFrameworksBuildPhase;
buildActionMask = 2147483647;
files = (
+ 47CEF4ED2052C3E700887CDB /* ObjectivePGP.framework in Frameworks */,
+ 47F867E42052B49800AA832F /* libbz2.tbd in Frameworks */,
+ 47F867E22052B48E00AA832F /* libz.tbd in Frameworks */,
+ 47F867E02052B47C00AA832F /* Security.framework in Frameworks */,
F120A7D31F7937BB006D5BF1 /* (null) in Frameworks */,
472F396E1E14F384009260FB /* CoreData.framework in Frameworks */,
9935BC866A86C4A4B9819F35 /* Pods_enzevalos_iphone.framework in Frameworks */,
@@ -804,158 +603,6 @@
name = Invitation;
sourceTree = "<group>";
};
- 471BC8931F960B7C00D64416 /* ObjectivePGP */ = {
- isa = PBXGroup;
- children = (
- 471BC8941F960B7C00D64416 /* CryptoBox */,
- 471BC89F1F960B7C00D64416 /* Info.plist */,
- 471BC8A01F960B7C00D64416 /* ObjectivePGP-Prefix.pch */,
- 471BC8A11F960B7C00D64416 /* ObjectivePGP.h */,
- 471BC8A21F960B7C00D64416 /* ObjectivePGPObject.h */,
- 471BC8A31F960B7C00D64416 /* ObjectivePGPObject.m */,
- 471BC8A41F960B7C00D64416 /* Packets */,
- 471BC8D51F960B7C00D64416 /* PGPArmor.h */,
- 473AC39920054D54006EB8A6 /* ObjectivePGP-Private.h */,
- 471BC8D61F960B7C00D64416 /* PGPArmor.m */,
- 471BC8D71F960B7C00D64416 /* PGPBigNum+Private.h */,
- 471BC8D81F960B7C00D64416 /* PGPBigNum.h */,
- 471BC8D91F960B7C00D64416 /* PGPBigNum.m */,
- 471BC8DA1F960B7C00D64416 /* PGPCryptoCFB.h */,
- 471BC8DB1F960B7C00D64416 /* PGPCryptoCFB.m */,
- 471BC8DC1F960B7C00D64416 /* PGPExportableProtocol.h */,
- 471BC8DD1F960B7C00D64416 /* PGPFingerprint.h */,
- 471BC8DE1F960B7C00D64416 /* PGPFingerprint.m */,
- 471BC8DF1F960B7C00D64416 /* PGPFoundation.h */,
- 471BC8E01F960B7C00D64416 /* PGPFoundation.m */,
- 471BC8E11F960B7C00D64416 /* PGPKey+Private.h */,
- 471BC8E21F960B7C00D64416 /* PGPKey.h */,
- 471BC8E31F960B7C00D64416 /* PGPKey.m */,
- 471BC8E41F960B7C00D64416 /* PGPKeyGenerator.h */,
- 471BC8E51F960B7C00D64416 /* PGPKeyGenerator.m */,
- 471BC8E61F960B7C00D64416 /* PGPKeyID.h */,
- 471BC8E71F960B7C00D64416 /* PGPKeyID.m */,
- 471BC8E81F960B7C00D64416 /* PGPLogging.h */,
- 471BC8E91F960B7C00D64416 /* PGPMacros+Private.h */,
- 471BC8EA1F960B7C00D64416 /* PGPMacros.h */,
- 471BC8EB1F960B7C00D64416 /* PGPMPI.h */,
- 471BC8EC1F960B7C00D64416 /* PGPMPI.m */,
- 471BC8ED1F960B7C00D64416 /* PGPPacketFactory.h */,
- 471BC8EE1F960B7C00D64416 /* PGPPacketFactory.m */,
- 473AC3B020054EB2006EB8A6 /* PGPKeyring+Private.h */,
- 471BC8EF1F960B7C00D64416 /* PGPPartialKey.h */,
- 473AC3AD20054EAA006EB8A6 /* PGPKeyring.h */,
- 473AC3AC20054EAA006EB8A6 /* PGPKeyring.m */,
- 471BC8F01F960B7C00D64416 /* PGPPartialKey.m */,
- 471BC8F11F960B7C00D64416 /* PGPPartialSubKey.h */,
- 471BC8F21F960B7C00D64416 /* PGPPartialSubKey.m */,
- 471BC8F31F960B7C00D64416 /* PGPPKCSEme.h */,
- 471BC8F41F960B7C00D64416 /* PGPPKCSEme.m */,
- 471BC8F51F960B7C00D64416 /* PGPPKCSEmsa.h */,
- 471BC8F61F960B7C00D64416 /* PGPPKCSEmsa.m */,
- 471BC8F71F960B7C00D64416 /* PGPS2K.h */,
- 471BC8F81F960B7C00D64416 /* PGPS2K.m */,
- 471BC8F91F960B7C00D64416 /* PGPTypes.h */,
- 471BC8FA1F960B7C00D64416 /* PGPUser.h */,
- 471BC8FB1F960B7C00D64416 /* PGPUser.m */,
- 471BC8FC1F960B7C00D64416 /* Utils */,
- );
- path = ObjectivePGP;
- sourceTree = "<group>";
- };
- 471BC8941F960B7C00D64416 /* CryptoBox */ = {
- isa = PBXGroup;
- children = (
- 473AC3A720054E25006EB8A6 /* twofish */,
- 471BC8951F960B7C00D64416 /* PGPCryptoHash.h */,
- 471BC8961F960B7C00D64416 /* PGPCryptoHash.m */,
- 471BC8971F960B7C00D64416 /* PGPCryptoUtils.h */,
- 471BC8981F960B7C00D64416 /* PGPCryptoUtils.m */,
- 471BC8991F960B7C00D64416 /* PGPDSA.h */,
- 471BC89A1F960B7C00D64416 /* PGPDSA.m */,
- 471BC89B1F960B7C00D64416 /* PGPKeyMaterial.h */,
- 471BC89C1F960B7C00D64416 /* PGPKeyMaterial.m */,
- 471BC89D1F960B7C00D64416 /* PGPRSA.h */,
- 471BC89E1F960B7C00D64416 /* PGPRSA.m */,
- );
- path = CryptoBox;
- sourceTree = "<group>";
- };
- 471BC8A41F960B7C00D64416 /* Packets */ = {
- isa = PBXGroup;
- children = (
- 473AC39E20054DBA006EB8A6 /* PGPEncryptedSessionKeyPacketProtocol.h */,
- 473AC39220054D07006EB8A6 /* PGPUserAttributeImageSubpacket.h */,
- 473AC3A020054DDA006EB8A6 /* PGPPacketHeader.h */,
- 473AC39F20054DD9006EB8A6 /* PGPPacketHeader.m */,
- 473AC39120054D06006EB8A6 /* PGPUserAttributeImageSubpacket.m */,
- 473AC3A320054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.h */,
- 473AC3A420054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m */,
- 471BC8A51F960B7C00D64416 /* PGPCompressedPacket.h */,
- 471BC8A61F960B7C00D64416 /* PGPCompressedPacket.m */,
- 471BC8A71F960B7C00D64416 /* PGPLiteralPacket.h */,
- 471BC8A81F960B7C00D64416 /* PGPLiteralPacket.m */,
- 473AC39B20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.h */,
- 473AC39A20054D7C006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m */,
- 471BC8A91F960B7C00D64416 /* PGPModificationDetectionCodePacket.h */,
- 471BC8AA1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m */,
- 471BC8AB1F960B7C00D64416 /* PGPOnePassSignaturePacket.h */,
- 471BC8AC1F960B7C00D64416 /* PGPOnePassSignaturePacket.m */,
- 471BC8AD1F960B7C00D64416 /* PGPPacket+Private.h */,
- 471BC8AE1F960B7C00D64416 /* PGPPacket.h */,
- 471BC8AF1F960B7C00D64416 /* PGPPacket.m */,
- 471BC8B11F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.h */,
- 471BC8B21F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m */,
- 471BC8B31F960B7C00D64416 /* PGPPublicKeyPacket+Private.h */,
- 471BC8B41F960B7C00D64416 /* PGPPublicKeyPacket.h */,
- 471BC8B51F960B7C00D64416 /* PGPPublicKeyPacket.m */,
- 471BC8B61F960B7C00D64416 /* PGPPublicSubKeyPacket.h */,
- 471BC8B71F960B7C00D64416 /* PGPPublicSubKeyPacket.m */,
- 471BC8B81F960B7C00D64416 /* PGPSecretKeyPacket+Private.h */,
- 471BC8B91F960B7C00D64416 /* PGPSecretKeyPacket.h */,
- 471BC8BA1F960B7C00D64416 /* PGPSecretKeyPacket.m */,
- 471BC8BB1F960B7C00D64416 /* PGPSecretSubKeyPacket.h */,
- 471BC8BC1F960B7C00D64416 /* PGPSecretSubKeyPacket.m */,
- 471BC8BD1F960B7C00D64416 /* PGPSignaturePacket+Private.h */,
- 471BC8BE1F960B7C00D64416 /* PGPSignaturePacket.h */,
- 471BC8BF1F960B7C00D64416 /* PGPSignaturePacket.m */,
- 471BC8C01F960B7C00D64416 /* PGPSignatureSubpacket+Private.h */,
- 471BC8C11F960B7C00D64416 /* PGPSignatureSubpacket.h */,
- 471BC8C21F960B7C00D64416 /* PGPSignatureSubpacket.m */,
- 471BC8C31F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.h */,
- 471BC8C41F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m */,
- 471BC8C51F960B7C00D64416 /* PGPSignatureSubpacketHeader.h */,
- 471BC8C61F960B7C00D64416 /* PGPSignatureSubpacketHeader.m */,
- 471BC8C71F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.h */,
- 471BC8C81F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m */,
- 471BC8C91F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h */,
- 471BC8CA1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m */,
- 471BC8CD1F960B7C00D64416 /* PGPTrustPacket.h */,
- 471BC8CE1F960B7C00D64416 /* PGPTrustPacket.m */,
- 471BC8CF1F960B7C00D64416 /* PGPUserAttributePacket.h */,
- 471BC8D01F960B7C00D64416 /* PGPUserAttributePacket.m */,
- 471BC8D11F960B7C00D64416 /* PGPUserAttributeSubpacket.h */,
- 471BC8D21F960B7C00D64416 /* PGPUserAttributeSubpacket.m */,
- 471BC8D31F960B7C00D64416 /* PGPUserIDPacket.h */,
- 471BC8D41F960B7C00D64416 /* PGPUserIDPacket.m */,
- );
- path = Packets;
- sourceTree = "<group>";
- };
- 471BC8FC1F960B7C00D64416 /* Utils */ = {
- isa = PBXGroup;
- children = (
- 471BC8FD1F960B7C00D64416 /* NSData+compression.h */,
- 471BC8FE1F960B7C00D64416 /* NSData+compression.m */,
- 471BC8FF1F960B7C00D64416 /* NSData+PGPUtils.h */,
- 473AC39520054D29006EB8A6 /* NSArray+PGPUtils.h */,
- 473AC39620054D29006EB8A6 /* NSArray+PGPUtils.m */,
- 471BC9001F960B7C00D64416 /* NSData+PGPUtils.m */,
- 471BC9031F960B7C00D64416 /* NSMutableData+PGPUtils.h */,
- 471BC9041F960B7C00D64416 /* NSMutableData+PGPUtils.m */,
- );
- path = Utils;
- sourceTree = "<group>";
- };
472F39921E279792009260FB /* protocols */ = {
isa = PBXGroup;
children = (
@@ -967,15 +614,6 @@
name = protocols;
sourceTree = "<group>";
};
- 473AC3A720054E25006EB8A6 /* twofish */ = {
- isa = PBXGroup;
- children = (
- 473AC3A820054E25006EB8A6 /* twofish.c */,
- 473AC3A920054E25006EB8A6 /* twofish.h */,
- );
- path = twofish;
- sourceTree = "<group>";
- };
47B91AC01EC0C1CF000AE3EE /* coredata */ = {
isa = PBXGroup;
children = (
@@ -1013,6 +651,10 @@
78280F99990BFF65543B7F0B /* Frameworks */ = {
isa = PBXGroup;
children = (
+ 47CEF4EC2052C3E600887CDB /* ObjectivePGP.framework */,
+ 47F867E32052B49800AA832F /* libbz2.tbd */,
+ 47F867E12052B48E00AA832F /* libz.tbd */,
+ 47F867DF2052B47C00AA832F /* Security.framework */,
472F396D1E14F384009260FB /* CoreData.framework */,
4AE42F42E91A1BFBF1D5BF6A /* Pods_enzevalos_iphone.framework */,
C9B9CE43043CF806E1C02FCA /* Pods_enzevalos_iphoneTests.framework */,
@@ -1119,6 +761,7 @@
A135266C1D955BDF00D3BFE1 = {
isa = PBXGroup;
children = (
+ 47CEF4EA2052C3C700887CDB /* ObjectivePGP.framework */,
A13526771D955BDF00D3BFE1 /* enzevalos_iphone */,
A135268F1D955BE000D3BFE1 /* enzevalos_iphoneTests */,
A135269A1D955BE000D3BFE1 /* enzevalos_iphoneUITests */,
@@ -1146,7 +789,6 @@
3EB4FA9C2012007C001D0625 /* Dialog */,
3EC35F1F2003755F008BDF95 /* Invitation */,
F1C733331FEC1CAC005A497E /* About */,
- 471BC8931F960B7C00D64416 /* ObjectivePGP */,
8428A8511F436952007649A5 /* Gamification */,
A17FDFF1202C680A00F7BA89 /* debug and study */,
47B91AC11EC0C1FB000AE3EE /* data */,
@@ -1392,6 +1034,8 @@
A13526731D955BDF00D3BFE1 /* Resources */,
1B3A7EC4B7EC43108D4CA42F /* [CP] Embed Pods Frameworks */,
9C00DB37D91C40FACD06D614 /* [CP] Copy Pods Resources */,
+ 47F867DB2052B33C00AA832F /* CopyFiles */,
+ 47F867E52052B4B500AA832F /* ShellScript */,
);
buildRules = (
);
@@ -1527,7 +1171,6 @@
3E9709421FAC95F5005825C9 /* alice_enzevalos_public.asc in Resources */,
3E9709431FAC95F5005825C9 /* providers.json in Resources */,
3E9709441FAC95F5005825C9 /* idsolutions-private.gpg in Resources */,
- 3E9709451FAC95F5005825C9 /* Info.plist in Resources */,
3EB4FAA22012007C001D0625 /* Dialog.storyboard in Resources */,
3E9709461FAC95F5005825C9 /* nchr-public.gpg in Resources */,
3E9709471FAC95F5005825C9 /* nchr-private.gpg in Resources */,
@@ -1571,7 +1214,6 @@
A19C12471DE602FF007F72E7 /* jabo.asc in Resources */,
479BBDDB1EFEA17900A2107C /* alice_enzevalos_public.asc in Resources */,
A16BA2121E0439B6005E29E3 /* providers.json in Resources */,
- 471BC90A1F960B7C00D64416 /* Info.plist in Resources */,
47953AA91FD7000200D4631A /* bitcoinde.asc in Resources */,
47CD5AAB2012368D00E771A1 /* bitcoinde.asc in Resources */,
F14D189D1ED880680080515D /* nchr-public.gpg in Resources */,
@@ -1652,6 +1294,20 @@
shellScript = "\"${SRCROOT}/../enzevalos_iphone_workspace/Pods/Target Support Files/Pods-enzevalos_iphone/Pods-enzevalos_iphone-frameworks.sh\"\n";
showEnvVarsInLog = 0;
};
+ 47F867E52052B4B500AA832F /* ShellScript */ = {
+ isa = PBXShellScriptBuildPhase;
+ buildActionMask = 8;
+ files = (
+ );
+ inputPaths = (
+ );
+ outputPaths = (
+ );
+ runOnlyForDeploymentPostprocessing = 1;
+ shellPath = /bin/sh;
+ shellScript = "bash \"${BUILT_PRODUCTS_DIR}/${FRAMEWORKS_FOLDER_PATH}/ObjectivePGP.framework/strip-frameworks.sh\"";
+ showEnvVarsInLog = 0;
+ };
60E197910FD6B0523F9273AE /* [CP] Check Pods Manifest.lock */ = {
isa = PBXShellScriptBuildPhase;
buildActionMask = 2147483647;
@@ -1721,11 +1377,11 @@
);
inputPaths = (
"${SRCROOT}/../enzevalos_iphone_workspace/Pods/Target Support Files/Pods-enzevalos_iphone/Pods-enzevalos_iphone-resources.sh",
- "${PODS_CONFIGURATION_BUILD_DIR}/HockeySDK/HockeySDKResources.bundle",
+ $PODS_CONFIGURATION_BUILD_DIR/HockeySDK/HockeySDKResources.bundle,
);
name = "[CP] Copy Pods Resources";
outputPaths = (
- "${TARGET_BUILD_DIR}/${UNLOCALIZED_RESOURCES_FOLDER_PATH}/HockeySDKResources.bundle",
+ "${TARGET_BUILD_DIR}/${UNLOCALIZED_RESOURCES_FOLDER_PATH}",
);
runOnlyForDeploymentPostprocessing = 0;
shellPath = /bin/sh;
@@ -1775,11 +1431,11 @@
);
inputPaths = (
"${SRCROOT}/../enzevalos_iphone_workspace/Pods/Target Support Files/Pods-enzevalos_iphone-AdHoc/Pods-enzevalos_iphone-AdHoc-resources.sh",
- "${PODS_CONFIGURATION_BUILD_DIR}/HockeySDK/HockeySDKResources.bundle",
+ $PODS_CONFIGURATION_BUILD_DIR/HockeySDK/HockeySDKResources.bundle,
);
name = "[CP] Copy Pods Resources";
outputPaths = (
- "${TARGET_BUILD_DIR}/${UNLOCALIZED_RESOURCES_FOLDER_PATH}/HockeySDKResources.bundle",
+ "${TARGET_BUILD_DIR}/${UNLOCALIZED_RESOURCES_FOLDER_PATH}",
);
runOnlyForDeploymentPostprocessing = 0;
shellPath = /bin/sh;
@@ -1875,48 +1531,27 @@
isa = PBXSourcesBuildPhase;
buildActionMask = 2147483647;
files = (
- 3E9708B31FAC95F5005825C9 /* PGPPartialKey.m in Sources */,
3E9708B41FAC95F5005825C9 /* Mail.swift in Sources */,
3E9708B51FAC95F5005825C9 /* Contact.swift in Sources */,
3E9708B61FAC95F5005825C9 /* Record.swift in Sources */,
- 3E9708B71FAC95F5005825C9 /* PGPPacket.m in Sources */,
- 473AC3AB20054E25006EB8A6 /* twofish.c in Sources */,
- 3E9708B81FAC95F5005825C9 /* PGPKeyID.m in Sources */,
- 3E9708B91FAC95F5005825C9 /* NSData+compression.m in Sources */,
3E9708BA1FAC95F5005825C9 /* TextFormatter.swift in Sources */,
- 3E9708BC1FAC95F5005825C9 /* PGPSymmetricallyEncryptedDataPacket.m in Sources */,
3E9708BD1FAC95F5005825C9 /* ListViewCell.swift in Sources */,
- 3E9708BE1FAC95F5005825C9 /* PGPUser.m in Sources */,
- 473AC39420054D07006EB8A6 /* PGPUserAttributeImageSubpacket.m in Sources */,
- 3E9708BF1FAC95F5005825C9 /* PGPSecretKeyPacket.m in Sources */,
3E9708C01FAC95F5005825C9 /* FolderListCell.swift in Sources */,
3E9708C11FAC95F5005825C9 /* NSDateCompare.swift in Sources */,
- 3E9708C21FAC95F5005825C9 /* PGPCompressedPacket.m in Sources */,
- 3E9708C31FAC95F5005825C9 /* PGPRSA.m in Sources */,
3E9708C41FAC95F5005825C9 /* InboxCellDelegator.swift in Sources */,
3E9708C51FAC95F5005825C9 /* Badges.swift in Sources */,
3E9708C61FAC95F5005825C9 /* BadgeCaseCollectionViewCell.swift in Sources */,
3E9708C71FAC95F5005825C9 /* Mail_Address+CoreDataClass.swift in Sources */,
3E9708C81FAC95F5005825C9 /* CollectionDataDelegate.swift in Sources */,
3E9708C91FAC95F5005825C9 /* DebugSettings.swift in Sources */,
- 473AC39D20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m in Sources */,
- 3E9708CA1FAC95F5005825C9 /* PGPS2K.m in Sources */,
- 3E9708CB1FAC95F5005825C9 /* PGPPacketFactory.m in Sources */,
3E9708CD1FAC95F5005825C9 /* SendViewController.swift in Sources */,
- 3E9708CE1FAC95F5005825C9 /* PGPModificationDetectionCodePacket.m in Sources */,
3E9708CF1FAC95F5005825C9 /* EphemeralMail.swift in Sources */,
- 3E9708D01FAC95F5005825C9 /* PGPPKCSEme.m in Sources */,
3E9708D11FAC95F5005825C9 /* SubBadgeHeaderTableViewCell.swift in Sources */,
3E9708D21FAC95F5005825C9 /* InboxViewController.swift in Sources */,
- 3E9708D31FAC95F5005825C9 /* PGPPublicSubKeyPacket.m in Sources */,
3E9708D41FAC95F5005825C9 /* IconsStyleKit.swift in Sources */,
- 3E9708D51FAC95F5005825C9 /* PGPKey.m in Sources */,
3E9708D61FAC95F5005825C9 /* UserNameGamificationTableViewCell.swift in Sources */,
3E9708D71FAC95F5005825C9 /* CNContactExtension.swift in Sources */,
- 3E9708D81FAC95F5005825C9 /* PGPPKCSEmsa.m in Sources */,
3E9708D91FAC95F5005825C9 /* QRScannerView.swift in Sources */,
- 473AC3A620054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m in Sources */,
- 3E9708DA1FAC95F5005825C9 /* PGPCryptoCFB.m in Sources */,
3E9708DB1FAC95F5005825C9 /* ReplaceSegue.swift in Sources */,
3E9708DD1FAC95F5005825C9 /* ArrowTableViewCell.swift in Sources */,
3E9708DE1FAC95F5005825C9 /* ContactViewController.swift in Sources */,
@@ -1926,49 +1561,32 @@
3E9708E21FAC95F5005825C9 /* UIViewResolver.swift in Sources */,
3EC35F2E200376A1008BDF95 /* SendViewController+Invitation.swift in Sources */,
3EB4FAA520120096001D0625 /* DialogOption.swift in Sources */,
- 3E9708E31FAC95F5005825C9 /* PGPArmor.m in Sources */,
3E9708E41FAC95F5005825C9 /* SwiftPGP.swift in Sources */,
- 3E9708E51FAC95F5005825C9 /* PGPCryptoUtils.m in Sources */,
3E9708E61FAC95F5005825C9 /* QRCodeGenerator.swift in Sources */,
- 473AC3A220054DDA006EB8A6 /* PGPPacketHeader.m in Sources */,
- 3E9708E81FAC95F5005825C9 /* NSMutableData+PGPUtils.m in Sources */,
3E9708E91FAC95F5005825C9 /* EnzevalosContact+CoreDataClass.swift in Sources */,
3E9708EA1FAC95F5005825C9 /* CustomCells.swift in Sources */,
3E9708EB1FAC95F5005825C9 /* GamificationStatusViewController.swift in Sources */,
- 3E9708EC1FAC95F5005825C9 /* ObjectivePGPObject.m in Sources */,
- 3E9708ED1FAC95F5005825C9 /* PGPFingerprint.m in Sources */,
- 3E9708EE1FAC95F5005825C9 /* PGPBigNum.m in Sources */,
3E9708EF1FAC95F5005825C9 /* FolderViewController.swift in Sources */,
3E9708F01FAC95F5005825C9 /* Theme.swift in Sources */,
- 473AC3AF20054EAA006EB8A6 /* PGPKeyring.m in Sources */,
3E9708F11FAC95F5005825C9 /* LinearBadgeViewController.swift in Sources */,
3E9708F21FAC95F5005825C9 /* ContactCell.swift in Sources */,
47A7975B1FCD56B7006B3BC4 /* enzevalos_iphone.xcdatamodeld in Sources */,
- 3E9708F41FAC95F5005825C9 /* PGPSecretSubKeyPacket.m in Sources */,
- 3E9708F51FAC95F5005825C9 /* PGPUserIDPacket.m in Sources */,
F1ADF0751FBDF7D20017AE31 /* Logger.swift in Sources */,
3E9708F61FAC95F5005825C9 /* Folder+CoreDataProperties.swift in Sources */,
3E9708F71FAC95F5005825C9 /* PersistentMail +CoreDataClass.swift in Sources */,
- 3E9708F81FAC95F5005825C9 /* PGPTrustPacket.m in Sources */,
3E9708F91FAC95F5005825C9 /* PersistentKey+CoreDataProperties.swift in Sources */,
3E9708FA1FAC95F5005825C9 /* AnimatedSendIcon.swift in Sources */,
3E9708FB1FAC95F5005825C9 /* ExportViewController.swift in Sources */,
3E9708FC1FAC95F5005825C9 /* RefreshControlExtension.swift in Sources */,
472276BE1FCD484C00ADA507 /* StringExtension.swift in Sources */,
472276BC1FCD46B200ADA507 /* LoggingEventType.swift in Sources */,
- 3E9708FD1FAC95F5005825C9 /* PGPMPI.m in Sources */,
3E9708FF1FAC95F5005825C9 /* Mail_Address+CoreDataProperties.swift in Sources */,
3E9709001FAC95F5005825C9 /* UserData.swift in Sources */,
- 3E9709011FAC95F5005825C9 /* PGPCryptoHash.m in Sources */,
- 3E9709021FAC95F5005825C9 /* PGPKeyMaterial.m in Sources */,
3E9709031FAC95F5005825C9 /* MessageBodyTableViewCell.swift in Sources */,
3E9709041FAC95F5005825C9 /* ReadVENDelegate.swift in Sources */,
- 3E9709051FAC95F5005825C9 /* PGPUserAttributePacket.m in Sources */,
3E9709061FAC95F5005825C9 /* PersistentKey+CoreDataClass.swift in Sources */,
- 3E9709071FAC95F5005825C9 /* PGPSignaturePacket.m in Sources */,
3E9709081FAC95F5005825C9 /* KeyViewController.swift in Sources */,
3E9709091FAC95F5005825C9 /* ExportCells.swift in Sources */,
- 3E97090A1FAC95F5005825C9 /* PGPSignatureSubpacketCreationTime.m in Sources */,
3E97090B1FAC95F5005825C9 /* CNMailAddressesExtension.swift in Sources */,
3E97090C1FAC95F5005825C9 /* FolderListViewController.swift in Sources */,
3E97090D1FAC95F5005825C9 /* ViewControllerPannable.swift in Sources */,
@@ -1976,7 +1594,6 @@
3E97090F1FAC95F5005825C9 /* CircleView.swift in Sources */,
3E9709101FAC95F5005825C9 /* PersistentMail +CoreDataProperties.swift in Sources */,
3E9709111FAC95F5005825C9 /* ArrowView.swift in Sources */,
- 473AC39820054D29006EB8A6 /* NSArray+PGPUtils.m in Sources */,
3E9709121FAC95F5005825C9 /* InboxTableViewCell.swift in Sources */,
3E9709131FAC95F5005825C9 /* Onboarding.swift in Sources */,
3E9709141FAC95F5005825C9 /* AppDelegate.swift in Sources */,
@@ -1984,34 +1601,21 @@
3E9709151FAC95F5005825C9 /* FolderCell.swift in Sources */,
3E9709161FAC95F5005825C9 /* GamificationData.swift in Sources */,
3E9709171FAC95F5005825C9 /* Folder+CoreDataClass.swift in Sources */,
- 3E9709181FAC95F5005825C9 /* PGPPublicKeyEncryptedSessionKeyPacket.m in Sources */,
3E97091A1FAC95F5005825C9 /* Cryptography.swift in Sources */,
3E97091B1FAC95F5005825C9 /* MailHandler.swift in Sources */,
3E97091C1FAC95F5005825C9 /* AddressHandler.swift in Sources */,
3E97091D1FAC95F5005825C9 /* DataHandler.swift in Sources */,
- 3E97091E1FAC95F5005825C9 /* PGPSignatureSubpacketHeader.m in Sources */,
- 3E97091F1FAC95F5005825C9 /* NSData+PGPUtils.m in Sources */,
3E9709201FAC95F5005825C9 /* ReadViewController.swift in Sources */,
- 3E9709211FAC95F5005825C9 /* PGPSignatureSubpacket.m in Sources */,
3E9709221FAC95F5005825C9 /* InitViewController.swift in Sources */,
3E9709231FAC95F5005825C9 /* MailAddress.swift in Sources */,
3E9709241FAC95F5005825C9 /* MailHandlerDelegator.swift in Sources */,
- 3E9709251FAC95F5005825C9 /* PGPFoundation.m in Sources */,
- 3E9709261FAC95F5005825C9 /* PGPLiteralPacket.m in Sources */,
- 3E9709271FAC95F5005825C9 /* PGPPublicKeyPacket.m in Sources */,
- 3E9709281FAC95F5005825C9 /* PGPKeyGenerator.m in Sources */,
- 3E9709291FAC95F5005825C9 /* PGPDSA.m in Sources */,
3E97092A1FAC95F5005825C9 /* LabelStyleKit.swift in Sources */,
3E048C061FAC9ABD00948524 /* HockeySDK.swift in Sources */,
- 3E97092B1FAC95F5005825C9 /* PGPPartialSubKey.m in Sources */,
3E97092C1FAC95F5005825C9 /* SubBadgeTableViewCell.swift in Sources */,
3E97092D1FAC95F5005825C9 /* FrequentCell.swift in Sources */,
3E97092E1FAC95F5005825C9 /* ListViewController.swift in Sources */,
3E97092F1FAC95F5005825C9 /* FlipTransition.swift in Sources */,
- 3E9709301FAC95F5005825C9 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m in Sources */,
3EB4FAA02012007C001D0625 /* DialogViewController.swift in Sources */,
- 3E9709311FAC95F5005825C9 /* PGPUserAttributeSubpacket.m in Sources */,
- 3E9709321FAC95F5005825C9 /* PGPOnePassSignaturePacket.m in Sources */,
3E9709331FAC95F5005825C9 /* EnzevalosContact+CoreDataProperties.swift in Sources */,
3E9709341FAC95F5005825C9 /* BadgeCase.swift in Sources */,
);
@@ -2021,50 +1625,29 @@
isa = PBXSourcesBuildPhase;
buildActionMask = 2147483647;
files = (
- 471BC92B1F960B7C00D64416 /* PGPPartialKey.m in Sources */,
47691A8A1ECB56D1004BCFC5 /* Mail.swift in Sources */,
472F398A1E251787009260FB /* Contact.swift in Sources */,
472F39861E1FA34E009260FB /* Record.swift in Sources */,
- 471BC9101F960B7C00D64416 /* PGPPacket.m in Sources */,
- 471BC9281F960B7C00D64416 /* PGPKeyID.m in Sources */,
- 471BC9311F960B7C00D64416 /* NSData+compression.m in Sources */,
A1C3270E1DB907D900CE2ED5 /* TextFormatter.swift in Sources */,
- 471BC91A1F960B7C00D64416 /* PGPSymmetricallyEncryptedDataPacket.m in Sources */,
F12041FD1DA409A5002E4940 /* ListViewCell.swift in Sources */,
- 471BC9301F960B7C00D64416 /* PGPUser.m in Sources */,
- 471BC9141F960B7C00D64416 /* PGPSecretKeyPacket.m in Sources */,
A1E2324E1F0FA41A00DC9D40 /* FolderListCell.swift in Sources */,
A1EB059C1D956957008659C1 /* NSDateCompare.swift in Sources */,
- 471BC90C1F960B7C00D64416 /* PGPCompressedPacket.m in Sources */,
- 471BC9091F960B7C00D64416 /* PGPRSA.m in Sources */,
A1EB05941D956931008659C1 /* InboxCellDelegator.swift in Sources */,
8428A85D1F436A05007649A5 /* Badges.swift in Sources */,
- 473AC3A120054DDA006EB8A6 /* PGPPacketHeader.m in Sources */,
8428A8651F436A11007649A5 /* BadgeCaseCollectionViewCell.swift in Sources */,
472F39811E1E5347009260FB /* Mail_Address+CoreDataClass.swift in Sources */,
A1EB05821D95685B008659C1 /* CollectionDataDelegate.swift in Sources */,
- 473AC3AA20054E25006EB8A6 /* twofish.c in Sources */,
47D1302B1F7CEE6D007B14DF /* DebugSettings.swift in Sources */,
- 471BC92F1F960B7C00D64416 /* PGPS2K.m in Sources */,
- 471BC92A1F960B7C00D64416 /* PGPPacketFactory.m in Sources */,
A1EB05801D956851008659C1 /* SendViewController.swift in Sources */,
- 471BC90E1F960B7C00D64416 /* PGPModificationDetectionCodePacket.m in Sources */,
47691A8C1ECC3EC7004BCFC5 /* EphemeralMail.swift in Sources */,
- 471BC92D1F960B7C00D64416 /* PGPPKCSEme.m in Sources */,
8428A8671F436A11007649A5 /* SubBadgeHeaderTableViewCell.swift in Sources */,
A1EB05981D956947008659C1 /* InboxViewController.swift in Sources */,
- 473AC39C20054D7D006EB8A6 /* PGPSymetricKeyEncryptedSessionKeyPacket.m in Sources */,
- 471BC9131F960B7C00D64416 /* PGPPublicSubKeyPacket.m in Sources */,
F1984D721E1D327200804E1E /* IconsStyleKit.swift in Sources */,
- 471BC9261F960B7C00D64416 /* PGPKey.m in Sources */,
F1737ACB2031D7D70000312B /* StudySettings.swift in Sources */,
8428A8691F436A11007649A5 /* UserNameGamificationTableViewCell.swift in Sources */,
A114E4321FACB23000E40243 /* StringExtension.swift in Sources */,
472F398C1E2519C8009260FB /* CNContactExtension.swift in Sources */,
- 471BC92E1F960B7C00D64416 /* PGPPKCSEmsa.m in Sources */,
F113C3851F30D06800E7F1D6 /* QRScannerView.swift in Sources */,
- 471BC9231F960B7C00D64416 /* PGPCryptoCFB.m in Sources */,
- 473AC39320054D07006EB8A6 /* PGPUserAttributeImageSubpacket.m in Sources */,
F18B44601E704C550080C041 /* ReplaceSegue.swift in Sources */,
8428A8661F436A11007649A5 /* ArrowTableViewCell.swift in Sources */,
F1ACF21C1E0C1C6800C1B843 /* ContactViewController.swift in Sources */,
@@ -2072,52 +1655,35 @@
A1EB057E1D956848008659C1 /* VENDataDelegate.swift in Sources */,
8428A86F1F436A1E007649A5 /* InviteFriendViewController.swift in Sources */,
A1E81B671DCA296200535F98 /* UIViewResolver.swift in Sources */,
- 471BC9211F960B7C00D64416 /* PGPArmor.m in Sources */,
475B00331F7B9565006CDD41 /* SwiftPGP.swift in Sources */,
- 471BC9061F960B7C00D64416 /* PGPCryptoUtils.m in Sources */,
3EB4FAA420120096001D0625 /* DialogOption.swift in Sources */,
F14239C11F30A99C00998A83 /* QRCodeGenerator.swift in Sources */,
- 471BC9341F960B7C00D64416 /* NSMutableData+PGPUtils.m in Sources */,
472F392A1E1277D2009260FB /* EnzevalosContact+CoreDataClass.swift in Sources */,
F1AF938F1E2D04BA00755128 /* CustomCells.swift in Sources */,
- 473AC3AE20054EAA006EB8A6 /* PGPKeyring.m in Sources */,
8428A8711F436A1E007649A5 /* GamificationStatusViewController.swift in Sources */,
- 471BC90B1F960B7C00D64416 /* ObjectivePGPObject.m in Sources */,
- 471BC9241F960B7C00D64416 /* PGPFingerprint.m in Sources */,
F1866C86201F707200B72453 /* EmailHelper.m in Sources */,
- 471BC9221F960B7C00D64416 /* PGPBigNum.m in Sources */,
47F79241203492E3005E7DB6 /* KeyRecord+CoreDataProperties.swift in Sources */,
A10DE4201EFAA2CE005E8189 /* FolderViewController.swift in Sources */,
- 473AC39720054D29006EB8A6 /* NSArray+PGPUtils.m in Sources */,
3EB4FA9F2012007C001D0625 /* DialogViewController.swift in Sources */,
476142081E07E52B00FD5E4F /* Theme.swift in Sources */,
8428A8701F436A1E007649A5 /* LinearBadgeViewController.swift in Sources */,
A1EB057A1D956829008659C1 /* ContactCell.swift in Sources */,
- 471BC9151F960B7C00D64416 /* PGPSecretSubKeyPacket.m in Sources */,
- 471BC9201F960B7C00D64416 /* PGPUserIDPacket.m in Sources */,
A12FC23120221A1400196008 /* ExportInfoViewController.swift in Sources */,
475DF47A1F0D54C9009D807F /* Folder+CoreDataProperties.swift in Sources */,
472F392C1E1277D2009260FB /* PersistentMail +CoreDataClass.swift in Sources */,
- 471BC91D1F960B7C00D64416 /* PGPTrustPacket.m in Sources */,
475B00431F7BB6D6006CDD41 /* PersistentKey+CoreDataProperties.swift in Sources */,
F119D2901E364B59001D732A /* AnimatedSendIcon.swift in Sources */,
4707096D1F8F9F4900657F41 /* ExportViewController.swift in Sources */,
F12060801DA540FE00F6EF37 /* RefreshControlExtension.swift in Sources */,
- 471BC9291F960B7C00D64416 /* PGPMPI.m in Sources */,
A13526811D955BDF00D3BFE1 /* enzevalos_iphone.xcdatamodeld in Sources */,
472F39821E1E5347009260FB /* Mail_Address+CoreDataProperties.swift in Sources */,
476373C21E09BA88004D5EFE /* UserData.swift in Sources */,
- 471BC9051F960B7C00D64416 /* PGPCryptoHash.m in Sources */,
- 471BC9081F960B7C00D64416 /* PGPKeyMaterial.m in Sources */,
A1EB05A01D95696C008659C1 /* MessageBodyTableViewCell.swift in Sources */,
F18B44621E73286C0080C041 /* ReadVENDelegate.swift in Sources */,
- 471BC91E1F960B7C00D64416 /* PGPUserAttributePacket.m in Sources */,
475B00421F7BB6D6006CDD41 /* PersistentKey+CoreDataClass.swift in Sources */,
- 471BC9161F960B7C00D64416 /* PGPSignaturePacket.m in Sources */,
3EC35F2420037651008BDF95 /* InvitationHelper.swift in Sources */,
A1D5076F1E80257A00B68B38 /* KeyViewController.swift in Sources */,
A1A9DE731F864B0500B808AA /* ExportCells.swift in Sources */,
- 471BC9181F960B7C00D64416 /* PGPSignatureSubpacketCreationTime.m in Sources */,
472F39901E252470009260FB /* CNMailAddressesExtension.swift in Sources */,
A1E2324C1F0FA13F00DC9D40 /* FolderListViewController.swift in Sources */,
F113C38B1F3344C200E7F1D6 /* ViewControllerPannable.swift in Sources */,
@@ -2135,36 +1701,22 @@
8428A85F1F436A05007649A5 /* GamificationData.swift in Sources */,
475DF4791F0D54C9009D807F /* Folder+CoreDataClass.swift in Sources */,
3EC35F2D200376A1008BDF95 /* SendViewController+Invitation.swift in Sources */,
- 471BC9111F960B7C00D64416 /* PGPPublicKeyEncryptedSessionKeyPacket.m in Sources */,
475B00341F7B9565006CDD41 /* Cryptography.swift in Sources */,
A1EB057C1D956838008659C1 /* MailHandler.swift in Sources */,
A1EB05881D956879008659C1 /* AddressHandler.swift in Sources */,
472F39701E14F75C009260FB /* DataHandler.swift in Sources */,
- 471BC9191F960B7C00D64416 /* PGPSignatureSubpacketHeader.m in Sources */,
A1C62E9A2018F716000E5273 /* OnboardingValueState.swift in Sources */,
- 471BC9321F960B7C00D64416 /* NSData+PGPUtils.m in Sources */,
A1EB05901D956923008659C1 /* ReadViewController.swift in Sources */,
- 471BC9171F960B7C00D64416 /* PGPSignatureSubpacket.m in Sources */,
A1C3DEEC1E0AB15300EB7D02 /* InitViewController.swift in Sources */,
472F398E1E251B8D009260FB /* MailAddress.swift in Sources */,
F12060821DA552FC00F6EF37 /* MailHandlerDelegator.swift in Sources */,
- 471BC9251F960B7C00D64416 /* PGPFoundation.m in Sources */,
- 471BC90D1F960B7C00D64416 /* PGPLiteralPacket.m in Sources */,
- 473AC3A520054DFB006EB8A6 /* PGPSignatureSubpacketEmbeddedSignature.m in Sources */,
- 471BC9121F960B7C00D64416 /* PGPPublicKeyPacket.m in Sources */,
- 471BC9271F960B7C00D64416 /* PGPKeyGenerator.m in Sources */,
A18E7D771FBDE5D9002F7CC9 /* LoggingEventType.swift in Sources */,
- 471BC9071F960B7C00D64416 /* PGPDSA.m in Sources */,
F1984D741E1E92B300804E1E /* LabelStyleKit.swift in Sources */,
3E048C051FAC9ABD00948524 /* HockeySDK.swift in Sources */,
- 471BC92C1F960B7C00D64416 /* PGPPartialSubKey.m in Sources */,
8428A8681F436A11007649A5 /* SubBadgeTableViewCell.swift in Sources */,
A1EB05861D956872008659C1 /* FrequentCell.swift in Sources */,
F12041FB1DA3FBF7002E4940 /* ListViewController.swift in Sources */,
F18B445E1E7044B70080C041 /* FlipTransition.swift in Sources */,
- 471BC91B1F960B7C00D64416 /* PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m in Sources */,
- 471BC91F1F960B7C00D64416 /* PGPUserAttributeSubpacket.m in Sources */,
- 471BC90F1F960B7C00D64416 /* PGPOnePassSignaturePacket.m in Sources */,
472F397E1E1D0B0B009260FB /* EnzevalosContact+CoreDataProperties.swift in Sources */,
8428A86E1F436A1E007649A5 /* BadgeCase.swift in Sources */,
);
@@ -2477,6 +2029,11 @@
CODE_SIGN_STYLE = Automatic;
DEFINES_MODULE = NO;
DEVELOPMENT_TEAM = "";
+ FRAMEWORK_SEARCH_PATHS = (
+ "$(inherited)",
+ "$(PROJECT_DIR)/enzevalos_iphone",
+ "$(PROJECT_DIR)_workspace",
+ );
GCC_SYMBOLS_PRIVATE_EXTERN = NO;
INFOPLIST_FILE = "enzevalos_iphone/PLists/enzevalos-Info.plist";
IPHONEOS_DEPLOYMENT_TARGET = 9.3;
@@ -2531,6 +2088,11 @@
CODE_SIGN_STYLE = Automatic;
DEFINES_MODULE = NO;
DEVELOPMENT_TEAM = "";
+ FRAMEWORK_SEARCH_PATHS = (
+ "$(inherited)",
+ "$(PROJECT_DIR)/enzevalos_iphone",
+ "$(PROJECT_DIR)_workspace",
+ );
GCC_SYMBOLS_PRIVATE_EXTERN = NO;
INFOPLIST_FILE = "enzevalos_iphone/PLists/enzevalos-Info.plist";
IPHONEOS_DEPLOYMENT_TARGET = 9.3;
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoHash.m b/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoHash.m
deleted file mode 100755
index 76baab74c5d63d5593f7114860c199c7fba77bcd..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoHash.m
+++ /dev/null
@@ -1,75 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPCryptoHash.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <Foundation/Foundation.h>
-#import <openssl/ripemd.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-NSData *_Nullable PGPCalculateHash(PGPHashAlgorithm algorithm, PGP_NOESCAPE PGPUpdateBlock update) {
- switch (algorithm) {
- case PGPHashMD5:
- return PGPmd5(update);
- case PGPHashSHA1:
- return PGPsha1(update);
- case PGPHashSHA224:
- return PGPsha224(update);
- case PGPHashSHA256:
- return PGPsha256(update);
- case PGPHashSHA384:
- return PGPsha384(update);
- case PGPHashSHA512:
- return PGPsha512(update);
- case PGPHashRIPEMD160:
- return PGPripemd160(update);
- default:
- PGPLogWarning(@"Hash algorithm code %@ is not supported.", @(algorithm));
- }
- return nil;
-}
-
-#define commonHashImpl(name, INITfn, UPDATEfn, FINALfn, CTX, DIGEST_LENGTH) \
- NSData *_Nullable PGP##name(PGP_NOESCAPE PGPUpdateBlock update) { \
- let ctx = calloc(1, sizeof(CTX)); \
- if (!ctx) { \
- return nil; \
- } \
- \
- INITfn(ctx); \
- \
- if (update) { \
- update(^(const void *data, int lenght) { \
- UPDATEfn(ctx, data, (CC_LONG)lenght); \
- }); \
- } \
- \
- UInt8 *outbuf = calloc(DIGEST_LENGTH, sizeof(UInt8)); \
- if (!outbuf) { \
- free(ctx); \
- return nil; \
- } \
- FINALfn(outbuf, ctx); \
- \
- let outData = [NSData dataWithBytes:outbuf length:DIGEST_LENGTH]; \
- \
- free(outbuf); \
- free(ctx); \
- \
- return outData; \
- }
-
-commonHashImpl(md5, CC_MD5_Init, CC_MD5_Update, CC_MD5_Final, CC_MD5_CTX, CC_MD5_DIGEST_LENGTH) commonHashImpl(sha1, CC_SHA1_Init, CC_SHA1_Update, CC_SHA1_Final, CC_SHA1_CTX, CC_SHA1_DIGEST_LENGTH) commonHashImpl(sha224, CC_SHA224_Init, CC_SHA224_Update, CC_SHA224_Final, CC_SHA256_CTX, CC_SHA224_DIGEST_LENGTH) commonHashImpl(sha256, CC_SHA256_Init, CC_SHA256_Update, CC_SHA256_Final, CC_SHA256_CTX, CC_SHA256_DIGEST_LENGTH);
-commonHashImpl(sha384, CC_SHA384_Init, CC_SHA384_Update, CC_SHA384_Final, CC_SHA512_CTX, CC_SHA384_DIGEST_LENGTH) commonHashImpl(sha512, CC_SHA512_Init, CC_SHA512_Update, CC_SHA512_Final, CC_SHA512_CTX, CC_SHA512_DIGEST_LENGTH) commonHashImpl(ripemd160, RIPEMD160_Init, RIPEMD160_Update, RIPEMD160_Final, RIPEMD160_CTX, RIPEMD160_DIGEST_LENGTH);
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoUtils.m b/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoUtils.m
deleted file mode 100755
index f915e1e0dd8e7fab67a7b3f9054219f5aa22c552..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPCryptoUtils.m
+++ /dev/null
@@ -1,125 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPCryptoUtils.h"
-#import "PGPRSA.h"
-#import "PGPDSA.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPMacros+Private.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <Security/Security.h>
-
-#import <openssl/aes.h>
-#import <openssl/blowfish.h>
-#import <openssl/camellia.h>
-#import <openssl/cast.h>
-#import <openssl/des.h>
-#import <openssl/idea.h>
-#import <openssl/ripemd.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPCryptoUtils
-
-+ (NSUInteger)blockSizeOfSymmetricAlhorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm {
- switch (symmetricAlgorithm) {
- case PGPSymmetricIDEA:
- return IDEA_BLOCK;
- case PGPSymmetricTripleDES:
- return kCCBlockSize3DES;
- case PGPSymmetricCAST5:
- return kCCBlockSizeCAST;
- case PGPSymmetricBlowfish:
- return kCCBlockSizeBlowfish; // 64bit
- case PGPSymmetricAES128:
- case PGPSymmetricAES192:
- case PGPSymmetricAES256:
- return kCCBlockSizeAES128;
- case PGPSymmetricTwofish256:
- return 16; // 128bit
- default:
- break;
- }
- return NSNotFound;
-}
-
-+ (NSUInteger)keySizeOfSymmetricAlgorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm {
- switch (symmetricAlgorithm) {
- case PGPSymmetricIDEA:
- return IDEA_KEY_LENGTH;
- case PGPSymmetricTripleDES:
- return kCCKeySize3DES; // 24 or 8 ?
- case PGPSymmetricCAST5:
- return kCCKeySizeMaxCAST;
- case PGPSymmetricBlowfish:
- return kCCKeySizeMaxBlowfish; // 16 bit (?)
- case PGPSymmetricAES128:
- return kCCKeySizeAES128;
- case PGPSymmetricAES192:
- return kCCKeySizeAES192;
- case PGPSymmetricAES256:
- return kCCKeySizeAES256;
- case PGPSymmetricTwofish256:
- return 32;
- default:
- break;
- }
- return NSNotFound;
-}
-
-+ (NSUInteger)hashSizeOfHashAlhorithm:(PGPHashAlgorithm)hashAlgorithm {
- switch (hashAlgorithm) {
- case PGPHashMD5:
- return CC_MD5_DIGEST_LENGTH;
- case PGPHashSHA1:
- return CC_SHA1_DIGEST_LENGTH;
- case PGPHashSHA224:
- return CC_SHA224_DIGEST_LENGTH;
- case PGPHashSHA256:
- return CC_SHA256_DIGEST_LENGTH;
- case PGPHashSHA384:
- return CC_SHA384_DIGEST_LENGTH;
- case PGPHashSHA512:
- return CC_SHA512_DIGEST_LENGTH;
- case PGPHashRIPEMD160:
- return RIPEMD160_DIGEST_LENGTH; // confirm RIPE/MD 160 value
- default:
- break;
- }
- return NSNotFound;
-}
-
-+ (NSData *)randomData:(NSUInteger)length {
- let data = [NSMutableData dataWithLength:length];
- int status = SecRandomCopyBytes(kSecRandomDefault, length, data.mutableBytes);
- NSAssert(status == errSecSuccess, @"Failed to generate secure random bytes");
- return data;
-}
-
-+ (nullable NSData *)decrypt:(NSData *)data usingSecretKeyPacket:(PGPSecretKeyPacket *)keyPacket {
- PGPAssertClass(data, NSData);
-
- switch (keyPacket.publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // return decrypted m
- return [PGPRSA privateDecrypt:data withSecretKeyPacket:keyPacket];
- } break;
- default:
- // TODO: add algorithms
- [NSException raise:@"PGPNotSupported" format:@"Algorithm not supported"];
- break;
- }
- return nil;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPDSA.m b/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPDSA.m
deleted file mode 100755
index bb86f0bc37c767789f64aae43ee9193689ac7dae..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPDSA.m
+++ /dev/null
@@ -1,158 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPDSA.h"
-#import "PGPMPI.h"
-#import "PGPPKCSEmsa.h"
-#import "PGPPartialKey.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPBigNum+Private.h"
-#import "PGPKey.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-#import <openssl/err.h>
-#import <openssl/ssl.h>
-
-#import <openssl/bn.h>
-#import <openssl/dsa.h>
-#import <openssl/ecdsa.h>
-
-#import <Security/Security.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPDSA
-
-+ (BOOL)verify:(NSData *)toVerify signature:(PGPSignaturePacket *)signaturePacket withPublicKeyPacket:(PGPPublicKeyPacket *)publicKeyPacket {
- DSA_SIG *sig = DSA_SIG_new();
- pgp_defer { if (sig) { DSA_SIG_free(sig); } };
-
- DSA *dsa = DSA_new();
- pgp_defer { if (dsa) { DSA_free(dsa); } };
-
- if (!dsa || !sig) {
- return NO;
- }
-
- dsa->p = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_P] bigNum] bignumRef]);
- dsa->q = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_Q] bigNum] bignumRef]);
- dsa->g = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_G] bigNum] bignumRef]);
- dsa->pub_key = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_Y] bigNum] bignumRef]);
-
- sig->r = BN_dup([[[signaturePacket signatureMPI:PGPMPI_R] bigNum] bignumRef]);
- sig->s = BN_dup([[[signaturePacket signatureMPI:PGPMPI_S] bigNum] bignumRef]);
-
- if (!dsa->p || !dsa->q || !dsa->g || !dsa->pub_key || sig->r || sig->s) {
- PGPLogError(@"Missing DSA values.");
- return NO;
- }
-
- var hashLen = toVerify.length;
- unsigned int qlen = 0;
- if ((qlen = (unsigned int)BN_num_bytes(dsa->q)) < hashLen) {
- hashLen = qlen;
- }
-
- if (DSA_do_verify(toVerify.bytes, (int)hashLen, sig, dsa) < 0) {
- ERR_load_crypto_strings();
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- pgp_defer { if (errBuf) { free(errBuf); } };
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- return NO;
- }
-
- dsa->p = dsa->q = dsa->g = dsa->pub_key = NULL;
- sig->r = sig->s = NULL;
- return YES;
-}
-
-+ (NSArray<PGPMPI *> *)sign:(NSData *)toSign key:(PGPKey *)key {
- DSA *dsa = DSA_new();
- pgp_defer { if (dsa) { DSA_free(dsa); } };
-
- if (!dsa) {
- return @[];
- }
-
- let signingKeyPacket = key.signingSecretKey;
- let publicKeyPacket = PGPCast(key.publicKey.primaryKeyPacket, PGPPublicKeyPacket);
-
- dsa->p = BN_dup([publicKeyPacket publicMPI:PGPMPI_P].bigNum.bignumRef);
- dsa->q = BN_dup([publicKeyPacket publicMPI:PGPMPI_Q].bigNum.bignumRef);
- dsa->g = BN_dup([publicKeyPacket publicMPI:PGPMPI_G].bigNum.bignumRef);
- dsa->pub_key = BN_dup([publicKeyPacket publicMPI:PGPMPI_Y].bigNum.bignumRef);
- dsa->priv_key = BN_dup([signingKeyPacket secretMPI:PGPMPI_X].bigNum.bignumRef);
-
- DSA_SIG * _Nullable sig = DSA_do_sign(toSign.bytes, (int)toSign.length, dsa);
- if (!sig) {
- ERR_load_crypto_strings();
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- pgp_defer { if (errBuf) { free(errBuf); } };
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- return @[];
- }
-
- let MPI_R = [[PGPMPI alloc] initWithBigNum:[[PGPBigNum alloc] initWithBIGNUM:sig->r] identifier:PGPMPI_R];
- let MPI_S = [[PGPMPI alloc] initWithBigNum:[[PGPBigNum alloc] initWithBIGNUM:sig->s] identifier:PGPMPI_S];
-
- dsa->p = dsa->q = dsa->g = dsa->pub_key = dsa->priv_key = NULL;
-
- return @[MPI_R, MPI_S];
-}
-
-
-#pragma mark - Generate
-
-+ (nullable PGPKeyMaterial *)generateNewKeyMPIArray:(const int)bits {
- BN_CTX *ctx = BN_CTX_new();
- pgp_defer { if (ctx) { BN_CTX_free(ctx); } };
- DSA *dsa = DSA_new();
- pgp_defer { if (dsa) { DSA_free(dsa); } };
-
- DSA_generate_parameters_ex(dsa, bits, NULL, 0, NULL, NULL, NULL);
- if (DSA_generate_key(dsa) != 1) {
- return nil;
- }
-
- let bigP = [[PGPBigNum alloc] initWithBIGNUM:dsa->p];
- let bigQ = [[PGPBigNum alloc] initWithBIGNUM:dsa->q];
- let bigG = [[PGPBigNum alloc] initWithBIGNUM:dsa->g];
- let bigR = [[PGPBigNum alloc] initWithBIGNUM:dsa->r];
- let bigX = [[PGPBigNum alloc] initWithBIGNUM:dsa->priv_key];
- let bigY = [[PGPBigNum alloc] initWithBIGNUM:dsa->pub_key];
-
- let mpiP = [[PGPMPI alloc] initWithBigNum:bigP identifier:PGPMPI_P];
- let mpiQ = [[PGPMPI alloc] initWithBigNum:bigQ identifier:PGPMPI_Q];
- let mpiG = [[PGPMPI alloc] initWithBigNum:bigG identifier:PGPMPI_G];
- let mpiR = [[PGPMPI alloc] initWithBigNum:bigR identifier:PGPMPI_R];
- let mpiX = [[PGPMPI alloc] initWithBigNum:bigX identifier:PGPMPI_X];
- let mpiY = [[PGPMPI alloc] initWithBigNum:bigY identifier:PGPMPI_Y];
-
- let keyMaterial = [[PGPKeyMaterial alloc] init];
- keyMaterial.p = mpiP;
- keyMaterial.q = mpiQ;
- keyMaterial.g = mpiG;
- keyMaterial.r = mpiR;
- keyMaterial.x = mpiX;
- keyMaterial.y = mpiY;
-
- return keyMaterial;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPKeyMaterial.m b/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPKeyMaterial.m
deleted file mode 100755
index 56b6eae84e98ea24fb0bc92ca03a244085d9aa25..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPKeyMaterial.m
+++ /dev/null
@@ -1,13 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPKeyMaterial.h"
-
-@implementation PGPKeyMaterial
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPRSA.m b/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPRSA.m
deleted file mode 100755
index 4d090e994a211940f29727133ad3e6f9661df12d..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/PGPRSA.m
+++ /dev/null
@@ -1,272 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPRSA.h"
-#import "PGPMPI.h"
-#import "PGPPKCSEmsa.h"
-#import "PGPPartialKey.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPBigNum+Private.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-#import <openssl/err.h>
-#import <openssl/ssl.h>
-
-#import <openssl/bn.h>
-#import <openssl/rsa.h>
-
-#import <Security/Security.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPRSA
-
-// encrypts the bytes
-+ (nullable NSData *)publicEncrypt:(NSData *)toEncrypt withPublicKeyPacket:(PGPPublicKeyPacket *)publicKeyPacket {
- RSA *rsa = RSA_new();
- if (!rsa) {
- return nil;
- }
- pgp_defer { RSA_free(rsa); };
-
- rsa->n = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_N] bigNum] bignumRef]);
- rsa->e = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_E] bigNum] bignumRef]);
-
- NSAssert(rsa->n && rsa->e, @"Missing N or E");
- if (!rsa->n || !rsa->e) {
- return nil;
- }
-
- uint8_t *encrypted_em = calloc((size_t)BN_num_bytes(rsa->n) & SIZE_T_MAX, 1);
- pgp_defer { free(encrypted_em); };
- int em_len = RSA_public_encrypt(toEncrypt.length & INT_MAX, toEncrypt.bytes, encrypted_em, rsa, RSA_NO_PADDING);
- if (em_len == -1 || em_len != (publicKeyPacket.keySize & INT_MAX)) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
- return nil;
- }
-
- // decrypted encoded EME
- NSData *encryptedEm = [NSData dataWithBytes:encrypted_em length:em_len];
-
- rsa->n = rsa->e = NULL;
- return encryptedEm;
-}
-
-// decrypt bytes
-+ (nullable NSData *)privateDecrypt:(NSData *)toDecrypt withSecretKeyPacket:(PGPSecretKeyPacket *)secretKeyPacket {
- RSA *rsa = RSA_new();
- if (!rsa) {
- return nil;
- }
- pgp_defer { RSA_free(rsa); };
-
- rsa->n = BN_dup([[[secretKeyPacket publicMPI:PGPMPI_N] bigNum] bignumRef]);
- rsa->e = BN_dup([[[secretKeyPacket publicMPI:PGPMPI_E] bigNum] bignumRef]);
-
- rsa->d = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_D] bigNum] bignumRef]);
- rsa->p = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_Q] bigNum] bignumRef]); /* p and q are round the other way in openssl */
- rsa->q = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_P] bigNum] bignumRef]);
-
- if (rsa->d == NULL) {
- return nil;
- }
-
- if (RSA_check_key(rsa) != 1) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
-
- ERR_free_strings();
- return nil;
- }
-
- uint8_t *outbuf = calloc(RSA_size(rsa) & SIZE_T_MAX, 1);
- pgp_defer { free(outbuf); };
- int t = RSA_private_decrypt(toDecrypt.length & INT_MAX, toDecrypt.bytes, outbuf, rsa, RSA_NO_PADDING);
- if (t == -1) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
-
- ERR_free_strings();
- return nil;
- }
-
- NSData *decryptedData = [NSData dataWithBytes:outbuf length:t];
- NSAssert(decryptedData, @"Missing data");
-
- rsa->n = rsa->d = rsa->p = rsa->q = rsa->e = NULL;
-
- return decryptedData;
-}
-
-// sign
-+ (nullable NSData *)privateEncrypt:(NSData *)toEncrypt withSecretKeyPacket:(PGPSecretKeyPacket *)secretKeyPacket {
- let rsa = RSA_new();
- if (!rsa) {
- return nil;
- }
- pgp_defer { RSA_free(rsa); };
-
- rsa->n = BN_dup([[[secretKeyPacket publicMPI:PGPMPI_N] bigNum] bignumRef]);
- rsa->d = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_D] bigNum] bignumRef]);
- rsa->p = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_Q] bigNum] bignumRef]); /* p and q are round the other way in openssl */
- rsa->q = BN_dup([[[secretKeyPacket secretMPI:PGPMPI_P] bigNum] bignumRef]);
- rsa->e = BN_dup([[[secretKeyPacket publicMPI:PGPMPI_E] bigNum] bignumRef]);
-
- if (toEncrypt.length > secretKeyPacket.keySize) {
- return nil;
- }
-
- /* If this isn't set, it's very likely that the programmer hasn't */
- /* decrypted the secret key. RSA_check_key segfaults in that case. */
- if (rsa->d == NULL) {
- return nil;
- }
-
- if (RSA_check_key(rsa) != 1) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
-
- ERR_free_strings();
- return nil;
- }
-
- uint8_t *outbuf = calloc(RSA_size(rsa) & SIZE_T_MAX, 1);
- pgp_defer { free(outbuf); };
-
- int t = RSA_private_encrypt(toEncrypt.length & INT_MAX, (UInt8 *)toEncrypt.bytes, outbuf, rsa, RSA_NO_PADDING);
- if (t == -1) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
-
- ERR_free_strings();
- return nil;
- }
-
- NSData *encryptedData = [NSData dataWithBytes:outbuf length:t];
- NSAssert(encryptedData, @"Missing calculated data");
-
- rsa->n = rsa->d = rsa->p = rsa->q = rsa->e = NULL;
-
- return encryptedData;
-}
-
-// recovers the message digest
-+ (nullable NSData *)publicDecrypt:(NSData *)toDecrypt withPublicKeyPacket:(PGPPublicKeyPacket *)publicKeyPacket {
- RSA *rsa = RSA_new();
- if (!rsa) {
- return nil;
- }
- pgp_defer { RSA_free(rsa); };
-
- rsa->n = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_N] bigNum] bignumRef]);
- rsa->e = BN_dup([[[publicKeyPacket publicMPI:PGPMPI_E] bigNum] bignumRef]);
-
- NSAssert(rsa->n && rsa->e, @"Missing N or E");
- if (!rsa->n || !rsa->e) {
- return nil;
- }
-
- uint8_t *decrypted_em = calloc(RSA_size(rsa) & SIZE_T_MAX, 1); // RSA_size(rsa) - 11
- pgp_defer { free(decrypted_em); };
- int em_len = RSA_public_decrypt(toDecrypt.length & INT_MAX, toDecrypt.bytes, decrypted_em, rsa, RSA_NO_PADDING);
- if (em_len == -1 || em_len != (publicKeyPacket.keySize & INT_MAX)) {
- ERR_load_crypto_strings();
-
- unsigned long err_code = ERR_get_error();
- char *errBuf = calloc(512, sizeof(char));
- ERR_error_string(err_code, errBuf);
- PGPLogDebug(@"%@", [NSString stringWithCString:errBuf encoding:NSASCIIStringEncoding]);
- free(errBuf);
-
- return nil;
- }
-
- // decrypted PKCS emsa
- let decryptedEm = [NSData dataWithBytes:decrypted_em length:em_len];
-
- rsa->n = rsa->e = NULL;
-
- return decryptedEm;
-}
-
-#pragma mark - Generate
-
-+ (nullable PGPKeyMaterial *)generateNewKeyMPIArray:(const int)bits {
- BN_CTX *ctx = BN_CTX_new();
- RSA *rsa = RSA_new();
- BIGNUM *e = BN_new();
-
- pgp_defer {
- BN_CTX_free(ctx);
- BN_clear_free(e);
- RSA_free(rsa);
- };
-
- BN_set_word(e, 65537UL);
-
- if (RSA_generate_key_ex(rsa, bits, e, NULL) != 1) {
- return nil;
- }
-
- let bigN = [[PGPBigNum alloc] initWithBIGNUM:rsa->n];
- let bigE = [[PGPBigNum alloc] initWithBIGNUM:rsa->e];
- let bigD = [[PGPBigNum alloc] initWithBIGNUM:rsa->d];
- let bigP = [[PGPBigNum alloc] initWithBIGNUM:rsa->p];
- let bigQ = [[PGPBigNum alloc] initWithBIGNUM:rsa->q];
- let bigU = [[PGPBigNum alloc] initWithBIGNUM:BN_mod_inverse(NULL, rsa->p, rsa->q, ctx)];
-
- let mpiN = [[PGPMPI alloc] initWithBigNum:bigN identifier:PGPMPI_N];
- let mpiE = [[PGPMPI alloc] initWithBigNum:bigE identifier:PGPMPI_E];
- let mpiD = [[PGPMPI alloc] initWithBigNum:bigD identifier:PGPMPI_D];
- let mpiP = [[PGPMPI alloc] initWithBigNum:bigP identifier:PGPMPI_P];
- let mpiQ = [[PGPMPI alloc] initWithBigNum:bigQ identifier:PGPMPI_Q];
- let mpiU = [[PGPMPI alloc] initWithBigNum:bigU identifier:PGPMPI_U];
-
- let keyMaterial = [[PGPKeyMaterial alloc] init];
- keyMaterial.n = mpiN;
- keyMaterial.e = mpiE;
- keyMaterial.d = mpiD;
- keyMaterial.p = mpiP;
- keyMaterial.q = mpiQ;
- keyMaterial.u = mpiU;
-
- return keyMaterial;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.c b/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.c
deleted file mode 100755
index a48cb38a2a94894e73ae413b116251059e037f70..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.c
+++ /dev/null
@@ -1,1691 +0,0 @@
-/*
- * Fast, portable, and easy-to-use Twofish implementation,
- * Version 0.3.
- * Copyright (c) 2002 by Niels Ferguson.
- * (See further down for the almost-unrestricted licensing terms.)
- *
- * --------------------------------------------------------------------------
- * There are two files for this implementation:
- * - twofish.h, the header file.
- * - twofish.c, the code file.
- *
- * To incorporate this code into your program you should:
- * - Check the licensing terms further down in this comment.
- * - Fix the two type definitions in twofish.h to suit your platform.
- * - Fix a few definitions in twofish.c in the section marked
- * PLATFORM FIXES. There is one important ones that affects
- * functionality, and then a few definitions that you can optimise
- * for efficiency but those have no effect on the functionality.
- * Don't change anything else.
- * - Put the code in your project and compile it.
- *
- * To use this library you should:
- * - Call Twofish_initialise() in your program before any other function in
- * this library.
- * - Use Twofish_prepare_key(...) to convert a key to internal form.
- * - Use Twofish_encrypt(...) and Twofish_decrypt(...) to encrypt and decrypt
- * data.
- * See the comments in the header file for details on these functions.
- * --------------------------------------------------------------------------
- *
- * There are many Twofish implementation available for free on the web.
- * Most of them are hard to integrate into your own program.
- * As we like people to use our cipher, I thought I would make it easier.
- * Here is a free and easy-to-integrate Twofish implementation in C.
- * The latest version is always available from my personal home page at
- * http://niels.ferguson.net/
- *
- * Integrating library code into a project is difficult because the library
- * header files interfere with the project's header files and code.
- * And of course the project's header files interfere with the library code.
- * I've tried to resolve these problems here.
- * The header file of this implementation is very light-weight.
- * It contains two typedefs, a structure, and a few function declarations.
- * All names it defines start with "Twofish_".
- * The header file is therefore unlikely to cause problems in your project.
- * The code file of this implementation doesn't need to include the header
- * files of the project. There is thus no danger of the project interfering
- * with all the definitions and macros of the Twofish code.
- * In most situations, all you need to do is fill in a few platform-specific
- * definitions in the header file and code file,
- * and you should be able to run the Twofish codevoid in your project.
- * I estimate it should take you less than an hour to integrate this code
- * into your project, most of it spent reading the comments telling you what
- * to do.
- *
- * For people using C++: it is very easy to wrap this library into a
- * TwofishKey class. One of the big advantages is that you can automate the
- * wiping of the key material in the destructor. I have not provided a C++
- * class because the interface depends too much on the abstract base class
- * you use for block ciphers in your program, which I don't know about.
- *
- * This implementation is designed for use on PC-class machines. It uses the
- * Twofish 'full' keying option which uses large tables. Total table size is
- * around 5-6 kB for static tables plus 4.5 kB for each pre-processed key.
- * If you need an implementation that uses less memory,
- * take a look at Brian Gladman's code on his web site:
- * http://fp.gladman.plus.com/cryptography_technology/aes/
- * He has code for all AES candidates.
- * His Twofish code has lots of options trading off table size vs. speed.
- * You can also take a look at the optimised code by Doug Whiting on the
- * Twofish web site
- * http://www.counterpane.com/twofish.html
- * which has loads of options.
- * I believe these existing implementations are harder to re-use because they
- * are not clean libraries and they impose requirements on the environment.
- * This implementation is very careful to minimise those,
- * and should be easier to integrate into any larger program.
- *
- * The default mode of this implementation is fully portable as it uses no
- * behaviour not defined in the C standard. (This is harder than you think.)
- * If you have any problems porting the default mode, please let me know
- * so that I can fix the problem. (But only if this code is at fault, I
- * don't fix compilers.)
- * Most of the platform fixes are related to non-portable but faster ways
- * of implementing certain functions.
- *
- * In general I've tried to make the code as fast as possible, at the expense
- * of memory and code size. However, C does impose limits, and this
- * implementation will be slower than an optimised assembler implementation.
- * But beware of assembler implementations: a good Pentium implementation
- * uses completely different code than a good Pentium II implementation.
- * You basically have to re-write the assembly code for every generation of
- * processor. Unless you are severely pressed for speed, stick with C.
- *
- * The initialisation routine of this implementation contains a self-test.
- * If initialisation succeeds without calling the fatal routine, then
- * the implementation works. I don't think you can break the implementation
- * in such a way that it still passes the tests, unless you are malicious.
- * In other words: if the initialisation routine returns,
- * you have successfully ported the implementation.
- * (Or not implemented the fatal routine properly, but that is your problem.)
- *
- * I'm indebted to many people who helped me in one way or another to write
- * this code. During the design of Twofish and the AES process I had very
- * extensive discussions of all implementation issues with various people.
- * Doug Whiting in particular provided a wealth of information. The Twofish
- * team spent untold hours discussion various cipher features, and their
- * implementation. Brian Gladman implemented all AES candidates in C,
- * and we had some fruitful discussions on how to implement Twofish in C.
- * Jan Nieuwenhuizen tested this code on Linux using GCC.
- *
- * Now for the license:
- * The author hereby grants a perpetual license to everybody to
- * use this code for any purpose as long as the copyright message is included
- * in the source code of this or any derived work.
- *
- * Yes, this means that you, your company, your club, and anyone else
- * can use this code anywhere you want. You can change it and distribute it
- * under the GPL, include it in your commercial product without releasing
- * the source code, put it on the web, etc.
- * The only thing you cannot do is remove my copyright message,
- * or distribute any source code based on this implementation that does not
- * include my copyright message.
- *
- * I appreciate a mention in the documentation or credits,
- * but I understand if that is difficult to do.
- * I also appreciate it if you tell me where and why you used my code.
- *
- * Please send any questions or comments to niels@ferguson.net
- *
- * Have Fun!
- *
- * Niels
- */
-
-/*
- * DISCLAIMER: As I'm giving away my work for free, I'm of course not going
- * to accept any liability of any form. This code, or the Twofish cipher,
- * might very well be flawed; you have been warned.
- * This software is provided as-is, without any kind of warrenty or
- * guarantee. And that is really all you can expect when you download
- * code for free from the Internet.
- *
- * I think it is really sad that disclaimers like this seem to be necessary.
- * If people only had a little bit more common sense, and didn't come
- * whining like little children every time something happens....
- */
-
-/*
- * Version history:
- * Version 0.0, 2002-08-30
- * First written.
- * Version 0.1, 2002-09-03
- * Added disclaimer. Improved self-tests.
- * Version 0.2, 2002-09-09
- * Removed last non-portabilities. Default now works completely within
- * the C standard. UInt32 can be larger than 32 bits without problems.
- * Version 0.3, 2002-09-28
- * Bugfix: use <string.h> instead of <memory.h> to adhere to ANSI/ISO.
- * Rename BIG_ENDIAN macro to CPU_IS_BIG_ENDIAN. The gcc library
- * header <string.h> already defines BIG_ENDIAN, even though it is not
- * supposed to.
- */
-
-
-/*
- * Minimum set of include files.
- * You should not need any application-specific include files for this code.
- * In fact, adding you own header files could break one of the many macros or
- * functions in this file. Be very careful.
- * Standard include files will probably be ok.
- */
-#include <string.h> /* for memset(), memcpy(), and memcmp() */
-#include "twofish.h"
-
-
-/*
- * PLATFORM FIXES
- * ==============
- *
- * Fix the type definitions in twofish.h first!
- *
- * The following definitions have to be fixed for each particular platform
- * you work on. If you have a multi-platform program, you no doubt have
- * portable definitions that you can substitute here without changing the
- * rest of the code.
- */
-
-
-/*
- * Function called if something is fatally wrong with the implementation.
- * This fatal function is called when a coding error is detected in the
- * Twofish implementation, or when somebody passes an obviously erroneous
- * parameter to this implementation. There is not much you can do when
- * the code contains bugs, so we just stop.
- *
- * The argument is a string. Ideally the fatal function prints this string
- * as an error message. Whatever else this function does, it should never
- * return. A typical implementation would stop the program completely after
- * printing the error message.
- *
- * This default implementation is not very useful,
- * but does not assume anything about your environment.
- * It will at least let you know something is wrong....
- * I didn't want to include any libraries to print and error or so,
- * as this makes the code much harder to integrate in a project.
- *
- * Note that the Twofish_fatal function may not return to the caller.
- * Unfortunately this is not something the self-test can test for,
- * so you have to make sure of this yourself.
- *
- * If you want to call an external function, be careful about including
- * your own header files here. This code uses a lot of macros, and your
- * header file could easily break it. Maybe the best solution is to use
- * a separate extern statement for your fatal function.
- */
-#define Twofish_fatal( msg ) {for(;;);}
-
-
-/*
- * The rest of the settings are not important for the functionality
- * of this Twofish implementation. That is, their default settings
- * work on all platforms. You can change them to improve the
- * speed of the implementation on your platform. Erroneous settings
- * will result in erroneous implementations, but the self-test should
- * catch those.
- */
-
-
-/*
- * Macros to rotate a Twofish_UInt32 value left or right by the
- * specified number of bits. This should be a 32-bit rotation,
- * and not rotation of, say, 64-bit values.
- *
- * Every encryption or decryption operation uses 32 of these rotations,
- * so it is a good idea to make these macros efficient.
- *
- * This fully portable definition has one piece of tricky stuff.
- * The UInt32 might be larger than 32 bits, so we have to mask
- * any higher bits off. The simplest way to do this is to 'and' the
- * value first with 0xffffffff and then shift it right. An optimising
- * compiler that has a 32-bit type can optimise this 'and' away.
- *
- * Unfortunately there is no portable way of writing the constant
- * 0xffffffff. You don't know which suffix to use (U, or UL?)
- * The UINT32_MASK definition uses a bit of trickery. Shift-left
- * is only defined if the shift amount is strictly less than the size
- * of the UInt32, so we can't use (1<<32). The answer it to take the value
- * 2, cast it to a UInt32, shift it left 31 positions, and subtract one.
- * Another example of how to make something very simple extremely difficult.
- * I hate C.
- *
- * The rotation macros are straightforward.
- * They are only applied to UInt32 values, which are _unsigned_
- * so the >> operator must do a logical shift that brings in zeroes.
- * On most platforms you will only need to optimise the ROL32 macro; the
- * ROR32 macro is not inefficient on an optimising compiler as all rotation
- * amounts in this code are known at compile time.
- *
- * On many platforms there is a faster solution.
- * For example, MS compilers have the __rotl and __rotr functions
- * that generate x86 rotation instructions.
- */
-#define UINT32_MASK ( (((UInt32)2)<<31) - 1 )
-#define ROL32( x, n ) ( (x)<<(n) | ((x) & UINT32_MASK) >> (32-(n)) )
-#define ROR32( x, n ) ROL32( (x), 32-(n) )
-
-
-/*
- * Select data type for q-table entries.
- *
- * Larger entry types cost more memory (1.5 kB), and might be faster
- * or slower depending on the CPU and compiler details.
- *
- * This choice only affects the static data size and the key setup speed.
- * Functionality, expanded key size, or encryption speed are not affected.
- * Define to 1 to get large q-table entries.
- */
-#define LARGE_Q_TABLE 0 /* default = 0 */
-
-
-/*
- * Method to select a single byte from a UInt32.
- * WARNING: non-portable code if set; might not work on all platforms.
- *
- * Inside the inner loop of Twofish it is necessary to access the 4
- * individual bytes of a UInt32. This can be done using either shifts
- * and masks, or memory accesses.
- *
- * Set to 0 to use shift and mask operations for the byte selection.
- * This is more ALU intensive. It is also fully portable.
- *
- * Set to 1 to use memory accesses. The UInt32 is stored in memory and
- * the individual bytes are read from memory one at a time.
- * This solution is more memory-intensive, and not fully portable.
- * It might be faster on your platform, or not. If you use this option,
- * make sure you set the CPU_IS_BIG_ENDIAN flag appropriately.
- *
- * This macro does not affect the conversion of the inputs and outputs
- * of the cipher. See the CONVERT_USING_CASTS macro for that.
- */
-#define SELECT_BYTE_FROM_UINT32_IN_MEMORY 0 /* default = 0 */
-
-
-/*
- * Method used to read the input and write the output.
- * WARNING: non-portable code if set; might not work on all platforms.
- *
- * Twofish operates on 32-bit words. The input to the cipher is
- * a byte array, as is the output. The portable method of doing the
- * conversion is a bunch of rotate and mask operations, but on many
- * platforms it can be done faster using a cast.
- * This only works if your CPU allows UInt32 accesses to arbitrary Byte
- * addresses.
- *
- * Set to 0 to use the shift and mask operations. This is fully
- * portable. .
- *
- * Set to 1 to use a cast. The Byte * is cast to a UInt32 *, and a
- * UInt32 is read. If necessary (as indicated by the CPU_IS_BIG_ENDIAN
- * macro) the byte order in the UInt32 is swapped. The reverse is done
- * to write the output of the encryption/decryption. Make sure you set
- * the CPU_IS_BIG_ENDIAN flag appropriately.
- * This option does not work unless a UInt32 is exactly 32 bits.
- *
- * This macro only changes the reading/writing of the plaintext/ciphertext.
- * See the SELECT_BYTE_FROM_UINT32_IN_MEMORY to affect the way in which
- * a UInt32 is split into 4 bytes for the S-box selection.
- */
-#define CONVERT_USING_CASTS 0 /* default = 0 */
-
-
-/*
- * Endianness switch.
- * Only relevant if SELECT_BYTE_FROM_UINT32_IN_MEMORY or
- * CONVERT_USING_CASTS is set.
- *
- * Set to 1 on a big-endian machine, and to 0 on a little-endian machine.
- * Twofish uses the little-endian convention (least significant byte first)
- * and big-endian machines (using most significant byte first)
- * have to do a few conversions.
- *
- * CAUTION: This code has never been tested on a big-endian machine,
- * because I don't have access to one. Feedback appreciated.
- */
-#define CPU_IS_BIG_ENDIAN 0
-
-
-/*
- * Macro to reverse the order of the bytes in a UInt32.
- * Used to convert to little-endian on big-endian machines.
- * This macro is always tested, but only used in the encryption and
- * decryption if CONVERT_USING_CASTS, and CPU_IS_BIG_ENDIAN
- * are both set. In other words: this macro is only speed-critical if
- * both these flags have been set.
- *
- * This default definition of SWAP works, but on many platforms there is a
- * more efficient implementation.
- */
-#define BSWAP(x) ((ROL32((x),8) & 0x00ff00ff) | (ROR32((x),8) & 0xff00ff00))
-
-
-/*
- * END OF PLATFORM FIXES
- * =====================
- *
- * You should not have to touch the rest of this file.
- */
-
-
-/*
- * Convert the external type names to some that are easier to use inside
- * this file. I didn't want to use the names Byte and UInt32 in the
- * header file, because many programs already define them and using two
- * conventions at once can be very difficult.
- * Don't change these definitions! Change the originals
- * in twofish.h instead.
- */
-/* A Byte must be an unsigned integer, 8 bits long. */
-typedef Twofish_Byte Byte;
-/* A UInt32 must be an unsigned integer at least 32 bits long. */
-typedef Twofish_UInt32 UInt32;
-
-
-/*
- * Define a macro ENDIAN_CONVERT.
- *
- * We define a macro ENDIAN_CONVERT that performs a BSWAP on big-endian
- * machines, and is the identity function on little-endian machines.
- * The code then uses this macro without considering the endianness.
- */
-#if CPU_IS_BIG_ENDIAN
-#define ENDIAN_CONVERT(x) BSWAP(x)
-#else
-#define ENDIAN_CONVERT(x) (x)
-#endif
-
-
-/*
- * Compute byte offset within a UInt32 stored in memory.
- *
- * This is only used when SELECT_BYTE_FROM_UINT32_IN_MEMORY is set.
- *
- * The input is the byte number 0..3, 0 for least significant.
- * Note the use of sizeof() to support UInt32 types that are larger
- * than 4 bytes.
- */
-#if CPU_IS_BIG_ENDIAN
-#define BYTE_OFFSET( n ) (sizeof(UInt32) - 1 - (n) )
-#else
-#define BYTE_OFFSET( n ) (n)
-#endif
-
-
-/*
- * Macro to get Byte no. b from UInt32 value X.
- * We use two different definition, depending on the settings.
- */
-#if SELECT_BYTE_FROM_UINT32_IN_MEMORY
- /* Pick the byte from the memory in which X is stored. */
-#define SELECT_BYTE( X, b ) (((Byte *)(&(X)))[BYTE_OFFSET(b)])
-#else
- /* Portable solution: Pick the byte directly from the X value. */
-#define SELECT_BYTE( X, b ) (((X) >> 8*(b)) & 0xff)
-#endif
-
-
-/* Some shorthands because we use byte selection in large formulae. */
-#define b0(X) SELECT_BYTE((X),0)
-#define b1(X) SELECT_BYTE((X),1)
-#define b2(X) SELECT_BYTE((X),2)
-#define b3(X) SELECT_BYTE((X),3)
-
-
-/*
- * We need macros to load and store UInt32 from/to byte arrays
- * using the least-significant-byte-first convention.
- *
- * GET32( p ) gets a UInt32 in lsb-first form from four bytes pointed to
- * by p.
- * PUT32( v, p ) writes the UInt32 value v at address p in lsb-first form.
- */
-#if CONVERT_USING_CASTS
-
- /* Get UInt32 from four bytes pointed to by p. */
-#define GET32( p ) ENDIAN_CONVERT( *((UInt32 *)(p)) )
- /* Put UInt32 into four bytes pointed to by p */
-#define PUT32( v, p ) *((UInt32 *)(p)) = ENDIAN_CONVERT(v)
-
-#else
-
- /* Get UInt32 from four bytes pointed to by p. */
-#define GET32( p ) \
- ( \
- (UInt32)((p)[0]) \
- | (UInt32)((p)[1])<< 8\
- | (UInt32)((p)[2])<<16\
- | (UInt32)((p)[3])<<24\
- )
- /* Put UInt32 into four bytes pointed to by p */
-#define PUT32( v, p ) \
- (p)[0] = (Byte)(((v) ) & 0xff);\
- (p)[1] = (Byte)(((v) >> 8) & 0xff);\
- (p)[2] = (Byte)(((v) >> 16) & 0xff);\
- (p)[3] = (Byte)(((v) >> 24) & 0xff)
-
-#endif
-
-
-/*
- * Test the platform-specific macros.
- * This function tests the macros defined so far to make sure the
- * definitions are appropriate for this platform.
- * If you make any mistake in the platform configuration, this should detect
- * that and inform you what went wrong.
- * Somewhere, someday, this is going to save somebody a lot of time,
- * because misbehaving macros are hard to debug.
- */
-static void test_platform()
- {
- /* Buffer with test values. */
- Byte buf[] = {0x12, 0x34, 0x56, 0x78, 0x9a, 0xbc, 0xde, 0};
- UInt32 C;
- UInt32 x,y;
- int i;
-
- /*
- * Some sanity checks on the types that can't be done in compile time.
- * A smart compiler will just optimise these tests away.
- * The pre-processor doesn't understand different types, so we cannot
- * do these checks in compile-time.
- *
- * I hate C.
- *
- * The first check in each case is to make sure the size is correct.
- * The second check is to ensure that it is an unsigned type.
- */
- if( ((UInt32) ((UInt32)1 << 31) == 0) || ((UInt32)-1 < 0) )
- {
- Twofish_fatal( "Twofish code: Twofish_UInt32 type not suitable" );
- }
- if( (sizeof( Byte ) != 1) || ((Byte)-1 < 0) )
- {
- Twofish_fatal( "Twofish code: Twofish_Byte type not suitable" );
- }
-
- /*
- * Sanity-check the endianness conversions.
- * This is just an aid to find problems. If you do the endianness
- * conversion macros wrong you will fail the full cipher test,
- * but that does not help you find the error.
- * Always make it easy to find the bugs!
- *
- * Detail: There is no fully portable way of writing UInt32 constants,
- * as you don't know whether to use the U or UL suffix. Using only U you
- * might only be allowed 16-bit constants. Using UL you might get 64-bit
- * constants which cannot be stored in a UInt32 without warnings, and
- * which generally behave subtly different from a true UInt32.
- * As long as we're just comparing with the constant,
- * we can always use the UL suffix and at worst lose some efficiency.
- * I use a separate '32-bit constant' macro in most of my other code.
- *
- * I hate C.
- *
- * Start with testing GET32. We test it on all positions modulo 4
- * to make sure we can handly any position of inputs. (Some CPUs
- * do not allow non-aligned accesses which we would do if you used
- * the CONVERT_USING_CASTS option.
- */
- if( GET32( buf ) != 0x78563412UL || GET32(buf+1) != 0x9a785634UL
- || GET32( buf+2 ) != 0xbc9a7856UL || GET32(buf+3) != 0xdebc9a78UL )
- {
- Twofish_fatal( "Twofish code: GET32 not implemented properly" );
- }
-
- /*
- * We can now use GET32 to test PUT32.
- * We don't test the shifted versions. If GET32 can do that then
- * so should PUT32.
- */
- C = GET32( buf );
- PUT32( 3*C, buf );
- if( GET32( buf ) != 0x69029c36UL )
- {
- Twofish_fatal( "Twofish code: PUT32 not implemented properly" );
- }
-
-
- /* Test ROL and ROR */
- for( i=1; i<32; i++ )
- {
- /* Just a simple test. */
- x = ROR32( C, i );
- y = ROL32( C, i );
- x ^= (C>>i) ^ (C<<(32-i));
- y ^= (C<<i) ^ (C>>(32-i));
- x |= y;
- /*
- * Now all we check is that x is zero in the least significant
- * 32 bits. Using the UL suffix is safe here, as it doesn't matter
- * if we get a larger type.
- */
- if( (x & 0xffffffffUL) != 0 )
- {
- Twofish_fatal( "Twofish ROL or ROR not properly defined." );
- }
- }
-
- /* Test the BSWAP macro */
- if( (BSWAP(C)) != 0x12345678UL )
- {
- /*
- * The BSWAP macro should always work, even if you are not using it.
- * A smart optimising compiler will just remove this entire test.
- */
- Twofish_fatal( "BSWAP not properly defined." );
- }
-
- /* And we can test the b<i> macros which use SELECT_BYTE. */
- if( (b0(C)!=0x12) || (b1(C) != 0x34) || (b2(C) != 0x56) || (b3(C) != 0x78) )
- {
- /*
- * There are many reasons why this could fail.
- * Most likely is that CPU_IS_BIG_ENDIAN has the wrong value.
- */
- Twofish_fatal( "Twofish code: SELECT_BYTE not implemented properly" );
- }
- }
-
-
-/*
- * Finally, we can start on the Twofish-related code.
- * You really need the Twofish specifications to understand this code. The
- * best source is the Twofish book:
- * "The Twofish Encryption Algorithm", by Bruce Schneier, John Kelsey,
- * Doug Whiting, David Wagner, Chris Hall, and Niels Ferguson.
- * you can also use the AES submission document of Twofish, which is
- * available from my list of publications on my personal web site at
- * http://niels.ferguson.net/.
- *
- * The first thing we do is write the testing routines. This is what the
- * implementation has to satisfy in the end. We only test the external
- * behaviour of the implementation of course.
- */
-
-
-/*
- * Perform a single self test on a (plaintext,ciphertext,key) triple.
- * Arguments:
- * key array of key bytes
- * key_len length of key in bytes
- * p plaintext
- * c ciphertext
- */
-static void test_vector( Byte key[], int key_len, Byte p[16], Byte c[16] )
- {
- Byte tmp[16]; /* scratch pad. */
- Twofish_key xkey; /* The expanded key */
- int i;
-
-
- /* Prepare the key */
- Twofish_prepare_key( key, key_len, &xkey );
-
- /*
- * We run the test twice to ensure that the xkey structure
- * is not damaged by the first encryption.
- * Those are hideous bugs to find if you get them in an application.
- */
- for( i=0; i<2; i++ )
- {
- /* Encrypt and test */
- Twofish_encrypt( &xkey, p, tmp );
- if( memcmp( c, tmp, 16 ) != 0 )
- {
- Twofish_fatal( "Twofish encryption failure" );
- }
-
- /* Decrypt and test */
- Twofish_decrypt( &xkey, c, tmp );
- if( memcmp( p, tmp, 16 ) != 0 )
- {
- Twofish_fatal( "Twofish decryption failure" );
- }
- }
-
- /* The test keys are not secret, so we don't need to wipe xkey. */
- }
-
-
-/*
- * Check implementation using three (key,plaintext,ciphertext)
- * test vectors, one for each major key length.
- *
- * This is an absolutely minimal self-test.
- * This routine does not test odd-sized keys.
- */
-static void test_vectors()
- {
- /*
- * We run three tests, one for each major key length.
- * These test vectors come from the Twofish specification.
- * One encryption and one decryption using randomish data and key
- * will detect almost any error, especially since we generate the
- * tables ourselves, so we don't have the problem of a single
- * damaged table entry in the source.
- */
-
- /* 128-bit test is the I=3 case of section B.2 of the Twofish book. */
- static Byte k128[] = {
- 0x9F, 0x58, 0x9F, 0x5C, 0xF6, 0x12, 0x2C, 0x32,
- 0xB6, 0xBF, 0xEC, 0x2F, 0x2A, 0xE8, 0xC3, 0x5A,
- };
- static Byte p128[] = {
- 0xD4, 0x91, 0xDB, 0x16, 0xE7, 0xB1, 0xC3, 0x9E,
- 0x86, 0xCB, 0x08, 0x6B, 0x78, 0x9F, 0x54, 0x19
- };
- static Byte c128[] = {
- 0x01, 0x9F, 0x98, 0x09, 0xDE, 0x17, 0x11, 0x85,
- 0x8F, 0xAA, 0xC3, 0xA3, 0xBA, 0x20, 0xFB, 0xC3
- };
-
- /* 192-bit test is the I=4 case of section B.2 of the Twofish book. */
- static Byte k192[] = {
- 0x88, 0xB2, 0xB2, 0x70, 0x6B, 0x10, 0x5E, 0x36,
- 0xB4, 0x46, 0xBB, 0x6D, 0x73, 0x1A, 0x1E, 0x88,
- 0xEF, 0xA7, 0x1F, 0x78, 0x89, 0x65, 0xBD, 0x44
- };
- static Byte p192[] = {
- 0x39, 0xDA, 0x69, 0xD6, 0xBA, 0x49, 0x97, 0xD5,
- 0x85, 0xB6, 0xDC, 0x07, 0x3C, 0xA3, 0x41, 0xB2
- };
- static Byte c192[] = {
- 0x18, 0x2B, 0x02, 0xD8, 0x14, 0x97, 0xEA, 0x45,
- 0xF9, 0xDA, 0xAC, 0xDC, 0x29, 0x19, 0x3A, 0x65
- };
-
- /* 256-bit test is the I=4 case of section B.2 of the Twofish book. */
- static Byte k256[] = {
- 0xD4, 0x3B, 0xB7, 0x55, 0x6E, 0xA3, 0x2E, 0x46,
- 0xF2, 0xA2, 0x82, 0xB7, 0xD4, 0x5B, 0x4E, 0x0D,
- 0x57, 0xFF, 0x73, 0x9D, 0x4D, 0xC9, 0x2C, 0x1B,
- 0xD7, 0xFC, 0x01, 0x70, 0x0C, 0xC8, 0x21, 0x6F
- };
- static Byte p256[] = {
- 0x90, 0xAF, 0xE9, 0x1B, 0xB2, 0x88, 0x54, 0x4F,
- 0x2C, 0x32, 0xDC, 0x23, 0x9B, 0x26, 0x35, 0xE6
- };
- static Byte c256[] = {
- 0x6C, 0xB4, 0x56, 0x1C, 0x40, 0xBF, 0x0A, 0x97,
- 0x05, 0x93, 0x1C, 0xB6, 0xD4, 0x08, 0xE7, 0xFA
- };
-
- /* Run the actual tests. */
- test_vector( k128, 16, p128, c128 );
- test_vector( k192, 24, p192, c192 );
- test_vector( k256, 32, p256, c256 );
- }
-
-
-/*
- * Perform extensive test for a single key size.
- *
- * Test a single key size against the test vectors from section
- * B.2 in the Twofish book. This is a sequence of 49 encryptions
- * and decryptions. Each plaintext is equal to the ciphertext of
- * the previous encryption. The key is made up from the ciphertext
- * two and three encryptions ago. Both plaintext and key start
- * at the zero value.
- * We should have designed a cleaner recurrence relation for
- * these tests, but it is too late for that now. At least we learned
- * how to do it better next time.
- * For details see appendix B of the book.
- *
- * Arguments:
- * key_len Number of bytes of key
- * final_value Final plaintext value after 49 iterations
- */
-static void test_sequence( int key_len, Byte final_value[] )
- {
- Byte buf[ (50+3)*16 ]; /* Buffer to hold our computation values. */
- Byte tmp[16]; /* Temp for testing the decryption. */
- Twofish_key xkey; /* The expanded key */
- int i;
- Byte * p;
-
- /* Wipe the buffer */
- memset( buf, 0, sizeof( buf ) );
-
- /*
- * Because the recurrence relation is done in an inconvenient manner
- * we end up looping backwards over the buffer.
- */
-
- /* Pointer in buffer points to current plaintext. */
- p = &buf[50*16];
- for( i=1; i<50; i++ )
- {
- /*
- * Prepare a key.
- * This automatically checks that key_len is valid.
- */
- Twofish_prepare_key( p+16, key_len, &xkey );
-
- /* Compute the next 16 bytes in the buffer */
- Twofish_encrypt( &xkey, p, p-16 );
-
- /* Check that the decryption is correct. */
- Twofish_decrypt( &xkey, p-16, tmp );
- if( memcmp( tmp, p, 16 ) != 0 )
- {
- Twofish_fatal( "Twofish decryption failure in sequence" );
- }
- /* Move on to next 16 bytes in the buffer. */
- p -= 16;
- }
-
- /* And check the final value. */
- if( memcmp( p, final_value, 16 ) != 0 )
- {
- Twofish_fatal( "Twofish encryption failure in sequence" );
- }
-
- /* None of the data was secret, so there is no need to wipe anything. */
- }
-
-
-/*
- * Run all three sequence tests from the Twofish test vectors.
- *
- * This checks the most extensive test vectors currently available
- * for Twofish. The data is from the Twofish book, appendix B.2.
- */
-static void test_sequences()
- {
- static Byte r128[] = {
- 0x5D, 0x9D, 0x4E, 0xEF, 0xFA, 0x91, 0x51, 0x57,
- 0x55, 0x24, 0xF1, 0x15, 0x81, 0x5A, 0x12, 0xE0
- };
- static Byte r192[] = {
- 0xE7, 0x54, 0x49, 0x21, 0x2B, 0xEE, 0xF9, 0xF4,
- 0xA3, 0x90, 0xBD, 0x86, 0x0A, 0x64, 0x09, 0x41
- };
- static Byte r256[] = {
- 0x37, 0xFE, 0x26, 0xFF, 0x1C, 0xF6, 0x61, 0x75,
- 0xF5, 0xDD, 0xF4, 0xC3, 0x3B, 0x97, 0xA2, 0x05
- };
-
- /* Run the three sequence test vectors */
- test_sequence( 16, r128 );
- test_sequence( 24, r192 );
- test_sequence( 32, r256 );
- }
-
-
-/*
- * Test the odd-sized keys.
- *
- * Every odd-sized key is equivalent to a one of 128, 192, or 256 bits.
- * The equivalent key is found by padding at the end with zero bytes
- * until a regular key size is reached.
- *
- * We just test that the key expansion routine behaves properly.
- * If the expanded keys are identical, then the encryptions and decryptions
- * will behave the same.
- */
-static void test_odd_sized_keys()
- {
- Byte buf[32];
- Twofish_key xkey;
- Twofish_key xkey_two;
- int i;
-
- /*
- * We first create an all-zero key to use as PRNG key.
- * Normally we would not have to fill the buffer with zeroes, as we could
- * just pass a zero key length to the Twofish_prepare_key function.
- * However, this relies on using odd-sized keys, and those are just the
- * ones we are testing here. We can't use an untested function to test
- * itself.
- */
- memset( buf, 0, sizeof( buf ) );
- Twofish_prepare_key( buf, 16, &xkey );
-
- /* Fill buffer with pseudo-random data derived from two encryptions */
- Twofish_encrypt( &xkey, buf, buf );
- Twofish_encrypt( &xkey, buf, buf+16 );
-
- /* Create all possible shorter keys that are prefixes of the buffer. */
- for( i=31; i>=0; i-- )
- {
- /* Set a byte to zero. This is the new padding byte */
- buf[i] = 0;
-
- /* Expand the key with only i bytes of length */
- Twofish_prepare_key( buf, i, &xkey );
-
- /* Expand the corresponding padded key of regular length */
- Twofish_prepare_key( buf, i<=16 ? 16 : i<= 24 ? 24 : 32, &xkey_two );
-
- /* Compare the two */
- if( memcmp( &xkey, &xkey_two, sizeof( xkey ) ) != 0 )
- {
- Twofish_fatal( "Odd sized keys do not expand properly" );
- }
- }
-
- /* None of the key values are secret, so we don't need to wipe them. */
- }
-
-
-/*
- * Test the Twofish implementation.
- *
- * This routine runs all the self tests, in order of importance.
- * It is called by the Twofish_initialise routine.
- *
- * In almost all applications the cost of running the self tests during
- * initialisation is insignificant, especially
- * compared to the time it takes to load the application from disk.
- * If you are very pressed for initialisation performance,
- * you could remove some of the tests. Make sure you did run them
- * once in the software and hardware configuration you are using.
- */
-static void self_test()
- {
- /* The three test vectors form an absolute minimal test set. */
- test_vectors();
-
- /*
- * If at all possible you should run these tests too. They take
- * more time, but provide a more thorough coverage.
- */
- test_sequences();
-
- /* Test the odd-sized keys. */
- test_odd_sized_keys();
- }
-
-
-/*
- * And now, the actual Twofish implementation.
- *
- * This implementation generates all the tables during initialisation.
- * I don't like large tables in the code, especially since they are easily
- * damaged in the source without anyone noticing it. You need code to
- * generate them anyway, and this way all the code is close together.
- * Generating them in the application leads to a smaller executable
- * (the code is smaller than the tables it generates) and a
- * larger static memory footprint.
- *
- * Twofish can be implemented in many ways. I have chosen to
- * use large tables with a relatively long key setup time.
- * If you encrypt more than a few blocks of data it pays to pre-compute
- * as much as possible. This implementation is relatively inefficient for
- * applications that need to re-key every block or so.
- */
-
-/*
- * We start with the t-tables, directly from the Twofish definition.
- * These are nibble-tables, but merging them and putting them two nibbles
- * in one byte is more work than it is worth.
- */
-static Byte t_table[2][4][16] = {
- {
- {0x8,0x1,0x7,0xD,0x6,0xF,0x3,0x2,0x0,0xB,0x5,0x9,0xE,0xC,0xA,0x4},
- {0xE,0xC,0xB,0x8,0x1,0x2,0x3,0x5,0xF,0x4,0xA,0x6,0x7,0x0,0x9,0xD},
- {0xB,0xA,0x5,0xE,0x6,0xD,0x9,0x0,0xC,0x8,0xF,0x3,0x2,0x4,0x7,0x1},
- {0xD,0x7,0xF,0x4,0x1,0x2,0x6,0xE,0x9,0xB,0x3,0x0,0x8,0x5,0xC,0xA}
- },
- {
- {0x2,0x8,0xB,0xD,0xF,0x7,0x6,0xE,0x3,0x1,0x9,0x4,0x0,0xA,0xC,0x5},
- {0x1,0xE,0x2,0xB,0x4,0xC,0x3,0x7,0x6,0xD,0xA,0x5,0xF,0x9,0x0,0x8},
- {0x4,0xC,0x7,0x5,0x1,0x6,0x9,0xA,0x0,0xE,0xD,0x8,0x2,0xB,0x3,0xF},
- {0xB,0x9,0x5,0x1,0xC,0x3,0xD,0xE,0x6,0x4,0x7,0xF,0x2,0x0,0x8,0xA}
- }
-};
-
-
-/* A 1-bit rotation of 4-bit values. Input must be in range 0..15 */
-#define ROR4BY1( x ) (((x)>>1) | (((x)<<3) & 0x8) )
-
-/*
- * The q-boxes are only used during the key schedule computations.
- * These are 8->8 bit lookup tables. Some CPUs prefer to have 8->32 bit
- * lookup tables as it is faster to load a 32-bit value than to load an
- * 8-bit value and zero the rest of the register.
- * The LARGE_Q_TABLE switch allows you to choose 32-bit entries in
- * the q-tables. Here we just define the Qtype which is used to store
- * the entries of the q-tables.
- */
-#if LARGE_Q_TABLE
-typedef UInt32 Qtype;
-#else
-typedef Byte Qtype;
-#endif
-
-/*
- * The actual q-box tables.
- * There are two q-boxes, each having 256 entries.
- */
-static Qtype q_table[2][256];
-
-
-/*
- * Now the function that converts a single t-table into a q-table.
- *
- * Arguments:
- * t[4][16] : four 4->4bit lookup tables that define the q-box
- * q[256] : output parameter: the resulting q-box as a lookup table.
- */
-static void make_q_table( Byte t[4][16], Qtype q[256] )
- {
- int ae,be,ao,bo; /* Some temporaries. */
- int i;
- /* Loop over all input values and compute the q-box result. */
- for( i=0; i<256; i++ ) {
- /*
- * This is straight from the Twofish specifications.
- *
- * The ae variable is used for the a_i values from the specs
- * with even i, and ao for the odd i's. Similarly for the b's.
- */
- ae = i>>4; be = i&0xf;
- ao = ae ^ be; bo = ae ^ ROR4BY1(be) ^ ((ae<<3)&8);
- ae = t[0][ao]; be = t[1][bo];
- ao = ae ^ be; bo = ae ^ ROR4BY1(be) ^ ((ae<<3)&8);
- ae = t[2][ao]; be = t[3][bo];
-
- /* Store the result in the q-box table, the cast avoids a warning. */
- q[i] = (Qtype) ((be<<4) | ae);
- }
- }
-
-
-/*
- * Initialise both q-box tables.
- */
-static void initialise_q_boxes() {
- /* Initialise each of the q-boxes using the t-tables */
- make_q_table( t_table[0], q_table[0] );
- make_q_table( t_table[1], q_table[1] );
- }
-
-
-/*
- * Next up is the MDS matrix multiplication.
- * The MDS matrix multiplication operates in the field
- * GF(2)[x]/p(x) with p(x)=x^8+x^6+x^5+x^3+1.
- * If you don't understand this, read a book on finite fields. You cannot
- * follow the finite-field computations without some background.
- *
- * In this field, multiplication by x is easy: shift left one bit
- * and if bit 8 is set then xor the result with 0x169.
- *
- * The MDS coefficients use a multiplication by 1/x,
- * or rather a division by x. This is easy too: first make the
- * value 'even' (i.e. bit 0 is zero) by xorring with 0x169 if necessary,
- * and then shift right one position.
- * Even easier: shift right and xor with 0xb4 if the lsbit was set.
- *
- * The MDS coefficients are 1, EF, and 5B, and we use the fact that
- * EF = 1 + 1/x + 1/x^2
- * 5B = 1 + 1/x^2
- * in this field. This makes multiplication by EF and 5B relatively easy.
- *
- * This property is no accident, the MDS matrix was designed to allow
- * this implementation technique to be used.
- *
- * We have four MDS tables, each mapping 8 bits to 32 bits.
- * Each table performs one column of the matrix multiplication.
- * As the MDS is always preceded by q-boxes, each of these tables
- * also implements the q-box just previous to that column.
- */
-
-/* The actual MDS tables. */
-static UInt32 MDS_table[4][256];
-
-/* A small table to get easy conditional access to the 0xb4 constant. */
-static UInt32 mds_poly_divx_const[] = {0,0xb4};
-
-/* Function to initialise the MDS tables. */
-static void initialise_mds_tables()
- {
- int i;
- UInt32 q,qef,q5b; /* Temporary variables. */
-
- /* Loop over all 8-bit input values */
- for( i=0; i<256; i++ )
- {
- /*
- * To save some work during the key expansion we include the last
- * of the q-box layers from the h() function in these MDS tables.
- */
-
- /* We first do the inputs that are mapped through the q0 table. */
- q = q_table[0][i];
- /*
- * Here we divide by x, note the table to get 0xb4 only if the
- * lsbit is set.
- * This sets qef = (1/x)*q in the finite field
- */
- qef = (q >> 1) ^ mds_poly_divx_const[ q & 1 ];
- /*
- * Divide by x again, and add q to get (1+1/x^2)*q.
- * Note that (1+1/x^2) = 5B in the field, and addition in the field
- * is exclusive or on the bits.
- */
- q5b = (qef >> 1) ^ mds_poly_divx_const[ qef & 1 ] ^ q;
- /*
- * Add q5b to qef to set qef = (1+1/x+1/x^2)*q.
- * Again, (1+1/x+1/x^2) = EF in the field.
- */
- qef ^= q5b;
-
- /*
- * Now that we have q5b = 5B * q and qef = EF * q
- * we can fill two of the entries in the MDS matrix table.
- * See the Twofish specifications for the order of the constants.
- */
- MDS_table[1][i] = q <<24 | q5b<<16 | qef<<8 | qef;
- MDS_table[3][i] = q5b<<24 | qef<<16 | q <<8 | q5b;
-
- /* Now we do it all again for the two columns that have a q1 box. */
- q = q_table[1][i];
- qef = (q >> 1) ^ mds_poly_divx_const[ q & 1 ];
- q5b = (qef >> 1) ^ mds_poly_divx_const[ qef & 1 ] ^ q;
- qef ^= q5b;
-
- /* The other two columns use the coefficient in a different order. */
- MDS_table[0][i] = qef<<24 | qef<<16 | q5b<<8 | q ;
- MDS_table[2][i] = qef<<24 | q <<16 | qef<<8 | q5b;
- }
- }
-
-
-/*
- * The h() function is the heart of the Twofish cipher.
- * It is a complicated sequence of q-box lookups, key material xors,
- * and finally the MDS matrix.
- * We use lots of macros to make this reasonably fast.
- */
-
-/* First a shorthand for the two q-tables */
-#define q0 q_table[0]
-#define q1 q_table[1]
-
-/*
- * Each macro computes one column of the h for either 2, 3, or 4 stages.
- * As there are 4 columns, we have 12 macros in all.
- *
- * The key bytes are stored in the Byte array L at offset
- * 0,1,2,3, 8,9,10,11, [16,17,18,19, [24,25,26,27]] as this is the
- * order we get the bytes from the user. If you look at the Twofish
- * specs, you'll see that h() is applied to the even key words or the
- * odd key words. The bytes of the even words appear in this spacing,
- * and those of the odd key words too.
- *
- * These macros are the only place where the q-boxes and the MDS table
- * are used.
- */
-#define H02( y, L ) MDS_table[0][q0[q0[y]^L[ 8]]^L[0]]
-#define H12( y, L ) MDS_table[1][q0[q1[y]^L[ 9]]^L[1]]
-#define H22( y, L ) MDS_table[2][q1[q0[y]^L[10]]^L[2]]
-#define H32( y, L ) MDS_table[3][q1[q1[y]^L[11]]^L[3]]
-#define H03( y, L ) H02( q1[y]^L[16], L )
-#define H13( y, L ) H12( q1[y]^L[17], L )
-#define H23( y, L ) H22( q0[y]^L[18], L )
-#define H33( y, L ) H32( q0[y]^L[19], L )
-#define H04( y, L ) H03( q1[y]^L[24], L )
-#define H14( y, L ) H13( q0[y]^L[25], L )
-#define H24( y, L ) H23( q0[y]^L[26], L )
-#define H34( y, L ) H33( q1[y]^L[27], L )
-
-/*
- * Now we can define the h() function given an array of key bytes.
- * This function is only used in the key schedule, and not to pre-compute
- * the keyed S-boxes.
- *
- * In the key schedule, the input is always of the form k*(1+2^8+2^16+2^24)
- * so we only provide k as an argument.
- *
- * Arguments:
- * k input to the h() function.
- * L pointer to array of key bytes at
- * offsets 0,1,2,3, ... 8,9,10,11, [16,17,18,19, [24,25,26,27]]
- * kCycles # key cycles, 2, 3, or 4.
- */
-static UInt32 h( int k, Byte L[], int kCycles )
- {
- switch( kCycles ) {
- /* We code all 3 cases separately for speed reasons. */
- case 2:
- return H02(k,L) ^ H12(k,L) ^ H22(k,L) ^ H32(k,L);
- case 3:
- return H03(k,L) ^ H13(k,L) ^ H23(k,L) ^ H33(k,L);
- case 4:
- return H04(k,L) ^ H14(k,L) ^ H24(k,L) ^ H34(k,L);
- default:
- /* This is always a coding error, which is fatal. */
- Twofish_fatal( "Twofish h(): Illegal argument" );
- }
- }
-
-
-/*
- * Pre-compute the keyed S-boxes.
- * Fill the pre-computed S-box array in the expanded key structure.
- * Each pre-computed S-box maps 8 bits to 32 bits.
- *
- * The S argument contains half the number of bytes of the full key, but is
- * derived from the full key. (See Twofish specifications for details.)
- * S has the weird byte input order used by the Hxx macros.
- *
- * This function takes most of the time of a key expansion.
- *
- * Arguments:
- * S pointer to array of 8*kCycles Bytes containing the S vector.
- * kCycles number of key words, must be in the set {2,3,4}
- * xkey pointer to Twofish_key structure that will contain the S-boxes.
- */
-static void fill_keyed_sboxes( Byte S[], int kCycles, Twofish_key * xkey )
- {
- int i;
- switch( kCycles ) {
- /* We code all 3 cases separately for speed reasons. */
- case 2:
- for( i=0; i<256; i++ )
- {
- xkey->s[0][i]= H02( i, S );
- xkey->s[1][i]= H12( i, S );
- xkey->s[2][i]= H22( i, S );
- xkey->s[3][i]= H32( i, S );
- }
- break;
- case 3:
- for( i=0; i<256; i++ )
- {
- xkey->s[0][i]= H03( i, S );
- xkey->s[1][i]= H13( i, S );
- xkey->s[2][i]= H23( i, S );
- xkey->s[3][i]= H33( i, S );
- }
- break;
- case 4:
- for( i=0; i<256; i++ )
- {
- xkey->s[0][i]= H04( i, S );
- xkey->s[1][i]= H14( i, S );
- xkey->s[2][i]= H24( i, S );
- xkey->s[3][i]= H34( i, S );
- }
- break;
- default:
- /* This is always a coding error, which is fatal. */
- Twofish_fatal( "Twofish fill_keyed_sboxes(): Illegal argument" );
- }
- }
-
-
-/* A flag to keep track of whether we have been initialised or not. */
-static int Twofish_initialised = 0;
-
-/*
- * Initialise the Twofish implementation.
- * This function must be called before any other function in the
- * Twofish implementation is called.
- * This routine also does some sanity checks, to make sure that
- * all the macros behave, and it tests the whole cipher.
- */
-void Twofish_initialise()
- {
- /* First test the various platform-specific definitions. */
- test_platform();
-
- /* We can now generate our tables, in the right order of course. */
- initialise_q_boxes();
- initialise_mds_tables();
-
- /* We're finished with the initialisation itself. */
- Twofish_initialised = 1;
-
- /*
- * And run some tests on the whole cipher.
- * Yes, you need to do this every time you start your program.
- * It is called assurance; you have to be certain that your program
- * still works properly.
- */
- self_test();
- }
-
-
-/*
- * The Twofish key schedule uses an Reed-Solomon code matrix multiply.
- * Just like the MDS matrix, the RS-matrix is designed to be easy
- * to implement. Details are below in the code.
- *
- * These constants make it easy to compute in the finite field used
- * for the RS code.
- *
- * We use Bytes for the RS computation, but these are automatically
- * widened to unsigned integers in the expressions. Having unsigned
- * ints in these tables therefore provides the fastest access.
- */
-static unsigned int rs_poly_const[] = {0, 0x14d};
-static unsigned int rs_poly_div_const[] = {0, 0xa6 };
-
-
-/*
- * Prepare a key for use in encryption and decryption.
- * Like most block ciphers, Twofish allows the key schedule
- * to be pre-computed given only the key.
- * Twofish has a fairly 'heavy' key schedule that takes a lot of time
- * to compute. The main work is pre-computing the S-boxes used in the
- * encryption and decryption. We feel that this makes the cipher much
- * harder to attack. The attacker doesn't even know what the S-boxes
- * contain without including the entire key schedule in the analysis.
- *
- * Unlike most Twofish implementations, this one allows any key size from
- * 0 to 32 bytes. Odd key sizes are defined for Twofish (see the
- * specifications); the key is simply padded with zeroes to the next real
- * key size of 16, 24, or 32 bytes.
- * Each odd-sized key is thus equivalent to a single normal-sized key.
- *
- * Arguments:
- * key array of key bytes
- * key_len number of bytes in the key, must be in the range 0,...,32.
- * xkey Pointer to an Twofish_key structure that will be filled
- * with the internal form of the cipher key.
- */
-void Twofish_prepare_key( Byte key[], int key_len, Twofish_key * xkey )
- {
- /* We use a single array to store all key material in,
- * to simplify the wiping of the key material at the end.
- * The first 32 bytes contain the actual (padded) cipher key.
- * The next 32 bytes contain the S-vector in its weird format,
- * and we have 4 bytes of overrun necessary for the RS-reduction.
- */
- Byte K[32+32+4];
-
- int kCycles; /* # key cycles, 2,3, or 4. */
-
- int i;
- UInt32 A, B; /* Used to compute the round keys. */
-
- Byte * kptr; /* Three pointers for the RS computation. */
- Byte * sptr;
- Byte * t;
-
- Byte b,bx,bxx; /* Some more temporaries for the RS computation. */
-
- /* Check that the Twofish implementation was initialised. */
- if( Twofish_initialised == 0 )
- {
- /*
- * You didn't call Twofish_initialise before calling this routine.
- * This is a programming error, and therefore we call the fatal
- * routine.
- *
- * I could of course call the initialisation routine here,
- * but there are a few reasons why I don't. First of all, the
- * self-tests have to be done at startup. It is no good to inform
- * the user that the cipher implementation fails when he wants to
- * write his data to disk in encrypted form. You have to warn him
- * before he spends time typing his data. Second, the initialisation
- * and self test are much slower than a single key expansion.
- * Calling the initialisation here makes the performance of the
- * cipher unpredictable. This can lead to really weird problems
- * if you use the cipher for a real-time task. Suddenly it fails
- * once in a while the first time you try to use it. Things like
- * that are almost impossible to debug.
- */
- Twofish_fatal( "Twofish implementation was not initialised." );
-
- /*
- * There is always a danger that the Twofish_fatal routine returns,
- * in spite of the specifications that it should not.
- * (A good programming rule: don't trust the rest of the code.)
- * This would be disasterous. If the q-tables and MDS-tables have
- * not been initialised, they are probably still filled with zeroes.
- * Suppose the MDS-tables are all zero. The key expansion would then
- * generate all-zero round keys, and all-zero s-boxes. The danger
- * is that nobody would notice as the encryption function still
- * mangles the input, and the decryption still 'decrypts' it,
- * but now in a completely key-independent manner.
- * To stop such security disasters, we use blunt force.
- * If your program hangs here: fix the fatal routine!
- */
- //for(;;); /* Infinite loop, which beats being insecure. */
- return;
- }
-
- /* Check for valid key length. */
- if( key_len < 0 || key_len > 32 )
- {
- /*
- * This can only happen if a programmer didn't read the limitations
- * on the key size.
- */
- Twofish_fatal( "Twofish_prepare_key: illegal key length" );
- /*
- * A return statement just in case the fatal macro returns.
- * The rest of the code assumes that key_len is in range, and would
- * buffer-overflow if it wasn't.
- *
- * Why do we still use a programming language that has problems like
- * buffer overflows, when these problems were solved in 1960 with
- * the development of Algol? Have we not leared anything?
- */
- return;
- }
-
- /* Pad the key with zeroes to the next suitable key length. */
- memcpy( K, key, key_len );
- memset( K+key_len, 0, sizeof(K)-key_len );
-
- /*
- * Compute kCycles: the number of key cycles used in the cipher.
- * 2 for 128-bit keys, 3 for 192-bit keys, and 4 for 256-bit keys.
- */
- kCycles = (key_len + 7) >> 3;
- /* Handle the special case of very short keys: minimum 2 cycles. */
- if( kCycles < 2 )
- {
- kCycles = 2;
- }
-
- /*
- * From now on we just pretend to have 8*kCycles bytes of
- * key material in K. This handles all the key size cases.
- */
-
- /*
- * We first compute the 40 expanded key words,
- * formulas straight from the Twofish specifications.
- */
- for( i=0; i<40; i+=2 )
- {
- /*
- * Due to the byte spacing expected by the h() function
- * we can pick the bytes directly from the key K.
- * As we use bytes, we never have the little/big endian
- * problem.
- *
- * Note that we apply the rotation function only to simple
- * variables, as the rotation macro might evaluate its argument
- * more than once.
- */
- A = h( i , K , kCycles );
- B = h( i+1, K+4, kCycles );
- B = ROL32( B, 8 );
-
- /* Compute and store the round keys. */
- A += B;
- B += A;
- xkey->K[i] = A;
- xkey->K[i+1] = ROL32( B, 9 );
- }
-
- /* Wipe variables that contained key material. */
- A=B=0;
-
- /*
- * And now the dreaded RS multiplication that few seem to understand.
- * The RS matrix is not random, and is specially designed to compute the
- * RS matrix multiplication in a simple way.
- *
- * We work in the field GF(2)[x]/x^8+x^6+x^3+x^2+1. Note that this is a
- * different field than used for the MDS matrix.
- * (At least, it is a different representation because all GF(2^8)
- * representations are equivalent in some form.)
- *
- * We take 8 consecutive bytes of the key and interpret them as
- * a polynomial k_0 + k_1 y + k_2 y^2 + ... + k_7 y^7 where
- * the k_i bytes are the key bytes and are elements of the finite field.
- * We multiply this polynomial by y^4 and reduce it modulo
- * y^4 + (x + 1/x)y^3 + (x)y^2 + (x + 1/x)y + 1.
- * using straightforward polynomial modulo reduction.
- * The coefficients of the result are the result of the RS
- * matrix multiplication. When we wrote the Twofish specification,
- * the original RS definition used the polynomials,
- * but that requires much more mathematical knowledge.
- * We were already using matrix multiplication in a finite field for
- * the MDS matrix, so I re-wrote the RS operation as a matrix
- * multiplication to reduce the difficulty of understanding it.
- * Some implementors have not picked up on this simpler method of
- * computing the RS operation, even though it is mentioned in the
- * specifications.
- *
- * It is possible to perform these computations faster by using 32-bit
- * word operations, but that is not portable and this is not a speed-
- * critical area.
- *
- * We explained the 1/x computation when we did the MDS matrix.
- *
- * The S vector is stored in K[32..64].
- * The S vector has to be reversed, so we loop cross-wise.
- *
- * Note the weird byte spacing of the S-vector, to match the even
- * or odd key words arrays. See the discussion at the Hxx macros for
- * details.
- */
- kptr = K + 8*kCycles; /* Start at end of key */
- sptr = K + 32; /* Start at start of S */
-
- /* Loop over all key material */
- while( kptr > K )
- {
- kptr -= 8;
- /*
- * Initialise the polynimial in sptr[0..12]
- * The first four coefficients are 0 as we have to multiply by y^4.
- * The next 8 coefficients are from the key material.
- */
- memset( sptr, 0, 4 );
- memcpy( sptr+4, kptr, 8 );
-
- /*
- * The 12 bytes starting at sptr are now the coefficients of
- * the polynomial we need to reduce.
- */
-
- /* Loop over the polynomial coefficients from high to low */
- t = sptr+11;
- /* Keep looping until polynomial is degree 3; */
- while( t > sptr+3 )
- {
- /* Pick up the highest coefficient of the poly. */
- b = *t;
-
- /*
- * Compute x and (x+1/x) times this coefficient.
- * See the MDS matrix implementation for a discussion of
- * multiplication by x and 1/x. We just use different
- * constants here as we are in a
- * different finite field representation.
- *
- * These two statements set
- * bx = (x) * b
- * bxx= (x + 1/x) * b
- */
- bx = (Byte)((b<<1) ^ rs_poly_const[ b>>7 ]);
- bxx= (Byte)((b>>1) ^ rs_poly_div_const[ b&1 ] ^ bx);
-
- /*
- * Subtract suitable multiple of
- * y^4 + (x + 1/x)y^3 + (x)y^2 + (x + 1/x)y + 1
- * from the polynomial, except that we don't bother
- * updating t[0] as it will become zero anyway.
- */
- t[-1] ^= bxx;
- t[-2] ^= bx;
- t[-3] ^= bxx;
- t[-4] ^= b;
-
- /* Go to the next coefficient. */
- t--;
- }
-
- /* Go to next S-vector word, obeying the weird spacing rules. */
- sptr += 8;
- }
-
- /* Wipe variables that contained key material. */
- b = bx = bxx = 0;
-
- /* And finally, we can compute the key-dependent S-boxes. */
- fill_keyed_sboxes( &K[32], kCycles, xkey );
-
- /* Wipe array that contained key material. */
- memset( K, 0, sizeof( K ) );
- }
-
-
-/*
- * We can now start on the actual encryption and decryption code.
- * As these are often speed-critical we will use a lot of macros.
- */
-
-/*
- * The g() function is the heart of the round function.
- * We have two versions of the g() function, one without an input
- * rotation and one with.
- * The pre-computed S-boxes make this pretty simple.
- */
-#define g0(X,xkey) \
- (xkey->s[0][b0(X)]^xkey->s[1][b1(X)]^xkey->s[2][b2(X)]^xkey->s[3][b3(X)])
-
-#define g1(X,xkey) \
- (xkey->s[0][b3(X)]^xkey->s[1][b0(X)]^xkey->s[2][b1(X)]^xkey->s[3][b2(X)])
-
-/*
- * A single round of Twofish. The A,B,C,D are the four state variables,
- * T0 and T1 are temporaries, xkey is the expanded key, and r the
- * round number.
- *
- * Note that this macro does not implement the swap at the end of the round.
- */
-#define ENCRYPT_RND( A,B,C,D, T0, T1, xkey, r ) \
- T0 = g0(A,xkey); T1 = g1(B,xkey);\
- C ^= T0+T1+xkey->K[8+2*(r)]; C = ROR32(C,1);\
- D = ROL32(D,1); D ^= T0+2*T1+xkey->K[8+2*(r)+1]
-
-/*
- * Encrypt a single cycle, consisting of two rounds.
- * This avoids the swapping of the two halves.
- * Parameter r is now the cycle number.
- */
-#define ENCRYPT_CYCLE( A, B, C, D, T0, T1, xkey, r ) \
- ENCRYPT_RND( A,B,C,D,T0,T1,xkey,2*(r) );\
- ENCRYPT_RND( C,D,A,B,T0,T1,xkey,2*(r)+1 )
-
-/* Full 16-round encryption */
-#define ENCRYPT( A,B,C,D,T0,T1,xkey ) \
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 0 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 1 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 2 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 3 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 4 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 5 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 6 );\
- ENCRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 7 )
-
-/*
- * A single round of Twofish for decryption. It differs from
- * ENCRYTP_RND only because of the 1-bit rotations.
- */
-#define DECRYPT_RND( A,B,C,D, T0, T1, xkey, r ) \
- T0 = g0(A,xkey); T1 = g1(B,xkey);\
- C = ROL32(C,1); C ^= T0+T1+xkey->K[8+2*(r)];\
- D ^= T0+2*T1+xkey->K[8+2*(r)+1]; D = ROR32(D,1)
-
-/*
- * Decrypt a single cycle, consisting of two rounds.
- * This avoids the swapping of the two halves.
- * Parameter r is now the cycle number.
- */
-#define DECRYPT_CYCLE( A, B, C, D, T0, T1, xkey, r ) \
- DECRYPT_RND( A,B,C,D,T0,T1,xkey,2*(r)+1 );\
- DECRYPT_RND( C,D,A,B,T0,T1,xkey,2*(r) )
-
-/* Full 16-round decryption. */
-#define DECRYPT( A,B,C,D,T0,T1, xkey ) \
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 7 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 6 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 5 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 4 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 3 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 2 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 1 );\
- DECRYPT_CYCLE( A,B,C,D,T0,T1,xkey, 0 )
-
-/*
- * A macro to read the state from the plaintext and do the initial key xors.
- * The koff argument allows us to use the same macro
- * for the decryption which uses different key words at the start.
- */
-#define GET_INPUT( src, A,B,C,D, xkey, koff ) \
- A = GET32(src )^xkey->K[ koff]; B = GET32(src+ 4)^xkey->K[1+koff]; \
- C = GET32(src+ 8)^xkey->K[2+koff]; D = GET32(src+12)^xkey->K[3+koff]
-
-/*
- * Similar macro to put the ciphertext in the output buffer.
- * We xor the keys into the state variables before we use the PUT32
- * macro as the macro might use its argument multiple times.
- */
-#define PUT_OUTPUT( A,B,C,D, dst, xkey, koff ) \
- A ^= xkey->K[ koff]; B ^= xkey->K[1+koff]; \
- C ^= xkey->K[2+koff]; D ^= xkey->K[3+koff]; \
- PUT32( A, dst ); PUT32( B, dst+ 4 ); \
- PUT32( C, dst+8 ); PUT32( D, dst+12 )
-
-
-/*
- * Twofish block encryption
- *
- * Arguments:
- * xkey expanded key array
- * p 16 bytes of plaintext
- * c 16 bytes in which to store the ciphertext
- */
-void Twofish_encrypt( Twofish_key * xkey, Byte p[16], Byte c[16])
- {
- UInt32 A,B,C,D,T0,T1; /* Working variables */
-
- /* Get the four plaintext words xorred with the key */
- GET_INPUT( p, A,B,C,D, xkey, 0 );
-
- /* Do 8 cycles (= 16 rounds) */
- ENCRYPT( A,B,C,D,T0,T1,xkey );
-
- /* Store them with the final swap and the output whitening. */
- PUT_OUTPUT( C,D,A,B, c, xkey, 4 );
- }
-
-
-/*
- * Twofish block decryption.
- *
- * Arguments:
- * xkey expanded key array
- * p 16 bytes of plaintext
- * c 16 bytes in which to store the ciphertext
- */
-void Twofish_decrypt( Twofish_key * xkey, Byte c[16], Byte p[16])
- {
- UInt32 A,B,C,D,T0,T1; /* Working variables */
-
- /* Get the four plaintext words xorred with the key */
- GET_INPUT( c, A,B,C,D, xkey, 4 );
-
- /* Do 8 cycles (= 16 rounds) */
- DECRYPT( A,B,C,D,T0,T1,xkey );
-
- /* Store them with the final swap and the output whitening. */
- PUT_OUTPUT( C,D,A,B, p, xkey, 0 );
- }
-
-/*
- * Using the macros it is easy to make special routines for
- * CBC mode, CTR mode etc. The only thing you might want to
- * add is a XOR_PUT_OUTPUT which xors the outputs into the
- * destinationa instead of overwriting the data. This requires
- * a XOR_PUT32 macro as well, but that should all be trivial.
- *
- * I thought about including routines for the separate cipher
- * modes here, but it is unclear which modes should be included,
- * and each encryption or decryption routine takes up a lot of code space.
- * Also, I don't have any test vectors for any cipher modes
- * with Twofish.
- */
diff --git a/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.h b/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.h
deleted file mode 100755
index 22452a3157cd16311b3bc54c73cc67b6ea037189..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/CryptoBox/twofish/twofish.h
+++ /dev/null
@@ -1,180 +0,0 @@
-/*
- * Fast, portable, and easy-to-use Twofish implementation,
- * Version 0.3.
- * Copyright (c) 2002 by Niels Ferguson.
- *
- * See the twofish.c file for the details of the how and why of this code.
- *
- * The author hereby grants a perpetual license to everybody to
- * use this code for any purpose as long as the copyright message is included
- * in the source code of this or any derived work.
- */
-
-#include <stdint.h>
-
-/*
- * PLATFORM FIXES
- * ==============
- *
- * The following definitions have to be fixed for each particular platform
- * you work on. If you have a multi-platform program, you no doubt have
- * portable definitions that you can substitute here without changing
- * the rest of the code.
- *
- * The defaults provided here should work on most PC compilers.
- */
-
-
-/*
- * A Twofish_Byte must be an unsigned 8-bit integer.
- * It must also be the elementary data size of your C platform,
- * i.e. sizeof( Twofish_Byte ) == 1.
- */
-typedef uint8_t Twofish_Byte;
-
-/*
- * A Twofish_UInt32 must be an unsigned integer of at least 32 bits.
- *
- * This type is used only internally in the implementation, so ideally it
- * would not appear in the header file, but it is used inside the
- * Twofish_key structure which means it has to be included here.
- */
-typedef uint32_t Twofish_UInt32;
-
-
-/*
- * END OF PLATFORM FIXES
- * =====================
- *
- * You should not have to touch the rest of this file, but the code
- * in twofish.c has a few things you need to fix too.
- */
-
-
-/*
- * Structure that contains a prepared Twofish key.
- * A cipher key is used in two stages. In the first stage it is converted
- * form the original form to an internal representation.
- * This internal form is then used to encrypt and decrypt data.
- * This structure contains the internal form. It is rather large: 4256 bytes
- * on a platform with 32-bit unsigned values.
- *
- * Treat this as an opague structure, and don't try to manipulate the
- * elements in it. I wish I could hide the inside of the structure,
- * but C doesn't allow that.
- */
-typedef
- struct
- {
- Twofish_UInt32 s[4][256]; /* pre-computed S-boxes */
- Twofish_UInt32 K[40]; /* Round key words */
- }
- Twofish_key;
-
-
-/*
- * Initialise and test the Twofish implementation.
- *
- * This function MUST be called before any other function in the
- * Twofish implementation is called.
- * It only needs to be called once.
- *
- * Apart from initialising the implementation it performs a self test.
- * If the Twofish_fatal function is not called, the code passed the test.
- * (See the twofish.c file for details on the Twofish_fatal function.)
- */
-extern void Twofish_initialise(void);
-
-
-/*
- * Convert a cipher key to the internal form used for
- * encryption and decryption.
- *
- * The cipher key is an array of bytes; the Twofish_Byte type is
- * defined above to a type suitable on your platform.
- *
- * Any key must be converted to an internal form in the Twofisk_key structure
- * before it can be used.
- * The encryption and decryption functions only work with the internal form.
- * The conversion to internal form need only be done once for each key value.
- *
- * Be sure to wipe all key storage, including the Twofish_key structure,
- * once you are done with the key data.
- * A simple memset( TwofishKey, 0, sizeof( TwofishKey ) ) will do just fine.
- *
- * Unlike most implementations, this one allows any key size from 0 bytes
- * to 32 bytes. According to the Twofish specifications,
- * irregular key sizes are handled by padding the key with zeroes at the end
- * until the key size is 16, 24, or 32 bytes, whichever
- * comes first. Note that each key of irregular size is equivalent to exactly
- * one key of 16, 24, or 32 bytes.
- *
- * WARNING: Short keys have low entropy, and result in low security.
- * Anything less than 8 bytes is utterly insecure. For good security
- * use at least 16 bytes. I prefer to use 32-byte keys to prevent
- * any collision attacks on the key.
- *
- * The key length argument key_len must be in the proper range.
- * If key_len is not in the range 0,...,32 this routine attempts to generate
- * a fatal error (depending on the code environment),
- * and at best (or worst) returns without having done anything.
- *
- * Arguments:
- * key Array of key bytes
- * key_len Number of key bytes, must be in the range 0,1,...,32.
- * xkey Pointer to an Twofish_key structure that will be filled
- * with the internal form of the cipher key.
- */
-extern void Twofish_prepare_key(
- Twofish_Byte key[],
- int key_len,
- Twofish_key * xkey
- );
-
-
-/*
- * Encrypt a single block of data.
- *
- * This function encrypts a single block of 16 bytes of data.
- * If you want to encrypt a larger or variable-length message,
- * you will have to use a cipher mode, such as CBC or CTR.
- * These are outside the scope of this implementation.
- *
- * The xkey structure is not modified by this routine, and can be
- * used for further encryption and decryption operations.
- *
- * Arguments:
- * xkey pointer to Twofish_key, internal form of the key
- * produces by Twofish_prepare_key()
- * p Plaintext to be encrypted
- * c Place to store the ciphertext
- */
-extern void Twofish_encrypt(
- Twofish_key * xkey,
- Twofish_Byte p[16],
- Twofish_Byte c[16]
- );
-
-
-/*
- * Decrypt a single block of data.
- *
- * This function decrypts a single block of 16 bytes of data.
- * If you want to decrypt a larger or variable-length message,
- * you will have to use a cipher mode, such as CBC or CTR.
- * These are outside the scope of this implementation.
- *
- * The xkey structure is not modified by this routine, and can be
- * used for further encryption and decryption operations.
- *
- * Arguments:
- * xkey pointer to Twofish_key, internal form of the key
- * produces by Twofish_prepare_key()
- * c Ciphertext to be decrypted
- * p Place to store the plaintext
- */
-extern void Twofish_decrypt(
- Twofish_key * xkey,
- Twofish_Byte c[16],
- Twofish_Byte p[16]
- );
diff --git a/enzevalos_iphone/ObjectivePGP/Info.plist b/enzevalos_iphone/ObjectivePGP/Info.plist
deleted file mode 100755
index 872bbbc6611e93a60bdf7d7264cbdcd552921033..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Info.plist
+++ /dev/null
@@ -1,24 +0,0 @@
-<?xml version="1.0" encoding="UTF-8"?>
-<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
-<plist version="1.0">
-<dict>
- <key>CFBundleDevelopmentRegion</key>
- <string>$(DEVELOPMENT_LANGUAGE)</string>
- <key>CFBundleExecutable</key>
- <string>$(EXECUTABLE_NAME)</string>
- <key>CFBundleIdentifier</key>
- <string>$(PRODUCT_BUNDLE_IDENTIFIER)</string>
- <key>CFBundleInfoDictionaryVersion</key>
- <string>6.0</string>
- <key>CFBundleName</key>
- <string>$(PRODUCT_NAME)</string>
- <key>CFBundlePackageType</key>
- <string>FMWK</string>
- <key>CFBundleShortVersionString</key>
- <string>0.10.0</string>
- <key>CFBundleVersion</key>
- <string>$(CURRENT_PROJECT_VERSION)</string>
- <key>NSPrincipalClass</key>
- <string></string>
-</dict>
-</plist>
diff --git a/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Prefix.pch b/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Prefix.pch
deleted file mode 100755
index eb2007ecd445f1dd0629e8d05ab8304a130e661e..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Prefix.pch
+++ /dev/null
@@ -1,9 +0,0 @@
-//
-// Prefix header
-//
-// The contents of this file are implicitly included at the beginning of every source file.
-//
-
-#ifdef __OBJC__
- #import <Foundation/Foundation.h>
-#endif
diff --git a/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Private.h b/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Private.h
deleted file mode 100755
index 1ea99ea786bac73244cd00e02d0cfc0d9cc14d03..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/ObjectivePGP-Private.h
+++ /dev/null
@@ -1,70 +0,0 @@
-//
-// ObjectivePGP
-//
-// Copyright © Marcin Krzyżanowski. All rights reserved.
-//
-// DO NOT MODIFY. FILE GENERATED AUTOMATICALLY.
-
-#import <Foundation/Foundation.h>
-
-//! Project version number for ObjectivePGP.
-FOUNDATION_EXPORT double ObjectivePGPVersionNumber;
-
-//! Project version string for ObjectivePGP.
-FOUNDATION_EXPORT const unsigned char ObjectivePGPVersionString[];
-
-#import "PGPCryptoHash.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import "PGPSecretKeyPacket+Private.h"
-#import "PGPPacket+Private.h"
-#import "PGPCryptoUtils.h"
-#import "PGPRSA.h"
-#import "PGPS2K.h"
-#import "NSArray+PGPUtils.h"
-#import "PGPUserIDPacket.h"
-#import "PGPSymetricKeyEncryptedSessionKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPPublicSubKeyPacket.h"
-#import "PGPUserAttributeImageSubpacket.h"
-#import "NSData+compression.h"
-#import "PGPSignatureSubpacket.h"
-#import "PGPSecretSubKeyPacket.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPUserAttributePacket.h"
-#import "PGPPacket.h"
-#import "NSData+PGPUtils.h"
-#import "PGPUser+Private.h"
-#import "PGPBigNum.h"
-#import "PGPKeyMaterial.h"
-#import "PGPMPI.h"
-#import "PGPLiteralPacket.h"
-#import "PGPTrustPacket.h"
-#import "PGPSignatureSubpacketHeader.h"
-#import "PGPSignatureSubpacketCreationTime.h"
-#import "PGPUserAttributeSubpacket.h"
-#import "PGPSignaturePacket.h"
-#import "PGPOnePassSignaturePacket.h"
-#import "PGPPublicKeyEncryptedSessionKeyPacket.h"
-#import "PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h"
-#import "PGPModificationDetectionCodePacket.h"
-#import "PGPEncryptedSessionKeyPacketProtocol.h"
-#import "PGPSymmetricallyEncryptedDataPacket.h"
-#import "PGPPKCSEmsa.h"
-#import "PGPPKCSEme.h"
-#import "PGPCryptoCFB.h"
-#import "PGPPacketHeader.h"
-#import "PGPLogging.h"
-#import "PGPCompressedPacket.h"
-#import "PGPPartialSubKey+Private.h"
-#import "PGPDSA.h"
-#import "PGPPublicKeyPacket+Private.h"
-#import "PGPSignatureSubpacket+Private.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPKey+Private.h"
-#import "PGPPacketFactory.h"
-#import "PGPKeyring+Private.h"
-#import "PGPBigNum+Private.h"
-#import "PGPPartialKey+Private.h"
-#import "PGPSignatureSubpacketEmbeddedSignature.h"
diff --git a/enzevalos_iphone/ObjectivePGP/ObjectivePGP.h b/enzevalos_iphone/ObjectivePGP/ObjectivePGP.h
deleted file mode 100755
index 5621dd2576fac6e1b84ba86f0ef1888efb6e3557..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/ObjectivePGP.h
+++ /dev/null
@@ -1,28 +0,0 @@
-//
-// ObjectivePGP
-//
-// Copyright © Marcin Krzyżanowski. All rights reserved.
-//
-// DO NOT MODIFY. FILE GENERATED AUTOMATICALLY.
-
-#import <Foundation/Foundation.h>
-
-//! Project version number for ObjectivePGP.
-FOUNDATION_EXPORT double ObjectivePGPVersionNumber;
-
-//! Project version string for ObjectivePGP.
-FOUNDATION_EXPORT const unsigned char ObjectivePGPVersionString[];
-
-#import "PGPMacros.h"
-#import "PGPTypes.h"
-#import "ObjectivePGPObject.h"
-#import "PGPKeyGenerator.h"
-#import "PGPKeyring.h"
-#import "PGPFingerprint.h"
-#import "PGPKeyID.h"
-#import "PGPUser.h"
-#import "PGPPartialSubKey.h"
-#import "PGPPartialKey.h"
-#import "PGPKey.h"
-#import "PGPExportableProtocol.h"
-#import "PGPArmor.h"
diff --git a/enzevalos_iphone/ObjectivePGP/ObjectivePGPObject.m b/enzevalos_iphone/ObjectivePGP/ObjectivePGPObject.m
deleted file mode 100755
index 823b8b02df0ac78c71a029bc7b7fc13167937265..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/ObjectivePGPObject.m
+++ /dev/null
@@ -1,936 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "ObjectivePGPObject.h"
-#import "PGPArmor.h"
-#import "PGPCompressedPacket.h"
-#import "PGPCryptoUtils.h"
-#import "PGPKey+Private.h"
-#import "PGPKey.h"
-#import "PGPLiteralPacket.h"
-#import "PGPMPI.h"
-#import "PGPS2K.h"
-#import "PGPModificationDetectionCodePacket.h"
-#import "PGPOnePassSignaturePacket.h"
-#import "PGPPacketFactory.h"
-#import "PGPPartialKey.h"
-#import "PGPPublicKeyEncryptedSessionKeyPacket.h"
-#import "PGPSymetricKeyEncryptedSessionKeyPacket.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPSignaturePacket.h"
-#import "PGPPartialSubKey.h"
-#import "PGPSymmetricallyEncryptedDataPacket.h"
-#import "PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h"
-#import "PGPUser.h"
-#import "PGPUserIDPacket.h"
-#import "NSMutableData+PGPUtils.h"
-#import "NSArray+PGPUtils.h"
-#import "PGPKeyring.h"
-#import "PGPKeyring+Private.h"
-
-#import "PGPFoundation.h"
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-#import "NSData+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation ObjectivePGP
-
-- (instancetype)init {
- if ((self = [super init])) {
- //
- }
- return self;
-}
-
-+ (ObjectivePGP *)sharedInstance {
- static ObjectivePGP *_ObjectivePGP;
- static dispatch_once_t onceToken;
- dispatch_once(&onceToken, ^{
- _ObjectivePGP = [[ObjectivePGP alloc] init];
- });
- return _ObjectivePGP;
-}
-
-+ (PGPKeyring *)defaultKeyring {
- static PGPKeyring *_keyring;
- static dispatch_once_t onceToken;
- dispatch_once(&onceToken, ^{
- _keyring = [[PGPKeyring alloc] init];
- });
- return _keyring;
-}
-
-#pragma mark - Encrypt & Decrypt
-
-+ (nullable NSData *)decrypt:(NSData *)data andVerifySignature:(BOOL)verifySignature usingKeys:(NSArray<PGPKey *> *)keys passphraseForKey:(nullable NSString * _Nullable(^NS_NOESCAPE)(PGPKey * _Nullable key))passphraseForKeyBlock error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(data, NSData);
- PGPAssertClass(keys, NSArray);
-
- // TODO: Decrypt all messages
- let binaryMessage = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:data error:error].firstObject;
- if (!binaryMessage) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Invalid message to decrypt." }];
- }
- return nil;
- }
-
- // parse packets
- var packets = [ObjectivePGP readPacketsFromData:binaryMessage];
- packets = [self decryptPackets:packets usingKeys:keys passphrase:passphraseForKeyBlock error:error];
-
- let literalPacket = PGPCast([[packets pgp_objectsPassingTest:^BOOL(PGPPacket *packet, BOOL *stop) {
- BOOL found = packet.tag == PGPLiteralDataPacketTag;
- *stop = found;
- return found;
- }] firstObject], PGPLiteralPacket);
-
- // Plaintext is available if literalPacket is available
- let plaintextData = literalPacket.literalRawData;
- if (!plaintextData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Nothing to decrypt." }];
- }
- return nil;
- }
-
- // Verify
- if (verifySignature) {
- if (![self verify:binaryMessage withSignature:nil usingKeys:keys passphraseForKey:passphraseForKeyBlock error:error]) {
- if (error && !*error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Unable to verify." }];
- }
- }
- }
-
- return plaintextData;
-}
-
-// Decrypt packets. Passphrase may be related to the key or to the symmetric encrypted message (no key in that keys)
-+ (nullable NSArray<PGPPacket *> *)decryptPackets:(NSArray<PGPPacket *> *)encryptedPackets usingKeys:(NSArray<PGPKey *> *)keys passphrase:(nullable NSString * _Nullable(^NS_NOESCAPE)(PGPKey * _Nullable key))passphraseBlock error:(NSError * __autoreleasing _Nullable *)error {
- // If the Symmetrically Encrypted Data packet is preceded by one or
- // more Symmetric-Key Encrypted Session Key packets, each specifies a
- // passphrase that may be used to decrypt the message. This allows a
- // message to be encrypted to a number of public keys, and also to one
- // or more passphrases.
- PGPSymmetricAlgorithm sessionKeyAlgorithm = UINT8_MAX;
- let packets = [NSMutableArray arrayWithArray:encryptedPackets];
-
- // 1. search for valid and known (do I have specified key?) ESK
- id <PGPEncryptedSessionKeyPacketProtocol> _Nullable eskPacket = nil;
- NSData * _Nullable sessionKeyData = nil;
-
- // Resolve session key: PGPSymetricKeyEncryptedSessionKeyPacket and/or PGPPublicKeyEncryptedSessionKeyPacket is expected
- for (PGPPacket *packet in packets) {
- if (packet.tag == PGPSymetricKeyEncryptedSessionKeyPacketTag) {
- let sESKPacket = PGPCast(packet, PGPSymetricKeyEncryptedSessionKeyPacket);
- sessionKeyAlgorithm = sESKPacket.symmetricAlgorithm;
- sessionKeyData = sESKPacket.encryptedSessionKey;
-
- // The S2K algorithm applied to the passphrase produces the session key for decrypting the file
- let passphrase = passphraseBlock ? passphraseBlock(nil) : nil;
- if (passphrase && !sESKPacket.encryptedSessionKey) {
- sessionKeyData = [sESKPacket.s2k produceSessionKeyWithPassphrase:passphrase symmetricAlgorithm:sESKPacket.symmetricAlgorithm];
- }
-
- eskPacket = sESKPacket;
- }
-
- if (packet.tag == PGPPublicKeyEncryptedSessionKeyPacketTag) {
- let pkESKPacket = PGPCast(packet, PGPPublicKeyEncryptedSessionKeyPacket);
- let decryptionKey = [PGPKeyring findKeyWithKeyID:pkESKPacket.keyID in:keys];
- if (!decryptionKey.secretKey) {
- // Can't proceed with this packet, but there may be other valid packet.
- continue;
- }
-
- // Found (match) secret key is used to decrypt
- PGPSecretKeyPacket * decryptionSecretKeyPacket = PGPCast([decryptionKey.secretKey decryptionPacketForKeyID:pkESKPacket.keyID error:error], PGPSecretKeyPacket);
- if (!decryptionSecretKeyPacket) {
- // Can't proceed with this packet, but there may be other valid packet.
- continue;
- }
-
- // decrypt key with passphrase if encrypted
- if (decryptionSecretKeyPacket && decryptionKey.isEncryptedWithPassword) {
- let passphrase = passphraseBlock ? passphraseBlock(decryptionKey) : nil;
- if (!passphrase) {
- // This is the match but can't proceed with this packet due to missing passphrase.
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorPassphraseRequired userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt with the encrypted key. Decrypt key first." }];
- }
- PGPLogWarning(@"Can't use key \"%@\". Passphrase is required to decrypt.", decryptionSecretKeyPacket.fingerprint);
- return nil;
- }
-
- decryptionSecretKeyPacket = [decryptionSecretKeyPacket decryptedWithPassphrase:passphrase error:error];
- if (!decryptionSecretKeyPacket || (error && *error)) {
- PGPLogWarning(@"Can't use key \"%@\".", decryptionKey.secretKey.fingerprint);
- decryptionSecretKeyPacket = nil;
- continue;
- }
- }
- eskPacket = pkESKPacket;
-
- sessionKeyData = [pkESKPacket decryptSessionKeyData:PGPNN(decryptionSecretKeyPacket) sessionKeyAlgorithm:&sessionKeyAlgorithm error:error];
- NSAssert(sessionKeyAlgorithm < PGPSymmetricMax, @"Invalid session key algorithm");
- }
- }
-
- if (error && *error) {
- return nil;
- }
-
- if (!eskPacket) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Invalid message." }];
- }
- return encryptedPackets;
- }
-
- if (!sessionKeyData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Missing session key" }];
- }
- return encryptedPackets;
- }
-
- // 2
- for (PGPPacket *packet in packets) {
- switch (packet.tag) {
- case PGPSymmetricallyEncryptedIntegrityProtectedDataPacketTag: {
- // decrypt PGPSymmetricallyEncryptedIntegrityProtectedDataPacket
- let symEncryptedDataPacket = PGPCast(packet, PGPSymmetricallyEncryptedIntegrityProtectedDataPacket);
- let decryptedPackets = [symEncryptedDataPacket decryptWithSessionKeyAlgorithm:sessionKeyAlgorithm sessionKeyData:sessionKeyData error:error];
- [packets addObjectsFromArray:decryptedPackets];
- } break;
- case PGPSymmetricallyEncryptedDataPacketTag: {
- let symEncryptedDataPacket = PGPCast(packet, PGPSymmetricallyEncryptedDataPacket);
- let decryptedPackets = [symEncryptedDataPacket decryptWithSessionKeyAlgorithm:sessionKeyAlgorithm sessionKeyData:sessionKeyData error:error];
- [packets addObjectsFromArray:decryptedPackets];
- }
- default:
- break;
- }
- }
-
- if (packets.count == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unable to find valid data to decrypt." }];
- }
- return encryptedPackets;
- }
-
- return packets;
-}
-
-+ (nullable NSData *)encrypt:(NSData *)dataToEncrypt addSignature:(BOOL)shouldSign usingKeys:(NSArray<PGPKey *> *)keys passphraseForKey:(nullable NSString * _Nullable(^NS_NOESCAPE)(PGPKey *key))passphraseForKeyBlock error:(NSError * __autoreleasing _Nullable *)error {
- let publicPartialKeys = [NSMutableArray<PGPPartialKey *> array];
- for (PGPKey *key in keys) {
- [publicPartialKeys pgp_addObject:key.publicKey];
- }
-
- let encryptedMessage = [NSMutableData data];
-
- // PGPPublicKeyEncryptedSessionKeyPacket goes here
- let preferredSymmeticAlgorithm = [PGPPartialKey preferredSymmetricAlgorithmForKeys:publicPartialKeys];
-
- // Random bytes as a string to be used as a key
- NSUInteger keySize = [PGPCryptoUtils keySizeOfSymmetricAlgorithm:preferredSymmeticAlgorithm];
- let sessionKeyData = [PGPCryptoUtils randomData:keySize];
-
- for (PGPPartialKey *publicPartialKey in publicPartialKeys) {
- // Encrypted Message :- Encrypted Data | ESK Sequence, Encrypted Data.
- // Encrypted Data :- Symmetrically Encrypted Data Packet | Symmetrically Encrypted Integrity Protected Data Packet
- // ESK :- Public-Key Encrypted Session Key Packet | Symmetric-Key Encrypted Session Key Packet.
-
- // ESK
- let encryptionKeyPacket = PGPCast([publicPartialKey encryptionKeyPacket:error], PGPPublicKeyPacket);
- if (!encryptionKeyPacket) {
- continue;
- }
-
- let pkESKeyPacket = [[PGPPublicKeyEncryptedSessionKeyPacket alloc] init];
- pkESKeyPacket.keyID = encryptionKeyPacket.keyID;
- pkESKeyPacket.publicKeyAlgorithm = encryptionKeyPacket.publicKeyAlgorithm;
- BOOL encrypted = [pkESKeyPacket encrypt:encryptionKeyPacket sessionKeyData:sessionKeyData sessionKeyAlgorithm:preferredSymmeticAlgorithm error:error];
- if (!encrypted || (error && *error)) {
- PGPLogDebug(@"Failed encrypt Symmetric-key Encrypted Session Key packet. Error: %@", error ? *error : @"Unknown");
- return nil;
- }
- [encryptedMessage pgp_appendData:[pkESKeyPacket export:error]];
- if (error && *error) {
- PGPLogDebug(@"Missing literal data. Error: %@", error ? *error : @"Unknown");
- return nil;
- }
-
- // TODO: find the compression type most common to the used keys
- }
-
- NSData *content;
- if (shouldSign) {
- // sign data if requested
- let signKeys = [NSMutableArray<PGPKey *> array];
- for (PGPKey* key in keys){
- if (key.secretKey && key.signingSecretKey != NULL){
- [signKeys addObject:key];
- }
-
- }
- content = [self sign:dataToEncrypt detached:NO usingKeys:signKeys passphraseForKey:passphraseForKeyBlock error:error];
- } else {
- // Prepare literal packet
- let literalPacket = [PGPLiteralPacket literalPacket:PGPLiteralPacketBinary withData:dataToEncrypt];
- literalPacket.filename = nil;
- literalPacket.timestamp = NSDate.date;
-
- let literalPacketData = [literalPacket export:error];
- if (error && *error) {
- PGPLogDebug(@"Missing literal packet data. Error: %@", *error);
- return nil;
- }
-
- // FIXME: do not use hardcoded value for compression type
- let compressedPacket = [[PGPCompressedPacket alloc] initWithData:literalPacketData type:PGPCompressionZLIB];
- content = [compressedPacket export:error];
- }
-
- if (!content || (error && *error)) {
- return nil;
- }
-
- let symEncryptedDataPacket = [[PGPSymmetricallyEncryptedIntegrityProtectedDataPacket alloc] init];
- [symEncryptedDataPacket encrypt:content symmetricAlgorithm:preferredSymmeticAlgorithm sessionKeyData:sessionKeyData error:error];
-
- if (error && *error) {
- return nil;
- }
-
- [encryptedMessage pgp_appendData:[symEncryptedDataPacket export:error]];
- if (error && *error) {
- return nil;
- }
-
- return encryptedMessage;
-}
-
-#pragma mark - Sign & Verify
-
-+ (nullable NSData *)sign:(NSData *)data detached:(BOOL)detached usingKeys:(NSArray<PGPKey *> *)keys passphraseForKey:(nullable NSString * _Nullable(^NS_NOESCAPE)(PGPKey *key))passphraseBlock error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(data, NSData);
- PGPAssertClass(keys, NSArray);
-
- // TODO: Use prefered hash alhorithm for key
- PGPHashAlgorithm preferedHashAlgorithm = PGPHashSHA512;
-
- // Calculate signatures signatures
- let signatures = [NSMutableArray<PGPSignaturePacket *> array];
- for (PGPKey *key in keys) {
- // Signed Message :- Signature Packet, Literal Message
- let signaturePacket = [PGPSignaturePacket signaturePacket:PGPSignatureBinaryDocument hashAlgorithm:preferedHashAlgorithm];
- let passphrase = passphraseBlock ? passphraseBlock(key) : nil;
- if (![signaturePacket signData:data withKey:key subKey:nil passphrase:passphrase userID:nil error:error]) {
- PGPLogDebug(@"Can't sign data");
- continue;
- }
-
- [signatures pgp_addObject:signaturePacket];
- }
-
- let outputData = [NSMutableData data];
-
- // Detached - export only signatures
- if (detached) {
- for (PGPSignaturePacket *signaturePacket in signatures) {
- NSError *exportError = nil;
- let _Nullable signaturePacketData = [signaturePacket export:&exportError];
- if (exportError) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Unable to sign. Can't create signature packet." }];
- }
- continue;
- }
- [outputData appendData:signaturePacketData];
- }
- // Detached return early with just signature packets.
- return outputData;
- }
-
- // Otherwise create sequence of:
- // OnePassSignature-Literal-Signature
- // Order: 1,2,3-Literal-3,2,1
-
- // Add One Pass Signature in order
- for (PGPSignaturePacket *signaturePacket in signatures) {
- // One Pass signature
- let onePassPacket = [[PGPOnePassSignaturePacket alloc] init];
- onePassPacket.signatureType = signaturePacket.type;
- onePassPacket.publicKeyAlgorithm = signaturePacket.publicKeyAlgorithm;
- onePassPacket.hashAlgorith = signaturePacket.hashAlgoritm;
- onePassPacket.keyID = PGPNN(signaturePacket.issuerKeyID);
- onePassPacket.isNested = NO;
- NSError * _Nullable onePassExportError = nil;
- [outputData pgp_appendData:[onePassPacket export:&onePassExportError]];
- if (onePassExportError) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing one signature passphrase data" }];
- }
- return nil;
- }
- }
-
- // Literal
- let literalPacket = [PGPLiteralPacket literalPacket:PGPLiteralPacketBinary withData:data];
- literalPacket.filename = nil;
- literalPacket.timestamp = [NSDate date];
-
- NSError *literalExportError = nil;
- [outputData pgp_appendData:[literalPacket export:&literalExportError]];
- if (literalExportError) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing literal data" }];
- }
- return nil;
- }
-
-// // Compressed
-// NSError *literalExportError = nil;
-// PGPCompressedPacket *compressedPacket = [[PGPCompressedPacket alloc] initWithData:[literalPacket exportPacket:&literalExportError] type:PGPCompressionBZIP2];
-// NSAssert(!literalExportError, @"Missing literal data");
-// if (literalExportError) {
-// if (error) {
-// *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Missing literal data"}];
-// }
-// return nil;
-// }
-//
-// NSError *compressedExportError = nil;
-// [signedMessage pgp_appendData:[compressedPacket exportPacket:&compressedExportError]];
-// NSAssert(!compressedExportError, @"Missing compressed data");
-// if (compressedExportError) {
-// if (error) {
-// *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Missing compressed data"}];
-// }
-// return nil;
-// }
-
- // Add in reversed-order
- for (PGPSignaturePacket *signaturePacket in [[signatures reverseObjectEnumerator] allObjects]) {
- // Signature coresponding to One Pass signature
- NSError *exportError = nil;
- let _Nullable signaturePacketData = [signaturePacket export:&exportError];
- if (exportError) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Unable to sign. Can't create signature packet." }];
- }
- return nil;
- }
- [outputData pgp_appendData:signaturePacketData];
- }
- return outputData;
-}
-
-+ (BOOL)verify:(NSData *)signedData withSignature:(nullable NSData *)detachedSignature usingKeys:(NSArray<PGPKey *> *)keys passphraseForKey:(nullable NSString * _Nullable(^NS_NOESCAPE)(PGPKey *key))passphraseForKeyBlock error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(signedData, NSData);
-
- let binaryMessages = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:signedData error:error];
- // TODO: Process all messages
- let binarySignedData = binaryMessages.count > 0 ? binaryMessages.firstObject : nil;
- if (!binarySignedData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Invalid input data" }];
- }
- return NO;
- }
-
- // Use detached signature if provided.
- // In that case treat input data as blob to be verified with the signature. Don't parse it.
- if (detachedSignature) {
- let binarydetachedSignature = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:detachedSignature error:error].firstObject;
- if (binarydetachedSignature) {
- let packet = [PGPPacketFactory packetWithData:binarydetachedSignature offset:0 consumedBytes:nil];
- let signaturePacket = PGPCast(packet, PGPSignaturePacket);
- let issuerKeyID = signaturePacket.issuerKeyID;
- if (issuerKeyID) {
- let issuerKey = [PGPKeyring findKeyWithKeyID:issuerKeyID in:keys];
- return [signaturePacket verifyData:binarySignedData publicKey:issuerKey error:error];
- }
- }
- return NO;
- }
-
- // Otherwise treat input data as PGP Message and process for literal data.
-
- // Propably not the best solution when it comes to memory consumption.
- // Literal data is copied more than once (first at parse phase, then when is come to build signature packet data.
- // I belive this is unecessary but require more work. Schedule to v2.0.
-
- // search for signature packet
- var accumulatedPackets = [NSMutableArray<PGPPacket *> array];
- NSUInteger offset = 0;
- NSUInteger consumedBytes = 0;
-
- @autoreleasepool {
- // TODO: don't parse data here, get raw data and pass to verify:withsignature:
- while (offset < binarySignedData.length) {
- let packet = [PGPPacketFactory packetWithData:binarySignedData offset:offset consumedBytes:&consumedBytes];
- [accumulatedPackets pgp_addObject:packet];
- offset += consumedBytes;
- }
- }
-
- //Try to decrypt first, in case of encrypted message inside
- //Not every message needs decryption though! Check for ESK to reason about it
- BOOL isEncrypted = [[accumulatedPackets pgp_objectsPassingTest:^BOOL(PGPPacket *packet, BOOL *stop) {
- BOOL found = (packet.tag == PGPPublicKeyEncryptedSessionKeyPacketTag) || (packet.tag == PGPSymetricKeyEncryptedSessionKeyPacketTag);
- *stop = found;
- return found;
- }] firstObject] != nil;
-
- if (isEncrypted) {
- NSError *decryptError = nil;
- accumulatedPackets = [[self.class decryptPackets:accumulatedPackets usingKeys:keys passphrase:passphraseForKeyBlock error:&decryptError] mutableCopy];
- if (decryptError) {
- if (error) {
- *error = [decryptError copy];
- }
- return NO;
- }
- }
-
- // PGPSignaturePacket * _Nullable signaturePacket = nil;
- let signatures = [NSMutableArray<PGPSignaturePacket *> array];
- PGPLiteralPacket * _Nullable literalPacket = nil;
-
- int onePassSignatureCount = 0;
- int signatureCount = 0;
- for (PGPPacket *packet in accumulatedPackets) {
- switch (packet.tag) {
- case PGPCompressedDataPacketTag:
- // ignore here
- break;
- case PGPOnePassSignaturePacketTag:
- // ignore here, but should check if the number of one-pass-sig is equal to attached signatures
- onePassSignatureCount++;
- break;
- case PGPLiteralDataPacketTag:
- literalPacket = PGPCast(packet, PGPLiteralPacket);
- break;
- case PGPSignaturePacketTag: {
- let signaturePacket = PGPCast(packet, PGPSignaturePacket);
- [signatures pgp_addObject:signaturePacket];
- signatureCount++;
- }
- break;
- default:
- break;
- }
- }
-
- if (onePassSignatureCount != signatureCount) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorMissingSignature userInfo:@{ NSLocalizedDescriptionKey: @"Message is not properly signed." }];
- }
- return NO;
- }
-
- if (signatures.count == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorNotSigned userInfo:@{ NSLocalizedDescriptionKey: @"Message is not signed." }];
- }
- return NO;
- }
-
- if (!literalPacket) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Message is not valid. Missing literal data." }];
- }
- return NO;
- }
-
-
- // Validate signatures
- BOOL isValid = YES;
-
- for (PGPSignaturePacket *signaturePacket in signatures) {
- if (!isValid) {
- continue;
- }
-
- let signedLiteralData = literalPacket.literalRawData;
- isValid = signedLiteralData && (!error || (error && *error == nil));
- if (isValid) {
- let issuerKeyID = signaturePacket.issuerKeyID;
- isValid = issuerKeyID != nil;
- if (isValid) {
- let issuerKey = [PGPKeyring findKeyWithKeyID:issuerKeyID in:keys];
- isValid = issuerKey != nil;
- if (!isValid) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Unable to check signature. No public key." }];
- }
- continue;
- }
- isValid = isValid && [signaturePacket verifyData:signedLiteralData publicKey:issuerKey error:error];
- }
- }
- }
-
- return isValid;
-}
-
-+ (nullable NSArray<PGPKey *> *)readKeysFromPath:(NSString *)path error:(NSError * __autoreleasing _Nullable *)error {
- NSString *fullPath = [path stringByExpandingTildeInPath];
-
- BOOL isDirectory = NO;
- if (![[NSFileManager defaultManager] fileExistsAtPath:fullPath isDirectory:&isDirectory] || isDirectory) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{NSLocalizedDescriptionKey: @"Can't read keys. Invalid input."}];
- }
- return nil;
- }
-
- let fileData = [NSData dataWithContentsOfFile:fullPath options:NSDataReadingMappedIfSafe | NSDataReadingUncached error:error];
- if (!fileData || (error && *error)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{NSLocalizedDescriptionKey: @"Can't read keys. Invalid input."}];
- }
- return nil;
- }
-
- return [self readKeysFromData:fileData error:error];
-}
-
-+ (nullable NSArray<PGPKey *> *)readKeysFromData:(NSData *)fileData error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(fileData, NSData);
-
- var keys = [NSArray<PGPKey *> array];
-
- if (fileData.length == 0) {
- PGPLogError(@"Empty input data");
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{NSLocalizedDescriptionKey: @"Can't read keys. Invalid input."}];
- }
- return keys;
- };
-
- let binRingData = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:fileData error:error];
- if (!binRingData || binRingData.count == 0) {
- PGPLogError(@"Invalid input data");
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{NSLocalizedDescriptionKey: @"Can't read keys. Invalid input."}];
- }
- return keys;
- }
-
- for (NSData *data in binRingData) {
- let readPartialKeys = [self readPartialKeysFromData:data];
- for (PGPPartialKey *key in readPartialKeys) {
- keys = [PGPKeyring addOrUpdatePartialKey:key inContainer:keys];
- }
- }
-
- return keys;
-}
-
-+ (nullable NSArray<PGPKeyID *> *)recipientsKeyIDForMessage:(NSData *)data error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(data, NSData);
-
- // TODO: Decrypt all messages
- let binaryMessage = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:data error:error].firstObject;
- if (!binaryMessage) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Invalid message to decrypt." }];
- }
- return nil;
- }
-
- // parse packets
- let foundKeys = [NSMutableOrderedSet<PGPKeyID *> orderedSetWithCapacity:1];
- var packets = [ObjectivePGP readPacketsFromData:binaryMessage];
- for (PGPPacket *packet in packets) {
- switch (packet.tag) {
- case PGPPublicKeyEncryptedSessionKeyPacketTag: {
- let publicKeyEncrypteSessionKey = PGPCast(packet, PGPPublicKeyEncryptedSessionKeyPacket);
- [foundKeys addObject:publicKeyEncrypteSessionKey.keyID];
- } break;
- default:
- break;
- }
- }
- return foundKeys.count > 0 ? foundKeys.array : nil;
-}
-
-#pragma mark - Private
-
-+ (NSArray<PGPPacket *> *)readPacketsFromData:(NSData *)keyringData {
- PGPAssertClass(keyringData, NSData);
-
- if (keyringData.length == 0) {
- return @[];
- }
-
- let accumulatedPackets = [NSMutableArray<PGPPacket *> array];
- NSUInteger offset = 0;
- NSUInteger consumedBytes = 0;
-
- while (offset < keyringData.length) {
- let packet = [PGPPacketFactory packetWithData:keyringData offset:offset consumedBytes:&consumedBytes];
- [accumulatedPackets pgp_addObject:packet];
-
- // corrupted data. Move by one byte in hope we find some packet there, or EOF.
- if (consumedBytes == 0) {
- offset++;
- }
- offset += consumedBytes;
- }
-
- return accumulatedPackets;
-}
-
-+ (NSArray<PGPPartialKey *> *)readPartialKeysFromData:(NSData *)messageData {
- let partialKeys = [NSMutableArray<PGPPartialKey *> array];
- let accumulatedPackets = [NSMutableArray<PGPPacket *> array];
- NSUInteger position = 0;
- NSUInteger consumedBytes = 0;
-
- while (position < messageData.length) {
- @autoreleasepool {
- let packet = [PGPPacketFactory packetWithData:messageData offset:position consumedBytes:&consumedBytes];
- if (!packet) {
- position += (consumedBytes > 0) ? consumedBytes : 1;
- continue;
- }
-
- if ((accumulatedPackets.count > 1) && ((packet.tag == PGPPublicKeyPacketTag) || (packet.tag == PGPSecretKeyPacketTag))) {
- let partialKey = [[PGPPartialKey alloc] initWithPackets:accumulatedPackets];
- [partialKeys addObject:partialKey];
- [accumulatedPackets removeAllObjects];
- }
-
- [accumulatedPackets pgp_addObject:packet];
- position += consumedBytes;
- }
- }
-
- if (accumulatedPackets.count > 1) {
- let key = [[PGPPartialKey alloc] initWithPackets:accumulatedPackets];
- [partialKeys addObject:key];
- [accumulatedPackets removeAllObjects];
- }
-
- return partialKeys;
-}
-
-// NEW FUNCTIONS
-+ (NSData*) transformKey: (NSString *) string{
- NSMutableDictionary *headers = [@{@"Comment": @"Created with ObjectivePGP",
- @"Charset": @"UTF-8"} mutableCopy];
- NSMutableString *headerString = [NSMutableString stringWithString:@"-----"];
- NSMutableString *footerString = [NSMutableString stringWithString:@"-----"];
- [headerString appendString:@"BEGIN PGP PUBLIC KEY BLOCK"];
- [footerString appendString:@"END PGP PUBLIC KEY BLOCK"];
- [headerString appendString:@"-----\n"];
- [footerString appendString:@"-----\n"];
- NSMutableString *armoredMessage = [NSMutableString string];
- // - An Armor Header Line, appropriate for the type of data
- [armoredMessage appendString:headerString];
-
- // - Armor Headers
- for (NSString *key in headers.allKeys) {
- [armoredMessage appendFormat:@"%@: %@\n", key, headers[key]];
- }
- // - A blank (zero-length, or containing only whitespace) line
- [armoredMessage appendString:@"\n"];
- [armoredMessage appendString:string];
- [armoredMessage appendString:@"\n"];
-
- // - An Armor Checksum
- NSData *binaryData = [[NSData alloc] initWithBase64EncodedString:string options:NSDataBase64DecodingIgnoreUnknownCharacters];
- UInt32 checksum = [binaryData pgp_CRC24];
- UInt8 c[3]; // 24 bit
- c[0] = checksum >> 16;
- c[1] = checksum >> 8;
- c[2] = checksum;
- NSData *checksumData = [NSData dataWithBytes:&c length:sizeof(c)];
- [armoredMessage appendString:@"="];
- [armoredMessage appendString:[checksumData base64EncodedStringWithOptions:(NSDataBase64Encoding76CharacterLineLength | NSDataBase64EncodingEndLineWithLineFeed)]];
- [armoredMessage appendString:@"\n"];
-
- // - The Armor Tail, which depends on the Armor Header Line
- [armoredMessage appendString:footerString];
-
- NSData *armoredData = [armoredMessage dataUsingEncoding:NSASCIIStringEncoding];
- return armoredData;
-}
-
-+ (nullable NSData *)symmetricEncrypt:(NSData *)dataToEncrypt signWithKey:(nullable PGPKey *)signKey encryptionKey: (nullable NSString *) key passphrase:(nullable NSString *)passphrase armored:(BOOL)armored error:(NSError *__autoreleasing _Nullable *)error {
- let encryptedMessage = [NSMutableData data];
- let symAlgo = PGPSymmetricAES128;
- let s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierIteratedAndSalted hashAlgorithm:PGPHashSHA256];
-
- PGPSymetricKeyEncryptedSessionKeyPacket *symEncKeyPacket = [[PGPSymetricKeyEncryptedSessionKeyPacket alloc] init];
- symEncKeyPacket.version = 4;
- symEncKeyPacket.symmetricAlgorithm = symAlgo;
- symEncKeyPacket.s2k = s2k;
-
- let sessionKeyData = [s2k produceSessionKeyWithPassphrase:passphrase symmetricAlgorithm:symAlgo];
-
- [encryptedMessage pgp_appendData: [symEncKeyPacket export:error]];
-
- NSData *content;
- // sign data if requested
- if (signKey) {
- //TODO
-
- } else {
- // Prepare literal packet
- let literalPacket = [PGPLiteralPacket literalPacket:PGPLiteralPacketBinary withData:dataToEncrypt];
- literalPacket.filename = nil;
- literalPacket.timestamp = [NSDate date];
- PGPLogWarning(@"Missing literal data");
- if (error && *error) {
- return nil;
- }
- let literalPacketData = [literalPacket export:error];
- if (error && *error) {
- return nil;
- }
-
- let compressedPacket = [[PGPCompressedPacket alloc] initWithData:literalPacketData type:PGPCompressionZIP];
- content = [compressedPacket export:error];
- if (error && *error) {
- return nil;
- }
- }
-
- let symEncryptedDataPacket = [[PGPSymmetricallyEncryptedIntegrityProtectedDataPacket alloc] init];
- [symEncryptedDataPacket encrypt:content symmetricAlgorithm:symEncKeyPacket.symmetricAlgorithm sessionKeyData:sessionKeyData error:error];
-
- if (error && *error) {
- return nil;
- }
-
- [encryptedMessage pgp_appendData:[symEncryptedDataPacket export:error]];
-
- if (error && *error) {
- return nil;
- }
-
- if (armored) {
- NSString* msg = [PGPArmor armored:encryptedMessage as:PGPArmorMessage];
- return [msg dataUsingEncoding:NSUTF8StringEncoding];
- }
- return encryptedMessage;
-}
-+ (nullable NSData *)symmetricDecrypt:(NSData *)messageDataToDecrypt key:(nullable NSString *)encKey verifyWithKey:(nullable PGPKey *)key signed:(nullable BOOL *)isSigned valid:(nullable BOOL *)isValid integrityProtected:(nullable BOOL *)isIntegrityProtected error:(NSError *__autoreleasing _Nullable *)error {
- PGPAssertClass(messageDataToDecrypt, NSData);
-
- let binaryMessages = [PGPArmor convertArmoredMessage2BinaryBlocksWhenNecessary:messageDataToDecrypt error:error];
-
- // decrypt first message only
- let binaryMessageToDecrypt = binaryMessages.count > 0 ? binaryMessages.firstObject : nil;
- if (!binaryMessageToDecrypt) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Invalid input data" }];
- }
- return nil;
- }
-
- // parse packets
- var packets = [self readPacketsFromData:binaryMessageToDecrypt];
- PGPSymetricKeyEncryptedSessionKeyPacket *sessionKey = nil;
- for (PGPPacket *packet in packets) {
- if (packet.tag == PGPSymetricKeyEncryptedSessionKeyPacketTag){
- sessionKey = PGPCast(packet, PGPSymetricKeyEncryptedSessionKeyPacket);
- break;
- }
- }
-
- NSAssert(sessionKey, @"Missing session key data");
- if (!sessionKey) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Missing session key data" }];
- }
- return nil;
- }
-
- // 2
-
- NSAssert(sessionKey.s2k, @"Missing s2k data\n");
- if (sessionKey.s2k == nil){
- if (error){
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Missing s2k data" }];
- }
- return nil;
- }
- let sessionKeyData = [sessionKey.s2k produceSessionKeyWithPassphrase: encKey symmetricAlgorithm:sessionKey.symmetricAlgorithm];
-
- for (PGPPacket *packet in packets) {
- switch (packet.tag) {
- case PGPSymmetricallyEncryptedIntegrityProtectedDataPacketTag: {
- // decrypt PGPSymmetricallyEncryptedIntegrityProtectedDataPacket
- let symEncryptedDataPacket = PGPCast(packet, PGPSymmetricallyEncryptedIntegrityProtectedDataPacket);
- packets = [symEncryptedDataPacket decryptWithSessionKeyAlgorithm:sessionKey.symmetricAlgorithm sessionKeyData:sessionKeyData error:error];
- } break;
- default:
- break;
- }
- }
-
- if (packets.count == 0) {
- return nil;
- }
-
- PGPLiteralPacket * _Nullable literalPacket = nil;
- PGPSignaturePacket * _Nullable signaturePacket = nil;
- for (PGPPacket *packet in packets) {
- switch (packet.tag) {
- case PGPCompressedDataPacketTag:
- case PGPOnePassSignaturePacketTag:
- // ignore here
- break;
- case PGPLiteralDataPacketTag:
- literalPacket = PGPCast(packet, PGPLiteralPacket);
- break;
- case PGPSignaturePacketTag:
- signaturePacket = PGPCast(packet, PGPSignaturePacket);
- break;
- default:
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unknown packet (expected literal or compressed)" }];
- }
- return nil;
- }
- }
-
- BOOL dataIsSigned = signaturePacket != nil;
- if (isSigned) { *isSigned = dataIsSigned; }
-
- // available if literalPacket is available
- let _Nullable plaintextData = literalPacket.literalRawData;
- if (!plaintextData) {
- return nil;
- }
-
- BOOL dataIsValid = NO;
- if (signaturePacket && key.publicKey) {
- // TODO
- }
- if (isValid) { *isValid = dataIsValid; }
-
- return plaintextData;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
-
diff --git a/enzevalos_iphone/ObjectivePGP/PGPArmor.m b/enzevalos_iphone/ObjectivePGP/PGPArmor.m
deleted file mode 100755
index 4cf3ae3b66389d2946e8ea3678e3ca8509c36b8a..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPArmor.m
+++ /dev/null
@@ -1,256 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPArmor.h"
-#import "PGPPacket.h"
-
-#import "NSData+PGPUtils.h"
-#import "NSArray+PGPUtils.h"
-
-#import "PGPFoundation.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPArmor
-
-+ (BOOL)isArmoredData:(NSData *)data {
- PGPAssertClass(data, NSData);
-
- // detect if armored, check for string -----BEGIN PGP
- NSString *str = [[NSString alloc] initWithData:data encoding:NSUTF8StringEncoding];
- if (str && [str hasPrefix:@"-----BEGIN PGP"]) {
- return YES;
- }
- return NO;
-}
-
-+ (NSString *)armored:(NSData *)data as:(PGPArmorType)type {
- return [[self class] armored:data as:type part:NSUIntegerMax of:NSUIntegerMax];
-}
-
-+ (NSString *)armored:(NSData *)data as:(PGPArmorType)type part:(NSUInteger)part of:(NSUInteger)ofParts {
- NSMutableDictionary *headers = [@{ @"Version": @"ObjectivePGP", @"Comment": @"https://www.objectivepgp.com", @"Charset": @"UTF-8" } mutableCopy];
-
- NSMutableString *headerString = [NSMutableString stringWithString:@"-----"];
- NSMutableString *footerString = [NSMutableString stringWithString:@"-----"];
- switch (type) {
- case PGPArmorPublicKey:
- [headerString appendString:@"BEGIN PGP PUBLIC KEY BLOCK"];
- [footerString appendString:@"END PGP PUBLIC KEY BLOCK"];
- break;
- case PGPArmorSecretKey:
- [headerString appendString:@"BEGIN PGP PRIVATE KEY BLOCK"];
- [footerString appendString:@"END PGP PRIVATE KEY BLOCK"];
- break;
- case PGPArmorSignature:
- [headerString appendString:@"BEGIN PGP SIGNATURE"];
- [footerString appendString:@"END PGP SIGNATURE"];
- break;
- case PGPArmorMessage:
- [headerString appendString:@"BEGIN PGP MESSAGE"];
- [footerString appendString:@"END PGP MESSAGE"];
- break;
- case PGPArmorMultipartMessagePartX:
- [headerString appendFormat:@"BEGIN PGP MESSAGE, PART %@", @(part)];
- [footerString appendFormat:@"END PGP MESSAGE, PART %@", @(part)];
- break;
- case PGPArmorMultipartMessagePartXOfY:
- [headerString appendFormat:@"BEGIN PGP MESSAGE, PART %@/%@", @(part), @(ofParts)];
- [footerString appendFormat:@"END PGP MESSAGE, PART %@/%@", @(part), @(ofParts)];
- break;
- default:
- NSAssert(true, @"Message type not supported");
- break;
- }
-
- [headerString appendString:@"-----\n"];
- [footerString appendString:@"-----\n"];
-
- NSMutableString *armoredMessage = [NSMutableString string];
- // - An Armor Header Line, appropriate for the type of data
- [armoredMessage appendString:headerString];
-
- // - Armor Headers
- for (NSString *key in headers.allKeys) {
- [armoredMessage appendFormat:@"%@: %@\n", key, headers[key]];
- }
-
- // - A blank (zero-length, or containing only whitespace) line
- [armoredMessage appendString:@"\n"];
-
- // - The ASCII-Armored data
- NSString *radix64 = [data base64EncodedStringWithOptions:NSDataBase64Encoding76CharacterLineLength | NSDataBase64EncodingEndLineWithLineFeed];
- [armoredMessage appendString:radix64];
- [armoredMessage appendString:@"\n"];
-
- // - An Armor Checksum
- UInt32 checksum = [data pgp_CRC24];
- UInt8 c[3]; // 24 bit
- c[0] = (UInt8)(checksum >> 16);
- c[1] = (UInt8)(checksum >> 8);
- c[2] = (UInt8)checksum;
-
- NSData *checksumData = [NSData dataWithBytes:&c length:sizeof(c)];
- [armoredMessage appendString:@"="];
- [armoredMessage appendString:[checksumData base64EncodedStringWithOptions:NSDataBase64Encoding76CharacterLineLength | NSDataBase64EncodingEndLineWithLineFeed]];
- [armoredMessage appendString:@"\n"];
-
- // - The Armor Tail, which depends on the Armor Header Line
- [armoredMessage appendString:footerString];
- return armoredMessage;
-};
-
-+ (nullable NSData *)readArmored:(NSString *)string error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(string, NSString);
-
- NSScanner *scanner = [[NSScanner alloc] initWithString:string];
- scanner.charactersToBeSkipped = nil;
-
- // check header line
- NSString *headerLine = nil;
- [scanner scanUpToCharactersFromSet:[NSCharacterSet newlineCharacterSet] intoString:&headerLine];
- if (!PGPEqualObjects(headerLine, @"-----BEGIN PGP MESSAGE-----") && !PGPEqualObjects(headerLine, @"-----BEGIN PGP PUBLIC KEY BLOCK-----") && !PGPEqualObjects(headerLine, @"-----BEGIN PGP PRIVATE KEY BLOCK-----") && !PGPEqualObjects(headerLine, @"-----BEGIN PGP SECRET KEY BLOCK-----") && // PGP 2.x generates the header "BEGIN PGP SECRET KEY BLOCK" instead of "BEGIN PGP PRIVATE KEY BLOCK"
- !PGPEqualObjects(headerLine, @"-----BEGIN PGP SIGNATURE-----") && ![headerLine hasPrefix:@"-----BEGIN PGP MESSAGE, PART"]) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Invalid header" }];
- }
- return nil;
- }
-
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
-
- NSString *line = nil;
-
- if (![scanner scanCharactersFromSet:[NSCharacterSet newlineCharacterSet] intoString:nil]) {
- // Scan headers (Optional)
- [scanner scanUpToCharactersFromSet:[[NSCharacterSet newlineCharacterSet] invertedSet] intoString:nil];
-
- while ([scanner scanCharactersFromSet:[[NSCharacterSet newlineCharacterSet] invertedSet] intoString:&line]) {
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
- }
- }
-
- // skip blank line
- [scanner scanCharactersFromSet:[NSCharacterSet newlineCharacterSet] intoString:nil];
-
- // read base64 data
- BOOL base64Section = YES;
- NSMutableString *base64String = [NSMutableString string];
- while (base64Section && [scanner scanCharactersFromSet:[[NSCharacterSet newlineCharacterSet] invertedSet] intoString:&line]) {
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
-
- if ([line hasPrefix:@"="]) {
- scanner.scanLocation = scanner.scanLocation - (line.length + 2);
- base64Section = NO;
- } else {
- [base64String appendFormat:@"%@\n", line];
- }
- }
-
- // read checksum
- NSString *checksumString = nil;
- [scanner scanUpToCharactersFromSet:[[NSCharacterSet newlineCharacterSet] invertedSet] intoString:&line];
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
-
- if ([scanner scanString:@"=" intoString:nil]) {
- [scanner scanUpToCharactersFromSet:[NSCharacterSet newlineCharacterSet] intoString:&checksumString];
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
- }
-
- // read footer
- BOOL footerMatchHeader = NO;
- [scanner scanUpToCharactersFromSet:[NSCharacterSet newlineCharacterSet] intoString:&line];
- // consume newline
- [scanner scanString:@"\r" intoString:nil];
- [scanner scanString:@"\n" intoString:nil];
-
- if ([line hasSuffix:[headerLine substringFromIndex:12]]) {
- footerMatchHeader = YES;
- }
-
- if (!footerMatchHeader) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Footer don't match to header" }];
- }
- return nil;
- }
-
- // binary data from base64 part
- NSData *binaryData = [[NSData alloc] initWithBase64EncodedString:base64String options:NSDataBase64DecodingIgnoreUnknownCharacters];
-
- // The checksum with its leading equal sign MAY appear on the first line after the base64 encoded data.
- // validate checksum
- if (checksumString) {
- let readChecksumData = [[NSData alloc] initWithBase64EncodedString:checksumString options:NSDataBase64DecodingIgnoreUnknownCharacters];
-
- UInt32 calculatedCRC24 = [binaryData pgp_CRC24];
- calculatedCRC24 = CFSwapInt32HostToBig(calculatedCRC24);
- calculatedCRC24 = calculatedCRC24 >> 8;
- let calculatedCRC24Data = [NSData dataWithBytes:&calculatedCRC24 length:3];
- if (!PGPEqualObjects(calculatedCRC24Data, readChecksumData)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Checksum mismatch" }];
- }
- return nil;
- }
- }
- return binaryData;
-}
-
-+ (nullable NSArray<NSData *> *)convertArmoredMessage2BinaryBlocksWhenNecessary:(NSData *)binOrArmorData error:(NSError * __autoreleasing _Nullable *)error {
- let binRingData = binOrArmorData;
- // detect if armored, check for string -----BEGIN PGP
- if ([PGPArmor isArmoredData:binRingData]) {
- var armoredString = [[NSString alloc] initWithData:binRingData encoding:NSUTF8StringEncoding];
-
- // replace \n to \r\n
- // propably unecessary since armore code care about \r\n or \n as newline sentence
- armoredString = [armoredString stringByReplacingOccurrencesOfString:@"\r\n" withString:@"\n"];
- armoredString = [armoredString stringByReplacingOccurrencesOfString:@"\n" withString:@"\r\n"];
-
- let extractedBlocks = [[NSMutableArray<NSString *> alloc] init];
- let regex = [[NSRegularExpression alloc] initWithPattern:@"(-----)(BEGIN|END)[ ](PGP)[A-Z ]*(-----)" options:NSRegularExpressionDotMatchesLineSeparators error:nil];
- __block NSInteger offset = 0;
- [regex enumerateMatchesInString:armoredString options:NSMatchingReportCompletion range:NSMakeRange(0, armoredString.length) usingBlock:^(NSTextCheckingResult *_Nullable result, __unused NSMatchingFlags flags, __unused BOOL *stop) {
- let substring = [armoredString substringWithRange:result.range];
- if ([substring containsString:@"END"]) {
- NSInteger endIndex = result.range.location + result.range.length;
- [extractedBlocks addObject:[armoredString substringWithRange:NSMakeRange(offset, endIndex - offset)]];
- } else if ([substring containsString:@"BEGIN"]) {
- offset = result.range.location;
- }
- }];
-
- let extractedData = [[NSMutableArray<NSData *> alloc] init];
- for (NSString *extractedString in extractedBlocks) {
- let armodedData = [PGPArmor readArmored:extractedString error:error];
- if (error && *error) {
- return nil;
- }
-
- [extractedData pgp_addObject:armodedData];
- }
- return extractedData;
- }
- return @[binRingData];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPBigNum.m b/enzevalos_iphone/ObjectivePGP/PGPBigNum.m
deleted file mode 100755
index e95412755271d52c8de6c2335720892d1d9f86d0..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPBigNum.m
+++ /dev/null
@@ -1,76 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPBigNum.h"
-#import "PGPBigNum+Private.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPBigNum
-
-- (instancetype)initWithBIGNUM:(BIGNUM *)bignumRef {
- NSParameterAssert(bignumRef);
-
- if ((self = [super init])) {
- _bignumRef = BN_dup(bignumRef);
- }
- return self;
-}
-
-- (int)bitsCount {
- return BN_num_bits(self.bignumRef);
-}
-
-- (int)bytesCount {
- return BN_num_bytes(self.bignumRef);
-}
-
-- (NSData *)data {
- let buflen = (size_t)self.bytesCount;
- let buf = calloc(buflen, 1);
- pgp_defer { if (buf) { free(buf); } };
- BN_bn2bin(self.bignumRef, buf);
- return [NSData dataWithBytes:buf length:buflen];
-}
-
-- (void)dealloc {
- BN_clear_free(_bignumRef);
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToBigNum:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToBigNum:(PGPBigNum *)other {
- return BN_cmp(self.bignumRef, other.bignumRef) == 0;
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
- result = prime * result + self.data.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- return [[self.class allocWithZone:zone] initWithBIGNUM:BN_dup(self.bignumRef)];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPCryptoCFB.m b/enzevalos_iphone/ObjectivePGP/PGPCryptoCFB.m
deleted file mode 100755
index 74366d49e5d677234bdbd3ac5516b2ee0bce324a..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPCryptoCFB.m
+++ /dev/null
@@ -1,196 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPCryptoCFB.h"
-#import "NSData+PGPUtils.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPCryptoUtils.h"
-#import "PGPS2K.h"
-#import "PGPTypes.h"
-#import "PGPMacros+Private.h"
-#import "PGPLogging.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <CommonCrypto/CommonCryptor.h>
-#import <CommonCrypto/CommonDigest.h>
-
-#import <openssl/aes.h>
-#import <openssl/blowfish.h>
-#import <openssl/camellia.h>
-#import <openssl/cast.h>
-#import <openssl/des.h>
-#import <openssl/idea.h>
-#import <openssl/sha.h>
-
-#import "twofish.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPCryptoCFB
-
-+ (nullable NSData *)decryptData:(NSData *)encryptedData
- sessionKeyData:(NSData *)sessionKeyData // s2k produceSessionKeyWithPassphrase
- symmetricAlgorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm
- iv:(NSData *)ivData
- syncCFB:(BOOL)syncCFB
-{
- return [self manipulateData:encryptedData sessionKeyData:sessionKeyData symmetricAlgorithm:symmetricAlgorithm iv:ivData syncCFB:syncCFB decrypt:YES];
-}
-
-+ (nullable NSData *)encryptData:(NSData *)encryptedData
- sessionKeyData:(NSData *)sessionKeyData // s2k produceSessionKeyWithPassphrase
- symmetricAlgorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm
- iv:(NSData *)ivData
- syncCFB:(BOOL)syncCFB
-{
- return [self manipulateData:encryptedData sessionKeyData:sessionKeyData symmetricAlgorithm:symmetricAlgorithm iv:ivData syncCFB:syncCFB decrypt:NO];
-}
-
-#pragma mark - Private
-
-// key binary string representation of key to be used to decrypt the ciphertext.
-+ (nullable NSData *)manipulateData:(NSData *)encryptedData
- sessionKeyData:(NSData *)sessionKeyData // s2k produceSessionKeyWithPassphrase
- symmetricAlgorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm
- iv:(NSData *)ivData
- syncCFB:(BOOL)syncCFB // weird OpenPGP CFB
- decrypt:(BOOL)decrypt
-{
- NSAssert(sessionKeyData.length > 0, @"Missing session key");
- NSAssert(encryptedData.length > 0, @"Missing data");
- NSAssert(ivData.length > 0, @"Missing IV");
-
- if (ivData.length == 0 || sessionKeyData.length == 0 || encryptedData.length == 0) {
- return nil;
- }
-
- NSUInteger keySize = [PGPCryptoUtils keySizeOfSymmetricAlgorithm:symmetricAlgorithm];
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:symmetricAlgorithm];
- NSAssert(keySize <= 32, @"Invalid key size");
- NSAssert(sessionKeyData.length >= keySize, @"Invalid session key.");
-
- let ivDataBytes = (uint8_t *)[NSMutableData dataWithData:ivData].mutableBytes;
- let encryptedBytes = (const uint8_t *)encryptedData.bytes;
- var decryptedData = [NSMutableData dataWithLength:encryptedData.length];
- let outBuffer = (uint8_t *)decryptedData.mutableBytes;
- let outBufferLength = decryptedData.length;
-
- // decrypt with CFB
- switch (symmetricAlgorithm) {
- case PGPSymmetricAES128:
- case PGPSymmetricAES192:
- case PGPSymmetricAES256: {
- AES_KEY aes_key;
- AES_set_encrypt_key(sessionKeyData.bytes, MIN((int)keySize * 8, (int)sessionKeyData.length * 8), &aes_key);
-
- int blocksNum = 0;
- AES_cfb128_encrypt(encryptedBytes, outBuffer, outBufferLength, &aes_key, ivDataBytes, &blocksNum, decrypt ? AES_DECRYPT : AES_ENCRYPT);
-
- memset(&aes_key, 0, sizeof(AES_KEY));
- } break;
- case PGPSymmetricIDEA: {
- IDEA_KEY_SCHEDULE encrypt_key;
- idea_set_encrypt_key(sessionKeyData.bytes, &encrypt_key);
-
- IDEA_KEY_SCHEDULE decrypt_key;
- idea_set_decrypt_key(&encrypt_key, &decrypt_key);
-
- int num = 0;
- idea_cfb64_encrypt(encryptedBytes, outBuffer, outBufferLength, decrypt ? &decrypt_key : &encrypt_key, ivDataBytes, &num, decrypt ? CAST_DECRYPT : CAST_ENCRYPT);
-
- memset(&encrypt_key, 0, sizeof(IDEA_KEY_SCHEDULE));
- memset(&decrypt_key, 0, sizeof(IDEA_KEY_SCHEDULE));
- } break;
- case PGPSymmetricTripleDES: {
- DES_key_schedule *keys = calloc(3, sizeof(DES_key_schedule));
- pgp_defer {
- if (keys) {
- memset(keys, 0, 3 * sizeof(DES_key_schedule));
- free(keys);
- }
- };
-
- for (NSUInteger n = 0; n < 3; ++n) {
- DES_set_key((DES_cblock *)(void *)(sessionKeyData.bytes + n * 8), &keys[n]);
- }
-
- int blocksNum = 0;
- DES_ede3_cfb64_encrypt(encryptedBytes, outBuffer, outBufferLength, &keys[0], &keys[1], &keys[2], (DES_cblock *)(void *)ivDataBytes, &blocksNum, decrypt ? DES_DECRYPT : DES_ENCRYPT);
- } break;
- case PGPSymmetricCAST5: {
- // initialize
- CAST_KEY encrypt_key;
- CAST_set_key(&encrypt_key, MIN((int)keySize, (int)sessionKeyData.length), sessionKeyData.bytes);
-
- // CAST_ecb_encrypt(in, out, encrypt_key, CAST_ENCRYPT);
- int num = 0; // how much of the 64bit block we have used
- CAST_cfb64_encrypt(encryptedBytes, outBuffer, outBufferLength, &encrypt_key, ivDataBytes, &num, decrypt ? CAST_DECRYPT : CAST_ENCRYPT);
-
- memset(&encrypt_key, 0, sizeof(CAST_KEY));
- } break;
- case PGPSymmetricBlowfish: {
- BF_KEY encrypt_key;
- BF_set_key(&encrypt_key, MIN((int)keySize, (int)sessionKeyData.length), sessionKeyData.bytes);
-
- int num = 0; // how much of the 64bit block we have used
- BF_cfb64_encrypt(encryptedBytes, outBuffer, outBufferLength, &encrypt_key, ivDataBytes, &num, decrypt ? BF_DECRYPT : BF_ENCRYPT);
-
- memset(&encrypt_key, 0, sizeof(BF_KEY));
- } break;
- case PGPSymmetricTwofish256: {
- static dispatch_once_t twoFishInit;
- dispatch_once(&twoFishInit, ^{ Twofish_initialise(); });
-
- Twofish_key xkey;
- Twofish_prepare_key((uint8_t *)sessionKeyData.bytes, (int)sessionKeyData.length, &xkey);
-
- if (syncCFB) {
- // TODO: OpenPGP CFB Mode is different here
- } else {
- if (decrypt) {
- // decrypt
- NSMutableData *decryptedOutMutableData = encryptedData.mutableCopy;
- var ciphertextBlock = [NSData dataWithData:ivData];
- let plaintextBlock = [NSMutableData dataWithLength:blockSize];
- for (NSUInteger index = 0; index < encryptedData.length; index += blockSize) {
- Twofish_encrypt(&xkey, (uint8_t *)ciphertextBlock.bytes, plaintextBlock.mutableBytes);
- ciphertextBlock = [encryptedData subdataWithRange:(NSRange){index, MIN(blockSize, decryptedOutMutableData.length - index)}];
- [decryptedOutMutableData XORWithData:plaintextBlock index:index];
- }
- decryptedData = decryptedOutMutableData;
- } else {
- // encrypt
- NSMutableData *encryptedOutMutableData = encryptedData.mutableCopy; // input plaintext
- var plaintextBlock = [NSData dataWithData:ivData];
- let ciphertextBlock = [NSMutableData dataWithLength:blockSize];
- for (NSUInteger index = 0; index < encryptedData.length; index += blockSize) {
- Twofish_encrypt(&xkey, (uint8_t *)plaintextBlock.bytes, ciphertextBlock.mutableBytes);
- [encryptedOutMutableData XORWithData:ciphertextBlock index:index];
- plaintextBlock = [encryptedOutMutableData subdataWithRange:(NSRange){index, MIN(blockSize, encryptedOutMutableData.length - index)}]; // ciphertext.copy;
- }
- decryptedData = encryptedOutMutableData;
- }
- }
-
- memset(&xkey, 0, sizeof(Twofish_key));
- } break;
- case PGPSymmetricPlaintext:
- PGPLogWarning(@"Can't decrypt plaintext");
- decryptedData = [NSMutableData dataWithData:encryptedData];
- break;
- default:
- PGPLogWarning(@"Unsupported cipher.");
- return nil;
- }
-
- return decryptedData;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPFingerprint.m b/enzevalos_iphone/ObjectivePGP/PGPFingerprint.m
deleted file mode 100755
index d83cfdda3aa16ecb3959d494ec2aea60f86ae6c2..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPFingerprint.m
+++ /dev/null
@@ -1,57 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPFingerprint.h"
-#import "NSData+PGPUtils.h"
-#import "PGPFoundation.h"
-
-@implementation PGPFingerprint
-
-- (instancetype)initWithData:(NSData *)keyData {
- if (self = [self init]) {
- _keyData = keyData;
- _hashedData = [keyData pgp_SHA1];
- }
- return self;
-}
-
-- (NSString *)description {
- NSMutableString *sbuf = [NSMutableString stringWithCapacity:self.hashedData.length * 2];
- const unsigned char *buf = self.hashedData.bytes;
- for (NSUInteger i = 0; i < self.hashedData.length; ++i) {
- [sbuf appendFormat:@"%02X", (unsigned int)buf[i]];
- }
- return sbuf;
-}
-
-#pragma mark - isEqual
-
-- (NSUInteger)hashLength {
- return self.hashedData.length;
-}
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToFingerprintPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToFingerprintPacket:(PGPFingerprint *)packet {
- return PGPEqualObjects(self.hashedData,packet.hashedData) && PGPEqualObjects(self.keyData,packet.keyData);
-}
-
-- (NSUInteger)hash {
- NSUInteger result = 1;
- result = 31 * result + self.hashedData.hash;
- result = 31 * result + self.keyData.hash;
- return result;
-}
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/PGPFoundation.m b/enzevalos_iphone/ObjectivePGP/PGPFoundation.m
deleted file mode 100755
index b6bcad90ba568adbf11e75d9e5d60540ae2fae65..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPFoundation.m
+++ /dev/null
@@ -1,24 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPFoundation.h"
-#import "PGPMacros+Private.h"
-
-@implementation PGPFoundation
-
-@end
-
-OBJC_EXTERN inline id _pgp__cast(id obj, Class objClass) {
- NSCParameterAssert(objClass);
- return [obj isKindOfClass:objClass] ? obj : nil;
-}
-
-BOOL PGPEqualObjects(id _Nullable obj1, id _Nullable obj2) {
- return obj1 == obj2 || [obj1 isEqual:obj2];
-}
-
diff --git a/enzevalos_iphone/ObjectivePGP/PGPKey.m b/enzevalos_iphone/ObjectivePGP/PGPKey.m
deleted file mode 100755
index e26acb64e8da565258f5aa1d1d6f1efc5cacb25b..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPKey.m
+++ /dev/null
@@ -1,162 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPKey.h"
-#import "PGPKey+Private.h"
-#import "PGPPartialSubKey.h"
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-#import "PGPSecretKeyPacket.h"
-#import "PGPSecretKeyPacket+Private.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPSignatureSubpacket+Private.h"
-#import "PGPRSA.h"
-#import "PGPDSA.h"
-#import "NSMutableData+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPKey
-
-- (instancetype)initWithSecretKey:(nullable PGPPartialKey *)secretKey publicKey:(nullable PGPPartialKey *)publicKey {
- if ((self = [super init])) {
- _secretKey = [secretKey copy];
- _publicKey = [publicKey copy];
- }
- return self;
-}
-
-- (BOOL)isSecret {
- return self.secretKey != nil;
-}
-
-- (BOOL)isPublic {
- return self.publicKey != nil;
-}
-
-- (BOOL)isEncryptedWithPassword {
- return self.publicKey.isEncryptedWithPassword || self.secretKey.isEncryptedWithPassword;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@, publicKey: %@, secretKey: %@", super.description, self.publicKey.keyID, self.secretKey.keyID];
-}
-
-- (nullable NSDate *)expirationDate {
- return self.publicKey.expirationDate ?: self.secretKey.expirationDate;
-}
-
-- (PGPKeyID *)keyID {
- return self.publicKey.keyID ?: self.secretKey.keyID;
-}
-
-- (nullable PGPSecretKeyPacket *)signingSecretKey {
- if (!self.secretKey) {
- PGPLogDebug(@"Need secret key to sign");
- return nil;
- }
-
- // find secret key based on the public key signature (unless self signed secret key)
- let signingPacket = PGPCast(self.secretKey.signingKeyPacket, PGPSecretKeyPacket);
- if (!signingPacket) {
- PGPLogWarning(@"Need secret key to sign");
- }
-
- return signingPacket;
-}
-
-- (nullable PGPKey *)decryptedWithPassphrase:(NSString *)passphrase error:(NSError * __autoreleasing _Nullable *)error {
- let decryptedPartialKey = [self.secretKey decryptedWithPassphrase:passphrase error:error];
- if (decryptedPartialKey) {
- return [[PGPKey alloc] initWithSecretKey:decryptedPartialKey publicKey:self.publicKey];
- }
- return nil;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToKey:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToKey:(PGPKey *)other {
- return PGPEqualObjects(self.secretKey,other.secretKey) && PGPEqualObjects(self.publicKey,other.publicKey);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
-
- result = prime * result + self.secretKey.hash;
- result = prime * result + self.publicKey.hash;
-
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([[self.class allocWithZone:zone] initWithSecretKey:self.secretKey publicKey:self.publicKey], PGPKey);
- return duplicate;
-}
-
-#pragma mark - PGPExportable
-
-/// Export public and secret keys together.
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- let exportData = [NSMutableData data];
- if (self.publicKey) {
- [exportData pgp_appendData:[self export:PGPKeyTypePublic error:error]];
- }
-
- if (self.secretKey) {
- [exportData pgp_appendData:[self export:PGPKeyTypeSecret error:error]];
- }
-
- return exportData;
-}
-
-- (nullable NSData *)export:(PGPKeyType)keyType error:(NSError * __autoreleasing _Nullable *)error {
- switch (keyType) {
- case PGPKeyTypePublic: {
- if (!self.publicKey) {
- return nil;
- }
-
- return [self.publicKey export:error];
- }
- break;
- case PGPKeyTypeSecret: {
- if (!self.secretKey) {
- return nil;
- }
-
- return [self.secretKey export:error];
- }
- break;
- default: {
- PGPLogDebug(@"Can't export unknown key type: %@", self);
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{NSLocalizedDescriptionKey: @"Can't export unknown key type"}];
- }
- }
- break;
- }
-
- return nil;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPKeyGenerator.m b/enzevalos_iphone/ObjectivePGP/PGPKeyGenerator.m
deleted file mode 100755
index 13d06eb65d46b669470f68803c248929a6261a40..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPKeyGenerator.m
+++ /dev/null
@@ -1,361 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPKeyGenerator.h"
-#import "PGPTypes.h"
-#import "PGPPartialSubKey+Private.h"
-#import "PGPPartialKey+Private.h"
-#import "PGPPublicKeyPacket+Private.h"
-#import "PGPSecretKeyPacket+Private.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPPublicSubKeyPacket.h"
-#import "PGPSecretSubKeyPacket.h"
-#import "PGPSignatureSubpacketEmbeddedSignature.h"
-#import "PGPUser+Private.h"
-#import "PGPUserIDPacket.h"
-#import "PGPCryptoHash.h"
-#import "PGPCryptoUtils.h"
-#import "PGPFoundation.h"
-#import "PGPRSA.h"
-#import "PGPDSA.h"
-#import "PGPCryptoCFB.h"
-#import "PGPMacros+Private.h"
-#import "NSData+PGPUtils.h"
-#import "NSMutableData+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPKeyGenerator ()
-
-@end
-
-@implementation PGPKeyGenerator
-
-- (instancetype)init {
- if ((self = [super init])) {
- _keyAlgorithm = PGPPublicKeyAlgorithmRSA;
- _keyBitsLength = 3072;
- _createDate = NSDate.date;
- _version = 0x04;
- _cipherAlgorithm = PGPSymmetricAES256;
- _hashAlgorithm = PGPHashSHA256;
- }
- return self;
-}
-
-- (nullable PGPKeyMaterial *)fillMPIForPublic:(PGPPublicKeyPacket *)publicKeyPacket andSecret:(PGPSecretKeyPacket *)secretKeyPacket withKeyAlgorithm:(PGPPublicKeyAlgorithm)algorithm bits:(int)bits {
- PGPKeyMaterial *keyMaterial = nil;
-
- switch (algorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- keyMaterial = [PGPRSA generateNewKeyMPIArray:bits];
- publicKeyPacket.publicMPIs = @[keyMaterial.n, keyMaterial.e];
- secretKeyPacket.secretMPIs = @[keyMaterial.d, keyMaterial.p, keyMaterial.q, keyMaterial.u];
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- keyMaterial = [PGPDSA generateNewKeyMPIArray:bits];
- publicKeyPacket.publicMPIs = @[keyMaterial.p, keyMaterial.q, keyMaterial.g, keyMaterial.y];
- secretKeyPacket.secretMPIs = @[keyMaterial.x];
- } break;
- default:
- NSAssert(NO, @"Not supported");
- return nil;
- }
-
- secretKeyPacket.publicMPIs = publicKeyPacket.publicMPIs;
- return keyMaterial;
-}
-
-- (nullable PGPKey *)buildKeyWithPassphrase:(nullable NSString *)passphrase {
- // Public key
- let publicKeyPacket = [[PGPPublicKeyPacket alloc] init];
- publicKeyPacket.version = self.version;
- publicKeyPacket.publicKeyAlgorithm = self.keyAlgorithm;
- publicKeyPacket.createDate = self.createDate;
-
- // Secret Key
- let secretKeyPacket = [[PGPSecretKeyPacket alloc] init];
- secretKeyPacket.version = self.version;
- secretKeyPacket.publicKeyAlgorithm = publicKeyPacket.publicKeyAlgorithm;
- secretKeyPacket.symmetricAlgorithm = self.cipherAlgorithm;
- secretKeyPacket.createDate = publicKeyPacket.createDate;
-
- // Fill MPIs
- [self fillMPIForPublic:publicKeyPacket andSecret:secretKeyPacket withKeyAlgorithm:self.keyAlgorithm bits:self.keyBitsLength];
-
- // Encrypt with passphrase
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:secretKeyPacket.symmetricAlgorithm];
- if (!passphrase) {
- secretKeyPacket.s2kUsage = PGPS2KUsageNonEncrypted;
- secretKeyPacket.s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierSimple hashAlgorithm:self.hashAlgorithm];
- secretKeyPacket.ivData = [NSMutableData dataWithLength:blockSize];
- } else {
- secretKeyPacket.ivData = [PGPCryptoUtils randomData:blockSize];
- secretKeyPacket.s2kUsage = PGPS2KUsageEncryptedAndHashed;
-
- let s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierIteratedAndSalted hashAlgorithm:self.hashAlgorithm];
- secretKeyPacket.s2k = s2k;
-
- // build encryptedMPIPartData
- let plaintextMPIPartData = [NSMutableData data];
-
- for (PGPMPI *mpi in secretKeyPacket.secretMPIs) {
- [plaintextMPIPartData pgp_appendData:[mpi exportMPI]];
- }
-
- switch (secretKeyPacket.s2kUsage) {
- case PGPS2KUsageEncryptedAndHashed: {
- // a 20-octet SHA-1 hash of the plaintext of the algorithm-specific portion
- let hashData = plaintextMPIPartData.pgp_SHA1;
- [plaintextMPIPartData pgp_appendData:hashData];
- } break;
- case PGPS2KUsageEncrypted: {
- // a two-octet checksum of the plaintext of the algorithm-specific portion
- UInt16 checksum = CFSwapInt16HostToBig(plaintextMPIPartData.pgp_Checksum);
- [plaintextMPIPartData appendBytes:&checksum length:2];
- } break;
- default:
- break;
- }
-
- let sessionKeyData = [s2k produceSessionKeyWithPassphrase:PGPNN(passphrase) symmetricAlgorithm:self.cipherAlgorithm];
- if (sessionKeyData) {
- secretKeyPacket.encryptedMPIPartData = [PGPCryptoCFB encryptData:plaintextMPIPartData sessionKeyData:sessionKeyData symmetricAlgorithm:self.cipherAlgorithm iv:secretKeyPacket.ivData syncCFB:NO];
- }
- }
-
- // Create Key
- let partialPublicKey = [[PGPPartialKey alloc] initWithPackets:@[publicKeyPacket]];
- let partialSecretKey = [[PGPPartialKey alloc] initWithPackets:@[secretKeyPacket]];
- return [[PGPKey alloc] initWithSecretKey:partialSecretKey publicKey:partialPublicKey];
-}
-
-- (PGPKey *)addSubKeyTo:(PGPKey *)parentKey passphrase:(nullable NSString *)passphrase {
- let publicSubKeyPacket = [[PGPPublicSubKeyPacket alloc] init];
- publicSubKeyPacket.version = self.version;
- publicSubKeyPacket.publicKeyAlgorithm = self.keyAlgorithm;
- publicSubKeyPacket.createDate = self.createDate;
-
- // Secret Key
- let secretSubKeyPacket = [[PGPSecretSubKeyPacket alloc] init];
- secretSubKeyPacket.version = self.version;
- secretSubKeyPacket.publicKeyAlgorithm = publicSubKeyPacket.publicKeyAlgorithm;
- secretSubKeyPacket.symmetricAlgorithm = self.cipherAlgorithm;
- secretSubKeyPacket.createDate = publicSubKeyPacket.createDate;
-
- // Fill MPIs
- [self fillMPIForPublic:publicSubKeyPacket andSecret:secretSubKeyPacket withKeyAlgorithm:self.keyAlgorithm bits:self.keyBitsLength];
-
- // TODO: refactor duplicated code
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:secretSubKeyPacket.symmetricAlgorithm];
- if (!passphrase) {
- secretSubKeyPacket.s2kUsage = PGPS2KUsageNonEncrypted;
- secretSubKeyPacket.s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierSimple hashAlgorithm:self.hashAlgorithm];
- secretSubKeyPacket.ivData = [NSMutableData dataWithLength:blockSize];
- } else {
- secretSubKeyPacket.ivData = [PGPCryptoUtils randomData:blockSize];
- secretSubKeyPacket.s2kUsage = PGPS2KUsageEncryptedAndHashed;
-
- let s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierIteratedAndSalted hashAlgorithm:self.hashAlgorithm];
- secretSubKeyPacket.s2k = s2k;
-
- // build encryptedMPIPartData
- let plaintextMPIPartData = [NSMutableData data];
-
- for (PGPMPI *mpi in secretSubKeyPacket.secretMPIs) {
- [plaintextMPIPartData pgp_appendData:[mpi exportMPI]];
- }
-
- switch (secretSubKeyPacket.s2kUsage) {
- case PGPS2KUsageEncryptedAndHashed: {
- // a 20-octet SHA-1 hash of the plaintext of the algorithm-specific portion
- let hashData = plaintextMPIPartData.pgp_SHA1;
- [plaintextMPIPartData pgp_appendData:hashData];
- } break;
- case PGPS2KUsageEncrypted: {
- // a two-octet checksum of the plaintext of the algorithm-specific portion
- UInt16 checksum = CFSwapInt16HostToBig(plaintextMPIPartData.pgp_Checksum);
- [plaintextMPIPartData appendBytes:&checksum length:2];
- } break;
- default:
- break;
- }
-
- let sessionKeyData = [s2k produceSessionKeyWithPassphrase:PGPNN(passphrase) symmetricAlgorithm:self.cipherAlgorithm];
- if (sessionKeyData) {
- secretSubKeyPacket.encryptedMPIPartData = [PGPCryptoCFB encryptData:plaintextMPIPartData sessionKeyData:sessionKeyData symmetricAlgorithm:self.cipherAlgorithm iv:secretSubKeyPacket.ivData syncCFB:NO];
- }
- }
-
- // Create Key
- let publicSubKey = [[PGPPartialSubKey alloc] initWithPacket:publicSubKeyPacket];
- let secretSubKey = [[PGPPartialSubKey alloc] initWithPacket:secretSubKeyPacket];
-
- parentKey.publicKey.subKeys = [parentKey.publicKey.subKeys arrayByAddingObject:publicSubKey];
- parentKey.secretKey.subKeys = [parentKey.secretKey.subKeys arrayByAddingObject:secretSubKey];
-
- return [[PGPKey alloc] initWithSecretKey:secretSubKey publicKey:publicSubKey];
-}
-
-- (NSArray<PGPSignatureSubpacket *> *)signatureCommonHashedSubpackets {
- return @[
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeSignatureCreationTime andValue:self.createDate],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeKeyFlags andValue:@[@(PGPSignatureFlagAllowSignData), @(PGPSignatureFlagAllowCertifyOtherKeys)]],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypePreferredHashAlgorithm andValue:@[@(PGPHashSHA256), @(PGPHashSHA384), @(PGPHashSHA512)]],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypePreferredSymetricAlgorithm andValue:@[@(PGPSymmetricAES256), @(PGPSymmetricAES192), @(PGPSymmetricAES128), @(PGPSymmetricCAST5), @(PGPSymmetricTripleDES), @(PGPSymmetricIDEA)]],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypePreferredCompressionAlgorithm andValue:@[@(PGPCompressionBZIP2), @(PGPCompressionZLIB), @(PGPCompressionZIP)]],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeFeatures andValue:@[@(PGPFeatureModificationDetection)]],
- [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeKeyServerPreference andValue:@[@(PGPKeyServerPreferenceNoModify)]]
- ];
-}
-
-- (nullable PGPSignaturePacket *)buildPublicSignaturePacketFor:(PGPKey *)key {
- let publicKeyPacket = PGPCast(key.publicKey.primaryKeyPacket, PGPPublicKeyPacket);
-
- let publicKeySignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignaturePositiveCertificationUserIDandPublicKey hashAlgorithm:self.hashAlgorithm];
- publicKeySignaturePacket.version = publicKeyPacket.version;
- publicKeySignaturePacket.publicKeyAlgorithm = publicKeyPacket.publicKeyAlgorithm;
-
- let issuerKeyIDSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:publicKeyPacket.keyID];
-
- publicKeySignaturePacket.hashedSubpackets = [self.signatureCommonHashedSubpackets arrayByAddingObject:[[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypePrimaryUserID andValue:@(YES)]];
- publicKeySignaturePacket.unhashedSubpackets = @[issuerKeyIDSubpacket];
-
- // self sign the signature
- NSError *error;
- let userID = key.publicKey.users.firstObject.userID;
- if (![publicKeySignaturePacket signData:nil withKey:key subKey:nil passphrase:nil userID:userID error:&error]) {
- return nil;
- }
-
- return publicKeySignaturePacket;
-}
-
-- (nullable PGPSignaturePacket *)buildSecretSignaturePacketFor:(PGPKey *)key {
- let secretKeyPacket = PGPCast(key.secretKey.primaryKeyPacket, PGPSecretKeyPacket);
-
- let secretKeySignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignaturePositiveCertificationUserIDandPublicKey hashAlgorithm:self.hashAlgorithm];
- secretKeySignaturePacket.version = secretKeyPacket.version;
- secretKeySignaturePacket.publicKeyAlgorithm = secretKeyPacket.publicKeyAlgorithm;
-
- let issuerKeyIDSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:secretKeyPacket.keyID];
-
- secretKeySignaturePacket.hashedSubpackets = self.signatureCommonHashedSubpackets;
- secretKeySignaturePacket.unhashedSubpackets = @[issuerKeyIDSubpacket];
-
- // self sign the signature
- NSError *error;
- let userID = key.secretKey.users.firstObject.userID;
- if (![secretKeySignaturePacket signData:nil withKey:key subKey:nil passphrase:nil userID:userID error:&error]) {
- return nil;
- }
-
- return secretKeySignaturePacket;
-}
-
-
-- (nullable PGPSignaturePacket *)buildPublicSignaturePacketForSubKey:(PGPKey *)subKey parentKey:(PGPKey *)parentKey {
- NSError *error;
-
- let publicSubKeyPacket = PGPCast(subKey.publicKey.primaryKeyPacket, PGPPublicSubKeyPacket);
-
- let publicSubKeySignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignatureSubkeyBinding hashAlgorithm:self.hashAlgorithm];
- publicSubKeySignaturePacket.version = publicSubKeyPacket.version;
- publicSubKeySignaturePacket.publicKeyAlgorithm = publicSubKeyPacket.publicKeyAlgorithm;
-
- let creationTimeSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeSignatureCreationTime andValue:NSDate.date];
- let keyFlagsSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeKeyFlags andValue:@[@(PGPSignatureFlagAllowEncryptCommunications), @(PGPSignatureFlagAllowEncryptStorage)]];
- let issuerKeyIDSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:parentKey.signingSecretKey.keyID];
-
- // embeded signature
- let embeddedSignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignaturePrimaryKeyBinding hashAlgorithm:self.hashAlgorithm];
- embeddedSignaturePacket.version = 0x04;
- embeddedSignaturePacket.publicKeyAlgorithm = publicSubKeyPacket.publicKeyAlgorithm;
- [embeddedSignaturePacket signData:nil withKey:subKey subKey:nil passphrase:nil userID:nil error:&error];
- let subpacketEmbeddedSignature = [[PGPSignatureSubpacketEmbeddedSignature alloc] initWithSignature:embeddedSignaturePacket];
- let embeddedSignatureSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeEmbeddedSignature andValue:subpacketEmbeddedSignature];
-
- publicSubKeySignaturePacket.hashedSubpackets = @[creationTimeSubpacket, keyFlagsSubpacket, embeddedSignatureSubpacket];
- publicSubKeySignaturePacket.unhashedSubpackets = @[issuerKeyIDSubpacket];
-
- // self sign the signature
- let userID = parentKey.publicKey.users.firstObject.userID;
- if (![publicSubKeySignaturePacket signData:nil withKey:parentKey subKey:subKey passphrase:nil userID:userID error:&error]) {
- return nil;
- }
-
- return publicSubKeySignaturePacket;
-}
-
-- (nullable PGPSignaturePacket *)buildSecretSignaturePacketForSubKey:(PGPKey *)subKey parentKey:(PGPKey *)parentKey {
- NSError *error;
-
- let secretSubKeyPacket = PGPCast(subKey.secretKey.primaryKeyPacket, PGPSecretSubKeyPacket);
-
- let secretSubKeySignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignatureSubkeyBinding hashAlgorithm:self.hashAlgorithm];
- secretSubKeySignaturePacket.version = secretSubKeyPacket.version;
- secretSubKeySignaturePacket.publicKeyAlgorithm = secretSubKeyPacket.publicKeyAlgorithm;
-
- let creationTimeSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeSignatureCreationTime andValue:NSDate.date];
- let keyFlagsSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeKeyFlags andValue:@[@(PGPSignatureFlagAllowEncryptCommunications), @(PGPSignatureFlagAllowEncryptStorage)]];
- let issuerKeyIDSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:parentKey.signingSecretKey.keyID];
-
- // embeded signature
- let embeddedSignaturePacket = [PGPSignaturePacket signaturePacket:PGPSignaturePrimaryKeyBinding hashAlgorithm:self.hashAlgorithm];
- embeddedSignaturePacket.version = secretSubKeyPacket.version;
- embeddedSignaturePacket.publicKeyAlgorithm = secretSubKeyPacket.publicKeyAlgorithm;
- [embeddedSignaturePacket signData:nil withKey:subKey subKey:nil passphrase:nil userID:nil error:&error];
- let subpacketEmbeddedSignature = [[PGPSignatureSubpacketEmbeddedSignature alloc] initWithSignature:embeddedSignaturePacket];
- let embeddedSignatureSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeEmbeddedSignature andValue:subpacketEmbeddedSignature];
-
- secretSubKeySignaturePacket.hashedSubpackets = @[creationTimeSubpacket, keyFlagsSubpacket, embeddedSignatureSubpacket];
- secretSubKeySignaturePacket.unhashedSubpackets = @[issuerKeyIDSubpacket];
-
- // self sign the signature
- let userID = parentKey.secretKey.users.firstObject.userID;
- if (![secretSubKeySignaturePacket signData:nil withKey:parentKey subKey:subKey passphrase:nil userID:userID error:&error]) {
- return nil;
- }
-
- return secretSubKeySignaturePacket;
-}
-
-- (PGPKey *)generateFor:(NSString *)userID passphrase:(nullable NSString *)passphrase {
- let key = [self buildKeyWithPassphrase:passphrase];
- let subKey = [self addSubKeyTo:key passphrase:passphrase];
-
- let userPublic = [[PGPUser alloc] initWithUserIDPacket:[[PGPUserIDPacket alloc] initWithUserID:userID]];
- let userSecret = [[PGPUser alloc] initWithUserIDPacket:[[PGPUserIDPacket alloc] initWithUserID:userID]];
- key.publicKey.users = @[userPublic];
- key.secretKey.users = @[userSecret];
-
- // Public
-
- let publicKeySignaturePacket = [self buildPublicSignaturePacketFor:key];
- userPublic.selfCertifications = [userPublic.selfCertifications arrayByAddingObject:publicKeySignaturePacket];
-
- let publicSubKeySignaturePacket = [self buildPublicSignaturePacketForSubKey:subKey parentKey:key];
- key.publicKey.subKeys.firstObject.bindingSignature = publicSubKeySignaturePacket;
-
- // Secret
-
- let secretKeySignaturePacket = [self buildSecretSignaturePacketFor:key];
- userSecret.selfCertifications = [userSecret.selfCertifications arrayByAddingObject:secretKeySignaturePacket];
-
- let secretSubKeySignaturePacket = [self buildSecretSignaturePacketForSubKey:subKey parentKey:key];
- key.secretKey.subKeys.firstObject.bindingSignature = secretSubKeySignaturePacket;
-
- return key;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPKeyID.m b/enzevalos_iphone/ObjectivePGP/PGPKeyID.m
deleted file mode 100755
index f6655ca70d78eac25a53dd6bd984504c9c80bd6a..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPKeyID.m
+++ /dev/null
@@ -1,107 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// Fingerprint: 4772 3A3C EE12 760F 7DC8 4AE0 1B63 BCB7 E810 38C6
-// Long Key ID: 1B63 BCB7 E810 38C6 <- this
-// Short Key ID: E810 38C6
-
-#import "PGPKeyID.h"
-#import "PGPMacros.h"
-#import "PGPFingerprint.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPKeyID ()
-
-@property (copy, nonatomic) NSData *longKey;
-
-@end
-
-@implementation PGPKeyID
-
-- (nullable instancetype)initWithLongKey:(NSData *)longKeyData {
- if (longKeyData.length != 8) {
- return nil;
- }
-
- if (self = [super init]) {
- _longKey = [longKeyData copy];
- }
- return self;
-}
-
-- (instancetype)initWithFingerprint:(PGPFingerprint *)fingerprint {
- PGPAssertClass(fingerprint, PGPFingerprint);
- PGPAssertClass(fingerprint.hashedData, NSData);
- return ((self = [self initWithLongKey:[fingerprint.hashedData subdataWithRange:(NSRange){fingerprint.hashLength - 8, 8}]]));
-}
-
-- (NSString *)description {
- return [self longIdentifier];
-}
-
-- (NSData *)shortKey {
- return [self.longKey subdataWithRange:(NSRange){4, 4}];
-}
-
-- (NSString *)shortIdentifier {
- NSData *sKey = self.shortKey;
- NSMutableString *sbuf = [NSMutableString stringWithCapacity:sKey.length * 2];
- const unsigned char *buf = sKey.bytes;
- for (NSUInteger i = 0; i < sKey.length; ++i) {
- [sbuf appendFormat:@"%02X", (unsigned int)buf[i]];
- }
- return sbuf;
-}
-
-- (NSString *)longIdentifier {
- NSData *lKey = self.longKey;
- NSMutableString *sbuf = [NSMutableString stringWithCapacity:lKey.length * 2];
- const unsigned char *buf = lKey.bytes;
- for (NSUInteger i = 0; i < lKey.length; ++i) {
- [sbuf appendFormat:@"%02X", (unsigned int)buf[i]];
- }
- return sbuf;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToKeyID:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToKeyID:(PGPKeyID *)packet {
- return PGPEqualObjects(self.longKey, packet.longKey);
-}
-
-- (NSUInteger)hash {
- NSUInteger result = 1;
- result = 31 * result + self.longKey.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- return PGPCast([[self.class allocWithZone:zone] initWithLongKey:self.longKey], PGPKeyID);
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [self.longKey copy];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPKeyring.m b/enzevalos_iphone/ObjectivePGP/PGPKeyring.m
deleted file mode 100755
index d6f2c8e2f611f17ecf68ef9b1decee02e3a12c8f..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPKeyring.m
+++ /dev/null
@@ -1,289 +0,0 @@
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPKeyring.h"
-
-#import "PGPUser.h"
-#import "PGPKey.h"
-#import "PGPKey+Private.h"
-#import "PGPPartialKey.h"
-#import "PGPPartialSubKey.h"
-#import "PGPArmor.h"
-
-#import "PGPFoundation.h"
-#import "PGPLogging.h"
-#import "NSMutableData+PGPUtils.h"
-#import "NSArray+PGPUtils.h"
-#import "PGPMacros+Private.h"
-
-#import "ObjectivePGPObject.h"
-
-@interface PGPKeyring ()
-
-@property (strong, nonatomic, readwrite) NSArray<PGPKey *> *keys;
-
-@end
-
-@implementation PGPKeyring
-
-- (instancetype)init {
- if ((self = [super init])) {
- _keys = [NSMutableArray<PGPKey *> array];
- }
- return self;
-}
-
-- (void)importKeys:(NSArray<PGPKey *> *)keys {
- PGPAssertClass(keys, NSArray);
-
- for (PGPKey *key in keys) {
- self.keys = [self.class addOrUpdatePartialKey:key.secretKey inContainer:self.keys];
- self.keys = [self.class addOrUpdatePartialKey:key.publicKey inContainer:self.keys];
- }
-}
-
-- (BOOL)importKey:(NSString *)keyIdentifier fromPath:(NSString *)path error:(NSError * __autoreleasing _Nullable *)error {
- let fullPath = [path stringByExpandingTildeInPath];
-
- let loadedKeys = [self.class readKeysFromPath:fullPath error:error];
- if (loadedKeys.count == 0 || (error && *error)) {
- return NO;
- }
-
- let foundKey = [[loadedKeys pgp_objectsPassingTest:^BOOL(PGPKey *key, BOOL *stop) {
- *stop = PGPEqualObjects(key.publicKey.keyID.shortIdentifier.uppercaseString, keyIdentifier.uppercaseString) || PGPEqualObjects(key.secretKey.keyID.shortIdentifier.uppercaseString, keyIdentifier.uppercaseString) ||
- PGPEqualObjects(key.publicKey.keyID.longIdentifier.uppercaseString, keyIdentifier.uppercaseString) || PGPEqualObjects(key.secretKey.keyID.longIdentifier.uppercaseString, keyIdentifier.uppercaseString);
- return *stop;
- }] firstObject];
-
- if (!foundKey) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorNotFound userInfo:@{NSLocalizedDescriptionKey: @"Key not found."}];
- }
- return NO;
- }
-
- self.keys = [self.keys arrayByAddingObject:foundKey];
-
- return YES;
-}
-
-- (void)deleteKeys:(NSArray<PGPKey *> *)keys {
- PGPAssertClass(keys, NSArray);
-
- let allKeys = [NSMutableArray<PGPKey *> arrayWithArray:self.keys];
- for (PGPKey *key in keys) {
- [allKeys removeObject:key];
- }
- self.keys = allKeys;
-}
-
-- (void)deleteAll {
- [self deleteKeys:self.keys];
-}
-
-- (NSArray<PGPKey *> *)findKeysForUserID:(nonnull NSString *)userID {
- return [self.keys pgp_objectsPassingTest:^BOOL(PGPKey *key, __unused BOOL *stop1) {
- let a = key.publicKey ? [key.publicKey.users indexOfObjectPassingTest:^BOOL(PGPUser *user, __unused NSUInteger idx, __unused BOOL *stop2) {
- return [userID isEqual:user.userID];
- }] : NSNotFound;
-
- let b = key.secretKey ? [key.secretKey.users indexOfObjectPassingTest:^BOOL(PGPUser *user, __unused NSUInteger idx, __unused BOOL *stop2) {
- return [userID isEqual:user.userID];
- }] : NSNotFound;
-
- return (a != NSNotFound) || (b != NSNotFound);
- }];
-}
-
-- (nullable PGPKey *)findKeyWithKeyID:(PGPKeyID *)searchKeyID {
- return [self.class findKeyWithKeyID:searchKeyID in:self.keys];
-}
-
-- (nullable PGPKey *)findKeyWithIdentifier:(NSString *)keyIdentifier {
- PGPAssertClass(keyIdentifier, NSString);
-
- if (keyIdentifier.length != 8 && keyIdentifier.length != 16) {
- PGPLogDebug(@"Invalid key identifier: %@", keyIdentifier);
- return nil;
- }
-
- BOOL useShortIdentifier = keyIdentifier.length == 8;
-
- // public
- for (PGPKey *key in self.keys) {
- if (key.publicKey) {
- let identifier = useShortIdentifier ? key.publicKey.keyID.shortIdentifier : key.publicKey.keyID.longIdentifier;
- if ([identifier.uppercaseString isEqual:keyIdentifier.uppercaseString]) {
- return key;
- }
-
- for (PGPPartialSubKey *subkey in key.publicKey.subKeys) {
- let subIdentifier = useShortIdentifier ? subkey.keyID.shortIdentifier : subkey.keyID.longIdentifier;
- if ([subIdentifier.uppercaseString isEqual:keyIdentifier.uppercaseString]) {
- return key;
- }
- }
- }
-
- if (key.secretKey) {
- let identifier = useShortIdentifier ? key.secretKey.keyID.shortIdentifier : key.secretKey.keyID.longIdentifier;
- if ([identifier.uppercaseString isEqual:keyIdentifier.uppercaseString]) {
- return key;
- }
-
- for (PGPPartialSubKey *subkey in key.secretKey.subKeys) {
- let subIdentifier = useShortIdentifier ? subkey.keyID.shortIdentifier : subkey.keyID.longIdentifier;
- if ([subIdentifier.uppercaseString isEqual:keyIdentifier.uppercaseString]) {
- return key;
- }
- }
- }
- }
-
- return nil;
-}
-
-- (nullable NSData *)exportKeysOfType:(PGPKeyType)type error:(NSError * __autoreleasing _Nullable *)error {
- let output = [NSMutableData data];
- for (PGPKey *key in self.keys) {
- if (type == PGPKeyTypePublic && key.publicKey) {
- [output pgp_appendData:[key.publicKey export:error]];
- }
- if (type == PGPKeyTypeSecret && key.secretKey) {
- [output pgp_appendData:[key.secretKey export:error]];
- }
- }
- return output.length > 0 ? output : nil;
-}
-
-- (nullable NSData *)exportKey:(PGPKey *)key armored:(BOOL)armored {
- PGPAssertClass(key, PGPKey);
-
- NSError *exportError = nil;
- NSData *keyData = [key export:&exportError];
- if (!keyData || exportError) {
- PGPLogDebug(@"%@", exportError);
- return nil;
- }
-
- if (armored) {
- return [[PGPArmor armored:keyData as:PGPArmorPublicKey] dataUsingEncoding:NSUTF8StringEncoding];
- } else {
- return keyData;
- }
- return nil;
-}
-
-+ (BOOL)appendKey:(PGPPartialKey *)key toKeyring:(NSString *)path error:(NSError * __autoreleasing *)error {
- NSFileManager *fm = [NSFileManager defaultManager];
-
- if (!path) {
- return NO;
- }
-
- let keyData = [key export:error];
- if (!keyData) {
- return NO;
- }
-
- BOOL result = NO;
- if (![fm fileExistsAtPath:path]) {
- NSDictionary *attributes = nil;
-#ifdef __IPHONE_OS_VERSION_MAX_ALLOWED
- attributes = @{ NSFileProtectionKey: NSFileProtectionComplete, NSFilePosixPermissions: @(0600) };
-#else
- attributes = @{ NSFilePosixPermissions: @(0600) };
-#endif
- result = [fm createFileAtPath:path contents:keyData attributes:attributes];
- } else {
- @try {
- NSFileHandle *fileHandle = [NSFileHandle fileHandleForUpdatingAtPath:path];
- [fileHandle seekToEndOfFile];
- [fileHandle writeData:keyData];
- [fileHandle closeFile];
- result = YES;
- } @catch (NSException *exception) {
- result = NO;
- }
- }
- return result;
-}
-
-+ (nullable PGPKey *)findKeyWithKeyID:(PGPKeyID *)searchKeyID in:(NSArray<PGPKey *> *)keys {
- PGPAssertClass(searchKeyID, PGPKeyID);
-
- return [[keys pgp_objectsPassingTest:^BOOL(PGPKey *key, BOOL *stop) {
- // top-level keys
- __block BOOL found = (key.publicKey && PGPEqualObjects(key.publicKey.keyID, searchKeyID));
- if (!found) {
- found = (key.secretKey && PGPEqualObjects(key.secretKey.keyID,searchKeyID));
- }
-
- // subkeys
- if (!found && key.publicKey.subKeys.count > 0) {
- found = [key.publicKey.subKeys indexOfObjectPassingTest:^BOOL(PGPPartialSubKey *subkey, __unused NSUInteger idx, BOOL *stop2) {
- *stop2 = PGPEqualObjects(subkey.keyID,searchKeyID);
- return *stop2;
- }] != NSNotFound;
- }
-
- if (!found && key.secretKey.subKeys.count > 0) {
- found = [key.secretKey.subKeys indexOfObjectPassingTest:^BOOL(PGPPartialSubKey *subkey, __unused NSUInteger idx, BOOL *stop2) {
- *stop2 = PGPEqualObjects(subkey.keyID,searchKeyID);
- return *stop2;
- }] != NSNotFound;
- }
-
- *stop = found;
- return found;
- }] firstObject];
-}
-
-// Add or update compound key. Returns updated set.
-+ (NSArray<PGPKey *> *)addOrUpdatePartialKey:(nullable PGPPartialKey *)key inContainer:(NSArray<PGPKey *> *)keys {
- if (!key) {
- return keys;
- }
-
- NSMutableArray *updatedContainer = [NSMutableArray<PGPKey *> arrayWithArray:keys];
-
- PGPKey *foundCompoundKey = nil;
- for (PGPKey *searchKey in keys) {
- if (PGPEqualObjects(searchKey.publicKey.keyID,key.keyID) || PGPEqualObjects(searchKey.secretKey.keyID,key.keyID)) {
- foundCompoundKey = searchKey;
- break;
- }
- }
-
- if (!foundCompoundKey) {
- let compoundKey = [[PGPKey alloc] initWithSecretKey:(key.type == PGPKeyTypeSecret ? key : nil) publicKey:(key.type == PGPKeyTypePublic ? key : nil)];
- [updatedContainer addObject:compoundKey];
- } else {
- if (key.type == PGPKeyTypePublic) {
- foundCompoundKey.publicKey = key;
- }
- if (key.type == PGPKeyTypeSecret) {
- foundCompoundKey.secretKey = key;
- }
- }
-
- return updatedContainer;
-}
-
-#pragma mark - PGPExportable
-
-- (NSData *)export:(NSError * _Nullable __autoreleasing *)error {
- let output = [NSMutableData data];
- for (PGPKey *key in self.keys) {
- let keyData = [key export:error];
- [output pgp_appendData:keyData];
- }
- return output;
-}
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/PGPMPI.m b/enzevalos_iphone/ObjectivePGP/PGPMPI.m
deleted file mode 100755
index 508a47faf2cb3c45f1f822f84dd58a81672e14ad..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPMPI.m
+++ /dev/null
@@ -1,142 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// Multiprecision integers (also called MPIArray) are unsigned integers used
-// to hold large integers such as the ones used in cryptographic
-// calculations.
-
-#import "PGPMPI.h"
-#import "PGPBigNum+Private.h"
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import <openssl/bn.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-NSString * const PGPMPI_N = @"N";
-NSString * const PGPMPI_E = @"E";
-NSString * const PGPMPI_P = @"P";
-NSString * const PGPMPI_G = @"G";
-NSString * const PGPMPI_Q = @"Q";
-NSString * const PGPMPI_D = @"D";
-NSString * const PGPMPI_U = @"U";
-NSString * const PGPMPI_X = @"X";
-NSString * const PGPMPI_R = @"R";
-NSString * const PGPMPI_S = @"S";
-NSString * const PGPMPI_Y = @"Y";
-NSString * const PGPMPI_M = @"M";
-
-@interface PGPMPI ()
-
-@property (nonatomic, readwrite) PGPBigNum *bigNum;
-@property (nonatomic, readwrite) NSUInteger packetLength;
-
-@end
-
-@implementation PGPMPI
-
-- (instancetype)initWithData:(NSData *)dataToMPI identifier:(NSString *)identifier {
- if ((self = [super init])) {
- _bigNum = [[PGPBigNum alloc] initWithBIGNUM:BN_bin2bn(dataToMPI.bytes, dataToMPI.length & INT_MAX, NULL)];
- _packetLength = dataToMPI.length + 2;
- _identifier = [identifier copy];
- }
- return self;
-}
-
-- (instancetype)initWithBigNum:(PGPBigNum *)bigNum identifier:(NSString *)identifier {
- return (self = [self initWithData:bigNum.data identifier:identifier]);
-}
-
-// parse mpi "packet"
-- (instancetype)initWithMPIData:(NSData *)mpiData identifier:(NSString *)identifier atPosition:(NSUInteger)position {
- UInt16 bitsBE = 0;
- [mpiData getBytes:&bitsBE range:(NSRange){position, 2}];
- UInt16 bits = CFSwapInt16BigToHost(bitsBE);
- NSUInteger mpiBytesLength = (bits + 7) / 8;
-
- let intData = [mpiData subdataWithRange:(NSRange){position + 2, mpiBytesLength}];
- return (self = [self initWithData:intData identifier:identifier]);
-}
-
-- (nullable NSData *)bodyData {
- if (!self.bigNum) {
- PGPLogDebug(@"Missing bignum");
- return nil;
- }
-
- let mpi_BN = BN_dup(self.bigNum.bignumRef);
- let mpi_BN_length = (BN_num_bits(mpi_BN) + 7) / 8;
- UInt8 *bn_bin = calloc((size_t)mpi_BN_length, sizeof(UInt8));
- let len = (NSUInteger)BN_bn2bin(mpi_BN, bn_bin);
- BN_clear_free(mpi_BN);
-
- let data = [NSData dataWithBytes:bn_bin length:len];
- free(bn_bin);
- return data;
-}
-
-- (nullable NSData *)exportMPI {
- if (!self.bigNum) {
- return nil;
- }
-
- let outData = [NSMutableData data];
-
- // length
- UInt16 bits = (UInt16)BN_num_bits(self.bigNum.bignumRef);
- UInt16 bitsBE = CFSwapInt16HostToBig(bits);
- [outData appendBytes:&bitsBE length:2];
-
- // mpi
- UInt8 *buf = calloc((size_t)BN_num_bytes(self.bigNum.bignumRef), sizeof(UInt8));
- pgp_defer { free(buf); };
- UInt16 bytes = (bits + 7) / 8;
- BN_bn2bin(self.bigNum.bignumRef, buf);
- [outData appendBytes:buf length:bytes];
-
- return outData;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@, \"%@\", %@ bytes, total: %@ bytes", [super description], self.identifier, @(self.bigNum.bytesCount), @(self.packetLength)];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToMPI:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToMPI:(PGPMPI *)other {
- return PGPEqualObjects(self.identifier, other.identifier) && PGPEqualObjects(self.bigNum, other.bigNum);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
- result = prime * result + self.identifier.hash;
- result = prime * result + self.bigNum.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([[self.class allocWithZone:zone] initWithBigNum:self.bigNum identifier:self.identifier], PGPMPI);
- duplicate.packetLength = self.packetLength;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPPKCSEme.m b/enzevalos_iphone/ObjectivePGP/PGPPKCSEme.m
deleted file mode 100755
index 8b4b7bf6d483479f5a3162308d71d8f6758efc82..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPPKCSEme.m
+++ /dev/null
@@ -1,65 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPKCSEme.h"
-#import "NSData+PGPUtils.h"
-#import "PGPCryptoUtils.h"
-#import "PGPTypes.h"
-#import "PGPMacros+Private.h"
-
-@implementation PGPPKCSEme
-
-+ (NSData *)encodeMessage:(NSData *)m keyModulusLength:(NSUInteger)k error:(NSError * __autoreleasing *)error {
- if (m.length > k - 11) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Message to long" }];
- }
- return nil;
- }
-
- // Generate an octet string PS of length k - mLen - 3 consisting of
- // pseudo-randomly generated nonzero octets. The length of PS will
- // be at least eight octets.
- let psLen = MAX((k - m.length) - 3, (NSUInteger)8);
- NSMutableData *psData = [NSMutableData data];
- for (NSUInteger i = 0; i < psLen; i++) {
- UInt8 b = (UInt8)arc4random_uniform(254) + 1;
- [psData appendBytes:&b length:1];
- }
-
- NSMutableData *emData = [NSMutableData data];
- UInt8 emPrefix[] = {0x00, 0x02};
- UInt8 emSuffix[] = {0x00};
- [emData appendBytes:emPrefix length:sizeof(emPrefix)];
- [emData appendData:psData];
- [emData appendBytes:emSuffix length:sizeof(emSuffix)];
- [emData appendData:m];
- return emData;
-}
-
-+ (NSData *)decodeMessage:(NSData *)m error:(NSError * __autoreleasing *)error {
- NSUInteger position = 0;
- UInt8 emPrefix[2];
- [m getBytes:&emPrefix range:(NSRange){position, sizeof(emPrefix)}];
- position = position + sizeof(emPrefix);
-
- // read until 0x00
- NSUInteger *psLength = 0;
- Byte b = 0;
- do {
- [m getBytes:&b range:(NSRange){position, 1}];
- position = position + 1;
- psLength = psLength + 1;
- } while (b != 0x00 && position < (m.length - 1));
-
- // last read is separator 0x00, so current position at start of M
- let emData = [m subdataWithRange:(NSRange){position, m.length - position}];
- return emData;
-}
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/PGPPKCSEmsa.m b/enzevalos_iphone/ObjectivePGP/PGPPKCSEmsa.m
deleted file mode 100755
index 30afd78f5d90f8ddfb51d31ac86b51a7af0d71c7..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPPKCSEmsa.m
+++ /dev/null
@@ -1,110 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPKCSEmsa.h"
-#import "NSData+PGPUtils.h"
-#import "PGPMacros+Private.h"
-#import "PGPCryptoUtils.h"
-#import "PGPTypes.h"
-
-static UInt8 prefix_md5[] = {0x30, 0x20, 0x30, 0x0C, 0x06, 0x08, 0x2A, 0x86, 0x48, 0x86, 0xF7, 0x0D, 0x02, 0x05, 0x05, 0x00, 0x04, 0x10};
-
-static UInt8 prefix_sha1[] = {0x30, 0x21, 0x30, 0x09, 0x06, 0x05, 0x2b, 0x0E, 0x03, 0x02, 0x1A, 0x05, 0x00, 0x04, 0x14};
-
-static UInt8 prefix_sha224[] = {0x30, 0x2d, 0x30, 0x0d, 0x06, 0x09, 0x60, 0x86, 0x48, 0x01, 0x65, 0x03, 0x04, 0x02, 0x04, 0x05, 0x00, 0x04, 0x1C};
-
-static UInt8 prefix_sha256[] = {0x30, 0x31, 0x30, 0x0d, 0x06, 0x09, 0x60, 0x86, 0x48, 0x01, 0x65, 0x03, 0x04, 0x02, 0x01, 0x05, 0x00, 0x04, 0x20};
-
-static UInt8 prefix_sha384[] = {0x30, 0x41, 0x30, 0x0d, 0x06, 0x09, 0x60, 0x86, 0x48, 0x01, 0x65, 0x03, 0x04, 0x02, 0x02, 0x05, 0x00, 0x04, 0x30};
-
-static UInt8 prefix_sha512[] = {0x30, 0x51, 0x30, 0x0d, 0x06, 0x09, 0x60, 0x86, 0x48, 0x01, 0x65, 0x03, 0x04, 0x02, 0x03, 0x05, 0x00, 0x04, 0x40};
-
-static UInt8 prefix_ripemd160[] = {0x30, 0x21, 0x30, 0x09, 0x06, 0x05, 0x2B, 0x24, 0x03, 0x02, 0x01, 0x05, 0x00, 0x04, 0x14};
-
-@implementation PGPPKCSEmsa
-
-/**
- * create a EMSA-PKCS1-v1_5 padding (See {@link http://tools.ietf.org/html/rfc4880#section-13.1.3|RFC 4880 13.1.3})
- *
- * @param hashAlgorithm Hash algoritm
- * @param m message to be encoded
- * @param emLen intended length in octets of the encoded message
- *
- * @return encoded message
- */
-+ (NSData *)encode:(PGPHashAlgorithm)hashAlgorithm message:(NSData *)m encodedMessageLength:(NSUInteger)emLength error:(NSError * __autoreleasing *)error {
- let tData = [NSMutableData data]; // prefix + hash
- switch (hashAlgorithm) {
- case PGPHashMD5: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_md5 length:sizeof(prefix_md5)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_MD5];
- } break;
- case PGPHashSHA1: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_sha1 length:sizeof(prefix_sha1)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_SHA1];
- } break;
- case PGPHashSHA224: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_sha224 length:sizeof(prefix_sha224)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_SHA224];
- } break;
- case PGPHashSHA256: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_sha256 length:sizeof(prefix_sha256)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_SHA256];
- } break;
- case PGPHashSHA384: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_sha384 length:sizeof(prefix_sha384)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_SHA384];
- } break;
- case PGPHashSHA512: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_sha512 length:sizeof(prefix_sha512)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_SHA512];
- } break;
- case PGPHashRIPEMD160: {
- NSData *hashPrefixData = [NSData dataWithBytes:prefix_ripemd160 length:sizeof(prefix_ripemd160)];
- [tData appendData:hashPrefixData];
- [tData appendData:m.pgp_RIPEMD160];
- } break;
- default:
- NSAssert(false, @"Missing implementation");
- break;
- }
-
- if (emLength < tData.length + 11) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"intended encoded message length too short" }];
- }
- return nil;
- }
-
- // Generate an octet string PS consisting of emLen - tLen - 3
- // octets with hexadecimal value 0xFF. The length of PS will be at
- // least 8 octets.
- NSMutableData *psData = [NSMutableData data];
- UInt8 ff = 0xff;
- for (NSUInteger i = 0; i < emLength - tData.length - 3; i++) {
- [psData appendBytes:&ff length:1];
- }
-
- NSMutableData *emData = [NSMutableData data];
- UInt8 emPrefix[] = {0x00, 0x01};
- UInt8 emSuffix[] = {0x00};
- [emData appendBytes:emPrefix length:sizeof(emPrefix)];
- [emData appendData:psData];
- [emData appendBytes:emSuffix length:sizeof(emSuffix)];
- [emData appendData:tData];
-
- return emData;
-}
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/PGPPacketFactory.m b/enzevalos_iphone/ObjectivePGP/PGPPacketFactory.m
deleted file mode 100755
index f31b564d92db3bc1aa03864a7861f44816120a1c..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPPacketFactory.m
+++ /dev/null
@@ -1,122 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPacketFactory.h"
-#import "PGPPacket+Private.h"
-#import "PGPCompressedPacket.h"
-#import "PGPLiteralPacket.h"
-#import "PGPModificationDetectionCodePacket.h"
-#import "PGPOnePassSignaturePacket.h"
-#import "PGPPublicKeyEncryptedSessionKeyPacket.h"
-#import "PGPSymetricKeyEncryptedSessionKeyPacket.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPPublicSubKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPSecretSubKeyPacket.h"
-#import "PGPSignaturePacket.h"
-#import "PGPSymmetricallyEncryptedDataPacket.h"
-#import "PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h"
-#import "PGPTrustPacket.h"
-#import "PGPUserAttributePacket.h"
-#import "PGPUserIDPacket.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPacketFactory
-
-/**
- * Parse packet data and return packet object instance
- *cc
- * @param packetData Data with all the packets. Packet sequence data. Keyring.
- * @param offset offset of current packet
- *
- * @return Packet instance object
- */
-+ (nullable PGPPacket *)packetWithData:(NSData *)packetData offset:(NSUInteger)offset consumedBytes:(nullable NSUInteger *)consumedBytes {
- // parse header and get actual header data
- PGPPacketTag packetTag = 0;
- UInt32 headerLength = 0;
- BOOL indeterminateLength = NO;
- let data = [packetData subdataWithRange:(NSRange){offset, packetData.length - offset}];
- let packetBodyData = [PGPPacket readPacketBody:data headerLength:&headerLength consumedBytes:consumedBytes packetTag:&packetTag indeterminateLength:&indeterminateLength];
- let packetHeaderData = [packetData subdataWithRange:(NSRange){offset, headerLength}];
-
- if (packetHeaderData.length > 0) {
- // Analyze body0
- PGPPacket *packet = nil;
- switch (packetTag) {
- case PGPPublicKeyPacketTag:
- packet = [PGPPublicKeyPacket packetWithBody:packetBodyData];
- break;
- case PGPPublicSubkeyPacketTag:
- packet = [PGPPublicSubKeyPacket packetWithBody:packetBodyData];
- break;
- case PGPSignaturePacketTag:
- packet = [PGPSignaturePacket packetWithBody:packetBodyData];
- break;
- case PGPUserAttributePacketTag:
- packet = [PGPUserAttributePacket packetWithBody:packetBodyData];
- break;
- case PGPUserIDPacketTag:
- packet = [PGPUserIDPacket packetWithBody:packetBodyData];
- break;
- case PGPTrustPacketTag:
- packet = [PGPTrustPacket packetWithBody:packetBodyData];
- break;
- case PGPLiteralDataPacketTag:
- packet = [PGPLiteralPacket packetWithBody:packetBodyData];
- break;
- case PGPSecretKeyPacketTag:
- packet = [PGPSecretKeyPacket packetWithBody:packetBodyData];
- break;
- case PGPSecretSubkeyPacketTag:
- packet = [PGPSecretSubKeyPacket packetWithBody:packetBodyData];
- break;
- case PGPModificationDetectionCodePacketTag:
- packet = [PGPModificationDetectionCodePacket packetWithBody:packetBodyData];
- break;
- case PGPOnePassSignaturePacketTag:
- packet = [PGPOnePassSignaturePacket packetWithBody:packetBodyData];
- break;
- case PGPCompressedDataPacketTag:
- packet = [PGPCompressedPacket packetWithBody:packetBodyData];
- break;
- case PGPSymmetricallyEncryptedDataPacketTag:
- packet = [PGPSymmetricallyEncryptedDataPacket packetWithBody:packetBodyData];
- break;
- case PGPSymmetricallyEncryptedIntegrityProtectedDataPacketTag:
- packet = [PGPSymmetricallyEncryptedIntegrityProtectedDataPacket packetWithBody:packetBodyData];
- break;
- case PGPPublicKeyEncryptedSessionKeyPacketTag:
- packet = [PGPPublicKeyEncryptedSessionKeyPacket packetWithBody:packetBodyData];
- break;
- case PGPSymetricKeyEncryptedSessionKeyPacketTag:
- packet = [PGPSymetricKeyEncryptedSessionKeyPacket packetWithBody:packetBodyData];
- break;
- default:
- PGPLogWarning(@"Packet tag %@ is not supported", @(packetTag));
- packet = [PGPPacket packetWithBody:packetBodyData];
- break;
- }
-
- PGPAssertClass(packet, PGPPacket);
-
- if (indeterminateLength) {
- packet.indeterminateLength = YES;
- }
- return packet;
- }
- return nil;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPPartialKey.m b/enzevalos_iphone/ObjectivePGP/PGPPartialKey.m
deleted file mode 100755
index 7afe20df2782a97ef5d6833ba9075d1d5d9b07ac..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPPartialKey.m
+++ /dev/null
@@ -1,530 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPartialKey.h"
-#import "PGPPartialKey+Private.h"
-#import "PGPLogging.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPPublicSubKeyPacket.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPSecretSubKeyPacket.h"
-#import "PGPSignaturePacket.h"
-#import "PGPSignatureSubpacket.h"
-#import "PGPPartialSubKey.h"
-#import "PGPPartialSubKey+Private.h"
-#import "PGPUser.h"
-#import "PGPUser+Private.h"
-#import "PGPUserAttributePacket.h"
-#import "PGPUserAttributeSubpacket.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import "NSMutableData+PGPUtils.h"
-#import "NSArray+PGPUtils.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPartialKey
-
-- (instancetype)initWithPackets:(NSArray<PGPPacket *> *)packets {
- if ((self = [super init])) {
- _subKeys = [NSArray<PGPPartialSubKey *> array];
- _directSignatures = [NSArray<PGPSignaturePacket *> array];
- _users = [NSArray<PGPUser *> array];
- [self loadPackets:packets];
- }
- return self;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@, Type %@, primary key: %@", [super description], self.type == PGPKeyTypePublic ? @"public" : @"secret", self.primaryKeyPacket];
-}
-
-#pragma mark - Properties
-
-- (PGPKeyID *)keyID {
- let primaryKeyPacket = PGPCast(self.primaryKeyPacket, PGPPublicKeyPacket);
- NSParameterAssert(primaryKeyPacket);
- return [[PGPKeyID alloc] initWithFingerprint:primaryKeyPacket.fingerprint];
-}
-
-- (PGPFingerprint *)fingerprint {
- let primaryKeyPacket = PGPCast(self.primaryKeyPacket, PGPPublicKeyPacket);
- NSParameterAssert(primaryKeyPacket);
- return primaryKeyPacket.fingerprint;
-}
-
-- (BOOL)isEncryptedWithPassword {
- if (self.type == PGPKeyTypeSecret) {
- return PGPCast(self.primaryKeyPacket, PGPSecretKeyPacket).isEncryptedWithPassphrase;
- }
- return NO;
-}
-
-- (nullable NSDate *)expirationDate {
- PGPSignaturePacket * _Nullable primaryUserSelfCertificate = nil;
- [self primaryUserAndSelfCertificate:&primaryUserSelfCertificate];
- if (primaryUserSelfCertificate && primaryUserSelfCertificate.expirationDate) {
- return primaryUserSelfCertificate.expirationDate;
- }
-
- for (PGPPartialSubKey *subKey in self.subKeys) {
- if (PGPEqualObjects(subKey.keyID,self.keyID)) {
- let _Nullable signaturePacket = subKey.bindingSignature;
- if (signaturePacket && signaturePacket.expirationDate) {
- return signaturePacket.expirationDate;
- }
- }
- }
- return nil;
-}
-
-#pragma mark -
-
-- (PGPKeyType)type {
- PGPKeyType t = PGPKeyTypeUnknown;
-
- switch (self.primaryKeyPacket.tag) {
- case PGPPublicKeyPacketTag:
- case PGPPublicSubkeyPacketTag:
- t = PGPKeyTypePublic;
- break;
- case PGPSecretKeyPacketTag:
- case PGPSecretSubkeyPacketTag:
- t = PGPKeyTypeSecret;
- break;
- default:
- break;
- }
-
- return t;
-}
-
-- (void)loadPackets:(NSArray<PGPPacket *> *)packets {
- // based on packetlist2structure
- PGPKeyID *primaryKeyID;
- PGPPartialSubKey *subKey;
- PGPUser *user;
-
- for (PGPPacket *packet in packets) {
- switch (packet.tag) {
- case PGPPublicKeyPacketTag:
- primaryKeyID = PGPCast(packet, PGPPublicKeyPacket).keyID;
- self.primaryKeyPacket = packet;
- break;
- case PGPSecretKeyPacketTag:
- primaryKeyID = PGPCast(packet, PGPPublicKeyPacket).keyID;
- self.primaryKeyPacket = packet;
- break;
- case PGPUserAttributePacketTag:
- if (!user) {
- continue;
- }
- user.userAttribute = PGPCast(packet, PGPUserAttributePacket);
- break;
- case PGPUserIDPacketTag: {
- let parsedUser = [[PGPUser alloc] initWithUserIDPacket:(PGPUserIDPacket *)packet];
- if (!user) {
- user = parsedUser;
- }
- self.users = [self.users arrayByAddingObject:parsedUser];
- } break;
- case PGPPublicSubkeyPacketTag:
- case PGPSecretSubkeyPacketTag:
- user = nil;
- subKey = [[PGPPartialSubKey alloc] initWithPacket:packet];
- self.subKeys = [self.subKeys arrayByAddingObject:subKey];
- break;
- case PGPSignaturePacketTag: {
- let signaturePacket = PGPCast(packet, PGPSignaturePacket);
- PGPAssertClass(signaturePacket, signaturePacket);
- switch (signaturePacket.type) {
- case PGPSignatureGenericCertificationUserIDandPublicKey:
- case PGPSignatureCasualCertificationUserIDandPublicKey:
- case PGPSignaturePositiveCertificationUserIDandPublicKey:
- case PGPSignaturePersonalCertificationUserIDandPublicKey:
- if (!user) {
- continue;
- }
- if (PGPEqualObjects(signaturePacket.issuerKeyID,primaryKeyID)) {
- user.selfCertifications = [user.selfCertifications arrayByAddingObject:signaturePacket];
- } else {
- user.otherSignatures = [user.otherSignatures arrayByAddingObject:signaturePacket];
- }
- break;
- case PGPSignatureCertificationRevocation:
- if (user) {
- user.revocationSignatures = [user.revocationSignatures arrayByAddingObject:signaturePacket];
- } else {
- self.directSignatures = [self.directSignatures arrayByAddingObject:signaturePacket];
- }
- break;
- case PGPSignatureDirectlyOnKey:
- self.directSignatures = [self.directSignatures arrayByAddingObject:signaturePacket];
- break;
- case PGPSignatureSubkeyBinding:
- if (!subKey) {
- continue;
- }
-
- // TODO: check embedded signature "PGPSignaturePrimaryKeyBinding"
- // A signature that binds a signing subkey MUST have
- // an Embedded Signature subpacket in this binding signature that
- // contains a 0x19 signature made by the signing subkey on the
- // primary key and subkey.
-
- subKey.bindingSignature = PGPCast(packet, PGPSignaturePacket);
- break;
- case PGPSignatureKeyRevocation:
- self.revocationSignature = PGPCast(packet, PGPSignaturePacket);
- break;
- case PGPSignatureSubkeyRevocation:
- if (!subKey) {
- continue;
- }
- subKey.revocationSignature = PGPCast(packet, PGPSignaturePacket);
- break;
- default:
- break;
- }
- } break;
- default:
- break;
- }
- }
-}
-
-// signature packet that is available for signing data
-- (nullable PGPPacket *)signingKeyPacket {
- // It's private key for sign and public for verify as so thi can't be checked here
-
- NSAssert(self.type == PGPKeyTypeSecret, @"Need secret key to sign");
- if (self.type == PGPKeyTypePublic) {
- PGPLogDebug(@"Need secret key to sign\n %@", [NSThread callStackSymbols]);
- return nil;
- }
-
- // Favor subkey over primary key.
- // check subkeys, by default first check the subkeys
- for (PGPPartialSubKey *subKey in self.subKeys) {
- PGPSignaturePacket *signaturePacket = subKey.bindingSignature;
- if (signaturePacket.canBeUsedToSign) {
- return subKey.primaryKeyPacket;
- }
- }
-
- // check primary user self certificates
- PGPSignaturePacket *primaryUserSelfCertificate = nil;
- [self primaryUserAndSelfCertificate:&primaryUserSelfCertificate];
- if (primaryUserSelfCertificate) {
- if (primaryUserSelfCertificate.canBeUsedToSign) {
- return self.primaryKeyPacket;
- }
- }
-
- // By convention, the top-level key provides signature services
- return PGPCast(self.primaryKeyPacket, PGPSecretKeyPacket);
-}
-
-// signature packet that is available for verifying signature with a keyID
-- (nullable PGPPacket *)signingKeyPacketWithKeyID:(PGPKeyID *)keyID {
- for (PGPPartialSubKey *subKey in self.subKeys) {
- if (PGPEqualObjects(subKey.keyID,keyID)) {
- PGPSignaturePacket *signaturePacket = subKey.bindingSignature;
- if (signaturePacket.canBeUsedToSign) {
- return subKey.primaryKeyPacket;
- }
- }
- }
-
- // check primary user self certificates
- PGPSignaturePacket *primaryUserSelfCertificate = nil;
- [self primaryUserAndSelfCertificate:&primaryUserSelfCertificate];
- if (primaryUserSelfCertificate) {
- if (PGPEqualObjects(self.keyID,keyID)) {
- if (primaryUserSelfCertificate.canBeUsedToSign) {
- return self.primaryKeyPacket;
- }
- }
- }
-
- // By convention, the top-level key provides signature services
- return PGPCast(self.primaryKeyPacket, PGPSecretKeyPacket);
-}
-
-// signature packet that is available for signing data
-- (nullable PGPPacket *)encryptionKeyPacket:(NSError * __autoreleasing *)error {
- NSAssert(self.type == PGPKeyTypePublic, @"Need public key to encrypt");
- if (self.type == PGPKeyTypeSecret) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Wrong key type, require public key" }];
- }
- PGPLogDebug(@"Need public key to encrypt");
- return nil;
- }
-
- for (PGPPartialSubKey *subKey in self.subKeys) {
- let bindingSignature = subKey.bindingSignature;
- if (bindingSignature.canBeUsedToEncrypt) {
- return subKey.primaryKeyPacket;
- }
- }
-
- // check primary user self certificates
- PGPSignaturePacket *primaryUserSelfCertificate = nil;
- [self primaryUserAndSelfCertificate:&primaryUserSelfCertificate];
- if (primaryUserSelfCertificate) {
- if (primaryUserSelfCertificate.canBeUsedToEncrypt) {
- return self.primaryKeyPacket;
- }
- }
-
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Encryption key not found" }];
- }
-
- return nil;
-}
-
-- (nullable PGPSecretKeyPacket *)decryptionPacketForKeyID:(PGPKeyID *)keyID error:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(self.type == PGPKeyTypeSecret, @"Need secret key to encrypt");
- if (self.type == PGPKeyTypePublic) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Wrong key type, require secret key" }];
- }
- PGPLogDebug(@"Need public key to encrypt");
- return nil;
- }
-
- for (PGPPartialSubKey *subKey in self.subKeys) {
- let signaturePacket = subKey.bindingSignature;
- if (signaturePacket.canBeUsedToEncrypt && PGPEqualObjects(PGPCast(subKey.primaryKeyPacket, PGPSecretKeyPacket).keyID, keyID)) {
- return PGPCast(subKey.primaryKeyPacket, PGPSecretKeyPacket);
- }
- }
-
- // assume primary key is always capable
- if (PGPEqualObjects(PGPCast(self.primaryKeyPacket, PGPSecretKeyPacket).keyID, keyID)) {
- return PGPCast(self.primaryKeyPacket, PGPSecretKeyPacket);
- }
- return nil;
-}
-
-// TODO: return error
-- (nullable PGPPartialKey *)decryptedWithPassphrase:(NSString *)passphrase error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(passphrase, NSString);
-
- // decrypt copy of self
- let encryptedPartialKey = PGPCast(self.copy, PGPPartialKey);
- PGPAssertClass(encryptedPartialKey, PGPPartialKey);
-
- let primarySecretPacket = PGPCast(encryptedPartialKey.primaryKeyPacket, PGPSecretKeyPacket);
- if (!primarySecretPacket) {
- return nil;
- }
-
- // decrypt primary packet
- var decryptedPrimaryPacket = [primarySecretPacket decryptedWithPassphrase:passphrase error:error];
- if (!decryptedPrimaryPacket || *error) {
- return nil;
- }
-
- // decrypt subkeys packets
- for (PGPPartialSubKey *subKey in encryptedPartialKey.subKeys) {
- let subKeySecretPacket = PGPCast(subKey.primaryKeyPacket, PGPSecretKeyPacket);
- if (subKeySecretPacket) {
- let subKeyDecryptedPacket = [subKeySecretPacket decryptedWithPassphrase:passphrase error:error];
- if (!subKeyDecryptedPacket || *error) {
- return nil;
- }
- subKey.primaryKeyPacket = [subKeyDecryptedPacket copy];
- }
- }
-
- encryptedPartialKey.primaryKeyPacket = decryptedPrimaryPacket;
- return encryptedPartialKey;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToPartialKey:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToPartialKey:(PGPPartialKey *)other {
- return self.type == other.type &&
- PGPEqualObjects(self.primaryKeyPacket, other.primaryKeyPacket) &&
- PGPEqualObjects(self.users, other.users) &&
- PGPEqualObjects(self.subKeys, other.subKeys) &&
- PGPEqualObjects(self.directSignatures, other.directSignatures) &&
- PGPEqualObjects(self.revocationSignature, other.revocationSignature);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
-
- result = prime * result + self.type;
- result = prime * result + self.primaryKeyPacket.hash;
- result = prime * result + self.users.hash;
- result = prime * result + self.subKeys.hash;
- result = prime * result + self.directSignatures.hash;
- result = prime * result + self.revocationSignature.hash;
-
- return result;
-}
-
-#pragma mark - NSCopying
-
--(instancetype)copyWithZone:(nullable NSZone *)zone {
- let partialKey = PGPCast([[self.class allocWithZone:zone] initWithPackets:@[]], PGPPartialKey);
- PGPAssertClass(partialKey, PGPPartialKey);
-
- partialKey.type = self.type;
- partialKey.primaryKeyPacket = self.primaryKeyPacket;
- partialKey.users = [[NSArray alloc] initWithArray:self.users copyItems:YES];
- partialKey.subKeys = [[NSArray alloc] initWithArray:self.subKeys copyItems:YES];
- partialKey.directSignatures = [[NSArray alloc] initWithArray:self.directSignatures copyItems:YES];
- partialKey.revocationSignature = self.revocationSignature;
- return partialKey;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- let result = [NSMutableData data];
-
- for (PGPPacket *packet in self.allPacketsArray) {
- let exported = [packet export:error];
- if (!exported) {
- continue;
- }
-
- [result pgp_appendData:exported]; // TODO: decode secret key first
- if (error && *error) {
- PGPLogDebug(@"Problem while export public key: %@", [*error localizedDescription]);
- return nil;
- }
- }
- return result;
-}
-
-#pragma mark - Verification
-
-// Returns primary user with self certificate
-- (nullable PGPUser *)primaryUserAndSelfCertificate:(PGPSignaturePacket *__autoreleasing _Nullable *)selfCertificateOut {
- PGPUser *foundUser = nil;
-
- for (PGPUser *user in self.users) {
- if (!user.userID || user.userID.length == 0) {
- continue;
- }
-
- let selfCertificate = user.validSelfCertificate;
- if (!selfCertificate) {
- continue;
- }
-
- if (selfCertificate.isPrimaryUserID) {
- foundUser = user;
- } else if (!foundUser) {
- foundUser = user;
- }
-
- if (selfCertificateOut) {
- *selfCertificateOut = selfCertificate;
- }
- }
- return foundUser;
-}
-
-#pragma mark - Preferences
-
-- (PGPSymmetricAlgorithm)preferredSymmetricAlgorithm {
- return [self.class preferredSymmetricAlgorithmForKeys:@[self]];
-}
-
-+ (PGPSymmetricAlgorithm)preferredSymmetricAlgorithmForKeys:(NSArray<PGPPartialKey *> *)keys {
- // 13.2. Symmetric Algorithm Preferences
- // Since TripleDES is the MUST-implement algorithm, if it is not explicitly in the list, it is tacitly at the end.
-
- let preferecesArray = [NSMutableArray<NSArray<NSNumber *> *> array];
- for (PGPPartialKey *key in keys) {
- let keyAlgorithms = [NSMutableArray<NSNumber *> array];
-
- PGPSignaturePacket *selfCertificate = nil;
- let primaryUser = [key primaryUserAndSelfCertificate:&selfCertificate];
- if (primaryUser && selfCertificate) {
- let signatureSubpacket = [[selfCertificate subpacketsOfType:PGPSignatureSubpacketTypePreferredSymetricAlgorithm] firstObject];
- NSArray<NSNumber *> * _Nullable preferredSymetricAlgorithms = PGPCast(signatureSubpacket.value, NSArray);
- if (preferredSymetricAlgorithms) {
- [keyAlgorithms addObjectsFromArray:PGPNN(preferredSymetricAlgorithms)];
- }
- }
-
- if (keyAlgorithms.count > 0) {
- [preferecesArray addObject:keyAlgorithms];
- }
- }
-
- // intersect
- if (preferecesArray.count > 0) {
- let set = [NSMutableOrderedSet<NSNumber *> orderedSetWithArray:preferecesArray[0]];
- for (NSArray<NSNumber *> *prefArray in preferecesArray) {
- [set intersectSet:[NSSet setWithArray:prefArray]];
- }
- return (PGPSymmetricAlgorithm)[set[0] unsignedIntValue];
- }
-
- return PGPSymmetricTripleDES;
-}
-
-#pragma mark - Private
-
-/**
- * Ordered list of packets. Trust Packet is not exported.
- *
- * @return array
- */
-- (NSArray<PGPPacket *> *)allPacketsArray {
- // TODO: handle trust packet somehow. The Trust packet is used only within keyrings and is not normally exported.
- let arr = [NSMutableArray<PGPPacket *> array];
-
- [arr pgp_addObject:self.primaryKeyPacket];
- [arr pgp_addObject:self.revocationSignature];
-
- for (PGPSignaturePacket *packet in self.directSignatures) {
- [arr addObject:packet];
- }
-
- for (PGPUser *user in self.users) {
- [arr addObjectsFromArray:[user allPackets]];
- }
-
- for (PGPPartialSubKey *subKey in self.subKeys) {
- [arr addObjectsFromArray:[subKey allPackets]];
- }
-
- return arr;
-}
-
-- (NSArray<PGPPacket *> *)allKeyPackets {
- let arr = [NSMutableArray<PGPPacket *> arrayWithObject:self.primaryKeyPacket];
- for (PGPPartialSubKey *subKey in self.subKeys) {
- [arr addObject:subKey.primaryKeyPacket];
- }
- return arr;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPPartialSubKey.m b/enzevalos_iphone/ObjectivePGP/PGPPartialSubKey.m
deleted file mode 100755
index 02eb55e00d82fe749972f97ce7449b9765f71bec..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPPartialSubKey.m
+++ /dev/null
@@ -1,65 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPartialSubKey.h"
-#import "PGPPartialSubKey+Private.h"
-#import "PGPPartialKey.h"
-#import "PGPPartialKey+Private.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPFoundation.h"
-#import "PGPKeyID.h"
-#import "PGPMacros+Private.h"
-#import "NSArray+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPartialSubKey
-
-@dynamic revocationSignature;
-
-- (instancetype)initWithPacket:(PGPPacket *)packet {
- if ((self = [super initWithPackets:@[]])) {
- self.primaryKeyPacket = packet;
- }
- return self;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ %@", super.description, self.primaryKeyPacket.description];
-}
-
-- (PGPKeyID *)keyID {
- // note: public key packet because this is main class for public and secret class
- let primaryKeyPacket = PGPCast(self.primaryKeyPacket, PGPPublicKeyPacket);
- NSCAssert(primaryKeyPacket, @"Invalid packet");
- return [[PGPKeyID alloc] initWithFingerprint:primaryKeyPacket.fingerprint];
-}
-
-- (NSArray<PGPPacket *> *)allPackets {
- let arr = [NSMutableArray<PGPPacket *> arrayWithObject:self.primaryKeyPacket];
- [arr pgp_addObject:PGPCast(self.revocationSignature, PGPPacket)];
- [arr pgp_addObject:PGPCast(self.bindingSignature, PGPPacket)];
- return arr;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let _Nullable subKey = PGPCast([super copyWithZone:zone], PGPPartialSubKey);
- if (!subKey) {
- return nil;
- }
- subKey.primaryKeyPacket = self.primaryKeyPacket;
- subKey.bindingSignature = self.bindingSignature;
- subKey.revocationSignature = self.revocationSignature;
- return subKey;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPS2K.m b/enzevalos_iphone/ObjectivePGP/PGPS2K.m
deleted file mode 100755
index b8b3a4fc5b6a1a1b07f359a4e3f677968d2de10d..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPS2K.m
+++ /dev/null
@@ -1,265 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// A string to key (S2K) specifier encodes a mechanism for producing a key to be used with a symmetric block cipher from a string of octets.
-//
-
-#import "PGPS2K.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <CommonCrypto/CommonDigest.h>
-
-#import "NSData+PGPUtils.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPCryptoHash.h"
-#import "PGPCryptoUtils.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-static const unsigned int PGP_SALT_SIZE = 8;
-static const unsigned int PGP_DEFAULT_ITERATIONS_COUNT = 215;
-
-@interface PGPS2K ()
-
-@property (nonatomic, copy, readwrite) NSData *salt;
-
-@end
-
-@implementation PGPS2K
-
-- (instancetype)initWithSpecifier:(PGPS2KSpecifier)specifier hashAlgorithm:(PGPHashAlgorithm)hashAlgorithm {
- if ((self = [super init])) {
- _specifier = specifier;
- _hashAlgorithm = hashAlgorithm;
- _salt = [PGPCryptoUtils randomData:PGP_SALT_SIZE];
- _iterationsCount = PGP_DEFAULT_ITERATIONS_COUNT;
- }
- return self;
-}
-
-+ (PGPS2K *)S2KFromData:(NSData *)data atPosition:(NSUInteger)position length:(nullable NSUInteger *)length {
- PGPAssertClass(data, NSData);
-
- PGPS2K *s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierSimple hashAlgorithm:PGPHashSHA1]; // just default values, overriden in next line
- NSUInteger positionAfter = [s2k parseS2K:data atPosition:position];
- if (length) {
- *length = MAX(positionAfter - position, (NSUInteger)0);
- }
- return s2k;
-}
-
-- (NSUInteger)parseS2K:(NSData *)data atPosition:(NSUInteger)startingPosition {
- // S2K
-
- // string-to-key specifier is being given
- NSUInteger position = startingPosition;
- [data getBytes:&_specifier range:(NSRange){position, 1}];
- position = position + 1;
-
- NSAssert(_specifier == PGPS2KSpecifierIteratedAndSalted || _specifier == PGPS2KSpecifierSalted || _specifier == PGPS2KSpecifierSimple || _specifier == PGPS2KSpecifierGnuDummy || _specifier == PGPS2KSpecifierDivertToCard, @"Invalid s2k specifier");
-
- // this is not documented, but now I need to read S2K key specified by s2kSpecifier
- // 3.7.1.1. Simple S2K
-
- // Octet 1: hash algorithm
- [data getBytes:&_hashAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // Octets 2-9: 8-octet salt value
- if (self.specifier == PGPS2KSpecifierSalted || self.specifier == PGPS2KSpecifierIteratedAndSalted) {
- // read salt 8 bytes
- self.salt = [data subdataWithRange:(NSRange){position, PGP_SALT_SIZE}];
- position = position + self.salt.length;
- }
-
- // Octet 10: count, a one-octet, coded value
- if (_specifier == PGPS2KSpecifierIteratedAndSalted) {
- [data getBytes:&self->_iterationsCount range:(NSRange){position, 1}];
- position = position + 1;
- }
-
- if (self.specifier == PGPS2KSpecifierGnuDummy || self.specifier == PGPS2KSpecifierDivertToCard) {
- // read 3 bytes, and check if it's "GNU" followed by 0x01 || 0x02
- let gnuMarkerSize = 4;
- let gnuString = [[NSString alloc] initWithData:[data subdataWithRange:(NSRange){position, gnuMarkerSize - 1}] encoding:NSASCIIStringEncoding];
- if (PGPEqualObjects(gnuString,@"GNU")) {
- position = position + gnuMarkerSize;
- } else {
- PGPLogWarning(@"Unknown S2K");
- }
- }
-
- return position;
-}
-
-- (UInt32)codedIterationsCount {
- if (self.iterationsCount > 65011712) {
- return 255;
- }
-
- return ((UInt32)16 + (self.iterationsCount & 15)) << ((self.iterationsCount >> 4) + 6);
-}
-
-- (nullable NSData *)buildKeyDataForPassphrase:(NSData *)passphrase prefix:(nullable NSData *)prefix salt:(NSData *)salt codedCount:(UInt32)codedCount {
- PGPUpdateBlock updateBlock = nil;
- switch (self.specifier) {
- case PGPS2KSpecifierGnuDummy:
- // no secret key
- break;
- case PGPS2KSpecifierSimple: {
- let data = [NSMutableData dataWithData:prefix ?: [NSData data]];
- [data pgp_appendData:passphrase];
-
- // passphrase
- updateBlock = ^(PGP_NOESCAPE void (^update)(const void *data, int length)) {
- update(data.bytes, (int)data.length);
- };
- } break;
- case PGPS2KSpecifierSalted: {
- // salt + passphrase
- // This includes a "salt" value in the S2K specifier -- some arbitrary
- // data -- that gets hashed along with the passphrase string, to help
- // prevent dictionary attacks.
- let data = [NSMutableData dataWithData:prefix ?: [NSData data]];
- [data appendData:salt];
- [data pgp_appendData:passphrase];
-
- updateBlock = ^(PGP_NOESCAPE void (^update)(const void *data, int length)) {
- update(data.bytes, (int)data.length);
- };
- } break;
- case PGPS2KSpecifierIteratedAndSalted: {
- // iterated (salt + passphrase)
- let data = [NSMutableData dataWithData:salt];
- [data pgp_appendData:passphrase];
-
- updateBlock = ^(PGP_NOESCAPE void (^update)(const void *data, int length)) {
- // prefix first
- update(prefix.bytes, (int)prefix.length);
-
- // then iterate
- int iterations = 0;
- while (iterations * data.length < codedCount) {
- let nextTotalLength = (iterations + 1) * data.length;
- if (nextTotalLength > codedCount) {
- let totalLength = iterations * data.length;
- let remainder = [data subdataWithRange:(NSRange){0, codedCount - totalLength}];
- update(remainder.bytes, (int)remainder.length);
- } else {
- update(data.bytes, (int)data.length);
- }
- iterations++;
- }
- };
- } break;
- default:
- // unknown or unsupported
- break;
- }
-
- if (updateBlock) {
- return PGPCalculateHash(self.hashAlgorithm, updateBlock);
- }
-
- return nil;
-}
-
-/**
- * Calculate key for given passphrase
- * An S2K specifier can be stored in the secret keyring to specify how
- * to convert the passphrase to a key that unlocks the secret data.
- * Simple S2K hashes the passphrase to produce the session key.
- *
- * @param passphrase Passphrase
- * @param symmetricAlgorithm Cipher algorithm
- *
- * @return NSData with key
- */
-- (nullable NSData *)produceSessionKeyWithPassphrase:(NSString *)passphrase symmetricAlgorithm:(PGPSymmetricAlgorithm)symmetricAlgorithm {
- PGPAssertClass(passphrase, NSString);
-
- let passphraseData = [passphrase dataUsingEncoding:NSUTF8StringEncoding];
- var hashData = [self buildKeyDataForPassphrase:passphraseData prefix:nil salt:self.salt codedCount:self.codedIterationsCount];
- if (!hashData) {
- return nil;
- }
-
- // Keysize
- NSUInteger keySize = [PGPCryptoUtils keySizeOfSymmetricAlgorithm:symmetricAlgorithm];
- NSAssert(keySize <= 32, @"invalid keySize");
-
- /*
- If the hash size is less than the key size, multiple instances of the
- hash context are created -- enough to produce the required key data.
- These instances are preloaded with 0, 1, 2, ... octets of zeros (that
- is to say, the first instance has no preloading, the second gets
- preloaded with 1 octet of zero, the third is preloaded with two
- octets of zeros, and so forth).
- */
- if (hashData.length < keySize) {
- var level = 1;
- Byte zero = 0;
- let prefix = [NSMutableData data];
- let expandedHashData = [NSMutableData dataWithData:hashData];
- while (expandedHashData.length < keySize) {
- for (int i = 0; i < level; i++) {
- [prefix appendBytes:&zero length:1];
- }
-
- let prefixedHashData = [self buildKeyDataForPassphrase:passphraseData prefix:prefix salt:self.salt codedCount:self.codedIterationsCount];
- [expandedHashData appendData:prefixedHashData];
-
- level++;
- }
- hashData = expandedHashData;
- }
-
- // the high-order (leftmost) octets of the hash are used as the key.
- return [hashData subdataWithRange:(NSRange){0, MIN(hashData.length, keySize)}];
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- NSMutableData *data = [NSMutableData data];
- [data appendBytes:&_specifier length:1];
- [data appendBytes:&_hashAlgorithm length:1];
-
- if (self.specifier == PGPS2KSpecifierSalted || self.specifier == PGPS2KSpecifierIteratedAndSalted) {
- [data appendData:self.salt];
- }
-
- if (self.specifier == PGPS2KSpecifierIteratedAndSalted) {
- if (self.iterationsCount == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unexpected count: 0" }];
- }
- return nil;
- }
-
- [data appendBytes:&self->_iterationsCount length:1];
- }
-
- return data;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([[self.class allocWithZone:zone] initWithSpecifier:self.specifier hashAlgorithm:self.hashAlgorithm], PGPS2K);
- duplicate.salt = [self.salt copyWithZone:zone];
- duplicate.iterationsCount = self.iterationsCount;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/PGPUser.m b/enzevalos_iphone/ObjectivePGP/PGPUser.m
deleted file mode 100755
index 2d4b7325842188228087091d1b5eedfb86b1aa10..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/PGPUser.m
+++ /dev/null
@@ -1,218 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPUser.h"
-#import "PGPUser+Private.h"
-#import "PGPPartialKey.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPSignaturePacket.h"
-#import "PGPUserAttributePacket.h"
-#import "PGPUserAttributeImageSubpacket.h"
-#import "PGPUserIDPacket.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import "NSArray+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPUser
-
-@synthesize userIDPacket = _userIDPacket;
-
-- (instancetype)initWithUserIDPacket:(PGPUserIDPacket *)userPacket {
- PGPAssertClass(userPacket, PGPUserIDPacket);
-
- if (self = [super init]) {
- _userIDPacket = [userPacket copy];
- _otherSignatures = [NSArray<PGPSignaturePacket *> array];
- _revocationSignatures = [NSArray<PGPSignaturePacket *> array];
- _selfCertifications = [NSArray<PGPSignaturePacket *> array];
- }
- return self;
-}
-
-- (NSString *)userID {
- return self.userIDPacket.userID;
-}
-
-- (nullable NSData *)image {
- // find image uset attribute
- let imageAttributeSubpacket = PGPCast([[self.userAttribute.subpackets pgp_objectsPassingTest:^BOOL(PGPUserAttributeSubpacket * _Nonnull subpacket, BOOL * _Nonnull stop) {
- BOOL found = subpacket.type == PGPUserAttributeSubpacketImage;
- *stop = found;
- return found;
- }] firstObject], PGPUserAttributeImageSubpacket);
-
- return imageAttributeSubpacket.image;
-}
-
-- (void)setImage:(nullable NSData *)image {
- // Replace image subpacket
- if (!self.userAttribute) {
- self.userAttribute = [[PGPUserAttributePacket alloc] init];
- }
-
- NSMutableArray<PGPUserAttributeSubpacket *> *subpackets = [self.userAttribute.subpackets mutableCopy];
- let imageSubpacketIndex = [subpackets indexOfObjectPassingTest:^BOOL(PGPUserAttributeSubpacket * _Nonnull subpacket, NSUInteger __unused idx, BOOL * _Nonnull stop) {
- BOOL found = subpacket.type == PGPUserAttributeSubpacketImage;
- *stop = found;
- return found;
- }];
-
- if (imageSubpacketIndex != NSNotFound) {
- [subpackets removeObjectAtIndex:imageSubpacketIndex];
- }
-
- let imageSubpacket = [PGPUserAttributeImageSubpacket new];
- imageSubpacket.type = PGPUserAttributeSubpacketImage;
- imageSubpacket.image = image;
-
- [subpackets addObject:imageSubpacket];
- self.userAttribute.subpackets = [subpackets copy];
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ %@", [super description], self.userID];
-}
-
-- (NSArray<PGPPacket *> *)allPackets {
- let arr = [NSMutableArray<PGPPacket *> array];
-
- [arr pgp_addObject:self.userIDPacket];
- [arr pgp_addObject:self.userAttribute];
-
- for (id packet in self.revocationSignatures) {
- [arr addObject:packet];
- }
-
- for (id packet in self.selfCertifications) {
- [arr addObject:packet];
- }
-
- for (id packet in self.otherSignatures) {
- [arr addObject:packet];
- }
-
- return arr;
-}
-
-// TODO:
-// User.prototype.getValidSelfCertificate = function(primaryKey) {
-// if (!this.selfCertifications) {
-// return null;
-// }
-// var validCert = [];
-// for (var i = 0; i < this.selfCertifications.length; i++) {
-// if (this.isRevoked(this.selfCertifications[i], primaryKey)) {
-// continue;
-// }
-// if (!this.selfCertifications[i].isExpired() &&
-// (this.selfCertifications[i].verified ||
-// this.selfCertifications[i].verify(primaryKey, {userid: this.userId || this.userAttribute, key: primaryKey}))) {
-// validCert.push(this.selfCertifications[i]);
-// }
-// }
-// // most recent first
-// validCert = validCert.sort(function(a, b) {
-// a = a.created;
-// b = b.created;
-// return a>b ? -1 : a<b ? 1 : 0;
-// });
-// return validCert[0];
-//};
-
-// Returns the most significant (latest valid) self signature of the user
-- (nullable PGPSignaturePacket *)validSelfCertificate {
- if (self.selfCertifications.count == 0) {
- return nil;
- }
-
- NSMutableArray *certs = [NSMutableArray array];
- for (PGPSignaturePacket *signature in self.selfCertifications) {
- // TODO: check for revocation
-
- if (signature.isExpired) {
- continue;
- }
- [certs addObject:signature];
- // This only worked as verify wasn't implemented correctly
- // TODO: find a better solution
- //
- // // (this is the craziest thing I ever seen today)
- // NSError *error;
- // [signature verifyData:nil withKey:key signingKeyPacket:(PGPPublicKeyPacket *)key.primaryKeyPacket userID:self.userID error:&error];
- // //BOOL status = [signature verifyData:nil withKey:key signingKeyPacket:(PGPPublicKeyPacket *)key.primaryKeyPacket userID:self.userID error:&error];
- // //if (!status) {
- // // NSLog(@"ObjectivePGP: %@",error);
- // //}
- // //NSAssert(status == YES,@"not verified");
- //
- // if (status == YES) {
- // [certs addObject:signature];
- // }
- }
-
- [certs sortUsingComparator:^NSComparisonResult(id obj1, id obj2) {
- let sig1 = PGPCast(obj1, PGPSignaturePacket);
- let sig2 = PGPCast(obj2, PGPSignaturePacket);
- if (sig1.creationDate && sig2.creationDate) {
- return [PGPNN(sig1.creationDate) compare:PGPNN(sig2.creationDate)];
- }
- return NSOrderedSame;
- }];
-
- return [certs firstObject];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToUser:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToUser:(PGPUser *)other {
- return PGPEqualObjects(self.userID,other.userID) &&
- PGPEqualObjects(self.userAttribute,other.userAttribute) &&
- PGPEqualObjects(self.selfCertifications,other.selfCertifications) &&
- PGPEqualObjects(self.otherSignatures,other.otherSignatures) &&
- PGPEqualObjects(self.revocationSignatures,other.revocationSignatures) &&
- PGPEqualObjects(self.userIDPacket,other.userIDPacket);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
-
- result = prime * result + self.userID.hash;
- result = prime * result + self.userAttribute.hash;
- result = prime * result + self.selfCertifications.hash;
- result = prime * result + self.otherSignatures.hash;
- result = prime * result + self.revocationSignatures.hash;
- result = prime * result + self.userIDPacket.hash;
-
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let user = PGPCast([[self.class allocWithZone:zone] initWithUserIDPacket:self.userIDPacket], PGPUser);
- user.userAttribute = self.userAttribute;
- user.selfCertifications = [[NSArray alloc] initWithArray:self.selfCertifications copyItems:YES];
- user.otherSignatures = [[NSArray alloc] initWithArray:self.otherSignatures copyItems:YES];
- user.revocationSignatures = [[NSArray alloc] initWithArray:self.revocationSignatures copyItems:YES];
- return user;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPCompressedPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPCompressedPacket.m
deleted file mode 100755
index 812638102fe8090d2d6cf4674ddf73fe68918496..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPCompressedPacket.m
+++ /dev/null
@@ -1,142 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPCompressedPacket.h"
-#import "NSData+compression.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import "PGPLogging.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPCompressedPacket ()
-
-@property (nonatomic, readwrite) PGPCompressionAlgorithm compressionType;
-@property (nonatomic, copy, readwrite) NSData *decompressedData;
-
-@end
-
-@implementation PGPCompressedPacket
-
-- (instancetype)initWithData:(NSData *)data type:(PGPCompressionAlgorithm)type {
- if (self = [self init]) {
- _decompressedData = [data copy];
- _compressionType = type;
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPCompressedDataPacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // - One octet that gives the algorithm used to compress the packet.
- [packetBody getBytes:&_compressionType length:sizeof(_compressionType)];
- position = position + 1;
-
- // - Compressed data, which makes up the remainder of the packet.
- let compressedData = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
-
- switch (self.compressionType) {
- case PGPCompressionZIP:
- self.decompressedData = [compressedData zipDecompressed:error];
- break;
- case PGPCompressionZLIB:
- self.decompressedData = [compressedData zlibDecompressed:error];
- break;
- case PGPCompressionBZIP2:
- self.decompressedData = [compressedData bzip2Decompressed:error];
- break;
-
- default:
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"This type of compression is not supported" }];
- }
- break;
- }
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- let bodyData = [NSMutableData data];
-
- // - One octet that gives the algorithm used to compress the packet.
- [bodyData appendBytes:&_compressionType length:sizeof(_compressionType)];
-
- // - Compressed data, which makes up the remainder of the packet.
- NSData * _Nullable compressedData = nil;
- switch (self.compressionType) {
- case PGPCompressionZIP:
- compressedData = [self.decompressedData zipCompressed:error];
- break;
- case PGPCompressionZLIB:
- compressedData = [self.decompressedData zlibCompressed:error];
- break;
- case PGPCompressionBZIP2:
- compressedData = [self.decompressedData bzip2Compressed:error];
- break;
- default:
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"This type of compression is not supported" }];
- }
- return nil;
- break;
- }
-
- if (error && *error) {
- PGPLogDebug(@"Compression failed: %@", (*error).localizedDescription);
- return nil;
- }
- [bodyData pgp_appendData:compressedData];
-
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return bodyData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToCompressedPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToCompressedPacket:(PGPCompressedPacket *)packet {
- return self.compressionType == packet.compressionType &&
- PGPEqualObjects(self.decompressedData, packet.decompressedData);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.compressionType;
- result = prime * result + self.decompressedData.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([super copyWithZone:zone], PGPCompressedPacket);
- PGPAssertClass(duplicate, PGPCompressedPacket)
- duplicate.compressionType = self.compressionType;
- duplicate.decompressedData = self.decompressedData;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPLiteralPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPLiteralPacket.m
deleted file mode 100755
index 92f4ebe573c492dab9d5f72a20918d6264eaed93..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPLiteralPacket.m
+++ /dev/null
@@ -1,181 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPLiteralPacket.h"
-#import "PGPTypes.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPLiteralPacket ()
-@end
-
-@implementation PGPLiteralPacket
-
-- (instancetype)init {
- if (self = [super init]) {
- _format = PGPLiteralPacketBinary;
- }
- return self;
-}
-
-- (instancetype)initWithData:(NSData *)rawData {
- if (self = [self init]) {
- _literalRawData = [rawData copy];
- }
- return self;
-}
-
-+ (PGPLiteralPacket *)literalPacket:(PGPLiteralPacketFormat)format withData:(NSData *)rawData {
- let literalPacket = [[PGPLiteralPacket alloc] init];
- literalPacket.format = format;
- literalPacket.literalRawData = rawData;
- return literalPacket;
-}
-
-- (PGPPacketTag)tag {
- return PGPLiteralDataPacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // A one-octet field that describes how the data is formatted.
- [packetBody getBytes:&_format range:(NSRange){position, 1}];
- position = position + 1;
-
- NSAssert(self.format == PGPLiteralPacketBinary || self.format == PGPLiteralPacketText || self.format == PGPLiteralPacketTextUTF8, @"Unkown data format");
- if (self.format != PGPLiteralPacketBinary && self.format != PGPLiteralPacketText && self.format != PGPLiteralPacketTextUTF8) {
- // skip
- return 1 + packetBody.length;
- }
-
- UInt8 filenameLength = 0;
- [packetBody getBytes:&filenameLength range:(NSRange){position, 1}];
- position = position + 1;
-
- // filename
- if (filenameLength > 0) {
- self.filename = [[NSString alloc] initWithData:[packetBody subdataWithRange:(NSRange){position, filenameLength}] encoding:NSUTF8StringEncoding];
- position = position + filenameLength;
- }
-
- // If the special name "_CONSOLE" is used, the message is considered to be "for your eyes only".
-
- // data date
- UInt32 creationTimestamp = 0;
- [packetBody getBytes:&creationTimestamp range:(NSRange){position, 4}];
- creationTimestamp = CFSwapInt32BigToHost(creationTimestamp);
- self.timestamp = [NSDate dateWithTimeIntervalSince1970:creationTimestamp];
- position = position + 4;
- let data = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
-
- switch (self.format) {
- case PGPLiteralPacketBinary:
- case PGPLiteralPacketText:
- case PGPLiteralPacketTextUTF8:
- // don't tamper the data, otherwise signature verification fails
- self.literalRawData = data;
- break;
- default:
- break;
- }
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- if (!self.literalRawData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Missing literal data" }];
- }
- return nil;
- }
-
- let bodyData = [NSMutableData data];
- [bodyData appendBytes:&_format length:1];
-
- if (self.filename) {
- UInt8 filenameLength = (UInt8)[self.filename lengthOfBytesUsingEncoding:NSUTF8StringEncoding];
- [bodyData appendBytes:&filenameLength length:1];
- [bodyData appendBytes:[self.filename cStringUsingEncoding:NSUTF8StringEncoding] length:filenameLength];
- } else {
- UInt8 zero[] = {0x00};
- [bodyData appendBytes:&zero length:sizeof(zero)];
- }
-
- if (self.timestamp) {
- UInt32 timestampBytes = (UInt32)[self.timestamp timeIntervalSince1970];
- timestampBytes = CFSwapInt32HostToBig(timestampBytes);
- [bodyData appendBytes:×tampBytes length:4];
- } else {
- UInt8 zero4[] = {0, 0, 0, 0};
- [bodyData appendBytes:&zero4 length:4];
- }
-
- switch (self.format) {
- case PGPLiteralPacketText:
- case PGPLiteralPacketTextUTF8:
- case PGPLiteralPacketBinary:
- [bodyData appendData:self.literalRawData];
- break;
- default:
- break;
- }
-
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return bodyData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToLiteralPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToLiteralPacket:(PGPLiteralPacket *)packet {
- return self.format == packet.format &&
- PGPEqualObjects(self.timestamp, packet.timestamp) &&
- PGPEqualObjects(self.filename, packet.filename) &&
- PGPEqualObjects(self.literalRawData, packet.literalRawData);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.format;
- result = prime * result + self.timestamp.hash;
- result = prime * result + self.filename.hash;
- result = prime * result + self.literalRawData.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPLiteralPacket);
- if (!duplicate) {
- return nil;
- }
-
- duplicate.format = self.format;
- duplicate.timestamp = self.timestamp;
- duplicate.filename = self.filename;
- duplicate.literalRawData = self.literalRawData;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPModificationDetectionCodePacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPModificationDetectionCodePacket.m
deleted file mode 100755
index 148c01e7b33a077610a4a9380f7c34f7f3ed994f..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPModificationDetectionCodePacket.m
+++ /dev/null
@@ -1,92 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-// MDC
-
-#import "PGPModificationDetectionCodePacket.h"
-#import "NSData+PGPUtils.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPModificationDetectionCodePacket ()
-
-@property (nonatomic, readwrite) NSData *hashData;
-
-@end
-
-@implementation PGPModificationDetectionCodePacket
-
-- (instancetype)initWithData:(NSData *)data {
- if (self = [self init]) {
- self->_hashData = [data pgp_SHA1];
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPModificationDetectionCodePacketTag; // 19
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // 5.14. Modification Detection Code Packet (Tag 19)
- NSAssert(packetBody.length == CC_SHA1_DIGEST_LENGTH, @"A Modification Detection Code packet MUST have a length of 20 octets");
-
- self->_hashData = [packetBody subdataWithRange:(NSRange){position, CC_SHA1_DIGEST_LENGTH}];
- position = position + self.hashData.length;
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return [self.hashData subdataWithRange:(NSRange){0, CC_SHA1_DIGEST_LENGTH}]; // force limit to 20 octets
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToDetectionCodePacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToDetectionCodePacket:(PGPModificationDetectionCodePacket *)packet {
- return PGPEqualObjects(self.hashData, packet.hashData);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.hashData.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPModificationDetectionCodePacket);
- if (!duplicate) {
- return nil;
- }
-
- duplicate.hashData = self.hashData;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPOnePassSignaturePacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPOnePassSignaturePacket.m
deleted file mode 100755
index ccdcb52503eb43be8d1f0ff9cc3aadfc885f648d..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPOnePassSignaturePacket.m
+++ /dev/null
@@ -1,129 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPOnePassSignaturePacket.h"
-#import "PGPKeyID.h"
-#import "PGPMacros.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-#import "NSMutableData+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPOnePassSignaturePacket
-
-- (id)init {
- if (self = [super init]) {
- _version = 0x03;
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPOnePassSignaturePacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- [packetBody getBytes:&_version range:(NSRange){position, 1}];
- position = position + 1;
-
- [packetBody getBytes:&_signatureType range:(NSRange){position, 1}];
- position = position + 1;
-
- [packetBody getBytes:&_hashAlgorith range:(NSRange){position, 1}];
- position = position + 1;
-
- [packetBody getBytes:&_publicKeyAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- self.keyID = [[PGPKeyID alloc] initWithLongKey:[packetBody subdataWithRange:(NSRange){position, 8}]];
- position = position + 8;
-
- BOOL nestedValue;
- [packetBody getBytes:&nestedValue range:(NSRange){position, 1}];
- _isNested = nestedValue == 0 ? YES : NO;
- position = position + 1;
-
- return position;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToOnePassSignaturePacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToOnePassSignaturePacket:(PGPOnePassSignaturePacket *)packet {
- return self.version == packet.version &&
- self.signatureType == packet.signatureType &&
- self.hashAlgorith == packet.hashAlgorith &&
- self.publicKeyAlgorithm == packet.publicKeyAlgorithm &&
- PGPEqualObjects(self.keyID, packet.keyID) &&
- self.isNested == packet.isNested;
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.signatureType;
- result = prime * result + self.hashAlgorith;
- result = prime * result + self.publicKeyAlgorithm;
- result = prime * result + self.keyID.hash;
- result = prime * result + self.isNested;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPOnePassSignaturePacket);
- if (!duplicate) {
- return nil;
- }
-
- duplicate.version = self.version;
- duplicate.signatureType = self.signatureType;
- duplicate.hashAlgorith = self.hashAlgorith;
- duplicate.publicKeyAlgorithm = self.publicKeyAlgorithm;
- duplicate.keyID = self.keyID;
- duplicate.isNested = self.isNested;
- return duplicate;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(self.keyID, @"Missing keyID");
-
- pgpweakify(self);
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- pgpstrongify(self)
- let bodyData = [NSMutableData data];
-
- [bodyData appendBytes:&self->_version length:1];
- [bodyData appendBytes:&self->_signatureType length:1];
- [bodyData appendBytes:&self->_hashAlgorith length:1];
- [bodyData appendBytes:&self->_publicKeyAlgorithm length:1];
- [bodyData pgp_appendData:[self.keyID export:error]];
-
- [bodyData appendBytes:&self->_isNested length:1];
-
- return bodyData;
- }];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPPacket.m
deleted file mode 100755
index f61feb8030fa15829c23ec7049ef70a5c35262f2..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPPacket.m
+++ /dev/null
@@ -1,235 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPacket.h"
-#import "PGPPacket+Private.h"
-#import "PGPPacketHeader.h"
-#import "NSData+PGPUtils.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPacket
-
-- (instancetype)init {
- if ((self = [super init])) {
- _tag = PGPInvalidPacketTag;
- }
- return self;
-}
-
-+ (nullable instancetype)packetWithBody:(NSData *)bodyData {
- PGPAssertClass(bodyData, NSData);
-
- id packet = [[self.class alloc] init];
-
- NSError *error = nil;
- if ([packet respondsToSelector:@selector(parsePacketBody:error:)]) {
- [packet parsePacketBody:bodyData error:&error];
- } else {
- return nil;
- }
-
- if (error) {
- return nil;
- }
-
- return packet;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(packetBody, NSData);
- return 0;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- [NSException raise:@"MissingExportMethod" format:@"export: selector not overriden"];
- return nil;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToPacket:(PGPPacket *)packet {
- return self.tag == packet.tag && self.indeterminateLength == packet.indeterminateLength;
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
- result = prime * result + self.tag;
- result = prime * result + (NSUInteger)self.indeterminateLength;
- return result;
-}
-
-#pragma mark - Packet header
-
-// 4.2. Packet Headers
-/// Parse packet header and body, and return body. Parse packet header and read the followed data (packet body)
-+ (nullable NSData *)readPacketBody:(NSData *)data headerLength:(UInt32 *)headerLength consumedBytes:(nullable NSUInteger *)consumedBytes packetTag:(nullable PGPPacketTag *)tag indeterminateLength:(nullable BOOL *)indeterminateLength {
- NSParameterAssert(headerLength);
-
- UInt8 headerByte = 0;
- [data getBytes:&headerByte range:(NSRange){0, 1}];
-
- BOOL isPGPHeader = !!(headerByte & PGPHeaderPacketTagAllwaysSet);
- BOOL isNewFormat = !!(headerByte & PGPHeaderPacketTagNewFormat);
-
- if (!isPGPHeader) {
- // not a valida data, skip the whole data.
- if (consumedBytes) { *consumedBytes = data.length; }
- return nil;
- }
-
- PGPPacketHeader *header = nil;
- if (isNewFormat) {
- header = [PGPPacketHeader newFormatHeaderFromData:data];
- } else {
- header = [PGPPacketHeader oldFormatHeaderFromData:data];
- }
-
- if (header.isIndeterminateLength) {
- // overwrite header body length
- header.bodyLength = (UInt32)data.length - header.headerLength;
- }
-
- *headerLength = header.headerLength;
- if (tag) { *tag = header.packetTag; }
- if (indeterminateLength) { *indeterminateLength = header.isIndeterminateLength; }
-
- if (header.isPartialLength && !header.isIndeterminateLength) {
- // Partial data starts with length octets offset (right after the packet header byte)
- let partialData = [data subdataWithRange:(NSRange){header.headerLength - 1, data.length - (header.headerLength - 1)}];
- NSUInteger partialConsumedBytes = 0;
- let concatenatedData = [PGPPacket readPartialData:partialData consumedBytes:&partialConsumedBytes];
- if (consumedBytes) { *consumedBytes = partialConsumedBytes + 1; }
- return concatenatedData;
- }
-
- if (consumedBytes) { *consumedBytes = header.bodyLength + header.headerLength; }
- return [data subdataWithRange:(NSRange){header.headerLength, header.bodyLength}];
-}
-
-// Read partial data. Part by part and return concatenated body data
-+ (NSData *)readPartialData:(NSData *)data consumedBytes:(NSUInteger *)consumedBytes {
- BOOL hasMoreData = YES;
- NSUInteger offset = 0;
- let accumulatedData = [NSMutableData dataWithCapacity:data.length];
-
- while (hasMoreData) {
- BOOL isPartial = NO;
- NSUInteger partBodyLength = 0;
- UInt8 partLengthOctets = 0;
-
- // length + body
- let partData = [data subdataWithRange:(NSRange){offset, data.length - offset}];
- [PGPPacketHeader getLengthFromNewFormatOctets:partData bodyLength:&partBodyLength bytesCount:&partLengthOctets isPartial:&isPartial];
-
- // the last Body Length header can be a zero-length header.
- // in that case just skip it.
- if (partBodyLength > 0) {
- partBodyLength = MIN(partBodyLength, data.length - offset);
-
- // Append just body. Skip the length bytes.
- let partBodyData = [data subdataWithRange:(NSRange){offset + partLengthOctets, partBodyLength}];
- [accumulatedData appendData:partBodyData];
- }
-
- // move to next part
- offset = offset + partLengthOctets + partBodyLength;
- hasMoreData = isPartial;
- }
-
- *consumedBytes = offset;
- return accumulatedData;
-}
-
-#pragma mark - Build
-
-+ (NSData *)buildPacketOfType:(PGPPacketTag)tag withBody:(PGP_NOESCAPE NSData *(^)(void))body {
- return [self buildPacketOfType:tag isOld:NO withBody:body];
-}
-
-+ (NSData *)buildPacketOfType:(PGPPacketTag)tag isOld:(BOOL)isOld withBody:(PGP_NOESCAPE NSData *(^)(void))body {
- // 4.2.2. New Format Packet Lengths
- let data = [NSMutableData data];
- let bodyData = body();
-
- UInt8 packetTag = 0;
-
- // Bit 7 -- Always one
- packetTag |= PGPHeaderPacketTagAllwaysSet;
-
- // Bit 6 -- New packet format if set
- if (!isOld) {
- packetTag |= PGPHeaderPacketTagNewFormat;
- }
-
- if (isOld) {
- // Bits 5-2 -- packet tag
- packetTag |= (tag << 4) >> 2;
-
- // Bits 1-0 -- length-type
- UInt64 bodyLength = bodyData.length;
- if (bodyLength < 0xFF) {
- // 0 - The packet has a one-octet length. The header is 2 octets long.
- packetTag |= 0;
- } else if (bodyLength <= 0xFFFF) {
- // 1 - The packet has a two-octet length. The header is 3 octets long.
- packetTag |= 1;
- } else if (bodyLength <= 0xFFFFFFFF) {
- // 2 - The packet has a four-octet length. The header is 5 octets long.
- packetTag |= 2;
- } else {
- // 3 - The packet is of indeterminate length.
- // In general, an implementation SHOULD NOT use indeterminate-length packets except where the end of the data will be clear from the context
- packetTag |= 3;
- NSAssert(NO, @"In general, an implementation SHOULD NOT use indeterminate-length packets");
- }
- } else {
- // Bits 5-0 -- packet tag
- packetTag |= tag;
- }
-
- // write ptag
- [data appendBytes:&packetTag length:1];
-
- // write header
- if (isOld) {
- [data appendData:[PGPPacketHeader buildOldFormatLengthDataForData:bodyData]];
- } else {
- [data appendData:[PGPPacketHeader buildNewFormatLengthDataForData:bodyData]];
- }
-
- // write packet body
- [data appendData:bodyData];
-
- return data;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- PGPPacket *duplicate = [[self.class allocWithZone:zone] init];
- duplicate.tag = self.tag;
- duplicate.indeterminateLength = self.indeterminateLength;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPPacketHeader.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPPacketHeader.m
deleted file mode 100755
index 8fdca3541d89530f33f501be0abf799167a40327..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPPacketHeader.m
+++ /dev/null
@@ -1,213 +0,0 @@
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPacketHeader.h"
-#import "PGPMacros+Private.h"
-#import "PGPTypes.h"
-#import "PGPLogging.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPacketHeader
-
-- (instancetype)init {
- if ((self = [super init])) {
- _packetTag = PGPInvalidPacketTag;
- _bodyLength = PGPUnknownLength;
- _partialLength = NO;
- _indeterminateLength = NO;
- }
- return self;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"headerLength: %@, bodyLength: %@, isPartial: %@", @(self.headerLength), @(self.bodyLength), self.isPartialLength ? @"YES" : @"NO"];
-}
-
-+ (void)getLengthFromNewFormatOctets:(NSData *)lengthOctetsData bodyLength:(NSUInteger *)bodyLength bytesCount:(UInt8 *)bytesCount isPartial:(nullable BOOL *)isPartial {
- const UInt8 *lengthOctets = lengthOctetsData.bytes;
-
- // should check for partial? Is partial data expected?
- BOOL isExpectingPartialData = isPartial ? YES : NO;
-
- if (lengthOctets[0] < 192) {
- // 4.2.2.1. One-Octet Length
- // bodyLen = 1st_octet;
- *bodyLength = lengthOctets[0];
- *bytesCount = 1;
- } else if ((isExpectingPartialData && lengthOctets[0] >= 192 && lengthOctets[0] < 224) || (!isExpectingPartialData && lengthOctets[0] >= 192 && lengthOctets[0] < 255)) {
- // 4.2.2.2. Two-Octet Lengths
- // bodyLen = ((1st_octet - 192) << 8) + (2nd_octet) + 192
- *bodyLength = ((lengthOctets[0] - 192) << 8) + (lengthOctets[1]) + 192;
- *bytesCount = 2;
- } else if (isExpectingPartialData && lengthOctets[0] >= 224 && lengthOctets[0] < 255) {
- // 4.2.2.4. Partial Body Length
- // partialBodyLen = 1 << (1st_octet & 0x1F);
- *bodyLength = 1 << (lengthOctets[0] & 0x1F);
- *bytesCount = 1;
- *isPartial = YES;
- } else if (lengthOctets[0] == 255) {
- // 4.2.2.3. Five-Octet Length
- // bodyLen = (2nd_octet << 24) | (3rd_octet << 16) |
- // (4th_octet << 8) | 5th_octet
- *bodyLength = (lengthOctets[1] << 24) | (lengthOctets[2] << 16) | (lengthOctets[3] << 8) | lengthOctets[4];
- *bytesCount = 5;
- } else {
- // indeterminate length? that's not how it suppose to work, buy hey!
- PGPLogWarning(@"Unexpected indeterminate length for the packet.");
- *bodyLength = PGPUnknownLength;
- *bytesCount = 1;
- }
-}
-
-// 4.2. Packet Headers
-+ (nullable PGPPacketHeader *)newFormatHeaderFromData:(NSData *)data {
- NSParameterAssert(data);
-
- if (data.length < 1) {
- return nil;
- }
-
- UInt8 headerByte = 0;
- [data getBytes:&headerByte length:1];
- // Bits 5-0 -- packet tag
- UInt8 packetTag = (UInt8)(headerByte << 2);
- packetTag = (packetTag >> 2);
-
- // up to 5 bytes for length
- UInt8 lengthOctetsCount = 0;
- NSUInteger bodyLength = 0;
- BOOL isPartial = NO;
- let lengthOctets = [data subdataWithRange:(NSRange){1, MIN((NSUInteger)5, data.length - 1)}];
- [PGPPacketHeader getLengthFromNewFormatOctets:lengthOctets bodyLength:&bodyLength bytesCount:&lengthOctetsCount isPartial:&isPartial];
-
- PGPPacketHeader *header = [PGPPacketHeader new];
- header.packetTag = packetTag;
- header.headerLength = 1 + lengthOctetsCount; // packet header + length octets
- header.bodyLength = bodyLength;
- header.partialLength = isPartial;
- header.indeterminateLength = header.bodyLength == PGPUnknownLength;
- return header;
-}
-
-// 4.2. Packet Headers
-+ (nullable PGPPacketHeader *)oldFormatHeaderFromData:(NSData *)data {
- NSParameterAssert(data);
-
- if (data.length < 1) {
- return nil;
- }
-
- UInt8 headerByte = 0;
- [data getBytes:&headerByte length:1];
- // Bits 5-2 -- packet tag
- UInt8 packetTag = (UInt8)(headerByte << 2);
- packetTag = (packetTag >> 4);
-
- // Bits 1-0 -- length-type
- UInt8 bodyLengthType = (UInt8)(headerByte << 6);
- bodyLengthType = bodyLengthType >> 6;
-
- BOOL isIndeterminateLength = NO;
- UInt32 headerLength = 1;
- UInt32 bodyLength = 0;
- switch (bodyLengthType) {
- case 0: {
- NSRange range = (NSRange){1, 1};
- [data getBytes:&bodyLength range:range];
- headerLength = (UInt32)(1 + range.length);
- } break;
- case 1: {
- UInt16 bLen = 0;
- NSRange range = (NSRange){1, 2};
- [data getBytes:&bLen range:range];
- // value of a two-octet scalar is ((n[0] << 8) + n[1]).
- bodyLength = CFSwapInt16BigToHost(bLen);
- headerLength = (UInt32)(1 + range.length);
- } break;
- case 2: {
- NSRange range = (NSRange){1, 4};
- [data getBytes:&bodyLength range:range];
- bodyLength = CFSwapInt32BigToHost(bodyLength);
- headerLength = (UInt32)(1 + range.length);
- } break;
- case 3: {
- PGPLogWarning(@"(Old format) The packet is of indeterminate length");
- bodyLength = PGPUnknownLength;
- headerLength = 1;
- isIndeterminateLength = YES;
- } break;
- default:
- PGPLogWarning(@"Invalid packet length. Skipping...");
- return nil;
- }
-
- PGPPacketHeader *header = [PGPPacketHeader new];
- header.headerLength = headerLength;
- header.bodyLength = bodyLength;
- header.packetTag = packetTag;
- header.partialLength = NO;
- header.indeterminateLength = isIndeterminateLength;
-
- return header;
-}
-
-+ (NSData *)buildNewFormatLengthDataForData:(NSData *)bodyData {
- let data = [NSMutableData data];
- // write length octets
- UInt64 bodyLength = bodyData.length;
- if (bodyLength < 192) {
- // 1 octet
- [data appendBytes:&bodyLength length:1];
- } else if (bodyLength >= 192 && bodyLength <= 8383) {
- // 2 octet
- UInt8 buf[2] = {0, 0};
- UInt16 twoOctets = (UInt16)bodyLength;
- buf[0] = (UInt8)((twoOctets - 192) >> 8) + 192;
- buf[1] = (UInt8)(twoOctets - 192);
- [data appendBytes:buf length:2];
- } else {
- // 5 octet
- UInt64 fiveOctets = bodyLength;
-
- UInt8 buf[5] = {0xFF, 0, 0, 0, 0};
- buf[1] = (UInt8)(fiveOctets >> 24);
- buf[2] = (UInt8)(fiveOctets >> 16);
- buf[3] = (UInt8)(fiveOctets >> 8);
- buf[4] = (UInt8)(fiveOctets);
- [data appendBytes:buf length:5];
- }
- return data;
-}
-
-+ (NSData *)buildOldFormatLengthDataForData:(NSData *)bodyData {
- let data = [NSMutableData data];
- UInt64 bodyLength = bodyData.length;
- if (bodyLength < 0xFF) {
- // 0 - The packet has a one-octet length. The header is 2 octets long.
- let bodyLengthBE = bodyLength;
- [data appendBytes:&bodyLengthBE length:1];
- } else if (bodyLength <= 0xFFFF) {
- // 1 - The packet has a two-octet length. The header is 3 octets long.
- let bodyLengthBE = CFSwapInt16HostToBig((UInt16)bodyLength);
- [data appendBytes:&bodyLengthBE length:2];
- } else if (bodyLength <= 0xFFFFFFFF) {
- // 2 - The packet has a four-octet length. The header is 5 octets long.
- let bodyLengthBE = CFSwapInt64HostToBig(bodyLength);
- [data appendBytes:&bodyLengthBE length:4];
- } else {
- // 3 - The packet is of indeterminate length.
- // In general, an implementation SHOULD NOT use indeterminate-length packets except where the end of the data will be clear from the context
- NSAssert(NO, @"In general, an implementation SHOULD NOT use indeterminate-length packets");
- }
- return data;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
-
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyEncryptedSessionKeyPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyEncryptedSessionKeyPacket.m
deleted file mode 100755
index 5dd23dfbe6609d49240bb274a863ca8266a31e5b..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyEncryptedSessionKeyPacket.m
+++ /dev/null
@@ -1,250 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-// 5.1. Public-Key Encrypted Session Key Packets (Tag 1)
-
-#import "PGPPublicKeyEncryptedSessionKeyPacket.h"
-#import "NSData+PGPUtils.h"
-#import "PGPCryptoUtils.h"
-#import "PGPFingerprint.h"
-#import "PGPKeyID.h"
-#import "PGPMPI.h"
-#import "PGPPKCSEme.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPRSA.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPPublicKeyEncryptedSessionKeyPacket ()
-
-@property (nonatomic, copy) PGPMPI *encryptedMPI_M;
-
-@end
-
-@implementation PGPPublicKeyEncryptedSessionKeyPacket
-
-- (instancetype)init {
- if (self = [super init]) {
- _version = 3;
- _encryptedWithPassword = NO;
- _publicKeyAlgorithm = PGPPublicKeyAlgorithmRSA;
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPPublicKeyEncryptedSessionKeyPacketTag; // 1
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // - A one-octet number giving the version number of the packet type. The currently defined value for packet version is 3.
- [packetBody getBytes:&_version range:(NSRange){position, 1}];
- NSAssert(self.version == 3, @"The currently defined value for packet version is 3");
- position = position + 1;
-
- // - An eight-octet number that gives the Key ID of the public key
- self.keyID = [[PGPKeyID alloc] initWithLongKey:[packetBody subdataWithRange:(NSRange){position, 8}]];
- NSAssert(self.keyID, @"Missing KeyID");
- position = position + 8;
-
- // - A one-octet number giving the public-key algorithm used.
- [packetBody getBytes:&_publicKeyAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // - A string of octets that is the encrypted session key. This
- // string takes up the remainder of the packet, and its contents are
- // dependent on the public-key algorithm used.
- // RSA 1 MPI
- // Elgamal 2 MPI
-
- NSAssert(self.publicKeyAlgorithm == PGPPublicKeyAlgorithmRSA, @"Not supported.");
-
- let encryptedMPI_MData = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
- self.encryptedMPI_M = [[PGPMPI alloc] initWithMPIData:encryptedMPI_MData identifier:PGPMPI_M atPosition:0];
- position = position + encryptedMPI_MData.length;
-
- self.encryptedWithPassword = YES;
-
- return position;
-}
-
-// encryption update self.encryptedMPIPartData
-- (BOOL)encrypt:(PGPPublicKeyPacket *)publicKeyPacket sessionKeyData:(NSData *)sessionKeyData sessionKeyAlgorithm:(PGPSymmetricAlgorithm)sessionKeyAlgorithm error:(NSError * __autoreleasing _Nullable *)error {
- let mData = [NSMutableData data];
-
- // The value "m" in the above formulas is derived from the session key
- // as follows. First, the session key is prefixed with a one-octet
- // algorithm identifier that specifies the symmetric encryption
- // algorithm used to encrypt the following Symmetrically Encrypted Data
- // Packet. Then a two-octet checksum is appended, which is equal to the
- // sum of the preceding session key octets, not including the algorithm
- // identifier, modulo 65536. This value is then encoded as described in
- // PKCS#1 block encoding EME-PKCS1-v1_5 in Section 7.2.1 of [RFC3447] to
- // form the "m" value used in the formulas above. See Section 13.1 of
- // this document for notes on OpenPGP's use of PKCS#1.
-
- [mData appendBytes:&sessionKeyAlgorithm length:1];
-
- [mData appendData:sessionKeyData]; // keySize
-
- UInt16 checksum = [sessionKeyData pgp_Checksum];
- checksum = CFSwapInt16HostToBig(checksum);
- [mData appendBytes:&checksum length:2];
-
- let modulusMPI = [publicKeyPacket publicMPI:PGPMPI_N];
- if (!modulusMPI) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Cannot encrypt. Missing required MPI. Invalid key."}];
- }
- return NO;
- }
-
- unsigned int k = (unsigned int)modulusMPI.bigNum.bytesCount;
-
- let mEMEEncoded = [PGPPKCSEme encodeMessage:mData keyModulusLength:k error:error];
- let encryptedData = [publicKeyPacket encryptData:mEMEEncoded withPublicKeyAlgorithm:self.publicKeyAlgorithm];
- let mpiEncoded = [[PGPMPI alloc] initWithData:encryptedData identifier:PGPMPI_M];
- self.encryptedMPI_M = mpiEncoded;
- return YES;
-}
-
-- (nullable NSData *)decryptSessionKeyData:(PGPSecretKeyPacket *)secretKeyPacket sessionKeyAlgorithm:(PGPSymmetricAlgorithm *)sessionKeyAlgorithm error:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(!secretKeyPacket.isEncryptedWithPassphrase, @"Secret key can't be decrypted");
-
- let _Nullable secretKeyKeyID = [[PGPKeyID alloc] initWithFingerprint:secretKeyPacket.fingerprint];
- if (!secretKeyKeyID || !PGPEqualObjects(self.keyID, secretKeyKeyID)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: [NSString stringWithFormat:@"Invalid secret key used to decrypt session key, expected %@, got %@", self.keyID, secretKeyKeyID] }];
- }
- return nil;
- }
-
- // encrypted m value
- let encryptedM = [self.encryptedMPI_M bodyData];
-
- // decrypted m value
- let mEMEEncoded = [PGPCryptoUtils decrypt:encryptedM usingSecretKeyPacket:secretKeyPacket];
- let mData = [PGPPKCSEme decodeMessage:mEMEEncoded error:error];
- if (error && *error) {
- return nil;
- }
-
- NSUInteger position = 0;
- PGPSymmetricAlgorithm sessionKeyAlgorithmRead = PGPSymmetricPlaintext;
- [mData getBytes:&sessionKeyAlgorithmRead range:(NSRange){position, 1}];
- NSAssert(sessionKeyAlgorithmRead < PGPSymmetricMax, @"Invalid algorithm");
- if (sessionKeyAlgorithm) {
- *sessionKeyAlgorithm = sessionKeyAlgorithmRead;
- }
- position = position + 1;
-
- NSUInteger sessionKeySize = [PGPCryptoUtils keySizeOfSymmetricAlgorithm:sessionKeyAlgorithmRead];
- if (sessionKeySize == NSNotFound) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Invalid session key size" }];
- }
- return nil;
- }
- let sessionKeyData = [mData subdataWithRange:(NSRange){position, sessionKeySize}];
- position = position + sessionKeySize;
-
- UInt16 checksum = 0;
- [mData getBytes:&checksum range:(NSRange){position, 2}];
- checksum = CFSwapInt16BigToHost(checksum);
-
- // validate checksum
- UInt16 calculatedChecksum = [sessionKeyData pgp_Checksum];
- if (calculatedChecksum != checksum) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Invalid session key, checksum mismatch" }];
- }
- return nil;
- }
-
- return sessionKeyData;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- if (!self.encryptedMPI_M) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Cannot export session key packet"}];
- }
- return nil;
- }
-
- let bodyData = [NSMutableData data];
-
- [bodyData appendBytes:&_version length:1]; // 1
- [bodyData appendData:[self.keyID export:nil]]; // 8
- [bodyData appendBytes:&_publicKeyAlgorithm length:1]; // 1
- let exportedMPI = [self.encryptedMPI_M exportMPI];
- if (!exportedMPI) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Cannot export session key packet"}];
- }
- return nil;
- }
- [bodyData appendData:exportedMPI]; // m
-
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return bodyData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToSessionKeyPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToSessionKeyPacket:(PGPPublicKeyEncryptedSessionKeyPacket *)packet {
- return self.version == packet.version &&
- self.publicKeyAlgorithm == packet.publicKeyAlgorithm &&
- self.encryptedWithPassword == packet.encryptedWithPassword &&
- PGPEqualObjects(self.keyID, packet.keyID) &&
- PGPEqualObjects(self.encryptedMPI_M, packet.encryptedMPI_M);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.publicKeyAlgorithm;
- result = prime * result + self.keyID.hash;
- result = prime * result + self.encryptedWithPassword;
- result = prime * result + self.encryptedMPI_M.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([super copyWithZone:zone], PGPPublicKeyEncryptedSessionKeyPacket);
- PGPAssertClass(duplicate, PGPPublicKeyEncryptedSessionKeyPacket);
- duplicate.version = self.version;
- duplicate.publicKeyAlgorithm = self.publicKeyAlgorithm;
- duplicate.encryptedWithPassword = self.encryptedWithPassword;
- duplicate.keyID = self.keyID;
- duplicate.encryptedMPI_M = self.encryptedMPI_M;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyPacket.m
deleted file mode 100755
index c4bda286cb3a6c8a71a4f4ebabd5ce819e5e70cd..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPPublicKeyPacket.m
+++ /dev/null
@@ -1,310 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPPublicKeyPacket+Private.h"
-#import "PGPPacket+Private.h"
-#import "NSData+PGPUtils.h"
-#import "PGPMPI.h"
-#import "PGPRSA.h"
-#import "PGPTypes.h"
-#import "PGPFoundation.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPMacros+Private.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <CommonCrypto/CommonCryptor.h>
-#import <CommonCrypto/CommonDigest.h>
-
-#import <objc/runtime.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPPublicKeyPacket
-
-- (instancetype)init {
- if ((self = [super init])) {
- _version = 0x04;
- _createDate = NSDate.date;
- _publicMPIs = [NSArray<PGPMPI *> array];
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPPublicKeyPacketTag;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ %@", [super description], self.keyID];
-}
-
-- (nullable PGPMPI *)publicMPI:(NSString *)identifier {
- for (PGPMPI *mpi in self.publicMPIs) {
- if (PGPEqualObjects(mpi.identifier, identifier)) {
- return mpi;
- }
- }
-
- return nil;
-}
-
-#pragma mark - Properties
-
-- (NSUInteger)keySize {
- for (PGPMPI *mpi in self.publicMPIs) {
- if (PGPEqualObjects(mpi.identifier, PGPMPI_N)) {
- return (mpi.bigNum.bitsCount + 7) / 8; // ks
- }
- }
- return 0;
-}
-
-/**
- * 12.2. Key IDs and Fingerprints
- *
- * @return keyID
- */
-- (PGPKeyID *)keyID {
- return [[PGPKeyID alloc] initWithFingerprint:self.fingerprint];
-}
-
-/**
- * 12.2. Key IDs and Fingerprints
- * Calculate fingerprint
- *
- * @return Fingerprint data
- */
-- (PGPFingerprint *)fingerprint {
- return [[PGPFingerprint alloc] initWithData:[self exportKeyPacketOldStyle]];
-}
-
-#pragma mark - Parse data
-
-/**
- * 5.5.2. Public-Key Packet Formats
- *
- * @param packetBody Packet body
- */
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // A one-octet version number (2,3,4).
- [packetBody getBytes:&_version range:(NSRange){position, 1}];
- position = position + 1;
-
- NSAssert(self.version >= 3, @"To old packet version");
-
- // A four-octet number denoting the time that the key was created.
- UInt32 timestamp = 0;
- [packetBody getBytes:×tamp range:(NSRange){position, 4}];
- timestamp = CFSwapInt32BigToHost(timestamp);
- self.createDate = [NSDate dateWithTimeIntervalSince1970:timestamp];
- position = position + 4;
-
- // V3 keys are deprecated; an implementation MUST NOT generate a V3 key, but MAY accept it.
- if (self.version == 0x03) {
- // A two-octet number denoting the time in days that this key is
- // valid. If this number is zero, then it does not expire.
- [packetBody getBytes:&_V3validityPeriod range:(NSRange){position, 2}];
- _V3validityPeriod = CFSwapInt16BigToHost(_V3validityPeriod);
- position = position + 2;
- }
-
- // A one-octet number denoting the public-key algorithm of this key.
- [packetBody getBytes:&_publicKeyAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // A series of multiprecision integers comprising the key material.
- switch (self.publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // Algorithm-Specific Fields for RSA public keys:
- // MPI of RSA public modulus n;
- let mpiN = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_N atPosition:position];
- position = position + mpiN.packetLength;
-
- // MPI of RSA public encryption exponent e.
- let mpiE = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_E atPosition:position];
- position = position + mpiE.packetLength;
-
- self.publicMPIs = @[mpiN, mpiE];
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- // - MPI of DSA prime p;
- let mpiP = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_P atPosition:position];
- position = position + mpiP.packetLength;
-
- // - MPI of DSA group order q (q is a prime divisor of p-1);
- let mpiQ = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_Q atPosition:position];
- position = position + mpiQ.packetLength;
-
- // - MPI of DSA group generator g;
- let mpiG = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_G atPosition:position];
- position = position + mpiG.packetLength;
-
- // - MPI of DSA public-key value y (= g**x mod p where x is secret).
- let mpiY = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_Y atPosition:position];
- position = position + mpiY.packetLength;
-
- self.publicMPIs = @[mpiP, mpiQ, mpiG, mpiY];
- } break;
- case PGPPublicKeyAlgorithmElgamal:
- case PGPPublicKeyAlgorithmElgamalEncryptorSign: {
- // - MPI of Elgamal prime p;
- let mpiP = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_P atPosition:position];
- position = position + mpiP.packetLength;
-
- // - MPI of Elgamal group generator g;
- let mpiG = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_G atPosition:position];
- position = position + mpiG.packetLength;
-
- // - MPI of Elgamal public key value y (= g**x mod p where x is secret).
- let mpiY = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_Y atPosition:position];
- position = position + mpiY.packetLength;
-
- self.publicMPIs = @[mpiP, mpiG, mpiY];
- } break;
- default:
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Public key algorithm is not supported" }];
- }
- break;
- }
-
- return position;
-}
-
-/**
- * Build new style public key data
- *
- * @return public key data starting with version octet
- */
-- (NSData *)buildKeyBodyData:(BOOL)forceV4 {
- let data = [NSMutableData dataWithCapacity:128];
- [data appendBytes:&_version length:1];
-
- UInt32 timestamp = (UInt32)[self.createDate timeIntervalSince1970];
- UInt32 timestampBE = CFSwapInt32HostToBig(timestamp);
- [data appendBytes:×tampBE length:4];
-
- if (!forceV4 && self.version == 0x03) {
- // implementation MUST NOT generate a V3 key, but MAY accept it.
- // however it have to be generated here to calculate the very same fingerprint
- UInt16 V3ValidityPeriodBE = CFSwapInt16HostToBig(_V3validityPeriod);
- [data appendBytes:&V3ValidityPeriodBE length:2];
- }
-
- [data appendBytes:&_publicKeyAlgorithm length:1];
-
- // publicMPI is always available, no need to decrypt
- for (PGPMPI *mpi in self.publicMPIs) {
- let exportMPI = [mpi exportMPI];
- [data pgp_appendData:exportMPI];
- }
- return data;
-}
-
-// Old-style packet header for a key packet with two-octet length.
-// Old but used by fingerprint and with signing
-- (NSData *)exportKeyPacketOldStyle {
- let data = [NSMutableData data];
-
- let keyData = [self buildKeyBodyData:NO];
-
- NSUInteger length = keyData.length;
- UInt8 upper = (UInt8)(length >> 8);
- UInt8 lower = length & 0xff;
- UInt8 headWithLength[3] = {0x99, upper, lower};
- [data appendBytes:&headWithLength length:3];
- [data appendData:keyData];
- return data;
-}
-
-#pragma mark - PGPExportable
-
-/**
- * Packet data. Header with body data.
- *
- * @param error error
- *
- * @return data
- */
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return [self buildKeyBodyData:NO];
- }];
-}
-
-#pragma mark - Encrypt & Decrypt
-
-- (nullable NSData *)encryptData:(NSData *)data withPublicKeyAlgorithm:(PGPPublicKeyAlgorithm)publicKeyAlgorithm {
- switch (publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // return ecnrypted m
- return [PGPRSA publicEncrypt:data withPublicKeyPacket:self];
- } break;
- default:
- // TODO: add algorithms
- [NSException raise:@"PGPNotSupported" format:@"Algorith not supported"];
- break;
- }
- return nil;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToKeyPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToKeyPacket:(PGPPublicKeyPacket *)packet {
- return self.version == packet.version &&
- self.publicKeyAlgorithm == packet.publicKeyAlgorithm &&
- self.V3validityPeriod == packet.V3validityPeriod &&
- PGPEqualObjects(self.createDate, packet.createDate) &&
- PGPEqualObjects(self.publicMPIs, packet.publicMPIs);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.publicKeyAlgorithm;
- result = prime * result + self.V3validityPeriod;
- result = prime * result + self.createDate.hash;
- result = prime * result + self.publicMPIs.hash;
- return result;
-}
-
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPPublicKeyPacket);
- if (!duplicate) {
- return nil;
- }
- duplicate.version = self.version;
- duplicate.publicKeyAlgorithm = self.publicKeyAlgorithm;
- duplicate.V3validityPeriod = self.V3validityPeriod;
- duplicate.createDate = self.createDate;
- duplicate.publicMPIs = [[NSArray alloc] initWithArray:self.publicMPIs copyItems:YES];
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretKeyPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretKeyPacket.m
deleted file mode 100755
index ba603e47ed9d1fd26070a3c147dd6eb7f15c243c..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretKeyPacket.m
+++ /dev/null
@@ -1,429 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// A Secret-Key packet contains all the information that is found in a
-// Public-Key packet, including the public-key material, but also
-// includes the secret-key material after all the public-key fields.
-
-#import "PGPSecretKeyPacket.h"
-#import "PGPSecretKeyPacket+Private.h"
-#import "PGPPacket+Private.h"
-#import "PGPMPI.h"
-#import "PGPS2K.h"
-#import "PGPTypes.h"
-#import "NSMutableData+PGPUtils.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-#import "NSData+PGPUtils.h"
-#import "PGPCryptoCFB.h"
-#import "PGPCryptoUtils.h"
-#import "PGPRSA.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPSecretKeyPacket ()
-
-@property (nonatomic) BOOL wasDecrypted; // is decrypted
-
-@end
-
-@implementation PGPSecretKeyPacket
-
-- (PGPPacketTag)tag {
- return PGPSecretKeyPacketTag;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ isEncryptedWithPassphrase: %@", super.description, @(self.isEncryptedWithPassphrase)];
-}
-
-// Don't really know if key is passphrase protected.
-// Check the S2K settings and assume if the passphrase is set.
-- (BOOL)isEncryptedWithPassphrase {
- if (self.wasDecrypted) {
- return NO;
- }
-
- return (self.s2kUsage == PGPS2KUsageEncrypted || self.s2kUsage == PGPS2KUsageEncryptedAndHashed);
-}
-
-- (nullable PGPMPI *)secretMPI:(NSString *)identifier {
- for (PGPMPI *mpi in self.secretMPIs) {
- if (PGPEqualObjects(mpi.identifier, identifier)) {
- return mpi;
- }
- }
-
- return nil;
-}
-
-- (PGPFingerprint *)fingerprint {
- return [super fingerprint];
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(packetBody, NSData);
-
- NSUInteger position = [super parsePacketBody:packetBody error:error];
- // 5.5.3. Secret-Key Packet Formats
-
- NSAssert(self.version == 0x04 || self.version == 0x03, @"Only Secret Key version 3 and 4 is supported. Found version %@", @(self.version));
-
- // One octet indicating string-to-key usage conventions
- [packetBody getBytes:&_s2kUsage range:(NSRange){position, 1}];
- position = position + 1;
-
- if (self.s2kUsage == PGPS2KUsageEncrypted || self.s2kUsage == PGPS2KUsageEncryptedAndHashed) {
- // moved to parseEncryptedPart:error
- } else if (self.s2kUsage != PGPS2KUsageNonEncrypted) {
- // this is version 3, looks just like a V4 simple hash
- self.symmetricAlgorithm = (PGPSymmetricAlgorithm)self.s2kUsage; // this is tricky, but this is right. V3 algorithm is in place of s2kUsage of V4
- self.s2kUsage = PGPS2KUsageEncrypted;
-
- self.s2k = [[PGPS2K alloc] initWithSpecifier:PGPS2KSpecifierSimple hashAlgorithm:PGPHashMD5]; // not really parsed s2k, overwritten in parseEncryptedPart
- }
-
- let encryptedData = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
- NSUInteger length = 0;
- if (self.isEncryptedWithPassphrase && [self parseEncryptedPart:encryptedData length:&length error:error]) {
- position = position + length;
- } else if ([self parseUnencryptedPart:encryptedData length:&length error:error]) {
- position = position + length;
- }
-
- return position;
-}
-
-/**
- * Encrypted algorithm-specific fields for secret keys
- *
- * @param data Encrypted data
- * @param length Length of parsed data
- * @param error error
- *
- * @return YES on success.
- */
-- (BOOL)parseEncryptedPart:(NSData *)data length:(NSUInteger *)length error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = 0;
-
- if (self.s2kUsage == PGPS2KUsageEncrypted || self.s2kUsage == PGPS2KUsageEncryptedAndHashed) {
- // If string-to-key usage octet was 255 or 254, a one-octet symmetric encryption algorithm
- [data getBytes:&_symmetricAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // S2K
- NSUInteger s2kParsedLength = 0;
- self.s2k = [PGPS2K S2KFromData:data atPosition:position length:&s2kParsedLength];
- position = position + s2kParsedLength;
- }
-
- if (self.s2k.specifier == PGPS2KSpecifierGnuDummy) {
- self.ivData = NSData.data;
- } else if (self.s2k.specifier == PGPS2KSpecifierDivertToCard) {
- self.ivData = NSData.data;
- } else if (self.s2kUsage != PGPS2KUsageNonEncrypted) {
- // Initial Vector (IV) of the same length as the cipher's block size
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:self.symmetricAlgorithm];
- NSAssert(blockSize <= 16, @"invalid blockSize");
- self.ivData = [data subdataWithRange:(NSRange){position, blockSize}];
- position = position + blockSize;
- } else if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Cannot export packet. Unsupported S2K setup."}];
- *length = data.length;
- return NO;
- }
-
- // encrypted MPIArray
- // checksum or hash is encrypted together with the algorithm-specific fields (mpis) (if string-to-key usage octet is not zero).
- self.encryptedMPIPartData = [data subdataWithRange:(NSRange){position, data.length - position}];
- // position = position + self.encryptedMPIPartData.length;
-
- *length = data.length;
- return YES;
-}
-
-/**
- * Cleartext part, parse cleartext or unencrypted data
- * Store decrypted values in secretMPI array
- *
- * @param data packet data
- * @param error error
- *
- * @return length
- */
-- (BOOL)parseUnencryptedPart:(NSData *)data length:(nullable NSUInteger *)length error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = 0;
-
- // check hash before read actual data
- // hash is physically located at the end of dataBody
- switch (self.s2kUsage) {
- case PGPS2KUsageEncryptedAndHashed: {
- // a 20-octet SHA-1 hash of the plaintext of the algorithm-specific portion.
- NSUInteger hashSize = [PGPCryptoUtils hashSizeOfHashAlhorithm:PGPHashSHA1];
- if (hashSize == NSNotFound) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorPassphraseInvalid userInfo:@{ NSLocalizedDescriptionKey: @"Decrypted hash mismatch, invalid passphrase." }];
- }
- if (length) {
- *length = data.length;
- }
- return NO;
- }
-
- let clearTextData = [data subdataWithRange:(NSRange){0, data.length - hashSize}];
- let hashData = [data subdataWithRange:(NSRange){data.length - hashSize, hashSize}];
- let calculatedHashData = clearTextData.pgp_SHA1;
-
- if (!PGPEqualObjects(hashData,calculatedHashData)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorPassphraseInvalid userInfo:@{ NSLocalizedDescriptionKey: @"Decrypted hash mismatch, invalid passphrase." }];
- }
- if (length) {
- *length = data.length;
- }
- return NO;
- }
-
- } break;
- default: {
- // a two-octet checksum of the plaintext of the algorithm-specific portion
- NSUInteger checksumLength = 2;
- let clearTextData = [data subdataWithRange:(NSRange){0, data.length - checksumLength}];
- let checksumData = [data subdataWithRange:(NSRange){data.length - checksumLength, checksumLength}];
- NSUInteger calculatedChecksum = clearTextData.pgp_Checksum;
-
- UInt16 checksum = 0;
- [checksumData getBytes:&checksum length:checksumLength];
- checksum = CFSwapInt16BigToHost(checksum);
-
- if (checksum != calculatedChecksum) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Decrypted hash mismatch, check passphrase." }];
- }
-
- if (length) {
- *length = data.length;
- }
- return NO;
- }
- } break;
- }
-
- // now read the actual data
- switch (self.publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // multiprecision integer (MPI) of RSA secret exponent d.
- let mpiD = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_D atPosition:position];
- position = position + mpiD.packetLength;
-
- // MPI of RSA secret prime value p.
- let mpiP = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_P atPosition:position];
- position = position + mpiP.packetLength;
-
- // MPI of RSA secret prime value q (p < q).
- let mpiQ = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_Q atPosition:position];
- position = position + mpiQ.packetLength;
-
- // MPI of u, the multiplicative inverse of p, mod q.
- let mpiU = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_U atPosition:position];
- position = position + mpiU.packetLength;
-
- self.secretMPIs = @[mpiD, mpiP, mpiQ, mpiU];
- } break;
- case PGPPublicKeyAlgorithmDSA: {
- // MPI of DSA secret exponent x.
- let mpiX = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_X atPosition:position];
- position = position + mpiX.packetLength;
-
- self.secretMPIs = @[mpiX];
- } break;
- case PGPPublicKeyAlgorithmElgamal:
- case PGPPublicKeyAlgorithmElgamalEncryptorSign: {
- // MPI of Elgamal secret exponent x.
- let mpiX = [[PGPMPI alloc] initWithMPIData:data identifier:PGPMPI_X atPosition:position];
- position = position + mpiX.packetLength;
-
- self.secretMPIs = @[mpiX];
- } break;
- default:
- break;
- }
-
- if (length) {
- *length = data.length;
- }
- return YES;
-}
-
-#pragma mark - Decrypt
-
-/**
- * Decrypt parsed encrypted packet
- * Decrypt packet and store decrypted data on instance
- * TODO: V3 support - partially supported, need testing.
- * NOTE: Decrypted packet data should be released/forget after use
- */
-- (nullable PGPSecretKeyPacket *)decryptedWithPassphrase:(nullable NSString *)passphrase error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(passphrase, NSString);
-
- if (!self.isEncryptedWithPassphrase) {
- // PGPLogDebug(@"No need to decrypt key.");
- return self;
- }
-
- if (!self.ivData) {
- PGPLogError(@"IV is missing...");
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"IV is missing" } ]; };
- return nil;
- }
-
- PGPSecretKeyPacket *decryptedKeyPacket = self.copy;
- let encryptionSymmetricAlgorithm = decryptedKeyPacket.symmetricAlgorithm;
-
- // Session key for passphrase
- // producing a key to be used with a symmetric block cipher from a string of octets
- let sessionKeyData = [decryptedKeyPacket.s2k produceSessionKeyWithPassphrase:passphrase symmetricAlgorithm:encryptionSymmetricAlgorithm];
- if (!sessionKeyData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Can't build session key." } ];
- }
- return nil;
- }
-
- // Decrypted MPIArray
- let decryptedData = [PGPCryptoCFB decryptData:decryptedKeyPacket.encryptedMPIPartData sessionKeyData:sessionKeyData symmetricAlgorithm:encryptionSymmetricAlgorithm iv:decryptedKeyPacket.ivData syncCFB:NO];
-
- // now read mpis
- if (decryptedData) {
- [decryptedKeyPacket parseUnencryptedPart:decryptedData length:nil error:error];
- if (*error) {
- return nil;
- }
- }
-
- decryptedKeyPacket.wasDecrypted = YES;
- return decryptedKeyPacket;
-}
-
-#pragma mark - Private
-
-/**
- * Build public key data for fingerprint
- *
- * @return public key data starting with version octet
- */
-- (NSData *)buildSecretKeyDataAndForceV4:(BOOL)forceV4 {
- NSAssert(forceV4 == YES, @"Only V4 is supported");
-
- let data = [NSMutableData data];
- [data appendBytes:&self->_s2kUsage length:1];
-
- if (self.s2kUsage == PGPS2KUsageEncrypted || self.s2kUsage == PGPS2KUsageEncryptedAndHashed) {
- // If string-to-key usage octet was 255 or 254, a one-octet symmetric encryption algorithm
- [data appendBytes:&self->_symmetricAlgorithm length:1];
-
- // If string-to-key usage octet was 255 or 254, a string-to-key specifier.
- NSError *exportError = nil;
- let exportS2K = [self.s2k export:&exportError];
- [data pgp_appendData:exportS2K];
- NSAssert(!exportError, @"export failed");
- }
-
- if (self.s2kUsage != PGPS2KUsageNonEncrypted) {
- NSAssert(self.ivData, @"Require IV");
- // If secret data is encrypted (string-to-key usage octet not zero), an Initial Vector (IV) of the same length as the cipher's block size.
- // Initial Vector (IV) of the same length as the cipher's block size
- [data pgp_appendData:self.ivData];
- }
-
- if (self.s2kUsage == PGPS2KUsageNonEncrypted) {
- for (PGPMPI *mpi in self.secretMPIs) {
- let exportMPI = [mpi exportMPI];
- [data pgp_appendData:exportMPI];
- }
-
- // append hash
- UInt16 checksum = CFSwapInt16HostToBig(data.pgp_Checksum);
- [data appendBytes:&checksum length:2];
- } else if (self.encryptedMPIPartData) {
- // encrypted MPIArray with encrypted hash
- // hash is part of encryptedMPIPartData
- [data pgp_appendData:self.encryptedMPIPartData];
- } else {
- PGPLogWarning(@"Cannot build secret key data. Missing secret MPIs....");
- }
-
- return data;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- let secretKeyPacketData = [NSMutableData data];
- [secretKeyPacketData appendData:[self buildKeyBodyData:YES]];
- [secretKeyPacketData appendData:[self buildSecretKeyDataAndForceV4:YES]];
- return secretKeyPacketData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToKeyPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToKeyPacket:(PGPSecretKeyPacket *)packet {
- return self.version == packet.version &&
- self.s2kUsage == packet.s2kUsage &&
- self.publicKeyAlgorithm == packet.publicKeyAlgorithm &&
- self.V3validityPeriod == packet.V3validityPeriod &&
- PGPEqualObjects(self.createDate, packet.createDate) &&
- PGPEqualObjects(self.publicMPIs, packet.publicMPIs) &&
- PGPEqualObjects(self.secretMPIs, packet.secretMPIs);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.s2kUsage;
- result = prime * result + self.publicKeyAlgorithm;
- result = prime * result + self.V3validityPeriod;
- result = prime * result + self.createDate.hash;
- result = prime * result + self.publicMPIs.hash;
- result = prime * result + self.secretMPIs.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([super copyWithZone:zone], PGPSecretKeyPacket);
- duplicate.version = self.version;
- duplicate.s2kUsage = self.s2kUsage;
- duplicate.s2k = self.s2k;
- duplicate.symmetricAlgorithm = self.symmetricAlgorithm;
- duplicate.ivData = self.ivData;
- duplicate.secretMPIs = self.secretMPIs;
- duplicate.encryptedMPIPartData = self.encryptedMPIPartData;;
- duplicate.wasDecrypted = self.wasDecrypted;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretSubKeyPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretSubKeyPacket.m
deleted file mode 100755
index 3a6376931931b6863d0f49a2112deacac0c42166..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSecretSubKeyPacket.m
+++ /dev/null
@@ -1,23 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// A Secret-Subkey packet (tag 7) is the subkey analog of the Secret
-// Key packet and has exactly the same format.
-
-#import "PGPSecretSubKeyPacket.h"
-
-@implementation PGPSecretSubKeyPacket
-
-- (PGPPacketTag)tag {
- return PGPSecretSubkeyPacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- return [super parsePacketBody:packetBody error:error];
-}
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignaturePacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSignaturePacket.m
deleted file mode 100755
index b61ffcf09aff804850050404a8783b7d648afa55..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignaturePacket.m
+++ /dev/null
@@ -1,962 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSignaturePacket.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPKey.h"
-#import "PGPLiteralPacket.h"
-#import "PGPMPI.h"
-#import "PGPPKCSEmsa.h"
-#import "PGPPartialKey.h"
-#import "PGPRSA.h"
-#import "PGPDSA.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPSignatureSubpacket.h"
-#import "PGPSignatureSubpacket+Private.h"
-#import "PGPSignatureSubpacketHeader.h"
-#import "PGPUser.h"
-#import "PGPUserIDPacket.h"
-#import "PGPFoundation.h"
-#import "NSMutableData+PGPUtils.h"
-#import "NSArray+PGPUtils.h"
-#import "NSData+PGPUtils.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-#import <openssl/bn.h>
-#import <openssl/dsa.h>
-#import <openssl/err.h>
-#import <openssl/rsa.h>
-#import <openssl/ssl.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPSignaturePacket ()
-
-- (instancetype)init NS_DESIGNATED_INITIALIZER;
-
-@end
-
-@implementation PGPSignaturePacket
-
-- (instancetype)init {
- if (self = [super init]) {
- _version = 0x04;
- _type = PGPSignatureUnknown;
- _hashAlgoritm = PGPHashUnknown;
- _hashedSubpackets = [NSArray<PGPSignatureSubpacket *> array];
- _unhashedSubpackets = [NSArray<PGPSignatureSubpacket *> array];
- _signatureMPIs = [NSArray<PGPMPI *> array];
- }
- return self;
-}
-
-+ (PGPSignaturePacket *)signaturePacket:(PGPSignatureType)type hashAlgorithm:(PGPHashAlgorithm)hashAlgorithm {
- let signaturePacket = [[PGPSignaturePacket alloc] init];
- signaturePacket.type = type;
- signaturePacket.hashAlgoritm = hashAlgorithm;
- return signaturePacket;
-}
-
-- (PGPPacketTag)tag {
- return PGPSignaturePacketTag;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToSignaturePacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToSignaturePacket:(PGPSignaturePacket *)packet {
- return self.version == packet.version &&
- self.publicKeyAlgorithm == packet.publicKeyAlgorithm &&
- self.hashAlgoritm == packet.hashAlgoritm &&
- PGPEqualObjects(self.signedHashValueData, packet.signedHashValueData) &&
- PGPEqualObjects(self.signatureMPIs, packet.signatureMPIs) &&
- PGPEqualObjects(self.hashedSubpackets, packet.hashedSubpackets) &&
- PGPEqualObjects(self.unhashedSubpackets, packet.unhashedSubpackets);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.type;
- result = prime * result + self.publicKeyAlgorithm;
- result = prime * result + self.hashAlgoritm;
- result = prime * result + self.signedHashValueData.hash;
- result = prime * result + self.signatureMPIs.hash;
- result = prime * result + self.hashedSubpackets.hash;
- result = prime * result + self.unhashedSubpackets.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([super copyWithZone:zone], PGPSignaturePacket);
- PGPAssertClass(duplicate, PGPSignaturePacket)
- duplicate.version = self.version;
- duplicate.type = self.type;
- duplicate.publicKeyAlgorithm = self.publicKeyAlgorithm;
- duplicate.hashAlgoritm = self.hashAlgoritm;
- duplicate.signedHashValueData = self.signedHashValueData;
- duplicate.signatureMPIs = [[NSArray alloc] initWithArray:self.signatureMPIs copyItems:YES];
- duplicate.hashedSubpackets = [[NSArray alloc] initWithArray:self.hashedSubpackets copyItems:YES];
- duplicate.unhashedSubpackets = [[NSArray alloc] initWithArray:self.unhashedSubpackets copyItems:YES];
- return duplicate;
-}
-
-#pragma mark - Helper properties
-
-- (nullable PGPKeyID *)issuerKeyID {
- let subpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeIssuerKeyID] firstObject];
- return PGPCast(subpacket.value, PGPKeyID);
-}
-
-- (NSArray<PGPSignatureSubpacket *> *)subpackets {
- return [self.hashedSubpackets arrayByAddingObjectsFromArray:self.unhashedSubpackets ?: @[]];
-}
-
-- (NSArray<PGPSignatureSubpacket *> *)subpacketsOfType:(PGPSignatureSubpacketType)type {
- let filteredSubpackets = [NSMutableArray<PGPSignatureSubpacket *> array];
- for (PGPSignatureSubpacket *subPacket in self.subpackets) {
- if ((subPacket.type & 0x7F) == type) {
- [filteredSubpackets addObject:subPacket];
- }
- }
- return filteredSubpackets;
-}
-
-- (nullable NSDate *)expirationDate {
- PGPSignatureSubpacket *creationDateSubpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeSignatureCreationTime] firstObject];
- PGPSignatureSubpacket *validityPeriodSubpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeSignatureExpirationTime] firstObject];
- if (!validityPeriodSubpacket) {
- validityPeriodSubpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeKeyExpirationTime] firstObject];
- }
-
- let creationDate = PGPCast(creationDateSubpacket.value, NSDate);
- let validityPeriod = PGPCast(validityPeriodSubpacket.value, NSNumber);
- if (!validityPeriod || validityPeriod.unsignedIntegerValue == 0) {
- return nil;
- }
-
- return [creationDate dateByAddingTimeInterval:validityPeriod.unsignedIntegerValue];
-}
-
-- (BOOL)isExpired {
- // is no expiration date then signature never expires
- let expirationDate = self.expirationDate;
- if (!expirationDate) {
- return NO;
- }
-
- if ([expirationDate compare:NSDate.date] == NSOrderedAscending) {
- return YES;
- }
- return NO;
-}
-
-- (nullable NSDate *)creationDate {
- PGPSignatureSubpacket *creationDateSubpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeSignatureCreationTime] lastObject];
- return PGPCast(creationDateSubpacket.value, NSDate);
-}
-
-- (BOOL)isPrimaryUserID {
- PGPSignatureSubpacket *primaryUserIDSubpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypePrimaryUserID] firstObject];
- return [(NSNumber *)primaryUserIDSubpacket.value boolValue];
-}
-
-- (BOOL)canBeUsedToSign {
- BOOL result = self.publicKeyAlgorithm == PGPPublicKeyAlgorithmDSA || self.publicKeyAlgorithm == PGPPublicKeyAlgorithmRSA || self.publicKeyAlgorithm == PGPPublicKeyAlgorithmRSASignOnly;
-
- if (result) {
- PGPSignatureSubpacket *subpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeKeyFlags] firstObject];
- NSArray<NSNumber *> * _Nullable flags = PGPCast(subpacket.value, NSArray);
- if ([flags containsObject:@(PGPSignatureFlagAllowSignData)]) {
- return YES;
- }
- }
- return NO;
-}
-
-- (BOOL)canBeUsedToEncrypt {
- BOOL result = NO;
- PGPSignatureSubpacket *subpacket = [[self subpacketsOfType:PGPSignatureSubpacketTypeKeyFlags] firstObject];
- NSArray<NSNumber *> * _Nullable flags = PGPCast(subpacket.value, NSArray);
- if ([flags containsObject:@(PGPSignatureFlagAllowEncryptStorage)] || [flags containsObject:@(PGPSignatureFlagAllowEncryptCommunications)]) {
- result = YES;
- }
-
- // I'm not convinced if DSA is allowed here self.publicKeyAlgorithm != PGPPublicKeyAlgorithmDSA
- result = result && self.publicKeyAlgorithm != PGPPublicKeyAlgorithmRSASignOnly && self.publicKeyAlgorithm != PGPPublicKeyAlgorithmElgamalEncryptorSign;
-
- return result;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@, issuerKeyID: %@, canBeUsedToSign: %@, canBeUsedToEncrypt: %@", super.description, self.issuerKeyID, @(self.canBeUsedToSign), @(self.canBeUsedToEncrypt)];
-}
-
-- (nullable PGPMPI *)signatureMPI:(NSString *)identifier {
- for (PGPMPI *mpi in self.signatureMPIs) {
- if (PGPEqualObjects(mpi.identifier, identifier)) {
- return mpi;
- }
- }
-
- return nil;
-}
-
-#pragma mark - Build packet
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return [self buildFullSignatureBodyData];
- }];
-}
-
-- (NSData *)buildSignedPart:(NSArray *)hashedSubpackets {
- let data = [NSMutableData data];
-
- // One-octet version number (4).
- UInt8 exportVersion = 0x04;
- [data appendBytes:&exportVersion length:1];
-
- // One-octet signature type.
- [data appendBytes:&_type length:1];
-
- // One-octet public-key algorithm.
- [data appendBytes:&_publicKeyAlgorithm length:1];
-
- // One-octet hash algorithm.
- [data appendBytes:&_hashAlgoritm length:1];
-
- // hashed Subpackets
- [data appendData:[PGPSignaturePacket buildSubpacketsCollectionData:hashedSubpackets]];
-
- return data;
-}
-
-- (nullable NSData *)buildFullSignatureBodyData {
- let data = [NSMutableData data];
-
- // hashed Subpackets
- let signedPartData = [self buildSignedPart:self.hashedSubpackets];
- [data appendData:signedPartData];
-
- // unhashed Subpackets
- [data appendData:[PGPSignaturePacket buildSubpacketsCollectionData:self.unhashedSubpackets]];
-
- // signed hash value
- if (!self.signedHashValueData) {
- PGPLogError(@"Missing signed hash for the signature.");
- return nil;
- }
- [data pgp_appendData:self.signedHashValueData];
-
- // signed PGPMPI_M
- if (self.signatureMPIs.count == 0) {
- PGPLogError(@"Missing MPI for the signature.");
- return nil;
- }
-
- for (PGPMPI *mpi in self.signatureMPIs) {
- let exportMPI = [mpi exportMPI];
- [data pgp_appendData:exportMPI];
- }
-
- return data;
-}
-
-- (NSData *)calculateSignedHashForDataToSign:(NSData *)dataToSign {
- // The concatenation of the data being signed and the signature data
- // from the version number through the hashed subpacket data (inclusive)
- // is hashed.
- // toHash = toSignData + signedPartData + trailerData;
- let finalToHashData = [NSMutableData dataWithData:dataToSign];
-
- let signedPartData = [self buildSignedPart:self.hashedSubpackets];
- [finalToHashData appendData:signedPartData];
-
- let _Nullable trailerData = [self calculateTrailerFor:signedPartData];
- [finalToHashData appendData:trailerData];
-
- // Calculate hash value
- return [finalToHashData pgp_HashedWithAlgorithm:self.hashAlgoritm];
-}
-
-#pragma mark - Verify
-
-- (BOOL)verifyData:(NSData *)inputData publicKey:(PGPKey *)publicKey error:(NSError * __autoreleasing _Nullable *)error {
- return [self verifyData:inputData publicKey:publicKey signingKeyPacket:(PGPPublicKeyPacket *)[publicKey.publicKey signingKeyPacketWithKeyID:self.issuerKeyID] userID:nil error:error];
-}
-
-- (BOOL)verifyData:(NSData *)inputData publicKey:(PGPKey *)publicKey userID:(nullable NSString *)userID error:(NSError * __autoreleasing _Nullable *)error {
- return [self verifyData:inputData publicKey:publicKey signingKeyPacket:(PGPPublicKeyPacket *)[publicKey.publicKey signingKeyPacketWithKeyID:self.issuerKeyID] userID:userID error:error];
-}
-
-// Opposite to sign, with readed data (not produced)
-- (BOOL)verifyData:(NSData *)inputData publicKey:(PGPKey *)publicKey signingKeyPacket:(PGPPublicKeyPacket *)signingKeyPacket userID:(nullable NSString *)userID error:(NSError * __autoreleasing _Nullable *)error {
- // no signing packet was found, this we have no valid signature
- PGPAssertClass(signingKeyPacket, PGPPublicKeyPacket);
-
- if (self.type == PGPSignatureBinaryDocument && inputData.length == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Invalid signature packet type" }];
- }
- return NO;
- }
-
- // 5.2.4. Computing Signatures
-
- // build toSignData, toSign
- let toSignData = [self buildDataToSignForType:self.type inputData:inputData key:publicKey subKey:nil keyPacket:signingKeyPacket userID:userID error:error];
- if (!toSignData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Invalid signature." }];
- }
- return NO;
- }
-
- /// Calculate hash to compare
- // signedPartData
- let signedPartData = [self buildSignedPart:self.hashedSubpackets];
- // calculate trailer
- let trailerData = [self calculateTrailerFor:signedPartData];
-
- // toHash = toSignData + signedPartData + trailerData;
- let toHashData = [NSMutableData dataWithData:toSignData];
- [toHashData appendData:signedPartData];
- [toHashData appendData:trailerData];
-
- // TODO: Investigate how to handle V3 scenario here
- // check signed hash value, should match
- if (self.version == 0x04) {
- // Calculate hash value
- let calculatedHashValueData = [[toHashData pgp_HashedWithAlgorithm:self.hashAlgoritm] subdataWithRange:(NSRange){0, 2}];
-
- if (!PGPEqualObjects(self.signedHashValueData, calculatedHashValueData)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"Verification failed. Signature hash validation failed." }];
- }
- return NO;
- }
- }
-
- switch (signingKeyPacket.publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSASignOnly:
- case PGPPublicKeyAlgorithmRSAEncryptOnly: {
- // convert mpi data to binary signature_bn_bin
- let signatureMPI = self.signatureMPIs[0];
-
- // encoded m value
- let _Nullable encryptedEmData = [signatureMPI bodyData];
- // decrypted encoded m value
- let _Nullable decryptedEmData = [PGPRSA publicDecrypt:encryptedEmData withPublicKeyPacket:signingKeyPacket];
-
- // calculate EM and compare with decrypted EM. PKCS-emsa Encoded M.
- let emData = [PGPPKCSEmsa encode:self.hashAlgoritm message:toHashData encodedMessageLength:signingKeyPacket.keySize error:error];
- if (!PGPEqualObjects(emData, decryptedEmData)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidSignature userInfo:@{ NSLocalizedDescriptionKey: @"em hash dont match" }];
- }
- return NO;
- }
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- return [PGPDSA verify:toHashData signature:self withPublicKeyPacket:signingKeyPacket];
- } break;
- default:
- [NSException raise:@"PGPNotSupported" format:@"Algorith not supported"];
- break;
- }
-
- return YES;
-}
-
-#pragma mark - Sign
-
-// 5.2.4. Computing Signatures
-// http://tools.ietf.org/html/rfc4880#section-5.2.4
-// @see https://github.com/singpolyma/openpgp-spec/blob/master/key-signatures
-
-/// Sign the signature with the given key.
-/// Set signatureMPIArray and updates signed hash.
-///
-/// Update sign related values. This method mutate the signature.
-- (BOOL)signData:(nullable NSData *)inputData withKey:(PGPKey *)key subKey:(nullable PGPKey *)subKey passphrase:(nullable NSString *)passphrase userID:(nullable NSString *)userID error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(key, PGPKey);
-
- if (!key.secretKey) {
- PGPLogDebug(@"Missing secret key.");
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing secret key" }];
- }
- return NO;
- }
-
- PGPAssertClass(key.secretKey.primaryKeyPacket, PGPSecretKeyPacket); // Signing key packet not found
-
- var signingKeyPacket = key.signingSecretKey;
- if (!signingKeyPacket) {
- // As of PGP Desktop. The signing signature may be missing.
- PGPLogDebug(@"Missing signature for the secret key %@", key.secretKey.keyID);
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorMissingSignature userInfo:@{ NSLocalizedDescriptionKey: @"Missing signature for the secret key." }];
- }
- return NO;
- }
-
- // TODO: check it this is right ? setup public key algorithm from secret key packet
- self.publicKeyAlgorithm = signingKeyPacket.publicKeyAlgorithm;
-
- if (signingKeyPacket.isEncryptedWithPassphrase && passphrase && passphrase.length > 0) {
- NSError *decryptError;
- // Copy secret key instance, then decrypt on copy, not on the original (do not leave unencrypted instance around)
- signingKeyPacket = [signingKeyPacket decryptedWithPassphrase:PGPNN(passphrase) error:&decryptError];
-
- // When error can be passed back to caller, we want to avoid assertion, since there is no way to
- // know if packet can be decrypted and it is a typical user error to provide the wrong passhrase.
- if(signingKeyPacket == nil && error != nil) {
- *error = decryptError;
- return NO;
- }
-
- NSAssert(signingKeyPacket && !decryptError, @"decrypt error %@", decryptError);
- }
-
- // signed part data
- if (self.hashedSubpackets.count == 0) {
- // add hashed subpacket - REQUIRED
- let creationTimeSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeSignatureCreationTime andValue:NSDate.date];
- self.hashedSubpackets = @[creationTimeSubpacket];
- PGPLogDebug(@"Signature without subpackets. Adding minimal set of subpackets.");
- }
-
- let signedPartData = [self buildSignedPart:self.hashedSubpackets];
- // calculate trailer
- let _Nullable trailerData = [self calculateTrailerFor:signedPartData];
-
- // build toSignData, toSign
- let _Nullable toSignData = [self buildDataToSignForType:self.type inputData:inputData key:key subKey:subKey keyPacket:signingKeyPacket userID:userID error:error];
- if (!toSignData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Can't sign" }];
- }
- return NO;
- }
- // toHash = toSignData + signedPartData + trailerData;
- let toHashData = [NSMutableData dataWithData:toSignData];
- [toHashData appendData:signedPartData];
- [toHashData appendData:trailerData];
-
- // == Computing Signatures ==
- // Encrypt hash data Packet signature MPIArray
- switch (self.publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // Encrypted m value (PKCS emsa encrypted)
- NSData *em = [PGPPKCSEmsa encode:self.hashAlgoritm message:toHashData encodedMessageLength:signingKeyPacket.keySize error:nil];
- NSData *encryptedEmData = nil;
- encryptedEmData = [PGPRSA privateEncrypt:em withSecretKeyPacket:signingKeyPacket];
- if (!encryptedEmData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Sign Encryption failed" }];
- }
- return NO;
- }
-
- // store signature data as MPI
- self.signatureMPIs = @[[[PGPMPI alloc] initWithData:encryptedEmData identifier:PGPMPI_M]];
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- self.signatureMPIs = [PGPDSA sign:toHashData key:key];
- } break;
- default:
- [NSException raise:@"PGPNotSupported" format:@"Algorith not supported"];
- break;
- }
-
- if (self.unhashedSubpackets.count == 0) {
- // add unhashed PGPSignatureSubpacketTypeIssuer subpacket - REQUIRED
- let keyid = [[PGPKeyID alloc] initWithFingerprint:signingKeyPacket.fingerprint];
- PGPSignatureSubpacket *issuerSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:keyid];
- self.unhashedSubpackets = @[issuerSubpacket];
- PGPLogDebug(@"Signature without subpackets. Adding minimal set of subpackets.");
- }
-
- // Checksum
- // Two-octet field holding the left 16 bits of the signed hash value.
- // Calculate hash value
- let hashValueData = [[self calculateSignedHashForDataToSign:toSignData] subdataWithRange:(NSRange){0, 2}];
- self.signedHashValueData = hashValueData;
- return YES;
-}
-
-- (nullable NSData *)buildDataToSignForType:(PGPSignatureType)type inputData:(nullable NSData *)inputData key:(nullable PGPKey *)key subKey:(nullable PGPKey *)subKey keyPacket:(nullable PGPPublicKeyPacket *)signingKeyPacket userID:(nullable NSString *)userID error:(NSError * __autoreleasing _Nullable *)error {
- let toSignData = [NSMutableData data];
- switch (type) {
- case PGPSignatureBinaryDocument:
- case PGPSignatureCanonicalTextDocument: {
- if (!inputData) {
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Missing input data" }]; }
- return nil;
- }
- [toSignData pgp_appendData:inputData];
- } break;
- case PGPSignatureSubkeyBinding: { // 0x18
- // the subkey using the same format as the main key (also using 0x99 as the first octet).
- if (!signingKeyPacket || !subKey) {
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing valid key packet." }]; }
- return nil;
- }
-
- let signingKeyData = [signingKeyPacket exportKeyPacketOldStyle];
- [toSignData appendData:signingKeyData];
-
- let _Nullable signingSubKeyData = [PGPCast(subKey.publicKey.primaryKeyPacket, PGPPublicKeyPacket) exportKeyPacketOldStyle];
- PGPAssertClass(signingSubKeyData, NSData);
- [toSignData pgp_appendData:signingSubKeyData];
- } break;
- case PGPSignaturePrimaryKeyBinding: { // 0x19
- // A primary key binding signature (type 0x19) then hashes
- if (!signingKeyPacket) {
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing key packet." }]; }
- return nil;
- }
-
- let signingKeyData = [signingKeyPacket exportKeyPacketOldStyle];
- [toSignData appendData:signingKeyData];
- } break;
- case PGPSignatureGenericCertificationUserIDandPublicKey: // 0x10
- case PGPSignaturePersonalCertificationUserIDandPublicKey: // 0x11
- case PGPSignatureCasualCertificationUserIDandPublicKey: // 0x12
- case PGPSignaturePositiveCertificationUserIDandPublicKey: // 0x13
- case PGPSignatureCertificationRevocation: // 0x28
- {
- if (!signingKeyPacket) {
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing key packet." }]; }
- return nil;
- }
- // A certification signature (type 0x10 through 0x13)
-
- // When a signature is made over a key, the hash data starts with the
- // octet 0x99, followed by a two-octet length of the key, and then body
- // of the key packet. (Note that this is an old-style packet header for
- // a key packet with two-octet length.)
-
- let signingKeyData = [signingKeyPacket exportKeyPacketOldStyle];
- [toSignData appendData:signingKeyData];
-
- if (key.secretKey) {
- let secretPartialKey = key.secretKey;
- NSAssert(secretPartialKey.users.count > 0, @"Need at least one user for the key.");
-
- BOOL userIsValid = NO;
- for (PGPUser *user in secretPartialKey.users) {
- if (PGPEqualObjects(user.userID, userID)) {
- userIsValid = YES;
- }
- }
-
- if (!userIsValid) {
- PGPLogDebug(@"Invalid user id");
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Invalid user id" }]; }
- return nil;
- }
- }
-
- if (userID.length > 0) {
- let _Nullable userIDData = [userID dataUsingEncoding:NSUTF8StringEncoding];
- if (!userIDData) {
- if (error) { *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Invalid user id" }]; }
- return nil;
- }
-
- if (self.version == 0x04) {
- // constant tag (1)
- UInt8 userIDConstant = 0xB4;
- [toSignData appendBytes:&userIDConstant length:1];
-
- // length (4)
- UInt32 userIDLength = (UInt32)userIDData.length;
- userIDLength = CFSwapInt32HostToBig(userIDLength);
- [toSignData appendBytes:&userIDLength length:4];
- }
- // data
- [toSignData pgp_appendData:userIDData];
- }
- // TODO user attributes alternative
- // UInt8 userAttributeConstant = 0xD1;
- //[data appendBytes:&userAttributeConstant length:sizeof(userAttributeConstant)];
-
- } break;
- default:
- [toSignData pgp_appendData:inputData];
- break;
- }
- return toSignData;
-}
-
-- (nullable NSData *)calculateTrailerFor:(NSData *)signedPartData {
- if (self.version != 0x04) {
- PGPLogError(@"Unsupported signature version: %@, expected version 4", @(self.version));
- return nil;
- }
-
- let trailerData = [NSMutableData data];
- UInt8 prefix[2] = {self.version, 0xFF};
- [trailerData appendBytes:&prefix length:2];
-
- UInt32 signatureLength = (UInt32)signedPartData.length; // + 6; // ??? (note that this number does not include these final six octets)
- signatureLength = CFSwapInt32HostToBig(signatureLength);
- [trailerData appendBytes:&signatureLength length:4];
-
- return trailerData;
-}
-
-#pragma mark - Parse
-
-/**
- * 5.2. Signature Packet (Tag 2)
- *
- * @param packetBody Packet body
- */
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- __unused NSUInteger position = [super parsePacketBody:packetBody error:error];
- NSUInteger startPosition = position;
-
- UInt8 parsedVersion = 0;
- // One-octet version number.
- [packetBody getBytes:&parsedVersion range:(NSRange){position, 1}];
- position = position + 1;
-
- switch (parsedVersion) {
- case 0x04:
- position = [self parseV4PacketBody:packetBody error:error];
- break;
- case 0x03:
- position = [self parseV3PacketBody:packetBody error:error];
- break;
- default:
- NSAssert(true, @"Unsupported signature packet version");
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: [NSString stringWithFormat:@"Signature version %@ is supported at the moment", @(parsedVersion)] }];
- }
- return startPosition + packetBody.length;
- break;
- }
- return position;
-}
-
-// FIXME: V3 signatures fail somewehere (I don't know where yet) because everything is designed
-// for V4 and uses V4 specific data to (for example) validate signature
-- (NSUInteger)parseV3PacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(packetBody, NSData);
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // V3
- // One-octet version number (3).
- UInt8 parsedVersion = 0;
- [packetBody getBytes:&parsedVersion range:(NSRange){position, 1}];
- position = position + 1;
-
- if (parsedVersion != 0x03) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unexpected packed version. Expected version 3" }];
- }
- return position;
- }
-
- // One-octet length of following hashed material. MUST be 5.
- UInt8 parsedLength = 0;
- [packetBody getBytes:&parsedLength range:(NSRange){position, 1}];
- position = position + 1;
- NSAssert(parsedLength == 5, @"Invalid signature data");
-
- // One-octet signature type.
- [packetBody getBytes:&_type range:(NSRange){position, 1}];
- position = position + 1;
-
- // Four-octet creation time
- UInt32 parsedCreationTimestamp = 0;
- [packetBody getBytes:&parsedCreationTimestamp range:(NSRange){position, 4}];
- parsedCreationTimestamp = CFSwapInt32BigToHost(parsedCreationTimestamp);
- position = position + 4;
-
- // Eight-octet Key ID of signer
- PGPKeyID *parsedkeyID = [[PGPKeyID alloc] initWithLongKey:[packetBody subdataWithRange:(NSRange){position, 8}]];
- position = position + 8;
-
- // One-octet public-key algorithm.
- [packetBody getBytes:&_publicKeyAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // One-octet hash algorithm.
- [packetBody getBytes:&_hashAlgoritm range:(NSRange){position, 1}];
- position = position + 1;
-
- // Two-octet field holding the left 16 bits of the signed hash value.
- self.signedHashValueData = [packetBody subdataWithRange:(NSRange){position, 2}];
- position = position + 2;
-
- // 5.2.2. One or more multiprecision integers comprising the signature. This portion is algorithm specific
- // Signature
- switch (_publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // multiprecision integer (MPI) of RSA signature value m**d mod n.
- // MPI of RSA public modulus n;
- PGPMPI *mpiN = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_N atPosition:position];
- position = position + mpiN.packetLength;
-
- self.signatureMPIs = @[mpiN];
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- // MPI of DSA value r.
- PGPMPI *mpiR = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_R atPosition:position];
- position = position + mpiR.packetLength;
-
- // MPI of DSA value s.
- PGPMPI *mpiS = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_S atPosition:position];
- position = position + mpiS.packetLength;
-
- self.signatureMPIs = @[mpiR, mpiS];
- } break;
- case PGPPublicKeyAlgorithmElgamal: {
- // MPI of Elgamal (Diffie-Hellman) value g**k mod p.
- PGPMPI *mpiG = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_G atPosition:position];
- position = position + mpiG.packetLength;
-
- // MPI of Elgamal (Diffie-Hellman) value m * y**k mod p.
- PGPMPI *mpiY = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_Y atPosition:position];
- position = position + mpiY.packetLength;
-
- self.signatureMPIs = @[mpiG, mpiY];
- } break;
- default:
- break;
- }
-
- // convert V3 values to V4 subpackets
- let keyIDSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeIssuerKeyID andValue:parsedkeyID];
- self.unhashedSubpackets = [self.unhashedSubpackets arrayByAddingObject:keyIDSubpacket];
-
- let creationDateTime = [NSDate dateWithTimeIntervalSince1970:parsedCreationTimestamp];
- let creationTimeSubpacket = [[PGPSignatureSubpacket alloc] initWithType:PGPSignatureSubpacketTypeSignatureCreationTime andValue:creationDateTime];
- self.hashedSubpackets = [self.hashedSubpackets arrayByAddingObject:creationTimeSubpacket];
-
- return position;
-}
-
-- (NSUInteger)parseV4PacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- PGPAssertClass(packetBody, NSData);
-
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // A V4 signature hashes the packet body
- // starting from its first field, the version number, through the end
- // of the hashed subpacket data. Thus, the fields hashed are the
- // signature version, the signature type, the public-key algorithm, the
- // hash algorithm, the hashed subpacket length, and the hashed
- // subpacket body.
-
- UInt8 parsedVersion = 0;
- // V4
- // One-octet version number (4).
- [packetBody getBytes:&parsedVersion range:(NSRange){position, 1}];
- position = position + 1;
-
- if (parsedVersion != 0x04) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorInvalidMessage userInfo:@{ NSLocalizedDescriptionKey: @"Unexpected packed version. Expected version 4" }];
- }
- return position;
- }
-
- // One-octet signature type.
- [packetBody getBytes:&_type range:(NSRange){position, 1}];
- position = position + 1;
-
- // One-octet public-key algorithm.
- [packetBody getBytes:&_publicKeyAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // One-octet hash algorithm.
- [packetBody getBytes:&_hashAlgoritm range:(NSRange){position, 1}];
- position = position + 1;
-
- // Two-octet scalar octet count for following hashed subpacket data.
- UInt16 hashedOctetCount = 0;
- [packetBody getBytes:&hashedOctetCount range:(NSRange){position, 2}];
- hashedOctetCount = CFSwapInt16BigToHost(hashedOctetCount);
- position = position + 2;
-
- // Hashed subpacket data set (zero or more subpackets)
- NSData *hashedSubpacketsData = nil;
- if (hashedOctetCount > 0) {
- hashedSubpacketsData = [packetBody subdataWithRange:(NSRange){position, hashedOctetCount}];
- position = position + hashedOctetCount;
-
- NSMutableArray *hashedSubpackets = [NSMutableArray arrayWithCapacity:hashedOctetCount];
-
- NSUInteger positionSubpacket = 0;
- while (positionSubpacket < hashedSubpacketsData.length) {
- let _Nullable subpacket = [PGPSignaturePacket getSubpacketStartingAtPosition:positionSubpacket fromData:hashedSubpacketsData];
- if (subpacket) {
- [hashedSubpackets pgp_addObject:subpacket];
- positionSubpacket = positionSubpacket + subpacket.length;
- } else {
- positionSubpacket += 2; // move two bytes to next subpacket (header length)
- }
- }
-
- self.hashedSubpackets = hashedSubpackets;
- }
-
- // Two-octet scalar octet count for the following unhashed subpacket
- UInt16 unhashedOctetCount = 0;
- [packetBody getBytes:&unhashedOctetCount range:(NSRange){position, 2}];
- unhashedOctetCount = CFSwapInt16BigToHost(unhashedOctetCount);
- position = position + 2;
-
- // Unhashed subpacket data set (zero or more subpackets)
- NSData *unhashedSubpacketsData = nil;
- if (unhashedOctetCount > 0) {
- unhashedSubpacketsData = [packetBody subdataWithRange:(NSRange){position, unhashedOctetCount}];
- position = position + unhashedOctetCount;
-
- NSMutableArray *unhashedSubpackets = [NSMutableArray arrayWithCapacity:unhashedOctetCount];
-
- // Loop subpackets
- NSUInteger positionSubpacket = 0;
- while (positionSubpacket < unhashedSubpacketsData.length) {
- let _Nullable subpacket = [PGPSignaturePacket getSubpacketStartingAtPosition:positionSubpacket fromData:unhashedSubpacketsData];
- if (subpacket) {
- [unhashedSubpackets pgp_addObject:subpacket];
- positionSubpacket = positionSubpacket + subpacket.length;
- } else {
- positionSubpacket += 2; // move two bytes to next subpacket (header length)
- }
- }
-
- self.unhashedSubpackets = unhashedSubpackets;
- }
-
- // Two-octet field holding the left 16 bits of the signed hash value.
- self.signedHashValueData = [packetBody subdataWithRange:(NSRange){position, 2}];
-
- position = position + 2;
-
- // 5.2.2. One or more multiprecision integers comprising the signature. This portion is algorithm specific
- // Signature
- switch (_publicKeyAlgorithm) {
- case PGPPublicKeyAlgorithmRSA:
- case PGPPublicKeyAlgorithmRSAEncryptOnly:
- case PGPPublicKeyAlgorithmRSASignOnly: {
- // multiprecision integer (MPI) of RSA signature value m**d mod n.
- // MPI of RSA public modulus n;
- PGPMPI *mpiN = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_N atPosition:position];
- position = position + mpiN.packetLength;
-
- self.signatureMPIs = @[mpiN];
- } break;
- case PGPPublicKeyAlgorithmDSA:
- case PGPPublicKeyAlgorithmECDSA: {
- // MPI of DSA value r.
- PGPMPI *mpiR = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_R atPosition:position];
- position = position + mpiR.packetLength;
-
- // MPI of DSA value s.
- PGPMPI *mpiS = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_S atPosition:position];
- position = position + mpiS.packetLength;
-
- self.signatureMPIs = @[mpiR, mpiS];
- } break;
- case PGPPublicKeyAlgorithmElgamal: {
- // MPI of Elgamal (Diffie-Hellman) value g**k mod p.
- PGPMPI *mpiG = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_G atPosition:position];
- position = position + mpiG.packetLength;
-
- // MPI of Elgamal (Diffie-Hellman) value m * y**k mod p.
- PGPMPI *mpiY = [[PGPMPI alloc] initWithMPIData:packetBody identifier:PGPMPI_Y atPosition:position];
- position = position + mpiY.packetLength;
-
- self.signatureMPIs = @[mpiG, mpiY];
- } break;
- default:
- break;
- }
-
- return position;
-}
-
-#pragma mark - Private
-
-// I don't like this part, really ugly
-// This is because subpacket length is unknow and header need to be found first
-// then subpacket can be parsed
-+ (nullable PGPSignatureSubpacket *)getSubpacketStartingAtPosition:(NSUInteger)subpacketsPosition fromData:(NSData *)subpacketsData {
- let headerRange = (NSRange){subpacketsPosition, MIN((NSUInteger)6, subpacketsData.length - subpacketsPosition)}; // up to 5+1 octets
- let guessHeaderData = [subpacketsData subdataWithRange:headerRange]; // this is "may be" header to be parsed
- let subpacketHeader = [PGPSignatureSubpacket subpacketHeaderFromData:guessHeaderData];
-
- if (subpacketHeader.bodyLength == 0) {
- // missing body, ignore.
- return nil;
- }
-
- let subPacketBodyRange = (NSRange){subpacketsPosition + subpacketHeader.headerLength, subpacketHeader.bodyLength};
- let subPacketBody = [subpacketsData subdataWithRange:subPacketBodyRange];
- let subpacket = [[PGPSignatureSubpacket alloc] initWithHeader:subpacketHeader body:subPacketBody];
-
- return subpacket;
-}
-
-/// count + subpackets(count)
-+ (NSData *)buildSubpacketsCollectionData:(NSArray <PGPSignatureSubpacket *> *)subpacketsCollection {
- let data = [NSMutableData data];
- if (subpacketsCollection.count == 0) {
- // 0x00 0x00
- UInt16 zeroZero = 0;
- [data appendBytes:&zeroZero length:2];
- return data;
- }
-
- let subpackets = [NSMutableData data];
- // Hashed subpacket data set (zero or more subpackets)
- for (PGPSignatureSubpacket *subpacket in subpacketsCollection) {
- NSError *error = nil;
- let subpacketData = [subpacket export:&error];
- [subpackets pgp_appendData:subpacketData];
- }
- // Two-octet scalar octet count for following hashed subpacket data.
- UInt16 countBE = CFSwapInt16HostToBig((UInt16)subpackets.length);
- [data appendBytes:&countBE length:2];
- // subackets data
- [data appendData:subpackets];
- return data;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacket.m
deleted file mode 100755
index 7113a0c33f4870cad927a1bb7a079a1f7a166511..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacket.m
+++ /dev/null
@@ -1,452 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSignatureSubpacket.h"
-#import "PGPSignatureSubpacket+Private.h"
-#import "PGPSignatureSubpacketCreationTime.h"
-#import "PGPSignatureSubpacketEmbeddedSignature.h"
-#import "PGPSignatureSubpacketHeader.h"
-#import "PGPCompressedPacket.h"
-#import "PGPPacketHeader.h"
-#import "PGPSignaturePacket.h"
-#import "PGPKeyID.h"
-#import "PGPPacket.h"
-#import "PGPPacket+Private.h"
-#import "PGPFoundation.h"
-#import "NSMutableData+PGPUtils.h"
-
-#import "PGPLogging.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPSignatureSubpacket ()
-
-@property (nonatomic, readwrite) NSUInteger length;
-@end
-
-@implementation PGPSignatureSubpacket
-
-- (instancetype)initWithType:(PGPSignatureSubpacketType)type andValue:(nullable id<NSObject, NSCopying>)value {
- if ((self = [super init])) {
- _type = type;
- _value = [value copyWithZone:nil];
- }
- return self;
-}
-
-- (nullable instancetype)initWithHeader:(PGPSignatureSubpacketHeader *)header body:(NSData *)subPacketBodyData {
- if (self = [self initWithType:header.type andValue:nil]) {
- _length = header.headerLength + header.bodyLength;
- [self parseSubpacketBody:subPacketBodyData];
- }
- return self;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ type: %@ value: %@", [super description], @(self.type), self.value ?: @"nil"];
-}
-
-// Bit 7 of the subpacket type is the "critical" bit.
-- (BOOL)isCritical {
- return (1 << 7) & self.type;
-}
-
-/**
- * 5.2.3.1. Signature Subpacket Specification
- *
- * @param packetBodyData A single subpacket body data.
- */
-- (void)parseSubpacketBody:(NSData *)packetBodyData {
- switch (self.type & 0x7F) {
- case PGPSignatureSubpacketTypeSignatureCreationTime: // NSDate
- {
- // 5.2.3.4. Signature Creation Ti��me
- // Signature Creation Time MUST be present in the hashed area.
- self.value = [PGPSignatureSubpacketCreationTime packetWithData:packetBodyData].value;
- } break;
- case PGPSignatureSubpacketTypeEmbeddedSignature: {
- // 5.2.3.26. Embedded Signature
- // TODO: such a mess with subpackets. Needs refactor: specific subpacket inherit from the PGPSignatureSubpacket and implements import/export
- self.value = [PGPSignatureSubpacketEmbeddedSignature packetWithData:packetBodyData];
- } break;
- case PGPSignatureSubpacketTypeSignatureExpirationTime: // NSNumber
- case PGPSignatureSubpacketTypeKeyExpirationTime: {
- // 5.2.3.10. Signature Expiration Time
- // 5.2.3.6. Key Expiration Time
- // The validity period of the signature
- UInt32 validityPeriodTime = 0;
- [packetBodyData getBytes:&validityPeriodTime length:4];
- validityPeriodTime = CFSwapInt32BigToHost(validityPeriodTime);
- self.value = @(validityPeriodTime);
- } break;
- case PGPSignatureSubpacketTypeTrustSignature: {
- // (1 octet "level" (depth), 1 octet of trust amount)
- // TODO trust subpacket
- } break;
- case PGPSignatureSubpacketTypeIssuerKeyID: // PGPKeyID
- {
- // 5.2.3.5. Issuer
-
- let keyID = [[PGPKeyID alloc] initWithLongKey:packetBodyData];
- self.value = keyID; //[packetBody subdataWithRange:(NSRange){0,8}];
- } break;
- case PGPSignatureSubpacketTypeExportableCertification: // NSNumber BOOL
- {
- // 5.2.3.11. Exportable Certification
- UInt8 exportableValue = 0;
- [packetBodyData getBytes:&exportableValue length:1];
- self.value = @(exportableValue);
- } break;
- case PGPSignatureSubpacketTypePrimaryUserID: // NSNumber BOOL
- {
- // 5.2.3.19. Primary User ID
- UInt8 primaryUserIDValue = 0;
- [packetBodyData getBytes:&primaryUserIDValue length:1];
- self.value = @(primaryUserIDValue);
- } break;
- case PGPSignatureSubpacketTypeSignerUserID: // NSString
- // side note: This subpacket is not appropriate to use to refer to a User Attribute packet.
- case PGPSignatureSubpacketTypePreferredKeyServer: // NSString
- case PGPSignatureSubpacketTypePolicyURI: // NSString
- {
- self.value = [[NSString alloc] initWithData:packetBodyData encoding:NSUTF8StringEncoding];
- } break;
- case PGPSignatureSubpacketTypeReasonForRevocation: // NSNumber
- {
- UInt8 revocationCode = 0;
- [packetBodyData getBytes:&revocationCode length:1];
- self.value = @(revocationCode);
- } break;
- case PGPSignatureSubpacketTypeKeyFlags: // NSArray of NSNumber
- {
- // 5.2.3.21. Key Flags
- // (N octets of flags) ???
- // This implementation supports max 8 octets (64bit)
- UInt64 flagByte = 0;
- [packetBodyData getBytes:&flagByte length:MIN((NSUInteger)8, packetBodyData.length)];
- NSMutableArray *flagsArray = [NSMutableArray array];
-
- if (flagByte & PGPSignatureFlagAllowCertifyOtherKeys) {
- [flagsArray addObject:@(PGPSignatureFlagAllowCertifyOtherKeys)];
- }
- if (flagByte & PGPSignatureFlagAllowSignData) {
- [flagsArray addObject:@(PGPSignatureFlagAllowSignData)];
- }
- if (flagByte & PGPSignatureFlagAllowEncryptCommunications) {
- [flagsArray addObject:@(PGPSignatureFlagAllowEncryptCommunications)];
- }
- if (flagByte & PGPSignatureFlagAllowEncryptStorage) {
- [flagsArray addObject:@(PGPSignatureFlagAllowEncryptStorage)];
- }
- if (flagByte & PGPSignatureFlagSecretComponentMayBeSplit) {
- [flagsArray addObject:@(PGPSignatureFlagSecretComponentMayBeSplit)];
- }
- if (flagByte & PGPSignatureFlagAllowAuthentication) {
- [flagsArray addObject:@(PGPSignatureFlagAllowAuthentication)];
- }
- if (flagByte & PGPSignatureFlagPrivateKeyMayBeInThePossesionOfManyPersons) {
- [flagsArray addObject:@(PGPSignatureFlagPrivateKeyMayBeInThePossesionOfManyPersons)];
- }
-
- self.value = flagsArray;
- } break;
- case PGPSignatureSubpacketTypePreferredSymetricAlgorithm: // NSArray of NSNumber(PGPSymmetricAlgorithm)
- {
- // 5.2.3.7. Preferred Symmetric Algorithms
- let algorithmsArray = [NSMutableArray array];
-
- for (NSUInteger i = 0; i < packetBodyData.length; i++) {
- PGPSymmetricAlgorithm algorithm = PGPSymmetricPlaintext;
- [packetBodyData getBytes:&algorithm range:(NSRange){i, 1}];
- [algorithmsArray addObject:@(algorithm)];
- }
-
- self.value = algorithmsArray;
- } break;
- case PGPSignatureSubpacketTypePreferredHashAlgorithm: // NSArray of NSNumber(PGPHashAlgorithm)
- {
- // 5.2.3.8. Preferred Hash Algorithms
- let algorithmsArray = [NSMutableArray<NSNumber *> array];
-
- for (NSUInteger i = 0; i < packetBodyData.length; i++) {
- PGPHashAlgorithm algorithm = PGPHashUnknown;
- [packetBodyData getBytes:&algorithm range:(NSRange){i, 1}];
- [algorithmsArray addObject:@(algorithm)];
- }
-
- self.value = algorithmsArray;
- } break;
- case PGPSignatureSubpacketTypePreferredCompressionAlgorithm: // NSArray of NSNumber(PGPCompressionAlgorithm)
- {
- // 5.2.3.9. Preferred Compression Algorithms
- // If this subpacket is not included, ZIP is preferred.
- NSMutableArray *algorithmsArray = [NSMutableArray array];
-
- for (UInt8 i = 0; i < packetBodyData.length; i++) {
- PGPCompressionAlgorithm algorithm = PGPCompressionUncompressed;
- [packetBodyData getBytes:&algorithm range:(NSRange){i, 1}];
- [algorithmsArray addObject:@(algorithm)];
- }
-
- self.value = algorithmsArray;
- } break;
- case PGPSignatureSubpacketTypeKeyServerPreference: // NSArray of NSNumber(PGPKeyServerPreferenceFlags)
- {
- // 5.2.3.17. Key Server Preferences
- PGPKeyServerPreferenceFlags flag = PGPKeyServerPreferenceUnknown;
- [packetBodyData getBytes:&flag length:MIN((NSUInteger)8, packetBodyData.length)];
-
- NSMutableArray *flagsArray = [NSMutableArray array];
- if (flag & PGPKeyServerPreferenceNoModify) {
- [flagsArray addObject:@(PGPKeyServerPreferenceNoModify)];
- }
- self.value = flagsArray;
- } break;
- case PGPSignatureSubpacketTypeFeatures: // NSArray of NSNumber(PGPFeature)
- {
- // 5.2.3.24. Features
- NSMutableArray *featuresArray = [NSMutableArray array];
-
- for (NSUInteger i = 0; i < packetBodyData.length; i++) {
- PGPFeature feature = PGPFeatureModificationUnknown;
- [packetBodyData getBytes:&feature range:(NSRange){i, 1}];
- [featuresArray addObject:@(feature)];
- }
-
- self.value = featuresArray;
- } break;
- default:
- if (self.type & 0x80) {
- PGPLogWarning(@"Unsupported critical subpacket type %d", self.type);
- } else {
- PGPLogDebug(@"Unsupported subpacket type %d", self.type);
- }
- self.value = packetBodyData;
- break;
- }
-}
-
-+ (PGPSignatureSubpacketHeader *)subpacketHeaderFromData:(NSData *)headerData {
- NSUInteger position = 0;
-
- UInt8 lengthOctets = 0;
- NSUInteger subpacketLength = 0;
-
- // The length includes the type octet but not this length. Its format
- // is similar to the "new" format packet header lengths, but cannot have Partial Body Lengths.
- [PGPPacketHeader getLengthFromNewFormatOctets:headerData bodyLength:&subpacketLength bytesCount:&lengthOctets isPartial:nil];
- position = position + lengthOctets;
-
- // TODO: Bit 7 of the subpacket type is the "critical" bit.
- PGPSignatureSubpacketType subpacketType = PGPSignatureSubpacketTypeUnknown;
- [headerData getBytes:&subpacketType range:(NSRange){position, 1}];
- lengthOctets += 1;
-
- // Note: "The length includes the type octet but not this length"
- // Example: 02 19 01
- // length 0x02 = 2
- // type 0x19 = 25
- // body: 0x01 = 1
- // so... given body length is = 2 but body length is in fact = 1
- // this is because given body length include type octet which is from header namespace, not body really.
- // I'm drunk, or person who defined it this way was drunk.
- subpacketLength = subpacketLength - 1;
-
- let subpacketHeader = [[PGPSignatureSubpacketHeader alloc] init];
- subpacketHeader.type = subpacketType;
- subpacketHeader.headerLength = lengthOctets;
- subpacketHeader.bodyLength = subpacketLength;
-
- return subpacketHeader;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- NSMutableData *data = [NSMutableData data];
-
- // subpacket type
- PGPSignatureSubpacketType type = self.type;
- [data appendBytes:&type length:1];
-
- switch (self.type & 0x7F) {
- case PGPSignatureSubpacketTypeSignatureCreationTime: // NSDate
- {
- let date = PGPCast(self.value, NSDate);
- let signatureCreationTimestamp = CFSwapInt32HostToBig((UInt32)[date timeIntervalSince1970]);
- [data appendBytes:&signatureCreationTimestamp length:4];
- } break;
- case PGPSignatureSubpacketTypeEmbeddedSignature: // PGPSignature
- {
- let subpacketEmbeddedSignature = PGPCast(self.value, PGPSignatureSubpacketEmbeddedSignature);
- return [subpacketEmbeddedSignature export:error];
- } break;
- case PGPSignatureSubpacketTypeSignatureExpirationTime: // NSNumber
- case PGPSignatureSubpacketTypeKeyExpirationTime: {
- let validityPeriod = PGPCast(self.value, NSNumber);
- let validityPeriodInt = CFSwapInt32HostToBig((UInt32)validityPeriod.unsignedIntegerValue);
- [data appendBytes:&validityPeriodInt length:4];
- } break;
- case PGPSignatureSubpacketTypeIssuerKeyID: // PGPKeyID
- {
- let _Nullable keyID = PGPCast(self.value, PGPKeyID);
- [data pgp_appendData:[keyID export:nil]];
- } break;
- case PGPSignatureSubpacketTypeExportableCertification: // NSNumber BOOL
- case PGPSignatureSubpacketTypePrimaryUserID: // NSNumber BOOL
- {
- var boolValue = PGPCast(self.value, NSNumber).boolValue;
- [data appendBytes:&boolValue length:1];
- } break;
- case PGPSignatureSubpacketTypeSignerUserID: // NSString
- case PGPSignatureSubpacketTypePreferredKeyServer: // NSString
- case PGPSignatureSubpacketTypePolicyURI: // NSString
- {
- let stringValue = PGPCast(self.value, NSString);
- let _Nullable stringData = [stringValue dataUsingEncoding:NSUTF8StringEncoding];
- [data pgp_appendData:stringData];
- } break;
- case PGPSignatureSubpacketTypeReasonForRevocation: {
- // 5.2.3.23. Reason for Revocation
- let revocationCode = PGPCast(self.value, NSNumber);
- UInt8 revocationCodeByte = [revocationCode unsignedCharValue];
- [data appendBytes:&revocationCodeByte length:1];
- } break;
- case PGPSignatureSubpacketTypeKeyFlags: // NSArray of NSNumber PGPSignatureFlags
- {
- // TODO: actually it can be more than one byte (documented)
- // so I should calculate how many bytes do I need here
- let flagsArray = PGPCast(self.value, NSArray);
- if (!flagsArray) {
- break;
- }
- PGPSignatureFlags flagByte = PGPSignatureFlagUnknown;
- for (NSNumber *flagByteNumber in flagsArray) {
- flagByte = flagByte | ((UInt8)[flagByteNumber unsignedIntValue]);
- }
- [data appendBytes:&flagByte length:sizeof(PGPSignatureFlags)];
- } break;
- case PGPSignatureSubpacketTypePreferredSymetricAlgorithm: // NSArray of NSNumber(PGPSymmetricAlgorithm)
- {
- let algorithmsArray = PGPCast(self.value, NSArray);
- if (!algorithmsArray) {
- break;
- }
- for (NSNumber *val in algorithmsArray) {
- PGPSymmetricAlgorithm symmetricAlgorithm = (UInt8)val.unsignedIntValue;
- [data appendBytes:&symmetricAlgorithm length:sizeof(PGPSymmetricAlgorithm)];
- }
- } break;
- case PGPSignatureSubpacketTypePreferredHashAlgorithm: // NSArray of NSNumber(PGPHashAlgorithm)
- {
- let algorithmsArray = PGPCast(self.value, NSArray);
- if (!algorithmsArray) {
- break;
- }
-
- for (NSNumber *val in algorithmsArray) {
- PGPHashAlgorithm hashAlgorithm = (UInt8)val.unsignedIntValue;
- [data appendBytes:&hashAlgorithm length:sizeof(PGPHashAlgorithm)];
- }
- } break;
- case PGPSignatureSubpacketTypePreferredCompressionAlgorithm: // NSArray of NSNumber(PGPCompressionAlgorithm)
- {
- let algorithmsArray = PGPCast(self.value, NSArray);
- if (!algorithmsArray) {
- break;
- }
-
- for (NSNumber *val in algorithmsArray) {
- PGPCompressionAlgorithm hashAlgorithm = (UInt8)val.unsignedIntValue;
- [data appendBytes:&hashAlgorithm length:sizeof(PGPCompressionAlgorithm)];
- }
- } break;
- case PGPSignatureSubpacketTypeKeyServerPreference: // NSArray of NSNumber PGPKeyServerPreferenceFlags
- {
- // TODO: actually it can be more than one byte (documented)
- // so I should calculate how many bytes do I need here
- PGPKeyServerPreferenceFlags allFlags = PGPKeyServerPreferenceUnknown;
- let flagsArray = PGPCast(self.value, NSArray);
- if (!flagsArray) {
- break;
- }
- for (NSNumber *flagNumber in flagsArray) {
- PGPKeyServerPreferenceFlags flag = (PGPKeyServerPreferenceFlags)flagNumber.unsignedIntValue;
- allFlags = allFlags | flag;
- }
- [data appendBytes:&allFlags length:sizeof(PGPKeyServerPreferenceFlags)];
- } break;
- case PGPSignatureSubpacketTypeFeatures: // NSArray of NSNumber PGPFeature
- {
- // TODO: actually it can be more than one byte (documented)
- // so I should calculate how many bytes do I need here
- let flagsArray = PGPCast(self.value, NSArray);
- if (!flagsArray) {
- break;
- }
- PGPFeature flagByte = PGPFeatureModificationUnknown;
- for (NSNumber *flagByteNumber in flagsArray) {
- flagByte = flagByte | ((UInt8)[flagByteNumber unsignedIntValue]);
- }
- [data appendBytes:&flagByte length:sizeof(PGPSignatureFlags)];
- } break;
- default:
- if (self.type & 0x80) {
- PGPLogDebug(@"Unsupported critical subpacket type %d", self.type);
- } else {
- PGPLogDebug(@"Unsupported subpacket type %d", self.type);
- }
- let unsupportedValueData = PGPCast(self.value, NSData);
- [data appendData:unsupportedValueData];
- break;
- }
-
- // subpacket = length + tag(type) + body
- NSMutableData *subpacketData = [NSMutableData data];
- // the subpacket length (1, 2, or 5 octets),
- let subpacketLengthData = [PGPPacketHeader buildNewFormatLengthDataForData:data];
- [subpacketData pgp_appendData:subpacketLengthData]; // data with tag
- [subpacketData pgp_appendData:data];
- return subpacketData;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([other isKindOfClass:self.class]) {
- return [self isEqualToSignatureSubpacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToSignatureSubpacket:(PGPSignatureSubpacket *)packet {
- return self.type == packet.type &&
- self.length == packet.length &&
- PGPEqualObjects(self.value, packet.value);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = 1;
- result = prime * result + self.type;
- result = prime * result + self.length;
- result = prime * result + self.value.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone * __unused)zone {
- return [[PGPSignatureSubpacket alloc] initWithType:self.type andValue:self.value];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketCreationTime.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketCreationTime.m
deleted file mode 100755
index 8dabb154838be878c197434c8e821397a5a001d1..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketCreationTime.m
+++ /dev/null
@@ -1,46 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSignatureSubpacketCreationTime.h"
-#import "NSData+PGPUtils.h"
-#import "PGPPacket.h"
-#import "PGPPacket+Private.h"
-#import "PGPMacros+Private.h"
-
-// PGPSignatureSubpacketTypeSignatureCreationTime
-
-NS_ASSUME_NONNULL_BEGIN
-
-static const NSUInteger PGPSignatureSubpacketLength = 4;
-
-@implementation PGPSignatureSubpacketCreationTime
-
-- (instancetype)initWithDate:(NSDate *)date {
- if ((self = [super init])) {
- _value = [date copy];
- }
- return self;
-}
-
-+ (instancetype)packetWithData:(NSData *)packetBodyData {
- UInt32 signatureCreationTimestamp = 0;
- [packetBodyData getBytes:&signatureCreationTimestamp length:PGPSignatureSubpacketLength];
- signatureCreationTimestamp = CFSwapInt32BigToHost(signatureCreationTimestamp);
- let date = [NSDate dateWithTimeIntervalSince1970:signatureCreationTimestamp];
- return [[PGPSignatureSubpacketCreationTime alloc] initWithDate:date];
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone * __unused)zone {
- return [[PGPSignatureSubpacketCreationTime alloc] initWithDate:self.value];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketEmbeddedSignature.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketEmbeddedSignature.m
deleted file mode 100755
index 3c7311d2e051397a3be02ac8610aee4410d37a5d..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketEmbeddedSignature.m
+++ /dev/null
@@ -1,70 +0,0 @@
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSignatureSubpacketEmbeddedSignature.h"
-#import "PGPSignaturePacket+Private.h"
-#import "PGPMacros+Private.h"
-#import "NSData+PGPUtils.h"
-#import "PGPPacket+Private.h"
-#import "PGPPacketHeader.h"
-#import "PGPFoundation.h"
-
-// PGPSignatureSubpacketTypeEmbeddedSignature
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPSignatureSubpacketEmbeddedSignature ()
-
-@property (nonatomic, copy, readonly) PGPSignaturePacket *signaturePacket;
-
-@end
-
-@implementation PGPSignatureSubpacketEmbeddedSignature
-
-- (instancetype)initWithSignature:(PGPSignaturePacket *)signature {
- if ((self = [super init])) {
- _signaturePacket = [signature copy];
- }
- return self;
-}
-
-+ (instancetype)packetWithData:(NSData *)packetBodyData {
- let signaturePacket = [PGPSignaturePacket packetWithBody:packetBodyData];
- let embeddedSignature = [[PGPSignatureSubpacketEmbeddedSignature alloc] initWithSignature:signaturePacket];
- return embeddedSignature;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- let type = PGPSignatureSubpacketTypeEmbeddedSignature;
- let typedData = [NSMutableData dataWithBytes:&type length:1];
-
- let signatureValue = PGPCast(self.signaturePacket, PGPSignaturePacket);
- let _Nullable signatureBody = [signatureValue buildFullSignatureBodyData];
- if (!signatureBody) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Unable to export packet. Can't build signature." }];
- }
- return nil;
- }
-
- [typedData appendData:signatureBody];
-
- let output = [NSMutableData data];
- let length = [PGPPacketHeader buildNewFormatLengthDataForData:typedData];
- [output appendData:length];
- [output appendData:typedData];
-
- return output;
-}
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- return [[PGPSignatureSubpacketEmbeddedSignature alloc] initWithSignature:[self.signaturePacket copyWithZone:zone]];
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketHeader.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketHeader.m
deleted file mode 100755
index d369a328ad40544351053bc3eb210122ee139fe3..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSignatureSubpacketHeader.m
+++ /dev/null
@@ -1,13 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSignatureSubpacketHeader.h"
-
-@implementation PGPSignatureSubpacketHeader
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymetricKeyEncryptedSessionKeyPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSymetricKeyEncryptedSessionKeyPacket.m
deleted file mode 100755
index 536fa668f72930681e8c2ee6d9aade11f1ce0ed0..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymetricKeyEncryptedSessionKeyPacket.m
+++ /dev/null
@@ -1,122 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-// 5.3. Symmetric-Key Encrypted Session Key Packets (Tag 3)
-
-#import "PGPSymetricKeyEncryptedSessionKeyPacket.h"
-#import "NSData+PGPUtils.h"
-#import "NSMutableData+PGPUtils.h"
-#import "PGPCryptoUtils.h"
-#import "PGPFingerprint.h"
-#import "PGPKeyID.h"
-#import "PGPS2K.h"
-#import "PGPMPI.h"
-#import "PGPPKCSEme.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPRSA.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPSymetricKeyEncryptedSessionKeyPacket
-
-- (instancetype)init {
- if (self = [super init]) {
- _version = 4;
- _symmetricAlgorithm = PGPSymmetricPlaintext;
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPSymetricKeyEncryptedSessionKeyPacketTag; // 3
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // A one-octet number giving the version number of the packet type. The currently defined value for packet version is 3.
- [packetBody getBytes:&_version range:(NSRange){position, 1}];
- NSAssert(self.version == 4, @"The currently defined value for packet version is 4");
- position = position + 1;
-
- // A one-octet number describing the symmetric algorithm used.
- [packetBody getBytes:&_symmetricAlgorithm range:(NSRange){position, 1}];
- position = position + 1;
-
- // A string-to-key (S2K) specifier, length as defined above.
- NSUInteger s2kParsedLength = 0;
- self.s2k = [PGPS2K S2KFromData:packetBody atPosition:position length:&s2kParsedLength];
- position = position + s2kParsedLength;
-
- if (packetBody.length > position) {
- // Optionally, the encrypted session key itself, which is decrypted with the string-to-key object.
- self.encryptedSessionKey = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
- }
-
- return position;
-}
-
-#pragma mark - PGPExportable
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- let bodyData = [NSMutableData data];
-
- [bodyData appendBytes:&_version length:1]; // 1
- [bodyData appendBytes:&_symmetricAlgorithm length:1]; // 1
- [bodyData pgp_appendData:[self.s2k export:error]];
- [bodyData pgp_appendData:self.encryptedSessionKey];
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return bodyData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToSessionKeyPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToSessionKeyPacket:(PGPSymetricKeyEncryptedSessionKeyPacket *)packet {
- return self.version == packet.version &&
- self.symmetricAlgorithm == packet.symmetricAlgorithm &&
- PGPEqualObjects(self.s2k, packet.s2k) &&
- self.encryptedSessionKey == packet.encryptedSessionKey;
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- result = prime * result + self.symmetricAlgorithm;
- result = prime * result + self.s2k.hash;
- result = prime * result + self.encryptedSessionKey.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (instancetype)copyWithZone:(nullable NSZone *)zone {
- let duplicate = PGPCast([super copyWithZone:zone], PGPSymetricKeyEncryptedSessionKeyPacket);
- PGPAssertClass(duplicate, PGPSymetricKeyEncryptedSessionKeyPacket);
- duplicate.version = self.version;
- duplicate.symmetricAlgorithm = self.symmetricAlgorithm;
- duplicate.s2k = self.s2k;
- duplicate.encryptedSessionKey = self.encryptedSessionKey;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedDataPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedDataPacket.m
deleted file mode 100755
index b5327fab6a2451ed1d59586dd38c12008f2daa9c..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedDataPacket.m
+++ /dev/null
@@ -1,153 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-// Parse only
-
-#import "PGPSymmetricallyEncryptedDataPacket.h"
-#import "PGPCryptoCFB.h"
-#import "PGPCryptoUtils.h"
-#import "PGPPublicKeyPacket.h"
-#import "PGPPacket+Private.h"
-#import "PGPMacros+Private.h"
-#import "PGPCompressedPacket.h"
-#import "NSArray+PGPUtils.h"
-#import "PGPFoundation.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <CommonCrypto/CommonCryptor.h>
-#import <CommonCrypto/CommonDigest.h>
-
-#import <openssl/aes.h>
-#import <openssl/blowfish.h>
-#import <openssl/camellia.h>
-#import <openssl/cast.h>
-#import <openssl/des.h>
-#import <openssl/idea.h>
-#import <openssl/sha.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPSymmetricallyEncryptedDataPacket
-
-- (PGPPacketTag)tag {
- return PGPSymmetricallyEncryptedDataPacketTag; // 9
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- self.encryptedData = packetBody;
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- if (!self.encryptedData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Unable to export packet. Missing encrypted data." }];
- }
- return nil;
- }
-
- return self.encryptedData;
-}
-
-- (NSArray<PGPPacket *> *)readPacketsFromData:(NSData *)data offset:(NSUInteger)offsetPosition {
- let accumulatedPackets = [NSMutableArray<PGPPacket *> array];
- NSInteger offset = offsetPosition;
- NSUInteger consumedBytes = 0;
- while (offset < (NSInteger)data.length) {
- let packet = [PGPPacketFactory packetWithData:data offset:offset consumedBytes:&consumedBytes];
- [accumulatedPackets pgp_addObject:packet];
-
- // A compressed Packet contains more packets.
- // TODO: Compression should be moved outside, be more generic to handle compressed packet from anywhere
- let _Nullable compressedPacket = PGPCast(packet, PGPCompressedPacket);
- if (compressedPacket) {
- let uncompressedPackets = [self readPacketsFromData:compressedPacket.decompressedData offset:0];
- [accumulatedPackets addObjectsFromArray:uncompressedPackets ?: @[]];
- }
-
- // corrupted data. Move by one byte in hope we find some packet there, or EOF.
- if (consumedBytes == 0) {
- offset++;
- }
- offset += (NSInteger)consumedBytes;
- }
- return accumulatedPackets;
-}
-
-// return array of packets
-- (NSArray<PGPPacket *> *)decryptWithSessionKeyAlgorithm:(PGPSymmetricAlgorithm)sessionKeyAlgorithm sessionKeyData:(NSData *)sessionKeyData error:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(self.encryptedData, @"Missing encrypted data to decrypt");
-
- if (!self.encryptedData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Missing data to decrypt." }];
- }
- return @[];
- }
-
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:sessionKeyAlgorithm];
-
- // The Initial Vector (IV) is specified as all zeros.
- let ivData = [NSMutableData dataWithLength:blockSize];
-
- NSUInteger position = 0;
- // preamble + data
- let decryptedData = [PGPCryptoCFB decryptData:self.encryptedData sessionKeyData:sessionKeyData symmetricAlgorithm:sessionKeyAlgorithm iv:ivData syncCFB:YES];
- // full prefix blockSize + 2
- let prefixRandomFullData = [decryptedData subdataWithRange:(NSRange){position, blockSize + 2}];
- position = position + blockSize + 2;
-
- // check if suffix match
- if (!PGPEqualObjects([prefixRandomFullData subdataWithRange:(NSRange){blockSize + 2 - 4, 2}] ,[prefixRandomFullData subdataWithRange:(NSRange){blockSize + 2 - 2, 2}])) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Validation failed. Random suffix mismatch." }];
- }
- return @[];
- }
-
- let packets = [self readPacketsFromData:decryptedData offset:position];
- return packets.count > 0 ? [packets subarrayWithRange:(NSRange){0, packets.count - 1}] : packets;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToSymmetricallyEncryptedDataPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToSymmetricallyEncryptedDataPacket:(PGPSymmetricallyEncryptedDataPacket *)packet {
- return PGPEqualObjects(self.encryptedData, packet.encryptedData);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.encryptedData.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPSymmetricallyEncryptedDataPacket);
- if (!duplicate) {
- return nil;
- }
- duplicate.encryptedData = self.encryptedData;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m
deleted file mode 100755
index 6244ab10dc8dceb0f3808e920ac6335f26c8b861..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.m
+++ /dev/null
@@ -1,298 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPSymmetricallyEncryptedIntegrityProtectedDataPacket.h"
-#import "NSData+PGPUtils.h"
-#import "PGPPacket+Private.h"
-#import "PGPCompressedPacket.h"
-#import "PGPCryptoCFB.h"
-#import "PGPCryptoUtils.h"
-#import "PGPLiteralPacket.h"
-#import "PGPModificationDetectionCodePacket.h"
-#import "PGPOnePassSignaturePacket.h"
-#import "PGPPartialKey.h"
-#import "PGPRSA.h"
-#import "PGPSecretKeyPacket.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-#import <CommonCrypto/CommonCryptor.h>
-#import <CommonCrypto/CommonDigest.h>
-
-#import <openssl/aes.h>
-#import <openssl/blowfish.h>
-#import <openssl/camellia.h>
-#import <openssl/cast.h>
-#import <openssl/des.h>
-#import <openssl/idea.h>
-#import <openssl/sha.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPSymmetricallyEncryptedIntegrityProtectedDataPacket ()
-
-@property (nonatomic, readwrite) NSUInteger version;
-
-@end
-
-
-@implementation PGPSymmetricallyEncryptedIntegrityProtectedDataPacket
-
-- (instancetype)init {
- if (self = [super init]) {
- _version = 1;
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPSymmetricallyEncryptedIntegrityProtectedDataPacketTag; // 18
-}
-
-- (NSArray<PGPPacket *> *)readPacketsFromData:(NSData *)keyringData offset:(NSUInteger)offsetPosition mdcLength:(nullable NSUInteger *)mdcLength {
- let accumulatedPackets = [NSMutableArray<PGPPacket *> array];
- if (mdcLength) { *mdcLength = 0; }
- NSInteger offset = offsetPosition;
- NSUInteger consumedBytes = 0;
- while (offset < (NSInteger)keyringData.length) {
- let packet = [PGPPacketFactory packetWithData:keyringData offset:offset consumedBytes:&consumedBytes];
- if (packet) {
- [accumulatedPackets addObject:packet];
- if (packet.tag != PGPModificationDetectionCodePacketTag) {
- if (mdcLength) {
- *mdcLength += consumedBytes;
- }
- }
-
- // A compressed Packet contains more packets
- let _Nullable compressedPacket = PGPCast(packet, PGPCompressedPacket);
- if (compressedPacket) {
- // TODO: Compression should be moved outside, be more generic to handle compressed packet from anywhere
- let packets = [self readPacketsFromData:compressedPacket.decompressedData offset:0 mdcLength:nil];
- if (packets) {
- [accumulatedPackets addObjectsFromArray:packets];
- }
- }
-
- if (packet.indeterminateLength && accumulatedPackets.count > 0 && PGPCast(accumulatedPackets.firstObject, PGPCompressedPacket)) {
- // FIXME: substract size of PGPModificationDetectionCodePacket in this very special case - TODO: fix this
- offset -= 22;
- if (mdcLength) {
- *mdcLength -= 22;
- }
- }
- }
-
- // corrupted data. Move by one byte in hope we find some packet there, or EOF.
- if (consumedBytes == 0) {
- offset++;
- }
-
- offset += consumedBytes;
- }
- return accumulatedPackets;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = 0;
-
- // The content of an encrypted data packet is more OpenPGP packets
- // once decrypted, so recursively handle them
- [packetBody getBytes:&_version range:(NSRange){position, 1}];
- position = position + 1;
-
- // - Encrypted data, the output of the selected symmetric-key cipher
- // operating in OpenPGP's variant of Cipher Feedback (CFB) mode.
- self.encryptedData = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
- position = position + self.encryptedData.length;
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(self.encryptedData, @"No encrypted data?");
- NSAssert(self.version == 1, @"Require version == 1");
-
- if (!self.encryptedData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"No encrypted data? try encrypt first" }];
- }
- return nil;
- }
-
- let bodyData = [NSMutableData data];
- // A one-octet version number.
- [bodyData appendBytes:&_version length:1];
- // Encrypted data
- [bodyData appendData:self.encryptedData];
-
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return bodyData;
- }];
-}
-
-// return array of packets
-- (NSArray<PGPPacket *> *)decryptWithSessionKeyAlgorithm:(PGPSymmetricAlgorithm)sessionKeyAlgorithm sessionKeyData:(NSData *)sessionKeyData error:(NSError * __autoreleasing _Nullable *)error {
- NSAssert(self.encryptedData, @"Missing encrypted data to decrypt");
-
- if (!self.encryptedData) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Missing data to decrypt." }];
- }
- return @[];
- }
-
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:sessionKeyAlgorithm];
-
- // The Initial Vector (IV) is specified as all zeros.
- let ivData = [NSMutableData dataWithLength:blockSize];
-
- NSUInteger position = 0;
- // preamble + data + mdc
- let decryptedData = [PGPCryptoCFB decryptData:self.encryptedData sessionKeyData:sessionKeyData symmetricAlgorithm:sessionKeyAlgorithm iv:ivData syncCFB:NO];
- // full prefix blockSize + 2
- let prefixRandomFullData = [decryptedData subdataWithRange:(NSRange){position, blockSize + 2}];
- position = position + blockSize + 2;
-
- // check if suffix match
- if (!PGPEqualObjects([prefixRandomFullData subdataWithRange:(NSRange){blockSize + 2 - 4, 2}] ,[prefixRandomFullData subdataWithRange:(NSRange){blockSize + 2 - 2, 2}])) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Validation failed. Random suffix mismatch." }];
- }
- return @[];
- }
-
- NSUInteger mdcLength = 0;
- let packets = [self readPacketsFromData:decryptedData offset:position mdcLength:&mdcLength];
-
- let _Nullable lastPacket = PGPCast(packets.lastObject, PGPPacket);
- if (!lastPacket || lastPacket.tag != PGPModificationDetectionCodePacketTag) {
- // No Integrity Protected found, can't verify. Guess it's modified.
- // if (checkIsContentModified) { *checkIsContentModified = YES; }
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Content modification detected." }];
- }
- return @[];
- }
-
- let _Nullable mdcPacket = PGPCast(lastPacket, PGPModificationDetectionCodePacket);
- if (!mdcPacket) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Unexpected sequence of data (missing MDC)." }];
- }
- return @[];
- }
-
- let toMDCData = [[NSMutableData alloc] init];
- // preamble
- [toMDCData appendData:prefixRandomFullData];
- // validation: calculate MDC hash to check if literal data is modified
- [toMDCData appendData:[decryptedData subdataWithRange:(NSRange){position, mdcLength}]];
-
- // and then also includes two octets of values 0xD3, 0x14 (sha length)
- UInt8 mdc_suffix[2] = {0xD3, 0x14};
- [toMDCData appendBytes:&mdc_suffix length:2];
-
- let mdcHash = [toMDCData pgp_SHA1];
- if (!mdcPacket || !PGPEqualObjects(mdcHash,mdcPacket.hashData)) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{ NSLocalizedDescriptionKey: @"Unable to decrypt. Validation failed. Content modification detected." }];
- }
- return @[];
- }
-
- return [packets subarrayWithRange:(NSRange){0, packets.count - 1}];
-}
-
-- (BOOL)encrypt:(NSData *)literalPacketData symmetricAlgorithm:(PGPSymmetricAlgorithm)sessionKeyAlgorithm sessionKeyData:(NSData *)sessionKeyData error:(NSError * __autoreleasing _Nullable *)error {
- // OpenPGP does symmetric encryption using a variant of Cipher Feedback mode (CFB mode).
- NSUInteger blockSize = [PGPCryptoUtils blockSizeOfSymmetricAlhorithm:sessionKeyAlgorithm];
-
- // The Initial Vector (IV) is specified as all zeros.
- let ivData = [NSMutableData dataWithLength:blockSize];
-
- // Prepare preamble
- // Instead of using an IV, OpenPGP prefixes a string of length equal to the block size of the cipher plus two to the data before it is encrypted.
- // The first block-size octets (for example, 8 octets for a 64-bit block length) are random,
- uint8_t buf[blockSize];
- if (SecRandomCopyBytes(kSecRandomDefault, blockSize, buf) == -1) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{NSLocalizedDescriptionKey: @"Encryption failed. Cannot prepare random data."}];
- }
- return NO;
- }
- let prefixRandomData = [NSMutableData dataWithBytes:buf length:blockSize];
-
- // and the following two octets are copies of the last two octets of the IV.
- let prefixRandomFullData = [NSMutableData dataWithData:prefixRandomData];
- [prefixRandomFullData appendData:[prefixRandomData subdataWithRange:(NSRange){prefixRandomData.length - 2, 2}]];
-
- // Prepare MDC Packet
- let toMDCData = [[NSMutableData alloc] init];
- // preamble
- [toMDCData appendData:prefixRandomFullData];
- // plaintext
- [toMDCData appendData:literalPacketData];
- // and then also includes two octets of values 0xD3, 0x14 (sha length)
- UInt8 mdc_suffix[2] = {0xD3, 0x14};
- [toMDCData appendBytes:&mdc_suffix length:2];
-
- let mdcPacket = [[PGPModificationDetectionCodePacket alloc] initWithData:toMDCData];
- let _Nullable mdcPacketData = [mdcPacket export:error];
- if (!mdcPacketData || (error && *error)) {
- return NO;
- }
-
- // Finally build encrypted packet data
- // Encrypt at once (the same encrypt key) preamble + data + mdc
- let toEncrypt = [NSMutableData data];
- [toEncrypt appendData:prefixRandomFullData];
- [toEncrypt appendData:literalPacketData];
- [toEncrypt appendData:mdcPacketData];
- let encrypted = [PGPCryptoCFB encryptData:toEncrypt sessionKeyData:sessionKeyData symmetricAlgorithm:sessionKeyAlgorithm iv:ivData syncCFB:NO];
-
- self.encryptedData = encrypted;
- return YES;
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToPGPSymmetricallyEncryptedIntegrityProtectedDataPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToPGPSymmetricallyEncryptedIntegrityProtectedDataPacket:(PGPSymmetricallyEncryptedIntegrityProtectedDataPacket *)packet {
- return self.version == packet.version;
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.version;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPSymmetricallyEncryptedIntegrityProtectedDataPacket);
- if (!duplicate) {
- return nil;
- }
-
- duplicate.version = self.version;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPTrustPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPTrustPacket.m
deleted file mode 100755
index 32e958180c03d69aed2bb02271a9f9b9a3f83d88..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPTrustPacket.m
+++ /dev/null
@@ -1,75 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPTrustPacket.h"
-#import "PGPMacros.h"
-#import "PGPMacros+Private.h"
-#import "PGPFoundation.h"
-
-@interface PGPTrustPacket ()
-
-@property (nonatomic, copy, readwrite) NSData *data;
-
-@end
-
-@implementation PGPTrustPacket
-
-- (PGPPacketTag)tag {
- return PGPTrustPacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- // 5.10. Trust Packet (Tag 12)
- // The format of Trust packets is defined by a given implementation.
- self.data = packetBody;
- position = position + self.data.length;
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- // Don't export trust packets
- // (1 octet "level" (depth), 1 octet of trust amount)
- return [self.data copy];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToTrustPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToTrustPacket:(PGPTrustPacket *)packet {
- return PGPEqualObjects(self.data, packet.data);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.data.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPTrustPacket);
- if (!duplicate) {
- return nil;
- }
- duplicate.data = self.data;
- return duplicate;
-}
-
-
-@end
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeImageSubpacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeImageSubpacket.m
deleted file mode 100755
index f87c81597d51a2c192a481fe6fb368e24c9ee1dc..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeImageSubpacket.m
+++ /dev/null
@@ -1,90 +0,0 @@
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-// 5.12.1. The Image Attribute Subpacket
-
-#import "PGPUserAttributeImageSubpacket.h"
-#import "PGPLogging.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPUserAttributeImageSubpacket
-
-@synthesize type = _type;
-
-- (instancetype)init {
- if ((self = [super init])) {
- _type = PGPUserAttributeSubpacketImage;
- }
- return self;
-}
-
-- (nullable NSData *)image {
- NSUInteger position = 0;
- // The first two octets of the image header contain the length of the image header.
- // Note that unlike other multi-octet numerical values in this document,
- // due to a historical accident this value is encoded as a little-endian number.
- UInt16 imageHeaderLength = 0;
- [self.valueData getBytes:&imageHeaderLength range:(NSRange){position, 2}];
- imageHeaderLength = CFSwapInt16LittleToHost(imageHeaderLength);
- position = position + 2;
-
- // The image header length is followed by a single octet for the image header version.
- UInt8 version = 0;
- [self.valueData getBytes:&version range:(NSRange){position, 1}];
- position = position + 1;
-
- if (version != 1) {
- PGPLogWarning(@"Unknown image header version.");
- return nil;
- }
-
- // The only currently defined encoding format is the value 1 to indicate JPEG.
- UInt8 encodingFormat = 0;
- [self.valueData getBytes:&encodingFormat range:(NSRange){position, 1}];
- position = position + 1;
-
- if (encodingFormat != 1) {
- PGPLogWarning(@"Unknown image encodign format.");
- return nil;
- }
-
- // The rest of the version 1 image header is made up of 12 reserved octets, all of which MUST be set to 0.
- const UInt8 twelveBytes[12] = {0,0,0,0,0,0,0,0,0,0,0,0};
- if (memcmp(twelveBytes, [self.valueData subdataWithRange:(NSRange){position, 12}].bytes, 12) != 0) {
- PGPLogWarning(@"Unexpected values.");
- return nil;
- }
- position = position + 12;
-
- // The rest of the image subpacket contains the image itself.
- return [self.valueData subdataWithRange:(NSRange){position, self.valueData.length - position}];
-}
-
-- (void)setImage:(nullable NSData *)image {
- let valueData = [NSMutableData data];
-
- let imageLength = CFSwapInt16HostToLittle((UInt16)image.length);
- [valueData appendBytes:&imageLength length:2];
-
- UInt8 headerVersion = 1;
- [valueData appendBytes:&headerVersion length:1];
-
- UInt8 encodingFormat = 1;
- [valueData appendBytes:&encodingFormat length:1];
-
- const UInt8 twelveBytes[12] = {0,0,0,0,0,0,0,0,0,0,0,0};
- [valueData appendBytes:&twelveBytes length:12];
-
- [valueData appendData:image];
-
- self.valueData = valueData;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributePacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributePacket.m
deleted file mode 100755
index 445666b3ed344ced45acb61983d54044581e96b9..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributePacket.m
+++ /dev/null
@@ -1,122 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPUserAttributePacket.h"
-#import "PGPUserAttributeSubpacket.h"
-#import "PGPUserAttributeImageSubpacket.h"
-#import "PGPPacketHeader.h"
-#import "PGPFoundation.h"
-#import "PGPMacros+Private.h"
-#import "PGPLogging.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPUserAttributePacket
-
-- (instancetype)init {
- if ((self = [super init])) {
- _subpackets = [NSArray<PGPUserAttributeSubpacket *> array];
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPUserAttributePacketTag;
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- const NSUInteger startPosition = [super parsePacketBody:packetBody error:error];
- NSUInteger position = startPosition;
-
- // read subpackets
- while (position < packetBody.length) {
- NSUInteger bodyLength = 0;
- UInt8 lengthBytesCount = 0;
- let subPacketData = [packetBody subdataWithRange:(NSRange){position, packetBody.length - position}];
- [PGPPacketHeader getLengthFromNewFormatOctets:subPacketData bodyLength:&bodyLength bytesCount:&lengthBytesCount isPartial:nil];
- position = position + lengthBytesCount;
-
- PGPUserAttributeSubpacketType subpacketType = 0;
- [subPacketData getBytes:&subpacketType range:(NSRange){position, 1}];
- position = position + 1;
-
- // the subpacket type is part of body
- let subPacketBodyData = [subPacketData subdataWithRange:(NSRange){position, bodyLength - 1}];
-
- switch (subpacketType) {
- case PGPUserAttributeSubpacketImage: {
- let subpacket = [[PGPUserAttributeImageSubpacket alloc] init];
- subpacket.type = subpacketType;
- subpacket.valueData = subPacketBodyData;
- self.subpackets = [self.subpackets arrayByAddingObject:subpacket];
- } break;
- default:
- // Ignore everything else
- break;
- }
-
- position = position + subPacketBodyData.length;
- }
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:PGPUserAttributePacketTag withBody:^NSData * {
- let bodyData = [NSMutableData data];
- for (PGPUserAttributeSubpacket *subpacket in self.subpackets) {
- if (!subpacket.valueData) {
- continue;
- }
-
- let subpacketType = subpacket.type;
- let subBodyData = [NSMutableData dataWithBytes:&subpacketType length:1];
- [subBodyData appendData:subpacket.valueData];
-
- let lengthOctets = [PGPPacketHeader buildNewFormatLengthDataForData:subBodyData];
- [bodyData appendData:lengthOctets];
- [bodyData appendData:subBodyData];
- }
- return bodyData;
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToAttributePacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToAttributePacket:(PGPUserAttributePacket *)packet {
- return PGPEqualObjects(self.subpackets,packet.subpackets);
-}
-
-- (NSUInteger)hash {
- NSUInteger result = [super hash];
- result = 31 * result + self.subpackets.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPUserAttributePacket);
- if (!duplicate) {
- return nil;
- }
- duplicate.subpackets = [[NSArray alloc] initWithArray:self.subpackets copyItems:YES];
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeSubpacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeSubpacket.m
deleted file mode 100755
index 03826bd78a17afcdc780937dbce86133400324cd..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserAttributeSubpacket.m
+++ /dev/null
@@ -1,28 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPUserAttributeSubpacket.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation PGPUserAttributeSubpacket
-
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone * __unused)zone {
- let duplicate = [PGPUserAttributeSubpacket new];
- duplicate.type = self.type;
- duplicate.valueData = self.valueData;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserIDPacket.m b/enzevalos_iphone/ObjectivePGP/Packets/PGPUserIDPacket.m
deleted file mode 100755
index 32b16f0ffcb00ebbb76522d1955265e45a474a6c..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Packets/PGPUserIDPacket.m
+++ /dev/null
@@ -1,88 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "PGPUserIDPacket.h"
-#import "PGPPacket+Private.h"
-#import "PGPFoundation.h"
-#import "PGPMacros+Private.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@interface PGPUserIDPacket ()
-
-@property (nonatomic, copy, readwrite) NSString *userID;
-
-@end
-
-@implementation PGPUserIDPacket
-
-- (instancetype)initWithUserID:(NSString *)userID {
- if ((self = [super init])) {
- _userID = [userID copy];
- }
- return self;
-}
-
-- (PGPPacketTag)tag {
- return PGPUserIDPacketTag;
-}
-
-- (NSString *)description {
- return [NSString stringWithFormat:@"%@ %@", [super description], self.userID];
-}
-
-- (NSUInteger)parsePacketBody:(NSData *)packetBody error:(NSError * __autoreleasing _Nullable *)error {
- NSUInteger position = [super parsePacketBody:packetBody error:error];
-
- self.userID = [[NSString alloc] initWithData:packetBody encoding:NSUTF8StringEncoding];
- position = position + packetBody.length;
-
- return position;
-}
-
-- (nullable NSData *)export:(NSError * __autoreleasing _Nullable *)error {
- return [PGPPacket buildPacketOfType:self.tag withBody:^NSData * {
- return [self.userID dataUsingEncoding:NSUTF8StringEncoding];
- }];
-}
-
-#pragma mark - isEqual
-
-- (BOOL)isEqual:(id)other {
- if (self == other) { return YES; }
- if ([super isEqual:other] && [other isKindOfClass:self.class]) {
- return [self isEqualToUserIDPacket:other];
- }
- return NO;
-}
-
-- (BOOL)isEqualToUserIDPacket:(PGPUserIDPacket *)packet {
- return PGPEqualObjects(self.userID, packet.userID);
-}
-
-- (NSUInteger)hash {
- NSUInteger prime = 31;
- NSUInteger result = [super hash];
- result = prime * result + self.userID.hash;
- return result;
-}
-
-#pragma mark - NSCopying
-
-- (id)copyWithZone:(nullable NSZone *)zone {
- let _Nullable duplicate = PGPCast([super copyWithZone:zone], PGPUserIDPacket);
- if (!duplicate) {
- return nil;
- }
- duplicate.userID = self.userID;
- return duplicate;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Utils/NSArray+PGPUtils.m b/enzevalos_iphone/ObjectivePGP/Utils/NSArray+PGPUtils.m
deleted file mode 100755
index 28bcdac6b60f530bf0896c176fe9bb34ed4b4c68..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Utils/NSArray+PGPUtils.m
+++ /dev/null
@@ -1,41 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "NSArray+PGPUtils.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation NSMutableArray (PGPUtils)
-
-- (void)pgp_addObject:(nullable id)anObject {
- if (anObject) {
- [self addObject:anObject];
- }
-}
-
-@end
-
-@implementation NSArray (PGPUtils)
-
-- (NSArray *)pgp_objectsPassingTest:(BOOL (^)(id obj, BOOL *stop))predicate {
- BOOL stop = NO;
- NSMutableArray *result = [NSMutableArray array];
- for (id object in self) {
- if (predicate(object,&stop)) {
- [result addObject:object];
- }
- if (stop) {
- break;
- }
- }
- return result;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Utils/NSData+PGPUtils.m b/enzevalos_iphone/ObjectivePGP/Utils/NSData+PGPUtils.m
deleted file mode 100755
index b372b7cf8a71747fe95401a29e334d11fc09f31b..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Utils/NSData+PGPUtils.m
+++ /dev/null
@@ -1,140 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "NSData+PGPUtils.h"
-#import "PGPCryptoHash.h"
-#import "PGPCryptoUtils.h"
-#import "PGPMacros+Private.h"
-
-#import <CommonCrypto/CommonCrypto.h>
-
-#import <openssl/aes.h>
-#import <openssl/blowfish.h>
-#import <openssl/camellia.h>
-#import <openssl/cast.h>
-#import <openssl/des.h>
-#import <openssl/idea.h>
-#import <openssl/ripemd.h>
-#import <openssl/sha.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation NSData (PGPUtils)
-
-/**
- * Calculates a 16bit sum of a string by adding each character * codes modulus 65535
- *
- * @return checksum
- */
-- (UInt16)pgp_Checksum {
- UInt32 s = 0;
- const UInt8 *bytes = self.bytes;
- for (NSUInteger i = 0; i < self.length; i++) {
- s = (s + (UInt8)bytes[i]);
- }
- s = s % 65536;
- return (UInt16)s;
-}
-
-#define CRC24_POLY 0x1864cfbL
-#define CRC24_INIT 0xB704CEL
-
-- (UInt32)pgp_CRC24 {
- UInt32 crc = CRC24_INIT;
- NSUInteger len = self.length;
- NSUInteger j = 0;
- const UInt8 *octets = self.bytes;
- for (j = len; j > 0; j--) {
- crc ^= (*octets++) << 16;
- for (int i = 0; i < 8; i++) {
- crc <<= 1;
- if (crc & 0x1000000) crc ^= CRC24_POLY;
- }
- }
-
- return crc & 0xFFFFFFL;
-}
-
-- (NSData *)pgp_MD5 {
- return PGPmd5(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_SHA1 {
- return PGPsha1(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_SHA224 {
- return PGPsha224(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_SHA256 {
- return PGPsha256(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_SHA384 {
- return PGPsha384(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_SHA512 {
- return PGPsha512(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_RIPEMD160 {
- return PGPripemd160(^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-- (NSData *)pgp_HashedWithAlgorithm:(PGPHashAlgorithm)hashAlgorithm {
- return PGPCalculateHash(hashAlgorithm, ^(void (^update)(const void *, int)) {
- update(self.bytes, (int)self.length);
- });
-}
-
-+ (NSData *)xor:(NSData *)d1 d2:(NSData *)d2 {
- let output = [NSMutableData dataWithLength:d1.length];
- let outputBuf = (uint8_t *)output.mutableBytes;
- let d1buf = (uint8_t *)d1.bytes;
- let d2buf = (uint8_t *)d2.bytes;
- for (NSUInteger i = 0; i < d1.length; i++) {
- outputBuf[i] = d1buf[i] ^ d2buf[i];
- }
- return output;
-}
-
-#pragma mark - NSValue
-
-+ (NSData *)dataWithValue:(NSValue *)value {
- NSUInteger size = 0;
- let encoding = [value objCType];
- NSGetSizeAndAlignment(encoding, &size, nil);
-
- let ptr = calloc(size,1);
- [value getValue:ptr];
- let data = [NSData dataWithBytes:ptr length:size];
- free(ptr);
-
- return data;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
-
diff --git a/enzevalos_iphone/ObjectivePGP/Utils/NSData+compression.m b/enzevalos_iphone/ObjectivePGP/Utils/NSData+compression.m
deleted file mode 100755
index 517bcffd75d036afa0c993828bcdd43f93acc866..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Utils/NSData+compression.m
+++ /dev/null
@@ -1,219 +0,0 @@
-//
-// NSData+zlib.m
-//
-// rfc1950 (zlib format)
-
-#import "NSData+compression.h"
-#import "PGPCompressedPacket.h"
-#import "PGPMacros+Private.h"
-#import <bzlib.h>
-#import <zlib.h>
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation NSData (compression)
-
-- (nullable NSData *)zipCompressed:(NSError * __autoreleasing _Nullable *)error {
- return [self zlibCompressed:error compressionType:PGPCompressionZIP];
-}
-
-- (nullable NSData *)zlibCompressed:(NSError * __autoreleasing _Nullable *)error {
- return [self zlibCompressed:error compressionType:PGPCompressionZLIB];
-}
-
-- (nullable NSData *)zlibCompressed:(NSError * __autoreleasing _Nullable *)error compressionType:(PGPCompressionAlgorithm)compressionType {
- if (self.length == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Compression failed"}];
- }
- return nil;
- }
-
- z_stream strm;
- strm.zalloc = Z_NULL;
- strm.zfree = Z_NULL;
- strm.opaque = Z_NULL;
- if (compressionType == PGPCompressionZLIB ? deflateInit(&strm, Z_DEFAULT_COMPRESSION) : deflateInit2(&strm, Z_DEFAULT_COMPRESSION, Z_DEFLATED, -13, 8, Z_DEFAULT_STRATEGY) != Z_OK) {
- if (error) {
- NSString *errorMsg = [NSString stringWithCString:strm.msg encoding:NSASCIIStringEncoding];
- *error = [NSError errorWithDomain:@"ZLIB" code:0 userInfo:@{NSLocalizedDescriptionKey: errorMsg}];
- }
- return nil;
- }
-
- let compressed = [NSMutableData dataWithLength:deflateBound(&strm, self.length)];
- strm.next_out = compressed.mutableBytes;
- strm.avail_out = (uInt)compressed.length;
- strm.next_in = (void *)self.bytes;
- strm.avail_in = (uInt)self.length;
-
- int ret = 0;
- do {
- ret = deflate(&strm, Z_FINISH);
- if (ret == Z_STREAM_ERROR) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:ret userInfo:@{ NSLocalizedDescriptionKey: [NSString stringWithFormat:@"Deflate problem. %@", [NSString stringWithCString:strm.msg ?: "" encoding:NSASCIIStringEncoding]]}];
- }
- return nil;
- }
- // extend buffer
- compressed.length = (NSUInteger)(compressed.length * 1.5f);
- strm.avail_out = (uInt)(compressed.length - strm.total_out);
- strm.next_out = compressed.mutableBytes + strm.total_out;
- } while (ret != Z_STREAM_END);
-
- compressed.length = strm.total_out;
-
- if (deflateEnd(&strm) != Z_OK) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{NSLocalizedDescriptionKey: [NSString stringWithCString:strm.msg ?: "" encoding:NSASCIIStringEncoding]}];
- }
- return nil;
- }
-
- return compressed;
-}
-
-- (nullable NSData *)zipDecompressed:(NSError * __autoreleasing _Nullable *)error {
- return [self zlibDecompressed:error compressionType:PGPCompressionZIP];
-}
-
-- (nullable NSData *)zlibDecompressed:(NSError * __autoreleasing _Nullable *)error {
- return [self zlibDecompressed:error compressionType:PGPCompressionZLIB];
-}
-
-
-- (nullable NSData *)zlibDecompressed:(NSError * __autoreleasing _Nullable *)error compressionType:(PGPCompressionAlgorithm)compressionType {
- if (self.length == 0) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:PGPErrorGeneral userInfo:@{ NSLocalizedDescriptionKey: @"Decompression failed"}];
- }
- return nil;
- }
-
- z_stream strm;
- strm.zalloc = Z_NULL;
- strm.zfree = Z_NULL;
- strm.opaque = Z_NULL;
- if (Z_OK != (compressionType == PGPCompressionZIP ? inflateInit2(&strm, -15) : inflateInit(&strm))) {
- if (error) {
- NSString *errorMsg = [NSString stringWithCString:strm.msg encoding:NSASCIIStringEncoding];
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{NSLocalizedDescriptionKey: errorMsg}];
- }
- return nil;
- }
-
- let decompressed = [NSMutableData dataWithLength:(NSUInteger)(self.length * 2.5f)];
- strm.next_out = [decompressed mutableBytes];
- strm.avail_out = (uInt)[decompressed length];
- strm.next_in = (void *)[self bytes];
- strm.avail_in = (uInt)[self length];
- // From the gnupg sources this might be needed - of course not like this, as we need to extend the input buffer length for this
- // if (compressionType == PGPCompressionZIP)
- //{
- // *(strm.next_in + (uInt)[self length]) = 0xFF;
- //}
-
- while (inflate(&strm, Z_FINISH) != Z_STREAM_END) {
- // inflate should return Z_STREAM_END on the first call
- decompressed.length = (NSUInteger)(decompressed.length * 1.5f);
- strm.next_out = decompressed.mutableBytes + strm.total_out;
- strm.avail_out = (uInt)(decompressed.length - strm.total_out);
- NSLog(@"total in: %@ out: %@",@(strm.total_in), @(strm.total_out));
- }
-
- [decompressed setLength:strm.total_out];
-
- int status = inflateEnd(&strm);
- if (status != Z_OK) {
- if (error) {
- NSString *errorMsg = [NSString stringWithCString:strm.msg ?: "" encoding:NSASCIIStringEncoding];
- *error = [NSError errorWithDomain:PGPErrorDomain code:0 userInfo:@{NSLocalizedDescriptionKey: errorMsg}];
- }
- return nil;
- }
-
- return decompressed;
-}
-
-- (nullable NSData *)bzip2Decompressed:(NSError * __autoreleasing _Nullable *)error {
- int bzret = 0;
- bz_stream stream = {.avail_in = 0x00};
- stream.next_in = (void *)[self bytes];
- stream.avail_in = (uInt)self.length;
-
- const int buffer_size = 10000;
- NSMutableData *buffer = [NSMutableData dataWithLength:buffer_size];
- stream.next_out = [buffer mutableBytes];
- stream.avail_out = buffer_size;
-
- bzret = BZ2_bzDecompressInit(&stream, 0, NO);
- if (bzret != BZ_OK) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:bzret userInfo:@{ NSLocalizedDescriptionKey: NSLocalizedString(@"BZ2_bzDecompressInit failed", nil) }];
- }
- return nil;
- }
-
- NSMutableData *decompressedData = [NSMutableData data];
- do {
- bzret = BZ2_bzDecompress(&stream);
- if (bzret < BZ_OK) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:bzret userInfo:@{ NSLocalizedDescriptionKey: NSLocalizedString(@"BZ2_bzDecompress failed", nil) }];
- }
- return nil;
- }
-
- [decompressedData appendBytes:[buffer bytes] length:(buffer_size - stream.avail_out)];
- stream.next_out = [buffer mutableBytes];
- stream.avail_out = buffer_size;
- } while (bzret != BZ_STREAM_END);
-
- BZ2_bzDecompressEnd(&stream);
- return decompressedData;
-}
-
-- (nullable NSData *)bzip2Compressed:(NSError * __autoreleasing _Nullable *)error {
- int bzret = 0;
- bz_stream stream = {.avail_in = 0x00};
- stream.next_in = (void *)[self bytes];
- stream.avail_in = (uInt)self.length;
- unsigned int compression = 9; // should be a value between 1 and 9 inclusive
-
- const int buffer_size = 10000;
- NSMutableData *buffer = [NSMutableData dataWithLength:buffer_size];
- stream.next_out = [buffer mutableBytes];
- stream.avail_out = buffer_size;
-
- bzret = BZ2_bzCompressInit(&stream, compression, 0, 0);
- if (bzret != BZ_OK) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:bzret userInfo:@{ NSLocalizedDescriptionKey: NSLocalizedString(@"BZ2_bzCompressInit failed", nil) }];
- }
- return nil;
- }
-
- NSMutableData *compressedData = [NSMutableData data];
-
- do {
- bzret = BZ2_bzCompress(&stream, (stream.avail_in) ? BZ_RUN : BZ_FINISH);
- if (bzret < BZ_OK) {
- if (error) {
- *error = [NSError errorWithDomain:PGPErrorDomain code:bzret userInfo:@{ NSLocalizedDescriptionKey: NSLocalizedString(@"BZ2_bzCompress failed", nil) }];
- }
- return nil;
- }
- [compressedData appendBytes:[buffer bytes] length:(buffer_size - stream.avail_out)];
- stream.next_out = [buffer mutableBytes];
- stream.avail_out = buffer_size;
-
- } while (bzret != BZ_STREAM_END);
-
- BZ2_bzCompressEnd(&stream);
- return compressedData;
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/ObjectivePGP/Utils/NSMutableData+PGPUtils.m b/enzevalos_iphone/ObjectivePGP/Utils/NSMutableData+PGPUtils.m
deleted file mode 100755
index 6fd452a401e016441101927b9efb3d8d83afe349..0000000000000000000000000000000000000000
--- a/enzevalos_iphone/ObjectivePGP/Utils/NSMutableData+PGPUtils.m
+++ /dev/null
@@ -1,35 +0,0 @@
-//
-// Copyright (c) Marcin Krzyżanowski. All rights reserved.
-//
-// THIS SOURCE CODE AND ANY ACCOMPANYING DOCUMENTATION ARE PROTECTED BY
-// INTERNATIONAL COPYRIGHT LAW. USAGE IS BOUND TO THE LICENSE AGREEMENT.
-// This notice may not be removed from this file.
-//
-
-#import "NSMutableData+PGPUtils.h"
-#import "PGPMacros.h"
-
-NS_ASSUME_NONNULL_BEGIN
-
-@implementation NSMutableData (PGPUtils)
-
-- (void)pgp_appendData:(nullable NSData *)other {
- if (other) {
- [self appendData:PGPNN(other)];
- }
-}
-
-- (void)XORWithData:(NSData *)data index:(NSUInteger)index {
- uint8_t *dataPtr = (uint8_t *)self.mutableBytes;
- const uint8_t *data2Ptr = (uint8_t *)data.bytes;
-
- NSAssert(index < self.length, @"Invalid index");
-
- for (NSUInteger i = 0; i < data.length && (i + index) < self.length; i++) {
- dataPtr[i + index] = dataPtr[i + index] ^ data2Ptr[i];
- }
-}
-
-@end
-
-NS_ASSUME_NONNULL_END
diff --git a/enzevalos_iphone/enzevalos_iphone-Bridging-Header.h b/enzevalos_iphone/enzevalos_iphone-Bridging-Header.h
index c091287910e55f10fbe19d26c24d307be64baf08..0ea62e53284ddd5a74c3660c2256db97abc4445f 100644
--- a/enzevalos_iphone/enzevalos_iphone-Bridging-Header.h
+++ b/enzevalos_iphone/enzevalos_iphone-Bridging-Header.h
@@ -9,7 +9,7 @@
#import <MailCore/MailCore.h>
#import <Onboard/OnboardingViewController.h>
#import <Onboard/OnboardingContentViewController.h>
-#import "ObjectivePGP/ObjectivePGP.h"
+#import <ObjectivePGP/ObjectivePGP.h>
#import <CommonCrypto/CommonHMAC.h>
#import <AppAuth/AppAuth.h>
#import <GTMAppAuth/GTMAppAuth.h>